Forging the Path to Continuous Audit Readiness
Forging the path to continuous audit readiness isn’t just about ticking boxes; it’s about fundamentally shifting how organizations approach risk management and compliance. It’s about embracing a proactive, data-driven approach that allows for real-time monitoring, immediate identification of issues, and faster, more effective responses. This journey involves integrating technology, refining processes, and fostering a culture of continuous improvement – a journey we’ll explore in detail.
This post will delve into the core components of continuous audit readiness, outlining a practical implementation plan, highlighting the crucial role of data analysis and risk management, and exploring the power of automation and technology. We’ll also discuss the importance of effective communication, robust training programs, and strategies for overcoming common challenges. By the end, you’ll have a clearer understanding of how to build a robust and sustainable continuous audit program for your organization.
Defining Continuous Audit Readiness
Continuous audit readiness isn’t just about being prepared for a single, annual audit; it’s about embedding auditability into the very fabric of your organization’s operations. It’s a proactive, ongoing process that ensures your organization consistently meets regulatory and internal control requirements. This approach moves away from the traditional, reactive model of audits, offering significant advantages in efficiency and risk management.Continuous audit readiness involves a fundamental shift in mindset, from viewing audits as a periodic disruption to embracing them as an integral part of daily business.
This means proactively managing risks, implementing robust internal controls, and maintaining comprehensive documentation throughout the year. The goal isn’t just to pass an audit, but to demonstrate a consistent commitment to sound governance and operational excellence.
Core Components of Continuous Audit Readiness
Achieving continuous audit readiness relies on several key components working in harmony. These include a robust internal control framework, a culture of compliance, readily available and accurate data, and a proactive approach to risk management. Without a strong foundation in these areas, a truly continuous audit-ready state is difficult, if not impossible, to achieve. Each component supports and reinforces the others, creating a resilient system.
Benefits of Continuous Audit Readiness
The advantages of embracing continuous audit readiness extend beyond simply passing audits. Organizations benefit from improved risk management, reduced audit costs, enhanced operational efficiency, and a strengthened corporate reputation. The proactive approach allows for the identification and mitigation of potential issues before they escalate into significant problems, saving time, resources, and reputational damage. Furthermore, a culture of continuous improvement fostered by this approach can lead to overall better operational effectiveness.
Continuous Audit Readiness vs. Traditional Audit Approaches
Traditional audit approaches typically involve periodic, intensive reviews conducted by external auditors. This often leads to a flurry of activity in the weeks leading up to the audit, creating stress and potentially overlooking crucial details. Continuous audit readiness, on the other hand, involves a consistent monitoring and improvement process. Instead of a single, high-pressure event, audit readiness is an ongoing concern, allowing for a more efficient and less disruptive process.
The focus shifts from reacting to audits to proactively managing risks and maintaining a consistently audit-ready state.
Key Performance Indicators (KPIs) for Continuous Audit Readiness
Measuring continuous audit readiness requires a focus on specific KPIs. These metrics provide quantifiable insights into the effectiveness of your internal controls and your overall preparedness. Examples include the frequency of internal control failures, the time taken to remediate control deficiencies, the accuracy and completeness of audit trails, and the level of employee compliance with internal policies and procedures.
Regular monitoring of these KPIs allows for the identification of areas for improvement and demonstrates the ongoing commitment to audit readiness. For example, a high frequency of internal control failures would indicate a need for improved training or a review of existing controls. Similarly, a long remediation time suggests inefficiencies in the process.
Implementing a Continuous Audit Program
Building a continuous audit program isn’t a switch you flip; it’s a journey requiring careful planning and execution. Success hinges on a phased approach, seamless integration with existing processes, and leveraging the power of technology. This section details a practical strategy for implementing a robust continuous audit program.
