The Complete List of Phishing Attacks Definitions & Prevention
The complete list of types of phishing attacks their brief definitions and how to prevent them – Kicking off with “The Complete List of Phishing Attacks: Their Brief Definitions and How to Prevent Them,” let’s dive into the sneaky world of online scams. Phishing attacks are everywhere, from subtle email traps to elaborate phone schemes. Understanding the different types, how they work, and how to protect yourself is crucial in today’s digital age. This post will arm you with the knowledge to spot and avoid these online predators, keeping your personal information safe.
We’ll explore a wide range of phishing techniques, from the common email scams to more sophisticated attacks like spear phishing and whaling. We’ll break down each type, providing clear definitions, real-world examples, and practical prevention methods. By the end, you’ll have a comprehensive understanding of the threats and a solid strategy to protect yourself and your data.
Introduction to Phishing Attacks
Phishing is a type of cyberattack where malicious actors attempt to trick individuals into revealing sensitive information, such as usernames, passwords, credit card details, or social security numbers. These attacks are typically carried out through deceptive emails, text messages, or websites that mimic legitimate organizations or individuals. The goal is to gain unauthorized access to accounts, steal money, or install malware on the victim’s device.The motivations behind phishing attacks are primarily financial gain and data theft.
Cybercriminals profit directly from stolen financial information or use compromised accounts to conduct further fraudulent activities, such as identity theft or spreading malware. They may also sell stolen data on the dark web, generating significant revenue. In some cases, phishing is used as a means to gain access to a network to launch more sophisticated attacks, like ransomware.
Examples of Real-World Phishing Attacks and Their Impact
Phishing attacks take many forms, and their impact can be devastating. Consider the 2016 Yahoo data breach, where over 3 billion accounts were compromised due to a sophisticated phishing campaign. This resulted in the theft of vast amounts of personal information, including names, email addresses, phone numbers, and even security questions. The financial and reputational damage to Yahoo was substantial, and users faced the risk of identity theft and financial fraud for years afterward.
Another example is the widespread use of spear phishing, which targets specific individuals or organizations with highly personalized emails designed to bypass security filters. A successful spear phishing attack against a company executive could lead to the compromise of sensitive financial data or intellectual property, causing significant financial losses and reputational damage. The impact of these attacks extends beyond financial losses; the emotional distress and inconvenience caused to victims are significant.
The restoration of compromised accounts, the monitoring of credit reports, and the potential need for legal assistance can all add to the burden on individuals and organizations affected by phishing.
Understanding the complete list of types of phishing attacks, their brief definitions, and how to prevent them is crucial for online safety. Building secure applications is equally important, and that’s where advancements like those discussed in this article on domino app dev the low code and pro code future come into play. Ultimately, strong security practices, both online and in application development, are key to protecting ourselves from threats like phishing.
Types of Phishing Attacks
Phishing, in its various forms, presents a significant threat to individuals and organizations alike. Understanding the different types of phishing attacks is crucial for effective prevention and mitigation. This section details several common types, their characteristics, and strategies to protect yourself.
| Phishing Type | Definition | Example | Prevention Method |
|---|---|---|---|
| Spear Phishing | Highly targeted phishing attack focusing on a specific individual or organization, using personalized information to increase credibility. | An email appearing to be from a colleague, requesting sensitive information related to an ongoing project. | Verify sender identity, be cautious of urgent requests, and implement strong email authentication. |
| Whaling | Spear phishing targeting high-profile individuals, such as CEOs or executives, for large financial gains. | An email mimicking a board member, requesting a wire transfer to a fraudulent account. | Employ multi-factor authentication, train executives on security awareness, and implement robust fraud detection systems. |
| Clone Phishing | Phishing attack that duplicates a legitimate email or website to deceive the recipient. | A near-identical copy of a banking website, prompting users to enter their credentials. | Check the URL carefully, look for security indicators (like HTTPS), and be wary of unsolicited emails. |
| Smishing | Phishing attack conducted via SMS text messages. | A text message claiming a package delivery requires immediate payment via a suspicious link. | Be wary of unexpected text messages, never click links from unknown numbers, and report suspicious messages. |
| Vishing | Phishing attack conducted via voice calls (phone). | A phone call pretending to be from a bank’s fraud department, requesting account details. | Be cautious of unsolicited calls, never provide personal information over the phone, and verify caller identity independently. |
Spear Phishing Characteristics
Spear phishing attacks leverage detailed information about their targets to craft highly convincing messages. Attackers often research their victims online, gathering information from social media, company websites, and other public sources. This personalized approach significantly increases the likelihood of success, as the emails or messages appear genuine and trustworthy. The goal is to bypass typical security measures by exploiting the victim’s trust and familiarity with the apparent sender.
