Employee Experience is Key to Digital Transformation Success
Employee experience is key to digital transformation success. This isn’t just a buzzphrase; it’s the bedrock upon which successful digital overhauls are built. Think about it: new software, streamlined processes, and cutting-edge technology are all useless if your employees aren’t on board, trained properly, and feeling valued throughout the entire transition. This post dives deep into why a positive employee experience is crucial for a smooth, efficient, and ultimately successful digital transformation.
We’ll explore everything from creating effective training programs and fostering open communication to gathering crucial employee feedback and the vital role leadership plays in navigating this change. We’ll also look at how to measure the impact of your efforts and ensure that your digital transformation truly benefits everyone involved – leading to increased productivity, higher engagement, and a happier, more productive workforce.
The Correlation Between Employee Experience and Digital Transformation Success
Digital transformation isn’t just about upgrading technology; it’s about fundamentally changing how a company operates. And at the heart of successful transformation lies the employee experience. A positive employee experience directly fuels adoption of new tools and processes, while a negative one can derail even the best-laid plans. The connection is undeniable, and understanding this correlation is crucial for any organization embarking on a digital journey.Positive employee experience directly impacts the successful adoption of new digital tools and technologies.
When employees feel valued, supported, and empowered, they’re more likely to embrace change and actively participate in the digital transformation process. This translates to higher engagement with new systems, quicker learning curves, and ultimately, faster implementation and a smoother transition. Conversely, a poor employee experience creates resistance and friction. Employees may feel overwhelmed, under-trained, or simply resentful of the changes, leading to slow adoption, technical glitches, and ultimately, project failure.
Impact of Positive Employee Experience on Digital Tool Adoption
A positive employee experience fosters a culture of innovation and collaboration. When employees feel heard and their concerns are addressed, they’re more receptive to new technologies. Effective training programs, clear communication, and readily available support systems all contribute to a smoother transition. For instance, a company implementing a new CRM system might find significantly higher adoption rates if they provide comprehensive training, ongoing support, and actively solicit feedback from employees during the rollout.
This proactive approach reduces frustration and builds confidence, leading to a more successful integration of the new tool.
Impact of Negative Employee Experience on Digital Transformation Initiatives
Conversely, a negative employee experience can significantly hinder digital transformation. Poor communication, inadequate training, and a lack of support can lead to widespread resistance and ultimately, project failure. Employees may actively resist using new systems, leading to lower productivity and a slower return on investment. For example, a company forcing a new project management software without proper training or consideration for employee workflows could experience widespread dissatisfaction, leading to employees reverting to old, inefficient methods.
This undermines the entire purpose of the digital transformation.
Comparison of Companies with Strong vs. Weak Employee Experience Programs, Employee experience is key to digital transformation success
Companies with strong employee experience programs tend to demonstrate significantly better outcomes in their digital transformations. They often boast higher employee engagement, faster adoption rates of new technologies, and improved overall productivity. These organizations prioritize employee feedback, invest in robust training and development, and foster a culture of continuous improvement. In contrast, companies lacking robust employee experience programs often struggle with digital transformation initiatives.
They may experience low adoption rates, resistance to change, and ultimately, a lower return on investment. Their digital transformation projects often fall behind schedule and exceed budget. The difference boils down to a fundamental understanding that people are the key to success, not just the technology.
Hypothetical Scenario Illustrating Improved Employee Experience Leading to Faster Digital Transformation
Imagine a mid-sized marketing agency undergoing a digital transformation to improve client communication and project management. Initially, they introduce a new project management platform with minimal training and little consideration for employee workflows. The result is widespread confusion, frustration, and a significant drop in productivity. However, after recognizing the issue, the agency invests in comprehensive training, personalized onboarding, and regular feedback sessions.
They also adjust the platform’s interface to better suit employee needs. The result is a dramatic improvement in adoption rates, a significant increase in efficiency, and a much faster return on investment. The transformation, once a source of stress, becomes a catalyst for growth and improved team collaboration.