Phased Implementation Plan
A phased approach minimizes disruption and allows for iterative improvements. Starting with a pilot program focusing on a specific, manageable area helps build expertise and refine processes before scaling. Subsequent phases can then incorporate more complex areas and expand the scope of the program. A typical phased implementation might look like this:
- Phase 1: Assessment and Planning: This initial phase involves identifying key risks, selecting a pilot area, defining key performance indicators (KPIs), and selecting appropriate technology. A thorough risk assessment is crucial to prioritize areas needing immediate attention.
- Phase 2: Pilot Program Implementation: This phase focuses on implementing continuous auditing within the chosen pilot area. This allows for testing and refining processes before wider deployment. Regular monitoring and feedback are essential during this phase.
- Phase 3: Expansion and Optimization: Once the pilot program is successful, the continuous audit program can be expanded to other areas. This phase involves refining processes, integrating with other systems, and optimizing the use of technology.
- Phase 4: Ongoing Monitoring and Improvement: Continuous improvement is key. This phase involves regular reviews, updates to processes, and adaptation to changing business needs and regulatory requirements.
Integrating Continuous Auditing into Existing Workflows
Successful integration requires careful consideration of existing systems and processes. This involves training staff, establishing clear communication channels, and automating tasks wherever possible. Resistance to change is a common hurdle; clear communication of the benefits and addressing concerns proactively are crucial. For example, integrating continuous monitoring tools directly into existing ERP systems allows for real-time data analysis and anomaly detection without requiring significant workflow alterations.
The Role of Technology in Enabling Continuous Audit Readiness
Technology is the backbone of a successful continuous audit program. Data analytics tools, robotic process automation (RPA), and continuous monitoring software are essential for automating tasks, analyzing large datasets, and identifying anomalies in real-time. Cloud-based solutions offer scalability and accessibility, allowing for remote monitoring and collaboration. For instance, using data analytics tools to identify unusual patterns in transaction data can significantly reduce the time and effort required for traditional audits.
Checklist for Successful Implementation, Forging the path to continuous audit readiness
Careful planning and execution are critical. This checklist summarizes essential steps:
- Conduct a thorough risk assessment.
- Define clear objectives and KPIs.
- Select appropriate technology and tools.
- Develop a phased implementation plan.
- Train staff on new processes and technologies.
- Establish clear communication channels.
- Integrate continuous auditing into existing workflows.
- Monitor performance and make adjustments as needed.
