Cloud Native Data Security Laminars Future
The future of cloud native data security a look at laminars new capabilities – The future of cloud native data security: a look at Laminar’s new capabilities sets the stage for a fascinating exploration of how we’re bolstering defenses in the ever-evolving cloud landscape. We’ll delve into the critical challenges facing organizations today, examining how the shift to cloud-native architectures has introduced new vulnerabilities. This isn’t just another security product overview; it’s a journey into the innovative solutions Laminar offers to address these threats, and a glimpse into a future where data security is proactive, not reactive.
This post unpacks Laminar’s latest advancements, comparing them to existing solutions and demonstrating how they specifically tackle prevalent threats within Kubernetes, serverless environments, and other cloud-native setups. We’ll walk through practical implementation steps, best practices, and even a hypothetical case study showcasing the real-world impact and ROI. Get ready to explore the cutting edge of cloud security!
Laminar and the Future of Cloud Native Data Security: The Future Of Cloud Native Data Security A Look At Laminars New Capabilities
Laminar is emerging as a significant player in the cloud native security space, focusing on providing comprehensive data protection solutions tailored to the unique challenges of modern, distributed architectures. Its approach differs from traditional security methods by deeply integrating with the cloud native ecosystem, offering real-time visibility and control over data flows. This focus on data-centric security is crucial in an environment where traditional perimeter-based defenses are increasingly ineffective.The cloud native landscape presents a unique set of challenges for data security.
The dynamic nature of microservices, serverless functions, and containerized workloads makes it difficult to maintain a consistent security posture. Data is often scattered across multiple clouds and on-premises environments, making it harder to track and protect. Furthermore, the rapid pace of innovation in cloud native technologies often outpaces the development of security solutions, leaving organizations vulnerable to emerging threats.
The rise of sophisticated attacks targeting cloud-based infrastructure further exacerbates these challenges.
The Evolution and Current State of Cloud Native Security, The future of cloud native data security a look at laminars new capabilities
Cloud native security has evolved significantly from its early days, which largely relied on extending traditional security practices to cloud environments. Initially, security was often treated as an afterthought, with organizations struggling to adapt existing tools and processes to the dynamic nature of cloud native applications. However, as cloud adoption has accelerated, so has the recognition of the need for purpose-built security solutions.
The current state is characterized by a move towards more integrated, automated, and data-centric approaches. This shift is driven by the need to address the inherent complexities of cloud native architectures and the increasing sophistication of cyber threats. We’re seeing a growing emphasis on technologies like service meshes, cloud security posture management (CSPM) tools, and cloud workload protection platforms (CWPPs) to enhance security visibility and control.
However, the integration and orchestration of these diverse tools remain a significant hurdle for many organizations. A key challenge is achieving comprehensive data protection across the entire cloud native ecosystem without sacrificing agility and operational efficiency.
Laminar’s New Capabilities
Laminar has always been at the forefront of cloud-native data security, offering a robust platform for protecting sensitive information in dynamic environments. However, the ever-evolving landscape of cloud technologies and cyber threats necessitates continuous innovation. This section delves into Laminar’s latest advancements, focusing on the enhanced functionalities and their impact on securing cloud-native data. We’ll explore how these new capabilities address current challenges and provide a competitive edge in the market.
Laminar’s core functionality revolves around providing comprehensive data security across the entire cloud-native lifecycle. This includes robust data discovery, classification, and protection mechanisms, all orchestrated through a unified platform. The platform integrates seamlessly with various cloud providers and Kubernetes environments, allowing for consistent security policies regardless of deployment location. Existing features encompass granular access control, automated policy enforcement, and real-time threat detection capabilities.
The new capabilities build upon this foundation, significantly enhancing its power and reach.
Enhanced Data Discovery and Classification
Laminar’s improved data discovery capabilities now leverage advanced machine learning algorithms to identify sensitive data with greater accuracy and speed. This includes the ability to automatically classify data based on context, not just predefined s, significantly reducing false positives and improving overall efficiency. For example, the system can now distinguish between a social security number used in a test database versus one used in a production environment, providing more contextually relevant risk assessments.