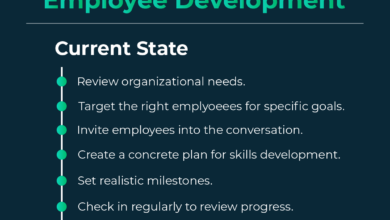
Employee Training and Onboarding in the Context of Digital Transformation: Employee Experience Is Key To Digital Transformation Success

Successful digital transformation hinges on effectively equipping your workforce with the skills and knowledge to navigate new systems and workflows. A well-structured training and onboarding program is crucial not only for operational efficiency but also for fostering a positive employee experience, boosting morale, and driving adoption of new technologies. Ignoring this aspect can lead to resistance, frustration, and ultimately, the failure of the transformation initiative.Effective employee training programs must be more than just technical tutorials; they should focus on building confidence and competence, making employees feel valued and supported throughout the transition.
This involves a holistic approach that considers the individual learning styles and needs of employees, incorporating various training methodologies and ongoing support mechanisms.
Designing an Effective Employee Training Program for Digital Systems
A successful training program should be meticulously planned and implemented, considering the specific digital tools being introduced. It should incorporate a blended learning approach, combining online modules, hands-on workshops, and mentoring opportunities. For instance, a company implementing a new CRM system might start with online modules introducing the system’s features, followed by workshops focusing on practical application scenarios using sample data, and finally, provide ongoing support through dedicated mentors or online forums.
The program should be modular and allow employees to learn at their own pace, providing regular assessments to track progress and identify areas needing further attention. Accessibility is key; ensure materials are available in multiple formats to cater to diverse learning preferences.
Onboarding New Employees in a Digitally Transformed Workplace
The onboarding process for new hires in a digitally transformed environment should be streamlined and engaging, focusing on a seamless integration into the new digital workflows. A step-by-step procedure might include: (1) Pre-boarding materials: Before their first day, new employees receive access to online resources introducing the company culture, digital tools, and expectations. (2) Initial orientation: A comprehensive introduction to the company’s digital infrastructure, including login credentials, access permissions, and essential software.
(3) System-specific training: Targeted training on the key digital systems they’ll be using, incorporating hands-on exercises and practical applications. (4) Mentorship and buddy system: Pairing new hires with experienced colleagues who can provide ongoing support and guidance. (5) Regular check-ins: Scheduled meetings with managers to monitor progress, address challenges, and provide feedback. This structured approach ensures new employees quickly become proficient in using the new systems and feel fully integrated into the team.
Best Practices for Creating Engaging and Effective Training Materials
Engaging training materials are critical for effective knowledge transfer. Microlearning modules, short videos, interactive simulations, and gamified exercises can significantly improve knowledge retention and engagement compared to lengthy, text-heavy manuals. For example, instead of a lengthy document explaining the new project management software, short, focused videos demonstrating specific features, followed by interactive quizzes, would be more effective. The materials should use clear, concise language, avoid technical jargon, and incorporate visuals, making the information easily digestible.
Regular feedback mechanisms, such as surveys and assessments, allow for continuous improvement of the training materials based on employee feedback.
Employee Handbook Section on New Digital Systems
The employee handbook section dedicated to new digital systems should be clear, concise, and easily navigable. It should provide a high-level overview of each system, its purpose, key features, and how it impacts daily tasks. Each system should have its own dedicated section with step-by-step instructions, screenshots, and FAQs. Contact information for IT support should be readily available.
The handbook should be regularly updated to reflect any changes or upgrades to the systems. Consider incorporating interactive elements, such as embedded videos or links to online tutorials, to enhance engagement and usability. This section should be treated as a living document, regularly reviewed and updated to reflect the evolving digital landscape within the company.
Communication and Collaboration in a Digitally Transformed Workplace
Digital transformation isn’t just about adopting new technologies; it’s about fundamentally changing how people work together. A successful transformation hinges on clear, consistent, and open communication, fostering a positive employee experience and driving adoption of new tools and processes. Without effective communication strategies, even the most innovative technologies can fail to deliver their promised benefits.Transparent and Open Communication Fosters a Positive Employee Experience During Digital TransformationOpen communication is the bedrock of a positive employee experience during any organizational change, especially one as significant as digital transformation.
