
Pentagon Unveils Updated Zero Trust Cybersecurity Strategy
The nature of cybersecurity defense pentagon to reveal updated zero trust cybersecurity strategy guidelines – The Pentagon’s updated zero trust cybersecurity strategy guidelines are finally here, and they’re shaking things up. For years, the traditional perimeter-based security model has felt increasingly inadequate in the face of sophisticated cyber threats. This new strategy represents a fundamental shift, moving away from trusting everything inside the network to verifying every user and device, regardless of location. It’s a massive undertaking, impacting everything from network architecture to data access protocols.
This post dives into the core principles, implementation challenges, and technological innovations driving this critical change.
The shift to a zero trust model isn’t just about adding new technologies; it’s about a complete cultural change within the Department of Defense. This means embracing a more proactive, risk-aware approach to security, constantly verifying identities and permissions. The Pentagon’s implementation plan will likely serve as a blueprint for other large organizations struggling to adapt to the evolving threat landscape, and the implications extend far beyond the military.
The Pentagon’s Zero Trust Strategy: The Nature Of Cybersecurity Defense Pentagon To Reveal Updated Zero Trust Cybersecurity Strategy Guidelines
The Department of Defense (DoD) has unveiled an updated zero trust cybersecurity strategy, marking a significant shift in its approach to securing sensitive information. This strategy moves away from traditional perimeter-based security models, acknowledging the increasingly complex and distributed nature of modern military networks. The core principle is to assume no implicit trust and verify every user, device, and network access request before granting access to resources.
Core Principles of the Pentagon’s Zero Trust Strategy
The updated strategy rests on several fundamental principles. It emphasizes continuous verification of identity, authorization, and device posture, regardless of location or network segment. This contrasts sharply with previous approaches that relied heavily on network perimeters (like firewalls) to protect sensitive data. The shift towards a zero trust architecture is a direct response to the evolving threat landscape, where sophisticated cyberattacks often bypass traditional security measures.
The Pentagon’s adoption of zero trust aligns with industry best practices, but also incorporates unique considerations related to national security and the sensitive nature of the data it handles.
Comparison with Previous Approaches and Industry Best Practices, The nature of cybersecurity defense pentagon to reveal updated zero trust cybersecurity strategy guidelines
Previously, the DoD relied heavily on network-based security, assuming that anything inside the network perimeter was trustworthy. This approach proved vulnerable to insider threats and sophisticated attacks that compromised internal systems. The new zero trust model eliminates this implicit trust, requiring continuous authentication and authorization for every access request. This is in line with industry best practices, where organizations are increasingly adopting zero trust architectures to mitigate the risks associated with cloud adoption, remote work, and increasingly complex IT infrastructures.
However, the Pentagon’s implementation requires a higher level of security and resilience due to the critical nature of its missions and data. The scale and complexity of the DoD’s IT infrastructure also present unique challenges compared to most private sector organizations.
Summary of Core Tenets
| Principle | Description | Implementation | Impact |
|---|---|---|---|
| Least Privilege Access | Users only have access to the minimum resources necessary to perform their jobs. | Role-based access control, granular permissions. | Reduces the impact of compromised accounts. |
| Continuous Verification | Ongoing authentication and authorization of users, devices, and applications. | Multi-factor authentication (MFA), device posture checks, continuous monitoring. | Detects and responds to threats in real-time. |
| Microsegmentation | Dividing the network into smaller, isolated segments to limit the impact of breaches. | Network segmentation technologies, micro-virtualization. | Contains the spread of malware and reduces attack surface. |
| Data-Centric Security | Protecting data regardless of its location, focusing on data classification and access control. | Data loss prevention (DLP) tools, encryption, access control lists. | Ensures data confidentiality, integrity, and availability. |
Implementation Challenges and Solutions

The Pentagon’s ambitious zero trust strategy, while crucial for bolstering cybersecurity, faces significant hurdles in its implementation. Successfully transitioning to a zero trust architecture requires a multifaceted approach addressing technological limitations, organizational inertia, and the need for comprehensive workforce training. Overcoming these challenges is paramount to achieving the strategy’s security goals.
The Department of Defense’s legacy systems present a major obstacle. Many systems are outdated, lack the necessary APIs for integration into a zero trust framework, and are not designed with security principles like least privilege access in mind. Furthermore, the sheer scale and complexity of the DoD’s IT infrastructure, encompassing diverse networks and numerous contractors, significantly complicates the implementation process.
