Social Engineering
-
Cybersecurity

Beware of the Cyber Scam Related to Bond Movie No Time to Die
Beware of the cyber scam related to Bond movie No Time to Die! Seriously, those sneaky villains aren’t just on…
Read More » -
Cybersecurity

Difference Between Whale and Spear Phishing
Difference between whale phishing and spear phishing: Ever wondered about the subtle yet significant differences between these two sophisticated cyberattacks?…
Read More » -
Cybersecurity
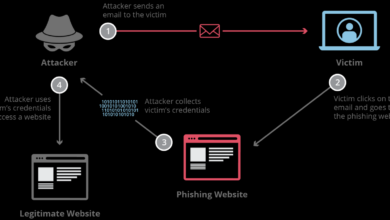
What is Simulated Phishing?
What is simulated phishing? It’s essentially a controlled attack used to test your organization’s security awareness and preparedness. Unlike real…
Read More » -
Cybersecurity
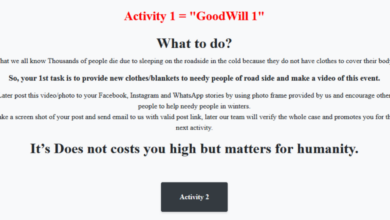
Goodwill Ransomware Victims Donate to the Poor
Goodwill ransomware making victims donate to poor – Goodwill ransomware making victims donate to the poor is a disturbing new…
Read More » -
Cybersecurity

Hackers Can Bypass HTTPS Security Risks Exposed
Hackers can bypass HTTPS, even though it’s designed to secure online communications. This isn’t about a single weakness, but a…
Read More » -
Cybersecurity

How MFA-Based Phishing Campaigns Target Schools
How mfa based phishing campaigns are targeting schools – How MFA-based phishing campaigns are targeting schools is a chilling reality.…
Read More »