The new classification engine supports a broader range of data types and formats, including unstructured data such as images and audio files, significantly improving its comprehensive data coverage.
Automated Remediation and Response
Previously, Laminar offered alerts and notifications upon detecting security breaches or policy violations. The new capabilities automate the remediation process, significantly reducing the time to resolution. This includes automated actions such as quarantining compromised data, revoking access privileges, and initiating incident response workflows. For instance, if a suspicious access attempt is detected, Laminar can automatically block the access and initiate an investigation without human intervention, minimizing potential damage.
This automation reduces the burden on security teams, allowing them to focus on more strategic tasks.
Advanced Threat Detection and Prevention
Laminar’s enhanced threat detection leverages behavioral analytics and anomaly detection to identify sophisticated attacks that might evade traditional signature-based approaches. This includes the ability to detect lateral movement within the cloud environment, identifying threats that might have already bypassed initial security measures. The system employs advanced machine learning to establish baselines of normal activity and promptly flags any deviations, enabling faster threat response.
Furthermore, the integration of threat intelligence feeds provides real-time updates on the latest attack vectors, allowing Laminar to proactively protect against emerging threats.
Comparison with Existing Solutions
The following table compares Laminar’s new capabilities with some leading competitors in the cloud-native data security space.
| Vendor | Feature | Description | Advantages |
|---|---|---|---|
| Laminar | Automated Remediation | Automates the process of fixing security breaches and policy violations. | Reduces response time, minimizes damage, frees up security teams. |
| Competitor A | Automated Remediation | Offers automated alerts but requires manual intervention for remediation. | Provides alerts, but lacks full automation. |
| Laminar | Contextual Data Classification | Classifies data based on context and meaning, not just s. | Reduces false positives, improves accuracy, enhances efficiency. |
| Competitor B | Data Classification | Relies primarily on -based classification. | Simpler to implement but less accurate and prone to false positives. |
| Laminar | Behavioral Analytics | Detects threats by analyzing user and system behavior. | Identifies sophisticated attacks that evade traditional methods. |
| Competitor C | Threat Detection | Primarily uses signature-based detection. | Less effective against zero-day exploits and advanced persistent threats. |
Addressing Specific Security Threats
Laminar’s new capabilities directly target several critical vulnerabilities prevalent in modern cloud-native environments. These enhancements focus on bolstering data security across various deployment models, improving the overall resilience of applications against increasingly sophisticated attacks. By strengthening the core security posture of Kubernetes clusters and serverless functions, Laminar aims to minimize the attack surface and enhance the protection of sensitive data.The primary threats Laminar’s new features are designed to mitigate include unauthorized access to sensitive data, data breaches stemming from misconfigurations, and attacks exploiting vulnerabilities in the underlying infrastructure.
These capabilities are particularly crucial in dynamic environments like Kubernetes, where the ephemeral nature of containers and the complex orchestration processes can create blind spots for traditional security tools. Furthermore, the serverless paradigm, while offering scalability and cost-effectiveness, introduces unique security challenges related to identity management and access control that Laminar’s enhanced features address.
Mitigation of Unauthorized Access
Laminar’s enhanced data encryption and access control mechanisms significantly reduce the risk of unauthorized data access. This involves implementing granular, role-based access control (RBAC) policies, ensuring that only authorized users and services can access specific data sets. Furthermore, Laminar’s advanced encryption capabilities utilize robust algorithms and key management practices to protect data both in transit and at rest, even if an attacker gains unauthorized access to the underlying infrastructure.
For instance, a hypothetical scenario involving a compromised Kubernetes node would still leave data encrypted and inaccessible to the attacker due to Laminar’s encryption at rest and in-transit. The attacker would not be able to decrypt the data even with access to the compromised node because the decryption keys are managed separately and securely by Laminar.
