Threat Intelligence
-
Cybersecurity
Backdoor for Malware 2 A Deep Dive
Backdoor for Malware 2 isn’t just a catchy title; it’s a chilling reality. We’re diving deep into the shadowy world…
Read More » -
Technology
Amazon, IBM, and Cloudflare Unite Against Cyber Threats
Amazon ibm and cloudflare joining alliance to thwart cyber threats – Amazon, IBM, and Cloudflare joining alliance to thwart cyber…
Read More » -
Cybersecurity

AlphaMountain Launches ThreatYeti New Cyber Threat Analysis Platform
AlphaMountain has launched a new cyber threat analysis platform called ThreatYeti, and it’s seriously shaking up the cybersecurity world! Imagine…
Read More » -
Cybersecurity

Alerts, Events, Incidents Where Should Your Security Team Focus?
Alerts events incidents where should your security team focus – Alerts, events, incidents: where should your security team focus? It’s…
Read More » -
Cybersecurity

A Reactive Cybersecurity Strategy Is No Strategy At All
A reactive cybersecurity strategy is no strategy at all. Think of it like this: would you wait until your house…
Read More » -
Cybersecurity

The Evolution of AI in Cybersecurity
The evolution of AI in cybersecurity is a fascinating journey, from the rudimentary expert systems of the early days to…
Read More » -
Cybersecurity
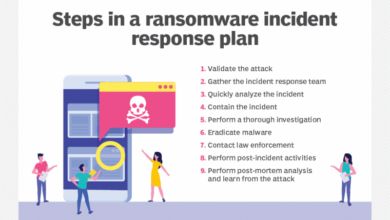
Harnessing AI to Thwart Ransomware Threats A Strategic Approach
Harnessing ai to thwart ransomware threats a strategic approach – Harnessing AI to thwart ransomware threats: a strategic approach. That’s…
Read More » -
Cybersecurity
Transforming SOC Operations Tacitred Threat Intel Boosts Efficiency
Transforming SOC operations how tacitred curated threat intelligence boosts analyst efficiency and delivers tactical attack surface intelligence is no longer…
Read More » -
Cybersecurity
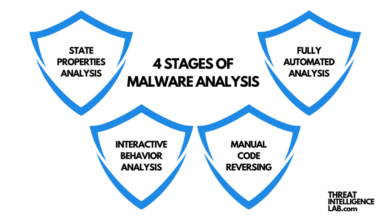
How to Analyze Malware in 5 Steps
How to analyze malware in 5 steps? It sounds daunting, right? But fear not, fellow digital sleuths! Uncovering the secrets…
Read More » -
Cybersecurity

The Underestimated Cyber Threat Anticipating & Combating Supply Chain Attacks
The underestimated cyber threat anticipating and combatting supply chain attacks – The Underestimated Cyber Threat: Anticipating & Combating Supply Chain…
Read More »