Whaling Attack Techniques
Whaling attacks rely on sophisticated techniques to gain access to high-value targets. These include extensive research to personalize the attack, using credible email addresses and mimicking legitimate communication styles. Attackers often exploit the target’s position and authority, creating a sense of urgency or importance to pressure them into action. They may leverage social engineering tactics, building rapport before requesting sensitive information or financial transactions.
Clone Phishing Process
Clone phishing involves creating an almost perfect replica of a legitimate email or website. Attackers obtain a genuine email (often through malware or data breaches) and modify it subtly to include malicious links or attachments. The website cloning technique mirrors the look and feel of a trusted site, often using SSL certificates to mask its malicious nature. Victims, trusting the familiar interface, unwittingly provide their credentials or download malware.
Smishing and Vishing Key Features
Smishing and vishing utilize SMS messages and phone calls, respectively, to deliver phishing attacks. Smishing attacks often involve short, urgent messages with links to fake websites or requests for personal information. Vishing attacks rely on social engineering techniques, impersonating authority figures or using scare tactics to manipulate victims into divulging sensitive data. Both methods leverage the immediacy and personal nature of these communication channels to increase their effectiveness.
Phishing and Pharming Differences
Phishing involves deceiving users into revealing sensitive information directly, typically through fraudulent emails or websites. Pharming, on the other hand, redirects users to fake websites without their knowledge, usually by manipulating DNS settings or installing malicious software. Phishing is an active attack requiring user interaction, while pharming is a passive attack that redirects users automatically.
Baiting Attacks Concept
Baiting attacks use enticing offers or rewards to lure victims into compromising their security. This might involve offering free software, gift cards, or access to exclusive content in exchange for personal information or access to systems. The lure is designed to overcome the victim’s caution and lead them to engage with malicious content.
Quid Pro Quo Phishing Examples
Quid pro quo phishing leverages the principle of reciprocity, offering something in return for information. Examples include surveys promising gift cards upon completion, fake software updates requiring personal details for activation, or fake charity donations requesting banking information. The inherent human tendency to reciprocate is exploited to gain access to sensitive data.
Pretexting Attack Methods
Pretexting attacks involve creating a believable scenario or pretext to justify the request for information. Attackers may impersonate government officials, law enforcement, or technical support personnel to gain the victim’s trust. They often use a combination of social engineering and intimidation to pressure victims into compliance. The pretext is carefully constructed to make the request seem legitimate and urgent.
Watering Hole Attacks Characteristics, The complete list of types of phishing attacks their brief definitions and how to prevent them
Watering hole attacks target specific groups of individuals by compromising websites they frequently visit. Attackers identify a website popular among the target group and inject malicious code. When victims visit the compromised site, they unknowingly download malware or have their credentials stolen. The attack is passive and relies on the victims visiting the infected website.