Organizational silos and a lack of standardized processes further hinder effective collaboration and resource allocation necessary for a successful zero trust deployment.
Technological Challenges and Solutions
Addressing the technological challenges necessitates a phased approach. This involves migrating legacy systems to more modern, secure platforms that support zero trust principles. This might involve cloud migration, where possible, leveraging cloud-native security features. Furthermore, robust identity and access management (IAM) solutions are critical, implementing multi-factor authentication (MFA) across all systems and enforcing least privilege access controls.
Investing in advanced threat detection and response capabilities, such as Security Information and Event Management (SIEM) systems and endpoint detection and response (EDR) solutions, is crucial to identify and mitigate security breaches quickly. Finally, micro-segmentation techniques can be employed to isolate different parts of the network, limiting the impact of a potential breach. For example, migrating sensitive data to a separate, highly secure cloud environment and restricting access based on granular policies would significantly reduce the attack surface.
Organizational Challenges and Solutions
Overcoming organizational challenges requires a cultural shift towards a security-first mindset. This involves establishing clear lines of responsibility and accountability for cybersecurity, fostering collaboration between different departments and agencies, and creating a culture of continuous improvement. A centralized cybersecurity team, responsible for overseeing the implementation and management of the zero trust architecture, is essential. This team would develop and enforce security policies, provide technical guidance, and monitor the overall security posture.
Establishing clear communication channels and creating a standardized set of processes will facilitate collaboration and improve efficiency. Furthermore, implementing robust change management processes is crucial to minimize disruptions during the transition to a zero trust environment. For example, a well-defined process for evaluating the security impact of new applications and systems before deployment would help mitigate risks.
The Role of Training and Education
Successful zero trust adoption hinges on a well-trained workforce. Comprehensive training programs should educate personnel on zero trust principles, security best practices, and the specific technologies implemented. This training should cover topics such as secure password management, phishing awareness, and the importance of reporting suspicious activity. Regular security awareness training, including simulated phishing attacks, can help improve user vigilance and reduce the risk of human error.
Furthermore, technical training for IT staff is essential to ensure they possess the necessary skills to manage and maintain the zero trust architecture. For instance, training on advanced threat detection techniques and incident response procedures would improve the organization’s ability to handle security incidents effectively.
Phased Implementation Plan
A phased approach is vital for successful zero trust implementation within a large organization like the Department of Defense. A phased rollout allows for iterative improvements, minimizes disruption, and facilitates continuous monitoring and adaptation.
- Phase 1: Assessment and Planning: Conduct a thorough assessment of the current IT infrastructure, identify critical assets, and develop a detailed implementation plan with clearly defined timelines and milestones. This includes identifying legacy systems and prioritizing their migration or replacement.
- Phase 2: Pilot Program: Implement the zero trust architecture in a limited scope, such as a single department or network segment. This allows for testing and refinement of the strategy before full-scale deployment. This would involve selecting a pilot group and providing them with extensive training on the new security protocols.
- Phase 3: Incremental Rollout: Gradually expand the zero trust architecture to other parts of the organization, ensuring continuous monitoring and adaptation based on lessons learned from the pilot program. This phase might involve migrating specific applications or data sets to a zero-trust environment, prioritizing those with the highest security risks.
- Phase 4: Continuous Monitoring and Improvement: Implement continuous monitoring and threat detection mechanisms to identify and address vulnerabilities. Regularly review and update security policies and procedures to adapt to evolving threats. This includes conducting regular security audits and penetration testing to validate the effectiveness of the zero-trust architecture.
Technological Components of the Zero Trust Framework
The Pentagon’s updated zero trust strategy relies on a robust technological foundation to achieve its security goals. This framework moves away from implicit trust and instead verifies every user and device before granting access to resources, regardless of location. The implementation requires a layered approach, integrating various technologies to ensure comprehensive protection. This section details the key technological components and how they interact.
The effectiveness of the Pentagon’s zero trust strategy hinges on the seamless integration and coordinated operation of multiple security technologies. These technologies work in concert to continuously assess risk, enforce access controls, and monitor activity, providing a multi-layered defense against sophisticated threats.