Addressing Misconfigurations in Kubernetes
Kubernetes deployments are often susceptible to misconfigurations that can lead to significant security vulnerabilities. Laminar’s new capabilities include automated policy enforcement and continuous monitoring to detect and rectify such misconfigurations. This proactive approach identifies potential vulnerabilities before they can be exploited, reducing the risk of data breaches. For example, if a Kubernetes pod is configured with overly permissive network policies, Laminar will detect this deviation from the established security baseline and automatically trigger an alert, prompting remediation.
This ensures that only authorized network communication is allowed, preventing lateral movement by malicious actors.
Neutralizing Serverless Function Vulnerabilities
Serverless functions, while offering significant advantages, introduce unique security challenges related to identity and access management. Laminar’s improved identity and access management (IAM) features provide fine-grained control over access to serverless functions, preventing unauthorized invocation and data manipulation. Imagine a scenario where a serverless function processing sensitive customer data is compromised due to a vulnerability in its code.
Laminar’s runtime protection mechanisms would immediately detect the malicious activity and automatically terminate the function, preventing further data compromise. Moreover, Laminar’s integrated logging and monitoring capabilities provide detailed insights into function execution, enabling rapid identification and response to security incidents.
Implementation and Integration
Integrating Laminar’s cloud-native data security solutions into your existing infrastructure is a streamlined process designed for minimal disruption. The approach emphasizes ease of use and rapid deployment, allowing you to quickly enhance your security posture without extensive re-architecting. This section details the integration process and offers best practices for optimal results.Laminar’s integration strategy focuses on leveraging existing infrastructure components and APIs wherever possible.
This minimizes the need for complex configurations and reduces the overall implementation time. The modular design of Laminar’s products allows for a phased approach, starting with critical components and gradually expanding coverage as needed. This flexible approach adapts to various organizational needs and scales effectively with growing data volumes and infrastructure complexity.
Integrating Laminar with Kubernetes
Integrating Laminar into a Kubernetes environment involves deploying the Laminar agent as a sidecar container within your existing pods. This approach provides deep visibility into application behavior and data flows without requiring significant code changes or infrastructure modifications. The following steps Artikel a typical integration scenario:
- Deploy the Laminar Agent: This involves adding a Laminar agent container to your Kubernetes deployment YAML file. The agent configuration is typically specified through environment variables or a configuration map, allowing for easy customization and management. The agent automatically discovers and integrates with existing Kubernetes APIs for seamless data collection and policy enforcement.
- Configure Policies: Using the Laminar management console, define data security policies based on your specific requirements. These policies can specify access controls, data encryption rules, and other security measures tailored to your application’s needs. The console provides an intuitive interface for policy creation and management, simplifying the process and minimizing the learning curve.
- Monitor and Manage: The Laminar console provides a centralized dashboard for monitoring the security posture of your Kubernetes cluster. This dashboard provides real-time insights into data access patterns, security events, and policy compliance. The system generates alerts for potential security violations, allowing for timely remediation and prevention of data breaches.
Best Practices for Maximizing Laminar’s Effectiveness
To fully leverage Laminar’s capabilities and ensure optimal protection, follow these best practices:
- Implement Least Privilege Access: Configure Laminar policies to grant only the minimum necessary access rights to applications and users. This limits the potential impact of a security breach by reducing the scope of compromised data.
- Regular Policy Reviews: Periodically review and update your Laminar policies to reflect changes in your application architecture, data sensitivity, and security requirements. Regular reviews help maintain the effectiveness of your security posture and adapt to evolving threats.
- Integrate with Existing Security Tools: Leverage Laminar’s integration capabilities with other security tools such as SIEM and SOAR platforms. This enables comprehensive security monitoring and incident response, enhancing overall security posture.
- Utilize Automated Remediation: Configure Laminar to automatically remediate identified security vulnerabilities whenever possible. This proactive approach reduces the time to resolution and minimizes the risk of exploitation.