- Regularly review and update the program.
Data Management and Analysis for Continuous Auditing: Forging The Path To Continuous Audit Readiness
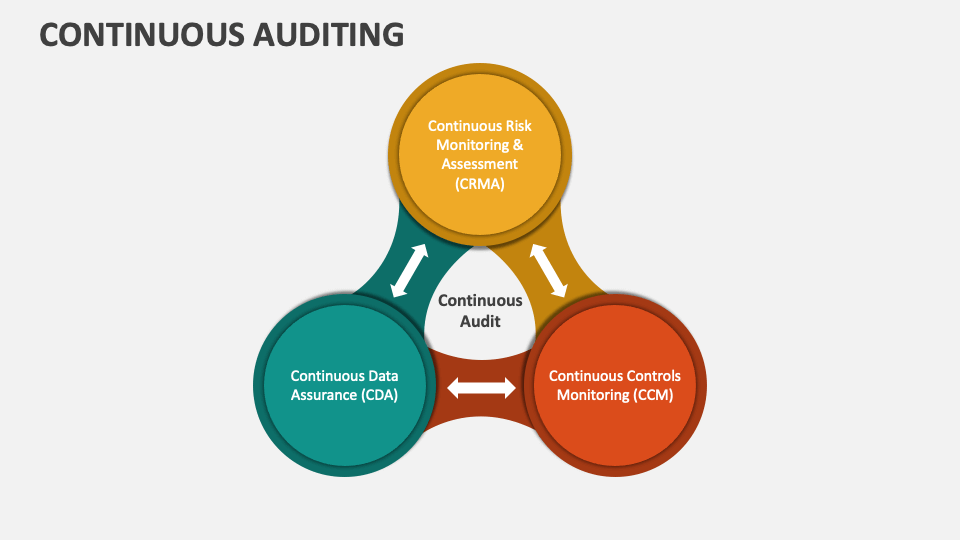
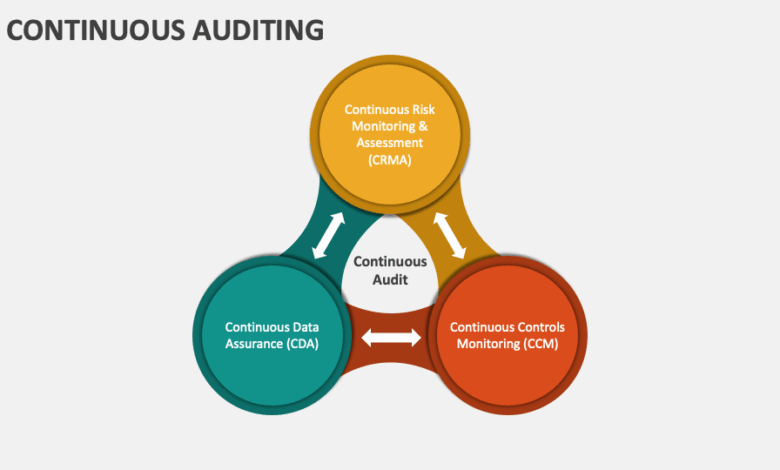
Continuous auditing relies heavily on the effective management and analysis of data. This involves establishing robust processes for data collection, storage, and analysis, all performed in a way that allows for real-time insights into the organization’s financial and operational activities. The goal is to identify and address potential risks and control failures promptly, minimizing their impact.Real-time data collection, storage, and analysis are crucial for continuous auditing.
This requires a shift from traditional, periodic audits to a more dynamic approach. Efficient data management systems are essential for this transformation.
Real-time Data Collection Strategies
Effective real-time data collection requires integrating diverse data sources. This can include transactional data from ERP systems, CRM data, operational data from various departments, and even external data sources like market data or regulatory information. The challenge lies in establishing seamless data flows and ensuring data consistency across these different systems. This often involves using ETL (Extract, Transform, Load) processes and data integration tools to consolidate data into a central repository.
Careful planning and consideration of data governance are critical for success. Real-time data streams, such as those from point-of-sale systems or network activity monitors, can provide immediate insights into operational processes and potential risks.
Potential Data Sources and Integration Challenges
A wide array of data sources can be leveraged for continuous auditing. These include:
- Enterprise Resource Planning (ERP) Systems: These systems provide a comprehensive view of financial transactions, inventory levels, and other key operational data. Integration challenges can arise from data silos within the ERP system itself or from difficulties in extracting data in a timely and reliable manner.
- Customer Relationship Management (CRM) Systems: CRM systems contain valuable information about customer interactions and sales processes, which can be relevant for revenue recognition audits and fraud detection. Integration may require mapping CRM data fields to relevant audit criteria.
- Operational Databases: These databases store data from various operational processes, offering insights into efficiency, compliance, and risk. Integrating these data sources can be challenging due to data inconsistencies and variations in data formats.
- External Data Sources: External data, such as market trends or regulatory changes, can provide context for internal data and improve the accuracy of risk assessments. Accessing and integrating external data often requires specialized tools and expertise.
Data Analysis Techniques in Continuous Auditing
Different data analysis techniques are employed in continuous auditing, each with its own strengths and weaknesses.