Identity and Access Management (IAM) Technologies
The foundation of any zero trust architecture is strong identity and access management. This involves rigorously verifying the identity of every user and device attempting to access network resources. Multi-Factor Authentication (MFA) is a crucial component, requiring users to provide multiple forms of authentication (e.g., password, one-time code, biometric scan) before access is granted. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
Privileged Access Management (PAM) solutions further enhance security by controlling and monitoring access for high-privilege accounts, minimizing the impact of potential insider threats. Centralized Identity and Access Management (CIAM) systems provide a single source of truth for user identities and access rights, simplifying administration and improving security posture.
Network Security Technologies
Network segmentation plays a vital role in limiting the impact of breaches. Micro-segmentation divides the network into smaller, isolated segments, limiting the lateral movement of attackers. Software-Defined Perimeter (SDP) technologies create secure tunnels between users and applications, further isolating resources and reducing the attack surface. Secure Web Gateways (SWG) inspect and filter web traffic, preventing access to malicious websites and protecting against phishing attacks.
Network Access Control (NAC) ensures only authorized and compliant devices can connect to the network, preventing unauthorized access points.
Data Protection Technologies
Protecting sensitive data is paramount. Data Loss Prevention (DLP) tools monitor data movement and prevent sensitive information from leaving the network without authorization. Cloud Access Security Brokers (CASB) secure access to cloud services, enforcing security policies and monitoring activity within cloud environments. Data Encryption ensures that even if data is compromised, it remains unreadable to unauthorized individuals.
These measures, used in conjunction, provide robust data protection across various environments.
| Function | Technology | Description | Example |
|---|---|---|---|
| Identity | Multi-Factor Authentication (MFA) | Requires multiple forms of authentication for access. | Using a password and a one-time code from an authenticator app. |
| Identity | Privileged Access Management (PAM) | Controls and monitors access for high-privilege accounts. | Restricting access to administrative accounts and auditing all actions. |
| Network | Micro-segmentation | Divides the network into smaller, isolated segments. | Isolating sensitive databases from less critical systems. |
| Network | Software-Defined Perimeter (SDP) | Creates secure tunnels between users and applications. | Establishing secure connections to cloud-based applications. |
| Data Protection | Data Loss Prevention (DLP) | Monitors data movement and prevents sensitive information from leaving the network. | Preventing sensitive documents from being emailed outside the organization. |
| Data Protection | Cloud Access Security Broker (CASB) | Secures access to cloud services and monitors activity. | Enforcing security policies for cloud storage services like AWS S3. |
Data Security and Protection within Zero Trust
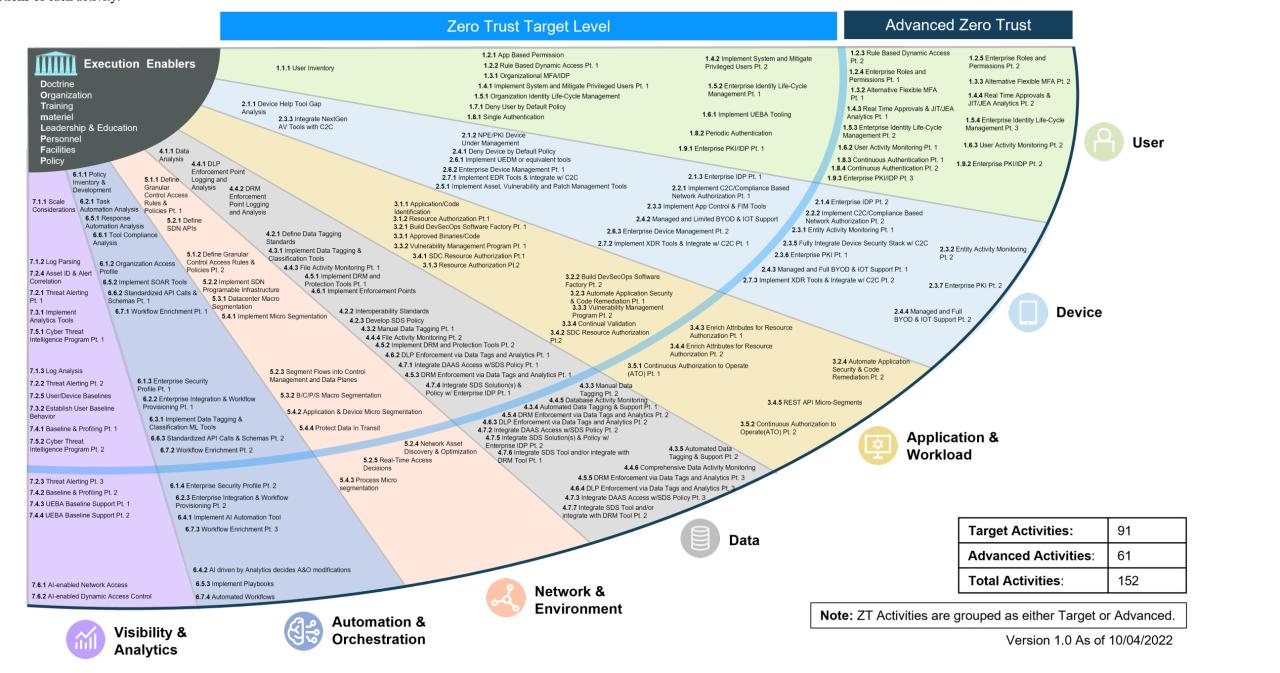
The Pentagon’s updated zero trust strategy necessitates a robust approach to data security, moving beyond perimeter-based defenses. This shift requires a granular, context-aware system that continuously verifies and authorizes access to sensitive data, regardless of location or device. This approach minimizes the impact of breaches and strengthens overall data protection.Data security under zero trust relies on a multi-layered approach that integrates various technologies and policies.
