Software Security
-
Cybersecurity

Januarys AppScan Innovation Workshop A Recap
Januarys appscan innovation workshop a recap – January’s AppScan Innovation Workshop: A Recap – Wow, what a whirlwind! This post…
Read More » -
Software Development

Third Party Component Security The Good, The Bad, The Ugly
Third party component security the good the not so good and the downright ugly – Third Party Component Security: The…
Read More » -
Cybersecurity

5 Key Reasons to Invest in Application Security Testing
5 Key Reasons to Invest in Application Security Testing – sounds boring, right? Wrong! In today’s digital world, a single…
Read More » -
Cybersecurity

Theres No AppSec in Baseball Or Is There?
Theres no appsec in baseball or is there – There’s no AppSec in baseball or is there? That’s the question…
Read More » -
Software Development

Bytecode Compiled vs Source Code Scanning
Bytecode compiled vs source code scanning: It’s a debate that often sparks lively discussions among developers and security experts. Both…
Read More » -
Software Development

Achieving Continuous Security Embedding Resilience in Software Development
Achieving continuous security embedding resilience throughout the software development lifecycle is no longer a luxury, but a necessity. In today’s…
Read More » -
Cybersecurity

Safeguarding the Digital Realm Application Security Testings Rise
Safeguarding the digital realm the rising importance of application security testing – Safeguarding the digital realm: the rising importance of…
Read More » -
Software Development

Demystifying PBOM and SBOM Understanding Key Differences
Demystifying pbom and sbom understanding the key differences – Demystifying PBOM and SBOM: Understanding the key differences is crucial in…
Read More » -
Software Development

The Evolving Role of GenAI in Software Development and Application Security
The evolving role of GenAI in software development and application security is rapidly reshaping the tech landscape. No longer a…
Read More » -
Software Development
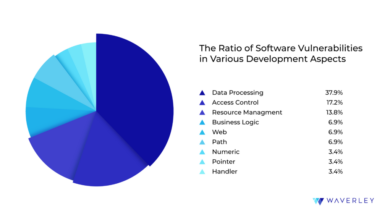
The Hidden Cost of Security Fixes for Software Developers
The hidden cost of security fixes for software developers isn’t just about patching vulnerabilities; it’s a silent drain on resources,…
Read More »