Future Trends and Implications
Laminar’s advancements in cloud native data security represent a significant shift in how we approach protecting sensitive information in dynamic, distributed environments. Its capabilities, particularly in areas like automated policy enforcement and granular access control, are poised to reshape the landscape of cloud security architectures and strategies in the coming years. The implications extend beyond simply improving existing security measures; they suggest a paradigm shift towards proactive, intelligent, and self-healing security systems.The integration of AI and machine learning within Laminar’s platform allows for a level of automation and predictive analysis previously unseen in cloud native security.
This allows security teams to move beyond reactive responses to breaches and instead focus on proactive threat mitigation and prevention. This proactive approach will be crucial as cloud native architectures become increasingly complex and distributed, making traditional security methods less effective. The ability to automatically adapt security policies based on real-time threat intelligence and behavioral analysis is a game-changer, significantly reducing the human error factor and improving overall security posture.
Impact on Future Security Architectures
Laminar’s capabilities are likely to influence future security architectures by promoting a shift towards decentralized, microservices-based security models. Instead of relying on centralized security gateways and firewalls, organizations will increasingly adopt distributed security solutions that integrate directly into their applications and infrastructure. This approach allows for more granular control and reduces the single point of failure inherent in centralized systems.
For example, imagine a future where each microservice within a complex application has its own embedded security layer, managed and monitored by Laminar, ensuring that data remains protected even as the application scales and evolves. This decentralized approach, facilitated by Laminar’s automated policy enforcement, will lead to more resilient and adaptive security architectures.
Potential Future Developments
The rapid evolution of cloud native technologies necessitates continuous innovation in security. Laminar’s future development roadmap likely includes addressing several key areas. One critical area is enhanced support for serverless computing, a rapidly growing segment of the cloud native landscape that presents unique security challenges. Another is the integration of more sophisticated threat detection capabilities, leveraging advanced machine learning techniques to identify and respond to zero-day exploits and sophisticated attacks.
Furthermore, improvements in automated remediation capabilities, enabling the system to automatically respond to security incidents and minimize downtime, will be essential. Finally, enhanced compliance and auditing features will become increasingly important as regulatory requirements around data security continue to evolve. For instance, Laminar could incorporate automated compliance checks for regulations such as GDPR and CCPA, providing organizations with real-time insights into their compliance posture.
Case Study: SecureCloud, a Fintech Startup
SecureCloud, a rapidly growing fintech startup, faced escalating security challenges as it migrated its core banking applications to a Kubernetes-based cloud-native infrastructure. Their existing security tools proved inadequate in managing the dynamic nature of containers and microservices, leading to increased vulnerabilities and operational overhead. They needed a solution that could provide comprehensive data security without impacting application performance or developer agility.
Challenges Faced by SecureCloud
SecureCloud’s primary concerns revolved around data breaches, unauthorized access, and compliance issues. Their legacy security tools struggled to keep pace with the rapid deployment cycles of their cloud-native environment. Specifically, they lacked granular control over data access within their microservices, making it difficult to identify and mitigate threats effectively. Maintaining compliance with stringent financial regulations also presented a significant challenge.
The complexity of their distributed system made it difficult to track data flow and ensure consistent security policies across all components.
Laminar’s Solution Implementation
SecureCloud implemented Laminar’s cloud-native data security platform to address these challenges. Laminar’s fine-grained access control policies allowed SecureCloud to precisely define who could access what data within each microservice. This granular control significantly reduced their attack surface and improved their overall security posture. Laminar’s automated policy enforcement ensured consistent security across their entire infrastructure, simplifying compliance efforts.
The platform’s integration with their existing monitoring tools provided real-time visibility into data access patterns, enabling proactive threat detection and response.