Employees need to understand the “why” behind the transformation, the expected changes, and how their roles will evolve. Transparency about the challenges and potential setbacks builds trust and reduces anxiety. Regular updates, both formal and informal, keep employees informed and engaged. This can involve town hall meetings, internal newsletters, or even informal Q&A sessions with leadership.
Actively soliciting feedback and addressing concerns demonstrates a commitment to employee well-being and fosters a sense of ownership in the transformation process. For example, a company implementing a new CRM system should proactively communicate the reasons behind the change, the training opportunities available, and how it will ultimately streamline workflows and improve customer service. This proactive approach minimizes resistance and encourages buy-in.Leveraging Digital Collaboration Tools to Enhance Teamwork and CommunicationThe digital workplace offers a plethora of tools designed to enhance teamwork and communication.
These tools can break down geographical barriers, facilitate real-time collaboration, and improve project management. Examples include project management software like Asana or Trello, instant messaging platforms like Slack or Microsoft Teams, and video conferencing tools like Zoom or Google Meet. Effective implementation involves selecting the right tools for specific needs, providing comprehensive training, and establishing clear communication protocols.
For instance, a team working on a cross-functional project might use a project management tool to track tasks, a messaging platform for quick updates, and video conferencing for regular meetings. The key is to ensure that the chosen tools are user-friendly, intuitive, and integrate seamlessly with existing workflows.Potential Communication Challenges During Digital Transformation and Mitigation StrategiesDigital transformation can introduce new communication challenges.
Information overload, lack of face-to-face interaction, and the potential for miscommunication through digital channels are common concerns. To mitigate these challenges, organizations need to establish clear communication guidelines, encourage regular check-ins, and provide training on effective digital communication etiquette. For example, establishing clear protocols for using different communication channels (e.g., email for formal communication, instant messaging for quick updates) can reduce confusion.
Encouraging the use of video conferencing for regular team meetings helps maintain personal connections and reduces misunderstandings. Moreover, organizations should actively monitor communication channels to identify and address any emerging issues promptly. A company might establish a feedback mechanism where employees can report communication issues or suggest improvements.Digital Communication Tools and Their Suitability for Employee Engagement
| Tool | Best Suited For | Pros | Cons |
|---|---|---|---|
| Slack | Instant messaging, team collaboration, quick updates | Real-time communication, file sharing, integrations | Can lead to information overload, requires careful channel management |
| Microsoft Teams | Team collaboration, video conferencing, file sharing, project management | Integrated platform, robust features, wide adoption | Can be complex for new users, requires training |
| Zoom | Video conferencing, webinars, online meetings | Easy to use, reliable, screen sharing capabilities | Can be less suitable for smaller, informal communication |
| Formal communication, announcements, sharing documents | Widely used, reliable, formal record | Can be slow, easily overlooked, less suitable for real-time communication |
Employee Feedback and Continuous Improvement in Digital Transformation
Digital transformation initiatives, while promising increased efficiency and productivity, often face resistance or unexpected challenges. A crucial element for mitigating these issues and ensuring a successful transition is the consistent gathering and analysis of employee feedback. By actively listening to employees’ experiences and incorporating their insights, organizations can refine their digital transformation strategies, improve employee adoption, and ultimately achieve better outcomes.
Ignoring this crucial feedback loop risks alienating employees, hindering progress, and potentially leading to project failure.
A robust feedback mechanism is essential for understanding the impact of digital transformation on the workforce. This involves not only identifying immediate problems but also uncovering latent issues that might emerge later. Regular feedback loops provide a continuous stream of data that can inform adjustments and prevent larger problems from developing.
Seriously, happy employees are the secret sauce to a smooth digital transformation. When your team’s onboard and empowered, change happens faster. That’s why I’ve been diving into the world of streamlined app development, checking out resources like this article on domino app dev the low code and pro code future to see how we can make things easier for everyone.