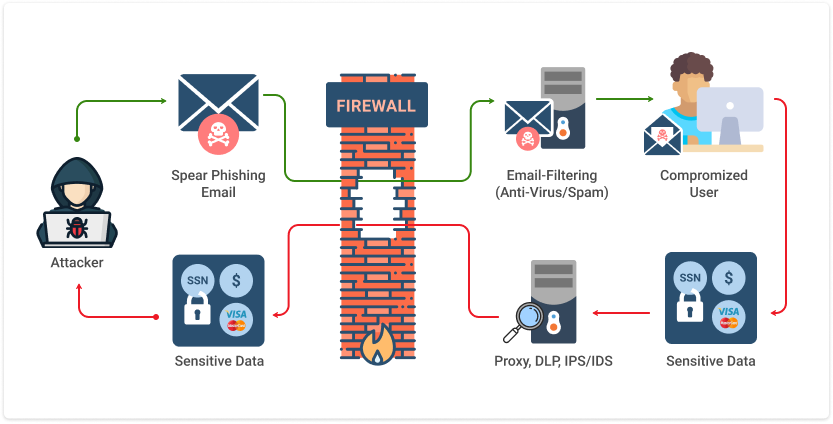
Phishing Attack Vectors

Phishing attacks, while relying on deception, are far from random. They leverage specific pathways and vulnerabilities to reach their targets. Understanding these attack vectors is crucial for effective prevention. This section details the common methods used to deliver phishing attempts and how they exploit weaknesses in our digital infrastructure and human psychology.
The success of a phishing attack hinges on the attacker’s ability to convincingly mimic legitimate entities and exploit vulnerabilities in both technology and human behavior. This involves carefully crafting malicious messages and choosing the right delivery method to maximize the chances of a successful compromise.
Stages of a Phishing Attack
A typical phishing attack follows a predictable sequence of events. Visualizing this process as a flowchart helps understand the attack lifecycle and identify key points for intervention.
Imagine a flowchart with the following stages: 1. Reconnaissance (gathering information on the target); 2. Bait Creation (crafting a convincing phishing email, SMS, or website); 3. Delivery (sending the phishing message via email, SMS, social media, etc.); 4. Interaction (the target clicks the link or opens the attachment); 5. Credential Theft (malware installation or data capture); 6. Exploitation (accessing accounts and systems); 7. Exfiltration (transferring stolen data); 8. Cleanup (covering tracks to avoid detection).
Common Phishing Attack Vectors
Phishing attacks utilize various methods to reach their targets. The choice of vector often depends on the attacker’s goals and the profile of the intended victim.
- Email Phishing (Email Spoofing): This is the most common vector. Attackers forge email addresses and create messages mimicking legitimate organizations (banks, online retailers, etc.).
- SMS Phishing (Smishing): Similar to email phishing, but uses text messages. Often involves urgent requests or threats to pressure the victim into action.
- Social Media Phishing: Attackers create fake profiles or compromise legitimate ones to send phishing messages or links to unsuspecting users. This can involve direct messages, comments, or posts.
- Website Phishing (Pharming): Redirecting users to fake websites that look identical to legitimate sites (e.g., a bank’s login page). This is often achieved through DNS manipulation.
- Voice Phishing (Vishing): Using phone calls to trick victims into revealing sensitive information. Often involves impersonating bank employees or tech support.
Exploiting Vulnerabilities in Email Clients and Web Browsers
Phishing attacks often exploit vulnerabilities in email clients and web browsers to gain access to sensitive information. These vulnerabilities can range from outdated software with known security flaws to user misconfigurations.
For example, some email clients might not adequately display security warnings or might be susceptible to malicious attachments. Similarly, outdated or poorly configured web browsers can be easily tricked into loading malicious code or bypassing security protocols. Attackers can use these vulnerabilities to execute malware or steal credentials directly from the browser’s session.
The Role of Social Engineering in Phishing Campaigns
Social engineering plays a pivotal role in successful phishing attacks. It involves manipulating human psychology to trick victims into divulging sensitive information or performing actions that compromise their security.