| Technique | Description | Advantages | Disadvantages |
|---|---|---|---|
| Descriptive Analytics | Summarizes historical data to understand past performance and identify trends. | Easy to understand and implement; provides a baseline for further analysis. | Limited predictive power; does not identify root causes. |
| Diagnostic Analytics | Investigates the reasons behind observed trends and anomalies. | Helps identify root causes of issues; facilitates targeted interventions. | Can be time-consuming; requires expertise in data interpretation. |
| Predictive Analytics | Uses historical data and statistical models to forecast future outcomes. | Enables proactive risk management; allows for early detection of potential issues. | Accuracy depends on data quality and model assumptions; may require specialized skills. |
| Prescriptive Analytics | Recommends actions to optimize outcomes based on predictions and simulations. | Supports data-driven decision-making; improves efficiency and effectiveness. | Requires sophisticated analytical techniques and modeling; may be complex to implement. |
Data Visualization for Enhanced Understanding
Data visualization plays a critical role in making audit findings more accessible and understandable. Instead of presenting large volumes of raw data, visualizations such as dashboards, charts, and graphs can effectively communicate key insights. For instance, a heatmap could highlight areas of high risk, while a line chart could illustrate trends in key performance indicators (KPIs) over time.
Interactive dashboards allow auditors to drill down into specific areas of interest, facilitating a deeper understanding of the underlying data. Effective visualizations transform complex data into easily digestible information, enabling stakeholders to quickly grasp the audit findings and take appropriate actions.
Risk Management and Continuous Monitoring
Continuous auditing isn’t just about finding problems after they’ve occurred; it’s about proactively identifying and mitigating risks before they escalate into significant issues. By constantly monitoring key data and processes, organizations gain a real-time understanding of their operational landscape and can respond swiftly to emerging threats. This proactive approach significantly reduces the impact of potential fraud, errors, and compliance breaches.Continuous auditing provides a dynamic risk assessment capability, constantly updating the risk profile based on real-time data.
This allows for a more agile and effective response to changing business conditions and emerging threats, compared to traditional, periodic audits which often provide a snapshot of the past rather than a prediction of the future. This shift from reactive to proactive risk management is a key benefit of implementing a continuous audit program.
Real-time Risk Monitoring Tools and Techniques
Real-time risk monitoring relies on a combination of automated tools and human expertise. Automated tools analyze vast datasets to identify anomalies and deviations from established baselines. These tools can range from simple rule-based systems that flag transactions exceeding pre-defined thresholds to sophisticated machine learning algorithms that can detect subtle patterns indicative of fraudulent activity. Human expertise remains crucial for interpreting the alerts generated by these tools and for conducting deeper investigations where necessary.
For example, a system might flag unusual activity in a specific account, prompting a human auditor to review the transactions and supporting documentation to determine whether the activity is legitimate or requires further action.
Critical Risk Escalation Procedures
A well-defined escalation procedure is essential for ensuring that critical risks are addressed promptly and effectively. This procedure should clearly Artikel the roles and responsibilities of different individuals and teams, as well as the communication channels to be used. A typical escalation path might involve reporting the risk to a supervisor, who then escalates it to a risk management committee or senior management if the risk is significant enough.
The escalation process should also include a mechanism for documenting the risk, the actions taken to mitigate it, and the outcome. For example, a system detecting a significant increase in unauthorized access attempts might trigger an immediate alert to the IT security team, who would then investigate the cause and implement appropriate security measures. This immediate response prevents a potential security breach.
Risk Assessment and Response Process Flowchart
The following describes a flowchart illustrating the risk assessment and response process in a continuous audit environment. Imagine a flowchart with distinct boxes and arrows.The process begins with Data Collection and Monitoring: Real-time data feeds from various systems are collected and continuously monitored using automated tools. This data is then analyzed to identify potential risks. This leads to Risk Identification and Assessment: Anomalies and deviations are identified, and their potential impact and likelihood are assessed using pre-defined risk scoring models.
The next step is Risk Prioritization: Risks are prioritized based on their severity and urgency, with the most critical risks addressed first. Then comes Risk Response Planning: Appropriate mitigation strategies are developed and implemented. This is followed by Implementation and Monitoring: The chosen mitigation strategies are implemented, and their effectiveness is continuously monitored. Finally, Reporting and Review: Regular reports are generated on the status of risks and the effectiveness of mitigation strategies, allowing for continuous improvement of the risk management process.
The entire process is cyclical, constantly looping back to data collection and monitoring to maintain a dynamic risk profile.