Positive Outcomes and ROI
Following the implementation of Laminar, SecureCloud experienced a significant reduction in security incidents. The granular access control policies minimized the impact of potential breaches, limiting the exposure of sensitive customer data. The automated policy enforcement significantly reduced the operational overhead associated with managing security, freeing up their security team to focus on more strategic initiatives. Moreover, Laminar’s seamless integration with their existing infrastructure minimized disruption to their development and deployment processes.The ROI for SecureCloud was substantial.
By reducing the risk of data breaches and associated fines, they avoided potentially catastrophic financial losses. The reduction in operational overhead and improved developer productivity also contributed significantly to their bottom line. While precise figures are confidential, SecureCloud estimates that the cost savings from reduced security incidents and improved operational efficiency exceeded the cost of implementing Laminar within the first six months.
This, coupled with the enhanced security posture and improved compliance, solidified Laminar as a key component of their infrastructure.
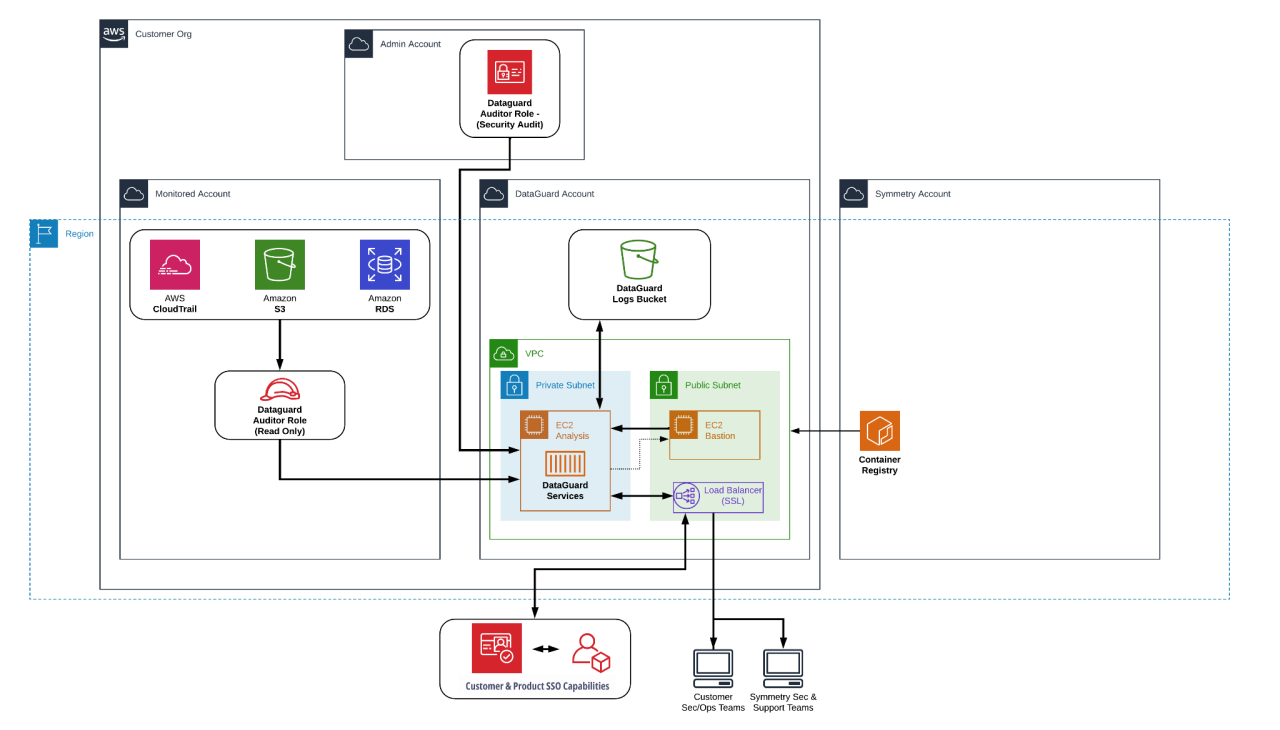
Visual Representation: Data Flow Diagram
Understanding the data flow within a secured cloud-native environment is crucial. This diagram illustrates how Laminar’s security features protect data at various stages, from creation to consumption. It showcases the interaction between different components and highlights the key security mechanisms implemented.The following data flow diagram depicts a simplified yet representative example of data movement within a cloud-native environment secured by Laminar.