The core principle is to assume no implicit trust and verify every access request. This involves stringent access controls, robust encryption, and continuous monitoring to ensure data remains protected throughout its lifecycle.
Data Loss Prevention (DLP) and Data Encryption
Data Loss Prevention (DLP) tools play a crucial role in the Pentagon’s zero trust architecture by identifying and preventing sensitive data from leaving the controlled environment without authorization. These tools monitor data movement across various channels, including email, cloud storage, and removable media. They employ techniques like content inspection and data fingerprinting to detect and block unauthorized data exfiltration attempts.
Simultaneously, robust encryption, both at rest and in transit, ensures that even if data is intercepted, it remains unreadable without the appropriate decryption keys. This layered approach—DLP preventing unauthorized access and encryption protecting the data itself—is vital for maintaining confidentiality and integrity. For example, the use of end-to-end encryption for all communications and at-rest encryption for all sensitive data stored on servers and in the cloud is paramount.
Data Classification Schemes in a Zero Trust Environment
Different data classification schemes are employed to categorize data based on its sensitivity and criticality. These schemes typically range from “Unclassified” to “Top Secret,” each level requiring increasingly stringent access controls. In a zero trust environment, data classification informs the access control policies, ensuring that only authorized users with the appropriate clearance and need-to-know access sensitive data. The Pentagon likely uses a highly refined classification scheme tailored to its specific needs, with stringent protocols for handling classified information, including strict access controls and audit trails.
A mismatch between classification and access rights would trigger an alert, highlighting a potential security risk.
Data Access Control and Monitoring
Imagine a visual representation: A central hub (the zero trust architecture) manages access requests. Each request passes through multiple verification points: authentication (verifying user identity), authorization (checking user permissions for specific data), and context-aware checks (considering location, device, and time). If all checks pass, access is granted, and the activity is logged. If any check fails, access is denied, and an alert is triggered.
Continuous monitoring tracks all data access attempts, both successful and unsuccessful, creating an audit trail for investigation and security analysis. This system employs various technologies, including micro-segmentation, identity and access management (IAM) systems, and security information and event management (SIEM) tools, to maintain a comprehensive overview of data access and security posture.
The Role of Artificial Intelligence and Automation
The Pentagon’s updated zero trust strategy relies heavily on the power of artificial intelligence (AI) and automation to bolster its defenses against increasingly sophisticated cyber threats. These technologies are no longer futuristic concepts; they are crucial components for achieving the speed, scale, and precision needed to effectively manage the complexities inherent in a zero trust architecture. By automating repetitive tasks and leveraging AI’s analytical capabilities, the Department of Defense can significantly improve its security posture and proactively address emerging risks.AI and automation are transforming how the Department of Defense approaches cybersecurity within the zero trust framework.
Automation streamlines processes like user authentication, access control, and incident response, reducing the burden on human analysts and improving overall efficiency. Simultaneously, AI algorithms analyze massive datasets to identify patterns and anomalies indicative of malicious activity, enabling faster threat detection and more effective responses. This proactive approach is vital in a zero-trust environment, where every access request is treated as potentially untrusted and requires rigorous verification.