Automation and Technology in Continuous Auditing

Continuous auditing, with its focus on real-time monitoring and analysis, heavily relies on automation and technology to achieve its goals. Manual processes simply can’t keep pace with the volume and velocity of data generated in modern organizations. Automation streamlines the audit process, improves efficiency, and enhances the overall quality of audit findings.The integration of technology into the audit function is no longer a luxury but a necessity for organizations striving for effective internal control and risk management.
This section explores the role of automation, showcases examples of relevant tools, compares different automation approaches, and proposes a framework for selecting the right technology for your specific needs.
Software Tools and Technologies for Continuous Auditing
A wide range of software tools and technologies support continuous auditing. These tools can be broadly categorized into those focused on data extraction, data analysis, and reporting. Data extraction tools automate the collection of audit data from various sources, including ERP systems, databases, and cloud platforms. Data analysis tools leverage advanced analytics techniques like machine learning and AI to identify anomalies and potential risks within the extracted data.
Reporting tools provide visualizations and dashboards that allow auditors to monitor key risk indicators and track the effectiveness of controls.Examples include Robotic Process Automation (RPA) tools which automate repetitive tasks such as data entry and reconciliation. Data analytics platforms, such as those offered by Alteryx or Tableau, provide robust capabilities for data visualization and statistical analysis. Specialized continuous auditing software solutions are also available, integrating data extraction, analysis, and reporting functions into a single platform.
Forging the path to continuous audit readiness requires a proactive approach to security. A key element of this is robust cloud security, and understanding how solutions like Bitglass contribute is vital. Check out this insightful article on bitglass and the rise of cloud security posture management to see how it helps build a strong security posture, ultimately simplifying your audit preparation.
This proactive strategy ensures you’re always ready for any audit.
These platforms often include features like workflow management, audit trail tracking, and automated alert generation. Furthermore, cloud-based solutions provide scalability and accessibility, allowing auditors to access data and perform analyses from anywhere.
Advantages and Disadvantages of Automation Solutions
Different automation solutions offer varying advantages and disadvantages. For instance, RPA excels at automating repetitive, rule-based tasks, improving efficiency and reducing manual effort. However, it may struggle with tasks requiring complex decision-making or significant human judgment. Data analytics platforms, on the other hand, are powerful tools for identifying patterns and anomalies in large datasets, but they require specialized skills to implement and interpret the results.
Finally, integrated continuous auditing platforms offer a comprehensive solution but can be expensive and require significant upfront investment in implementation and training.
| Automation Solution | Advantages | Disadvantages |
|---|---|---|
| Robotic Process Automation (RPA) | Increased efficiency, reduced manual effort, improved accuracy | Limited flexibility, struggles with complex tasks, requires initial setup and maintenance |
| Data Analytics Platforms | Powerful data analysis capabilities, identification of anomalies and patterns | Requires specialized skills, can be complex to implement, may require significant data preparation |
| Integrated Continuous Auditing Platforms | Comprehensive solution, streamlined workflow, automated alerts | High cost, significant implementation effort, requires specialized training |
Framework for Selecting Automation Tools
Selecting the appropriate automation tools requires a careful assessment of organizational needs and resources. A structured framework can guide this process. First, identify key audit objectives and the data required to achieve them. Next, evaluate the available automation solutions based on their capabilities, cost, and ease of integration with existing systems. Consider the skills and expertise available within the audit team and the need for training.
Finally, develop a phased implementation plan, starting with a pilot project to test and refine the chosen solution before scaling it across the organization.
A successful implementation of automation in continuous auditing requires a clear understanding of organizational needs, a well-defined selection process, and a phased implementation approach.
Forging the path to continuous audit readiness requires proactive security measures. This is especially crucial given recent news, like the concerning report on facebook asking bank account info and card transactions of users , highlighting the need for robust data protection. Strengthening your security posture is key to not only meeting audit requirements but also protecting your users’ sensitive information.
Continuous monitoring and improvement are essential for maintaining this readiness.