Ultimately, efficient tools mean happier employees, and happy employees mean a successful digital transformation.
Gathering and Analyzing Employee Feedback
Establishing a structured process for gathering employee feedback is paramount. This process should be multifaceted, utilizing a variety of methods to ensure diverse perspectives are captured. A multi-pronged approach ensures a more comprehensive understanding of employee experiences and perceptions. For example, a combination of surveys, focus groups, and one-on-one interviews can provide a richer data set than relying on a single method.
The data gathered should be analyzed systematically to identify trends, recurring issues, and areas for improvement. This might involve using qualitative data analysis techniques to interpret open-ended responses or quantitative methods to analyze survey data.
Effective Methods for Soliciting Honest and Constructive Feedback
Soliciting honest and constructive feedback requires building a culture of trust and open communication. Employees need to feel safe expressing their concerns without fear of retribution. Anonymity is a powerful tool; anonymous surveys, for instance, can encourage candid feedback on sensitive topics. Furthermore, providing regular opportunities for feedback, such as through pulse surveys or short feedback forms integrated into existing workflows, makes the process less burdensome and more approachable.
Using clear, concise, and unbiased language in feedback requests ensures that employees understand what is being asked of them and feel comfortable responding. For example, instead of asking “What do you think of the new software?”, a more effective question might be: “What are the top three things you find most challenging or frustrating when using the new software?”
Incorporating Employee Feedback into Ongoing Improvement
Once feedback is gathered and analyzed, it’s crucial to act on it. This requires a commitment to transparency and accountability. Communicating the results of the feedback analysis to employees, outlining the actions being taken to address concerns, and demonstrating a clear commitment to improvement builds trust and reinforces the value of employee input. This communication can take various forms, such as town hall meetings, internal newsletters, or dedicated intranet pages.
Regular follow-up communication, demonstrating the impact of employee feedback on improvements, further strengthens this cycle of continuous improvement. For example, if employees highlighted difficulties with a new software interface, the organization could share updates on interface changes made in response to this feedback.
Tracking and Addressing Employee Concerns
A dedicated system for tracking and addressing employee concerns related to new digital technologies is essential. This system could involve a centralized platform (like a dedicated intranet page or a ticketing system) where employees can submit their concerns, track their progress, and receive updates. This system should be accessible, easy to use, and provide clear communication channels. The system should also ensure that concerns are addressed promptly and effectively.
Prioritization of concerns based on their severity and impact is crucial, ensuring that urgent issues receive immediate attention. Regular reporting on the status of resolved and outstanding issues provides transparency and accountability, further fostering trust and engagement.
Leadership’s Role in Shaping Employee Experience During Digital Transformation
Digital transformation isn’t just about technology; it’s about people. Successful implementation hinges on how effectively leadership navigates the change, fostering a positive and supportive employee experience. Without strong leadership, even the most innovative technologies can fail to deliver expected results due to employee resistance, low adoption rates, and decreased productivity.Effective leadership significantly influences employee experience during digital transformation by creating a culture of trust, transparency, and open communication.
This proactive approach reduces anxieties surrounding new technologies and processes, leading to increased employee engagement and a smoother transition. Leaders who champion change and actively address employee concerns build confidence and demonstrate a commitment to their workforce’s well-being. This is crucial because digital transformation often involves learning new skills, adapting to new workflows, and potentially even facing job role changes – all of which can cause stress and uncertainty.
The Importance of Leadership in Championing Technology Adoption and Addressing Employee Anxieties
Leaders must actively champion the adoption of new technologies, not just by mandating their use, but by demonstrating their value and benefits firsthand. This involves actively participating in training sessions, openly discussing the rationale behind the changes, and addressing any concerns employees might have. For example, a CEO visibly using and praising a new project management software will significantly increase employee buy-in compared to simply announcing its mandatory implementation.