Techniques include creating a sense of urgency, fear, or trust. For example, a phishing email might claim that the victim’s account has been compromised and they need to immediately update their credentials. This pressure often overrides the victim’s critical thinking skills, leading them to fall prey to the scam. The effectiveness of social engineering highlights the importance of security awareness training in mitigating the risk of phishing attacks.
Prevention and Mitigation Techniques: The Complete List Of Types Of Phishing Attacks Their Brief Definitions And How To Prevent Them
Protecting yourself from phishing attacks requires a multi-layered approach encompassing individual vigilance, technological safeguards, and organizational awareness. By understanding the common tactics used by phishers and implementing robust preventative measures, you can significantly reduce your risk of falling victim to these scams. This section Artikels key strategies for preventing and mitigating phishing attacks.
Identifying Phishing Emails
Recognizing phishing emails is the first line of defense. Suspicious emails often contain grammatical errors, misspellings, and urgent or threatening language designed to pressure you into immediate action. They may use generic greetings (“Dear Customer”) instead of your name, and the sender’s email address might not match the organization it claims to represent. Look closely at links; hover your mouse over them to see the actual URL before clicking.
Legitimate organizations rarely request personal information via email. If you are unsure about an email’s authenticity, contact the organization directly using a known phone number or website address to verify.
Strong Passwords and Multi-Factor Authentication
Employing strong, unique passwords for each online account is crucial. Strong passwords are long (at least 12 characters), complex (combining uppercase and lowercase letters, numbers, and symbols), and unpredictable. Avoid using easily guessable information like birthdays or pet names. Furthermore, multi-factor authentication (MFA) adds an extra layer of security by requiring a second form of verification, such as a one-time code sent to your phone or email, in addition to your password.
MFA significantly reduces the risk of unauthorized access even if your password is compromised.
Security Awareness Training
Regular security awareness training is vital for individuals and organizations alike. These programs educate users about common phishing tactics, help them identify suspicious emails and websites, and reinforce best practices for online security. Interactive simulations and real-world examples can effectively demonstrate the dangers of phishing and the importance of cautious behavior. Investing in such training is a cost-effective way to significantly improve an organization’s cybersecurity posture.
Anti-Phishing Software and Tools
Numerous anti-phishing software and tools are available to enhance your protection. These tools can scan emails and websites for malicious content, block suspicious links, and warn you about potential phishing attempts. Many reputable antivirus programs include anti-phishing features, while dedicated anti-phishing software provides more comprehensive protection. Examples include email security solutions that use advanced heuristics and machine learning to detect phishing attempts with high accuracy.
Email Filtering and Spam Detection
Implementing robust email filtering and spam detection mechanisms is essential for organizations and individuals. Email filters can identify and block suspicious emails based on various criteria, such as sender address, content, and links. Spam detection mechanisms use algorithms to analyze incoming emails and identify those likely to be spam or phishing attempts. These filters can significantly reduce the number of phishing emails that reach your inbox.
Personal Vulnerability Assessment Checklist
Regularly assessing your vulnerability to phishing attacks is crucial. A simple checklist can help you identify areas for improvement. This checklist should include: Do you use strong, unique passwords for all accounts? Do you regularly update your software? Do you enable MFA where available?
Do you carefully examine emails before clicking links or opening attachments? Do you verify website authenticity before entering personal information? Do you participate in security awareness training?
Verifying Website Authenticity
Before entering any personal information on a website, verify its authenticity. Check the website’s URL for misspellings or unusual characters. Look for a secure connection (HTTPS) indicated by a padlock icon in the address bar. Examine the website’s design and content for inconsistencies or unprofessional aspects. If you are unsure, contact the organization directly using a known phone number or website address to verify the site’s legitimacy.
Reporting Phishing Attempts
Reporting phishing attempts is crucial for helping to combat the spread of these scams. Many organizations, including the Anti-Phishing Working Group (APWG) and the Federal Trade Commission (FTC), provide mechanisms for reporting phishing emails and websites. Forward suspicious emails to your email provider’s abuse reporting address. Reporting these attempts helps law enforcement and security researchers track down and disrupt phishing operations.