Communication and Reporting in Continuous Auditing
Effective communication is the cornerstone of a successful continuous audit program. Without clear, timely, and relevant reporting, the insights gained from continuous monitoring are useless. Stakeholders need to understand the risks identified, the mitigating controls in place, and the overall health of the organization’s processes. This section focuses on strategies for delivering this information effectively.Real-time communication of audit findings is crucial for enabling prompt corrective action.
Delayed reporting can exacerbate issues and increase potential losses. This necessitates a robust communication infrastructure and a clearly defined process for disseminating information.
Real-time Communication of Audit Findings
Effective real-time communication requires a multi-faceted approach. Firstly, it’s essential to identify key stakeholders and their preferred communication channels. This might include email alerts for critical findings, dashboards providing a real-time overview of key metrics, or regular briefings for senior management. Secondly, the information needs to be presented clearly and concisely, focusing on the most critical aspects.
Finally, a feedback loop should be established to ensure stakeholders understand the information and can provide input. For example, a sudden spike in failed login attempts might trigger an immediate alert to the IT security team, allowing them to investigate and prevent a potential breach before significant damage occurs.
Reporting Formats for Continuous Auditing
Several reporting formats are suitable for continuous auditing, each with its own strengths and weaknesses. Dashboards provide a visual overview of key metrics and trends, enabling quick identification of potential issues. Automated reports can be scheduled to deliver regular updates on specific areas of interest. Exception reports highlight deviations from established thresholds or benchmarks, drawing attention to areas requiring immediate attention.
Forging the path to continuous audit readiness requires a robust and adaptable system. Streamlining development processes is key, and that’s where exploring options like domino app dev, the low-code and pro-code future , becomes incredibly relevant. Leveraging these modern approaches can significantly improve transparency and traceability, making the audit process smoother and less stressful in the long run.
Ultimately, this proactive approach to development directly supports a more audit-ready environment.
Narrative reports provide a more in-depth analysis of specific findings, offering context and recommendations. The choice of format depends on the audience, the type of information being communicated, and the desired level of detail.
Managing Stakeholder Expectations and Addressing Concerns
Proactive communication is key to managing stakeholder expectations. Regular updates, even if no significant issues are identified, help maintain transparency and build trust. A well-defined communication plan should Artikel the frequency, format, and content of reports. When concerns arise, it’s crucial to address them promptly and transparently, providing clear explanations and offering solutions. Establishing a formal process for feedback and issue resolution can help build confidence and foster collaboration.
For example, a regularly scheduled meeting with key stakeholders to review the continuous audit dashboard and discuss any emerging concerns can effectively manage expectations and foster collaborative problem-solving.
Sample Communication Plan for Reporting Continuous Audit Results
A sample communication plan might include:
| Frequency | Report Type | Audience | Communication Channel | Content |
|---|---|---|---|---|
| Daily | Dashboard Update | Audit Team, IT Security | Email, Dashboard | Key metrics, alerts, exceptions |
| Weekly | Automated Report | Management | Summary of key findings, trends | |
| Monthly | Narrative Report | Executive Team, Audit Committee | Meeting, Formal Report | In-depth analysis of significant findings, recommendations |
This plan provides a framework for consistent and timely communication, ensuring stakeholders are informed about the continuous audit’s progress and findings. The specific details can be adjusted based on the organization’s needs and risk profile.
Training and Development for Continuous Audit Readiness
Continuous audit readiness isn’t just about technology; it’s about people. A successful continuous auditing program hinges on a skilled and knowledgeable team capable of leveraging technology and data effectively. This requires a robust training and development strategy focused on building the necessary expertise and fostering a culture of continuous improvement.
The transition to continuous auditing demands a shift in mindset and skillset. It’s no longer enough to simply perform periodic, manual audits. Auditors need to be comfortable working with large datasets, utilizing data analytics tools, and understanding the intricacies of automated systems. Furthermore, a strong understanding of the organization’s business processes and risk profile is crucial for effective continuous monitoring.