Addressing anxieties requires active listening, providing clear and consistent communication, and offering adequate support and resources, such as dedicated training programs and mentorship opportunities. Ignoring or dismissing employee concerns can lead to resentment, resistance, and ultimately, failure of the digital transformation initiative.
Crucial Leadership Qualities for Successful Digital Transformation
Several key leadership qualities are essential for a successful digital transformation while maintaining a positive employee experience. These include:
- Visionary Leadership: Leaders must articulate a clear vision for the transformation, explaining how it will benefit both the organization and its employees. This vision should be communicated consistently and persuasively to maintain momentum and engagement.
- Empathy and Emotional Intelligence: Understanding and addressing the emotional needs of employees during a period of change is paramount. Leaders must actively listen to concerns, validate feelings, and provide reassurance.
- Adaptability and Flexibility: Digital transformation is an iterative process. Leaders must be willing to adjust strategies and plans based on employee feedback and evolving circumstances. Rigidity can lead to resistance and frustration.
- Transparency and Open Communication: Keeping employees informed about the progress of the transformation, addressing their questions and concerns openly and honestly, is crucial for building trust and reducing uncertainty.
- Decisiveness and Accountability: Leaders must make timely decisions and take responsibility for the outcomes of the transformation. Hesitation or a lack of accountability can erode employee confidence.
Actionable Steps for Leaders to Foster a Supportive Environment
To create a supportive and encouraging environment during digital transformation, leaders should take the following steps:
- Invest in comprehensive training and onboarding programs: Provide employees with the necessary skills and knowledge to succeed in the new digital environment. This includes hands-on training, mentorship opportunities, and readily available support resources.
- Establish clear communication channels: Regularly communicate updates, address concerns, and solicit feedback through various channels, such as town hall meetings, email updates, and internal communication platforms.
- Recognize and reward early adopters and champions: Publicly acknowledge and reward employees who embrace the new technologies and assist their colleagues in adapting. This creates a positive feedback loop and encourages others to follow suit.
- Promote a culture of continuous learning and improvement: Encourage employees to embrace change as an opportunity for growth and development. Provide access to ongoing learning resources and support their professional development.
- Create opportunities for collaboration and knowledge sharing: Foster a collaborative environment where employees can share their experiences, best practices, and challenges. This can be achieved through cross-functional teams, knowledge-sharing platforms, and peer-to-peer mentoring.
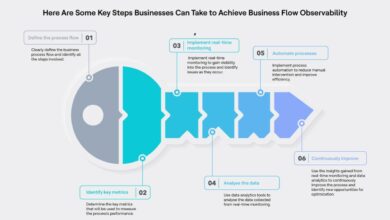
Measuring the Impact of Employee Experience on Digital Transformation Outcomes

Successfully navigating digital transformation hinges not just on technological advancements, but also on how those changes impact the employee experience. Measuring this impact is crucial for optimizing strategies and ensuring a smooth, productive transition. Without quantifiable data, improvements remain speculative, and the full potential of digital transformation may not be realized.
Understanding the correlation between employee experience and digital transformation success requires a multifaceted approach to measurement. This involves tracking key metrics across various aspects of the employee journey, analyzing the data collected, and using the insights gained to refine both employee experience initiatives and digital transformation strategies.
Key Metrics for Measuring Employee Experience Impact
Several key performance indicators (KPIs) can effectively gauge the influence of employee experience on digital transformation outcomes. These metrics provide a holistic view, allowing organizations to identify areas of strength and weakness.
- Employee Satisfaction: Measured through surveys, feedback forms, and pulse checks, satisfaction scores reveal employee sentiment towards the digital transformation process. A decrease in satisfaction could indicate issues with training, communication, or tool usability.
- Employee Net Promoter Score (eNPS): This metric measures employee willingness to recommend their workplace to others. A high eNPS reflects a positive employee experience, suggesting a smoother transition during digital transformation.
- Employee Productivity: Track key productivity metrics such as output per employee, task completion rates, and time spent on specific tasks. Improvements in these metrics post-transformation suggest a positive impact on employee efficiency.