Advanced Phishing Techniques
The world of phishing is constantly evolving, leveraging technological advancements to become increasingly sophisticated and harder to detect. While basic phishing tactics remain prevalent, attackers are now employing advanced techniques powered by artificial intelligence, leveraging the power of deepfakes, and utilizing readily available phishing kits to maximize their impact. Understanding these advanced methods is crucial for effective defense.
AI and Machine Learning in Phishing Attacks
AI and machine learning are transforming the phishing landscape, enabling attackers to automate and personalize their campaigns at an unprecedented scale. AI algorithms can analyze vast amounts of data to identify potential victims, craft highly targeted messages, and even dynamically adjust the attack based on the victim’s response. For example, AI can analyze social media profiles to identify personal information, creating highly convincing phishing emails tailored to individual interests and vulnerabilities.
Machine learning models can predict which phishing tactics are most likely to succeed, optimizing the attacker’s efforts and increasing the likelihood of a successful compromise. This automation leads to more efficient and effective phishing campaigns, making detection and prevention more challenging.
Deepfakes in Phishing
Deepfakes, synthetic media generated using artificial intelligence, pose a significant threat in phishing attacks. These highly realistic videos and audio recordings can be used to impersonate trusted individuals, such as CEOs, bank managers, or family members. A deepfake video of a CEO urgently requesting a wire transfer, for example, could easily trick an unsuspecting employee into releasing sensitive financial information.
The realism of deepfakes makes them particularly effective, as victims may find it difficult to distinguish them from genuine content. The increasing accessibility of deepfake creation tools further exacerbates the threat, making it easier for malicious actors to deploy this technique.
Phishing Kits and Their Impact
Phishing kits are pre-built packages of malicious code and templates that simplify the creation and deployment of phishing websites. These kits often include features such as automated email sending, credential harvesting, and payment processing. The availability of these kits on dark web marketplaces lowers the barrier to entry for aspiring phishers, even those with limited technical skills. The impact is significant: it increases the volume and sophistication of phishing attacks, making them harder to track and combat.
Phishing kits often incorporate advanced techniques such as cloaking and redirection to evade detection by security software. The ease of use and readily available features provided by phishing kits contribute to the proliferation of phishing attacks globally.
Emerging Trends in Phishing Attacks
Several emerging trends highlight the ongoing evolution of phishing attacks. One significant trend is the increasing use of social engineering techniques combined with advanced technical methods. Attackers are becoming more adept at building trust and exploiting human psychology alongside sophisticated technological tools. Another notable trend is the shift towards mobile-first phishing attacks, targeting users on their smartphones and tablets through SMS phishing (smishing) and malicious mobile applications.
Furthermore, the use of legitimate platforms and services to launch attacks, such as hijacking cloud storage accounts or creating fake profiles on social media, is becoming more prevalent. These trends underscore the need for continuous vigilance and adaptation in the fight against phishing.
Concluding Remarks
So, there you have it – a comprehensive guide to navigating the treacherous waters of phishing attacks. Remember, staying vigilant is key. By understanding the different types of phishing attacks, implementing strong security practices, and staying informed about emerging threats, you can significantly reduce your risk. Don’t let these digital crooks steal your peace of mind – stay safe online!
FAQ Explained
What is the difference between phishing and pharming?
Phishing involves tricking you into giving up information, while pharming redirects you to a fake website without your knowledge.
How can I report a phishing attempt?
Forward suspicious emails to your provider’s abuse department and report the website to the appropriate authorities (e.g., the FTC in the US).
Are there any free tools to help me identify phishing attempts?
Many email providers offer built-in spam filters and phishing detection. Several free browser extensions also help identify suspicious websites.
What should I do if I think I’ve fallen victim to a phishing attack?
Change your passwords immediately, monitor your accounts for unusual activity, and contact your bank or credit card company if necessary.