Essential Skills and Knowledge for Continuous Audit Professionals
Continuous audit professionals require a blend of technical and soft skills. Technical skills include proficiency in data analytics tools (e.g., SQL, Python, R), experience with data visualization software (e.g., Tableau, Power BI), and a strong understanding of database management systems. Soft skills are equally important, encompassing strong communication, problem-solving, and critical thinking abilities. Professionals should also possess a deep understanding of auditing standards and regulatory compliance.
Furthermore, knowledge of the organization’s specific business processes and risk profile is paramount for effective continuous monitoring. For example, an auditor working for a financial institution needs a deep understanding of financial regulations and internal controls, while an auditor in a manufacturing company needs to be familiar with production processes and supply chain management.
Designing a Training Program for Continuous Auditing
A comprehensive training program should incorporate various learning methods to cater to different learning styles. This could include online courses, workshops, on-the-job training, and mentoring programs. The program should be modular, allowing for flexibility and customization based on individual roles and responsibilities. For instance, a module on data analytics could cover basic SQL queries, data visualization techniques, and the application of statistical methods in audit analysis.
Another module could focus on risk management, covering risk assessment methodologies, key risk indicators (KRIs), and the development of continuous monitoring plans. Finally, a dedicated module on the organization’s specific business processes and control environment would ensure practical application of the learned skills. Regular assessments and feedback mechanisms are vital to ensure the effectiveness of the training.
Fostering a Culture of Continuous Audit Readiness
Creating a culture of continuous audit readiness requires a top-down approach. Leadership must champion the initiative, demonstrating a commitment to continuous improvement and providing the necessary resources. This includes allocating sufficient budget for training, technology, and personnel. Open communication is key; regular updates and feedback sessions should keep the team informed and engaged. Furthermore, creating a collaborative environment where knowledge sharing and best practices are encouraged is essential.
Incentivizing continuous learning and recognizing achievements can further reinforce this culture. For example, offering professional development stipends or sponsoring attendance at relevant conferences can demonstrate a commitment to employee growth and enhance motivation.
Ongoing Professional Development in Continuous Auditing
The field of continuous auditing is constantly evolving, with new technologies and methodologies emerging regularly. Therefore, ongoing professional development is crucial to maintain competence and stay abreast of the latest advancements. This can be achieved through participation in professional organizations (e.g., ISACA, IIA), attending conferences and webinars, and pursuing relevant certifications. Regular updates on relevant regulations and industry best practices should also be incorporated into the ongoing professional development plan.
For example, continuous learning might involve attending workshops on the latest developments in artificial intelligence (AI) and its application in auditing or engaging in self-directed learning through online courses on advanced data analytics techniques. This continuous learning ensures that the audit team is equipped to address emerging risks and leverage the latest technologies to enhance the effectiveness and efficiency of the continuous audit process.
Challenges and Mitigation Strategies
Implementing and maintaining continuous audit readiness isn’t a simple switch-flip. It requires a significant cultural shift within an organization, demanding buy-in from all levels, from the C-suite to individual employees. Overcoming the inherent challenges requires a proactive and strategic approach, focusing on both technological and human aspects of the process. Successful implementation hinges on careful planning, resource allocation, and a commitment to continuous improvement.The transition to continuous auditing presents a variety of obstacles, ranging from resistance to change to technological limitations.
Addressing these challenges effectively requires a multifaceted strategy that combines robust planning, technological investment, and a strong focus on employee training and engagement. Ignoring these hurdles can lead to project failure and a missed opportunity to leverage the benefits of continuous audit readiness.
Resistance to Change and Cultural Barriers
Implementing continuous auditing often faces resistance from employees accustomed to traditional audit methods. This resistance can stem from a lack of understanding of the new processes, concerns about increased workload, or even fear of job displacement due to automation. Addressing this requires a comprehensive communication strategy, emphasizing the benefits of continuous auditing, such as improved risk management and reduced audit fatigue.