AI in Threat Detection and Response
AI algorithms, particularly machine learning models, are exceptionally effective at identifying subtle indicators of compromise (IOCs) that might be missed by human analysts. These models can analyze network traffic, system logs, and user behavior to detect anomalies that suggest malicious activity. For example, an AI system might detect unusual login attempts from an unexpected geographical location or identify suspicious data exfiltration patterns.
Furthermore, AI can automate the response to identified threats, such as isolating infected systems or blocking malicious traffic, significantly reducing the impact of a successful attack. The speed and scale at which AI can perform these tasks are crucial advantages in the fast-paced world of cyber warfare. For instance, a successful AI-driven response to a distributed denial-of-service (DDoS) attack could mitigate the impact within minutes, whereas a purely human-driven response might take significantly longer.
Benefits and Risks of AI and Automation in Cybersecurity Defense
The benefits of integrating AI and automation into a zero trust framework are substantial. These include improved threat detection and response times, reduced operational costs through automation, and the ability to handle the ever-increasing volume of security data. However, the implementation of AI and automation also presents significant risks. AI models can be vulnerable to adversarial attacks, where malicious actors attempt to manipulate the model’s output to evade detection.
Additionally, there’s the risk of bias in AI algorithms, leading to inaccurate or unfair security decisions. The reliance on automation also raises concerns about the potential for unintended consequences, particularly if automated systems are not properly monitored and controlled. A comprehensive risk management strategy is essential to mitigate these potential downsides. This includes regular testing and validation of AI models, robust monitoring of automated systems, and a human-in-the-loop approach to ensure appropriate oversight.
Hypothetical System Architecture Incorporating AI and Automation
A robust zero trust system incorporating AI and automation would consist of several key components working in concert.
The following bullet points Artikel a hypothetical system architecture:
- AI-Powered Security Information and Event Management (SIEM): This system collects and analyzes security logs from various sources, using AI to identify and prioritize potential threats.
- Automated Threat Response System: This system automatically responds to identified threats based on pre-defined rules and AI-generated recommendations, such as isolating infected systems or blocking malicious traffic.
- AI-Driven User and Entity Behavior Analytics (UEBA): This system monitors user and device behavior to detect anomalies that may indicate malicious activity. For example, unusual login times or access patterns could trigger an alert.
- Automated Vulnerability Management System: This system automatically scans systems for vulnerabilities and prioritizes remediation efforts based on risk assessment. AI could be used to predict which vulnerabilities are most likely to be exploited.
- AI-Enhanced Access Control System: This system uses AI to dynamically assess user risk and grant access based on a continuous risk assessment. This ensures that access is only granted to authorized users and devices, even if they are already inside the network perimeter.
- Centralized Security Orchestration, Automation, and Response (SOAR) Platform: This platform integrates and orchestrates the various security tools and processes, automating workflows and improving overall efficiency.
These components interact by sharing data and insights. The SIEM system feeds data to the UEBA system, which then informs the access control system. The threat response system is triggered by alerts from the SIEM and UEBA systems. The SOAR platform orchestrates these interactions and provides a unified view of the security posture.
The Pentagon’s updated zero trust strategy is a game-changer, demanding a robust and adaptable security architecture. This shift necessitates agile development practices, which is where the power of domino app dev the low code and pro code future comes into play. Faster development cycles are crucial for implementing and updating security measures quickly, helping organizations stay ahead of evolving threats within the zero trust framework.
Ultimately, this focus on speed and efficiency is essential for strengthening national cybersecurity.
Compliance and Regulatory Aspects

The Pentagon’s adoption of a zero trust architecture isn’t just a technological shift; it’s a fundamental change in how the Department of Defense (DoD) approaches security and, consequently, compliance. Meeting the stringent regulatory demands placed upon handling sensitive national security information requires a robust and adaptable security framework, and zero trust provides that. This section delves into the specific compliance regulations and standards influencing the Pentagon’s zero trust strategy and examines how this new architecture facilitates compliance.The DoD operates under a complex web of regulations and standards designed to protect sensitive data and maintain operational security.
These include, but are not limited to, the National Institute of Standards and Technology (NIST) Cybersecurity Framework, the Federal Information Security Modernization Act (FISMA), and various directives related to data handling and access control within the DoD. Meeting these requirements traditionally involved perimeter-based security measures, which are increasingly inadequate in the face of sophisticated cyber threats. Zero trust, with its focus on continuous verification and least privilege access, offers a more effective approach.