- Employee Engagement: Engagement levels can be assessed through surveys, focus groups, and observation. High engagement indicates a positive work environment and employee buy-in to the digital transformation initiatives.
- Adoption Rate of New Technologies: This metric reflects how quickly and effectively employees embrace new digital tools and processes. A low adoption rate might signify a need for better training or more user-friendly interfaces.
Tracking Employee Satisfaction, Productivity, and Engagement
Tracking these metrics requires a combination of quantitative and qualitative data collection methods. Regular monitoring allows for early identification of potential problems.
- Surveys: Regularly administer surveys to gauge employee satisfaction with new tools, training programs, and overall work experience. Include open-ended questions to gather qualitative feedback.
- Performance Data: Analyze key performance indicators (KPIs) related to productivity, such as sales figures, project completion rates, and customer satisfaction scores. Compare pre- and post-transformation data to identify improvements or areas needing attention.
- Focus Groups: Conduct focus groups to gather in-depth insights into employee perceptions and experiences. These sessions provide valuable qualitative data to supplement quantitative findings.
- Pulse Surveys: Implement short, frequent pulse surveys to monitor employee sentiment in real-time. These quick checks allow for prompt identification and resolution of emerging issues.
Analyzing Data and Identifying Areas for Improvement
Data analysis is crucial for understanding the relationship between employee experience and digital transformation success. This involves identifying trends, correlations, and areas needing improvement.
- Correlation Analysis: Examine the correlation between employee satisfaction scores and productivity metrics. A strong positive correlation suggests that a positive employee experience contributes to increased productivity.
- Regression Analysis: Use regression analysis to determine the impact of specific digital transformation initiatives on employee engagement and satisfaction. This can help prioritize areas for improvement.
- Qualitative Data Analysis: Analyze qualitative data from surveys, focus groups, and interviews to identify recurring themes and underlying issues. This helps to understand the ‘why’ behind the quantitative data.
Visual Representation of Data
Presenting the collected data visually enhances understanding and facilitates decision-making. A simple chart can effectively illustrate the correlation between employee experience and digital transformation outcomes.
| Metric | Pre-Transformation | Post-Transformation | Change |
|---|---|---|---|
| Employee Satisfaction Score | 70 | 85 | +15 |
| Employee Productivity (Units per employee/month) | 100 | 120 | +20 |
| Employee Engagement Score | 65 | 78 | +13 |
| Adoption Rate of New CRM System (%) | 40 | 90 | +50 |
This table demonstrates a hypothetical scenario where improvements in employee experience (higher satisfaction, engagement) are correlated with improved productivity and higher adoption rates of new systems, illustrating a successful digital transformation.
Ultimate Conclusion
Ultimately, successful digital transformation isn’t just about adopting new technology; it’s about empowering your people. By prioritizing employee experience – from initial training and onboarding to ongoing feedback and support – you’ll not only ensure a smoother transition but also unlock the true potential of your digital investments. Remember, happy, engaged employees are the key to unlocking the full benefits of a successful digital transformation, driving innovation, and achieving lasting results.
It’s an investment in your future, and one well worth making.
Query Resolution
What if my employees resist the new technology?
Address resistance proactively through open communication, addressing concerns, and providing ample training and support. Focus on the benefits for them and the company. Sometimes, a phased rollout can ease the transition.
How can I measure the success of my employee experience initiatives during digital transformation?
Track key metrics like employee satisfaction (surveys, feedback sessions), productivity (output, efficiency), and engagement (participation, retention). Look for correlations between these metrics and the success of your digital transformation projects.
What if my budget is limited for employee training?
Prioritize training on the most critical systems and workflows. Utilize free online resources, internal knowledge sharing, and peer-to-peer learning to supplement formal training. Focus on practical, job-relevant skills.
How do I ensure that all employees are included and feel valued during the digital transformation?
Involve employees in the planning and implementation phases. Actively solicit feedback and address concerns. Use inclusive language and ensure accessibility for all employees, regardless of their technical skills or background.