Training programs should focus not only on the technical aspects but also on the broader benefits and how the new processes will improve their work. Successful change management requires demonstrating the value proposition clearly and involving employees in the implementation process. For example, early adopters can be showcased as success stories to inspire others.
Data Management and Integration Challenges
Continuous auditing relies heavily on the availability and quality of data from various sources across the organization. Integrating data from disparate systems can be complex and time-consuming, requiring significant technical expertise and investment in data integration tools. Data quality is paramount; inaccurate or incomplete data can lead to flawed audit conclusions. Effective data governance policies, robust data cleansing procedures, and the use of data quality monitoring tools are crucial.
For instance, a company might initially focus on integrating data from its core financial systems before expanding to other departments, gradually building a comprehensive data ecosystem.
Technological Limitations and Scalability
The success of continuous auditing is heavily dependent on the availability of appropriate technology. Organizations may lack the necessary infrastructure, software, or skilled personnel to implement and maintain a continuous audit program. Furthermore, scaling a continuous audit program to encompass the entire organization can be challenging, requiring careful planning and phased implementation. A phased approach, starting with a pilot program in a specific area, can help to identify and address challenges before scaling up.
For example, a company could start by automating the audit of a specific high-risk process before expanding to other areas.
Lack of Skilled Personnel and Training
Continuous auditing requires a workforce with the necessary skills and expertise in data analytics, audit technology, and risk management. Finding and retaining skilled personnel can be challenging, especially in a competitive job market. Investing in training and development programs is crucial to equip existing staff with the necessary skills and to attract new talent. This might include partnerships with universities, professional development courses, and internal training programs.
A successful program might include certifications in data analytics and audit technologies, creating a pathway for career advancement within the audit department.
Mitigation Strategies for Common Continuous Auditing Challenges
- Address Resistance to Change: Implement a comprehensive communication plan, provide thorough training, and actively involve employees in the implementation process. Show tangible benefits and address concerns proactively.
- Improve Data Management: Establish clear data governance policies, invest in data integration tools, and implement robust data quality monitoring processes. Prioritize data cleansing and validation.
- Enhance Technological Capabilities: Invest in appropriate technology, including data analytics platforms, automation tools, and cybersecurity solutions. Develop a phased implementation plan to manage scalability.
- Develop Skilled Personnel: Invest in training and development programs, recruit skilled professionals, and create career development paths within the audit function.
- Establish Clear Metrics and Reporting: Define key performance indicators (KPIs) to measure the effectiveness of the continuous audit program and communicate progress regularly to stakeholders.
- Foster Collaboration and Communication: Encourage open communication between the audit team, management, and other stakeholders. Establish regular meetings and reporting mechanisms.
Final Thoughts
Embracing continuous audit readiness isn’t simply a compliance exercise; it’s a strategic advantage. By proactively managing risk, leveraging data-driven insights, and fostering a culture of accountability, organizations can enhance operational efficiency, strengthen their internal controls, and build greater trust with stakeholders. The journey may require investment and effort, but the rewards—in terms of reduced risk, improved efficiency, and enhanced reputation—far outweigh the challenges.
So, are you ready to forge your path toward a more resilient and secure future?
Detailed FAQs
What is the difference between continuous auditing and traditional audits?
Traditional audits are periodic, often involving manual processes and retrospective analysis. Continuous auditing, conversely, leverages technology to monitor processes and data in real-time, enabling proactive risk identification and mitigation.
What are the key challenges in implementing continuous auditing?
Challenges include data integration complexities, the need for significant upfront investment in technology and training, resistance to change within the organization, and ensuring data security and privacy.
How can I measure the effectiveness of my continuous audit program?
Key Performance Indicators (KPIs) include the number of risks identified and mitigated, the time taken to address identified issues, the accuracy of real-time data, and overall cost savings achieved through proactive risk management.
What types of technology are commonly used in continuous auditing?
Common technologies include data analytics platforms, robotic process automation (RPA) tools, continuous monitoring software, and data visualization dashboards.