Risk Management
-
Cybersecurity

Common ISO 27001 Pitfalls and How to Avoid Them
Common iso iec 27001 pitfalls and how to avoid them – Common ISO 27001 pitfalls and how to avoid them…
Read More » -
Cybersecurity Leadership

CISOs Guide Presenting Cybersecurity to Boards
Cisos guide to presenting cybersecurity to board directors raising awareness and cultivating investment – CISOs Guide to Presenting Cybersecurity to…
Read More » -
Cybersecurity

CISOs Laxity Fuels Cyberattacks
Cisos laxity towards cybersecurity is leading to more cyber attacks – CISOs’ laxity towards cybersecurity is leading to more cyber…
Read More » -
Cybersecurity
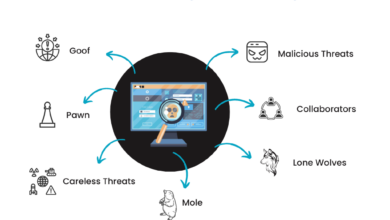
Ninety Percent of Organizations Vulnerable to Insider Threats A Cybersecurity Report
Ninety percent organizations vulnerable insider threats according new cybersecurity report – Ninety percent of organizations vulnerable to insider threats according…
Read More » -
IT Security

Be Cybersmart 4 ERP Security Best Practices
Be cybersmart 4 erp best practices to prioritize security – Be Cybersmart: 4 ERP Security Best Practices – that’s the…
Read More » -
WordPress Security
Across the Board Security A Holistic Approach
Across the Board Security isn’t just a buzzword; it’s the bedrock of a truly safe digital environment. Think of it…
Read More » -
Cybersecurity

A Briefing on What We Know Now on Insider Threats
A briefing on what we know now on insider threats sets the stage for a fascinating exploration of a critical…
Read More » -
Cybersecurity

5 Ways to Counteract Increasing Cyber Insurance Rates
5 Ways to Counteract Increasing Cyber Insurance Rates – Cyber insurance premiums are skyrocketing, leaving businesses scrambling for solutions. It’s…
Read More » -
IT Security

5 Reasons Why Governance Must Be a Priority for Secure File Sharing
5 Reasons Why Governance Must Be a Priority when it comes to secure file sharing: In today’s hyper-connected world, secure…
Read More » -
Cybersecurity

5 Advantages of Fraud Scoring
5 Advantages of Fraud Scoring: Ever wondered how businesses protect themselves from the sneaky world of fraud? It’s not just…
Read More »