Relevant Compliance Regulations and Standards
The Pentagon’s zero trust strategy must adhere to a range of critical compliance requirements. These regulations dictate data handling, access control, and security protocols, aiming to mitigate risks and ensure data integrity and confidentiality. Failure to comply can result in significant penalties and operational disruptions. Key regulations include FISMA, which mandates a risk-based approach to information security management; NIST SP 800-53, providing a comprehensive set of security controls; and NIST SP 800-207, which specifically addresses zero trust architecture implementation guidance.
Additionally, DoD-specific directives and instructions further refine these overarching standards, tailoring them to the unique needs and sensitivities of military operations and data.
Zero Trust’s Role in Meeting Compliance Requirements
Zero trust’s inherent design significantly improves the DoD’s ability to meet compliance requirements. Traditional perimeter-based security models struggle to manage the increasingly distributed and dynamic nature of modern networks. Zero trust, however, focuses on verifying every access request, regardless of location or network segment. This continuous verification inherently reduces the attack surface and minimizes the impact of potential breaches.
The principle of least privilege, a cornerstone of zero trust, ensures that users only have access to the minimum resources necessary to perform their tasks, limiting the potential damage from compromised accounts. This granular control directly addresses many of the requirements Artikeld in FISMA, NIST SP 800-53, and other relevant regulations. Furthermore, robust logging and monitoring capabilities inherent in a zero trust architecture facilitate compliance auditing and incident response, providing essential evidence for regulatory compliance demonstrations.
Comparison with Traditional Security Approaches
Traditional security approaches rely heavily on perimeter defenses, such as firewalls and intrusion detection systems, to protect internal networks. This “castle-and-moat” mentality assumes that anything inside the perimeter is trusted. Zero trust, in contrast, assumes no implicit trust, regardless of location. This fundamental shift dramatically alters the approach to compliance. In traditional models, compliance often focuses on demonstrating the effectiveness of perimeter defenses.
Zero trust shifts the focus to continuous verification, granular access control, and robust monitoring, requiring a more proactive and data-driven approach to compliance. This means a move away from simply checking boxes to a more dynamic and risk-based approach to security and compliance management.
Key Compliance Considerations
The successful implementation of a zero trust architecture within the DoD requires careful consideration of several key factors. These factors are crucial for ensuring compliance and maximizing the effectiveness of the zero trust strategy.
- Data Classification and Access Control: Implementing a robust data classification scheme is paramount. This ensures that sensitive data is appropriately protected based on its classification level, aligning with regulations like FISMA and DoD directives.
- Identity and Access Management (IAM): A strong IAM system is critical for verifying identities and managing access privileges. This system must be integrated with the zero trust architecture to ensure continuous authentication and authorization.
- Micro-segmentation: Dividing the network into smaller, isolated segments limits the impact of breaches, minimizing the potential exposure of sensitive data. This aligns with the principle of least privilege.
- Security Information and Event Management (SIEM): A robust SIEM system is essential for monitoring security events, detecting threats, and providing audit trails for compliance purposes.
- Regular Security Assessments and Audits: Regular assessments and audits are necessary to ensure the ongoing effectiveness of the zero trust architecture and compliance with relevant regulations.
- Incident Response Planning: A comprehensive incident response plan is crucial for handling security incidents effectively and minimizing their impact. This plan must be aligned with the zero trust architecture.
Last Point
The Pentagon’s updated zero trust strategy is a game-changer, not just for the Department of Defense, but for cybersecurity as a whole. The shift to a “never trust, always verify” model is crucial in today’s complex threat environment. While implementation will be challenging, the potential benefits – improved security posture, enhanced data protection, and more efficient incident response – are significant.
The journey towards full zero trust adoption will undoubtedly be iterative, but the direction is clear: a future where every access request is meticulously scrutinized and authorized.
FAQ Resource
What are the biggest hurdles in implementing zero trust within a large organization like the DoD?
Massive legacy systems, integrating diverse technologies, and widespread user training are major obstacles. Overcoming these requires careful planning, phased implementation, and significant investment.
How does the Pentagon’s approach to zero trust differ from commercial sector implementations?
While the core principles are similar, the Pentagon’s implementation will likely involve stricter regulatory compliance, heightened security requirements due to handling classified information, and a focus on national security concerns.
What role does AI play in the Pentagon’s zero trust strategy?
AI is crucial for automating threat detection, analyzing security logs, and enhancing incident response. It helps manage the vast amount of data generated in a zero trust environment, allowing for quicker identification and mitigation of threats.