Thinking about the future of cloud native data security and Laminar’s exciting new capabilities got me pondering development speed. To build secure, scalable apps quickly, we need efficient development tools, which is why I’ve been exploring the advancements in low-code/pro-code platforms like those discussed in this article on domino app dev the low code and pro code future.
Ultimately, faster development cycles are key to effectively implementing robust security measures like those offered by Laminar in the cloud native space.
It focuses on key aspects of data protection, including encryption and access control.
Data Flow in a Laminar-Secured Environment
Imagine a Fintech application, SecureCloud, processing sensitive customer financial data. The diagram illustrates how data flows through the system, highlighting Laminar’s role in maintaining security at each stage.
Data Source (e.g., SecureCloud Application): This is the origin point of the data, such as a user’s transaction details. Data is initially unencrypted.
Laminar Data Encryption Layer: Before data leaves the application, Laminar encrypts it using a robust encryption algorithm (e.g., AES-256). This ensures data confidentiality during transit and at rest.
Secure Cloud Storage (e.g., AWS S3): The encrypted data is stored in a secure cloud storage service. Laminar integrates with the storage provider to enforce access control policies and further protect the data.
Laminar Access Control Layer: This layer manages user access to the data based on predefined roles and permissions. Only authorized users with the necessary credentials can decrypt and access the data. This is implemented using techniques like role-based access control (RBAC).
Data Processing (e.g., Analytics Engine): When data needs processing, Laminar ensures that it is decrypted only within a secure environment, such as a trusted execution environment (TEE) or a Kubernetes pod with strict network policies. After processing, the data is re-encrypted before being stored back in the secure storage.
Data Consumer (e.g., SecureCloud Application, authorized users): Authorized users or applications can access the data after successful authentication and authorization via Laminar. Laminar ensures that only authorized entities can decrypt and utilize the data.
Data Encryption and Access Control Mechanisms
Laminar employs a multi-layered approach to data security. Data encryption is applied at rest and in transit, using industry-standard algorithms and key management practices. Access control is enforced through RBAC, ensuring that only authorized users and applications can access specific data based on their roles and permissions. This granular control minimizes the risk of unauthorized data access.
Furthermore, Laminar’s integration with various cloud providers allows for leveraging their native security features, creating a robust and layered security posture. For example, Laminar can leverage AWS KMS for key management, enhancing the security of the encryption keys.
Conclusion
Ultimately, Laminar’s new capabilities represent a significant leap forward in cloud native data security. By addressing vulnerabilities proactively and offering seamless integration, they empower organizations to confidently embrace the agility and scalability of cloud-native architectures without compromising security. The future of cloud security is less about patching holes and more about building resilient, adaptive systems – and Laminar is leading the charge.
Stay tuned for even more innovative developments in this rapidly evolving field!
FAQ Section
What are the biggest risks Laminar addresses that other solutions miss?
Laminar excels in addressing the unique challenges posed by dynamic cloud-native environments, like ephemeral infrastructure and microservices. Many existing solutions struggle to keep up with the rapid changes and distributed nature of these systems, leaving gaps in protection. Laminar’s approach provides more comprehensive, real-time visibility and control.
How does Laminar’s pricing model compare to competitors?
Laminar’s pricing is typically usage-based, offering flexibility and scalability to match your cloud environment’s needs. Direct comparisons depend on specific features and usage, but generally, it aims for competitive pricing while delivering superior value through enhanced security and reduced operational overhead.
What level of technical expertise is required for implementation?
While some technical understanding is necessary, Laminar prioritizes ease of integration. Their documentation and support resources are designed to help even teams with limited cloud-native experience get up and running quickly. They also offer professional services for more complex deployments.