The Zen of Cybersecurity BigFix Peace of Mind
The Zen of Cybersecurity BigFix and the path to peace of mind: Imagine a world where cybersecurity isn’t a constant source of stress, but a calm, proactive practice. This isn’t some utopian dream; it’s achievable with the right tools and mindset. This post dives into how BigFix can help you find that elusive cybersecurity zen, transforming anxiety into confident control over your digital landscape.
We’ll explore how a mindful approach, combined with the powerful capabilities of BigFix, can build a robust and resilient security posture.
We’ll unpack BigFix’s features, showing you how it simplifies vulnerability management, automates patching, and even helps with endpoint detection and response (EDR). But it’s not just about the technology; we’ll also discuss the crucial human element – building a security-conscious culture within your organization and empowering your team with the knowledge and skills to navigate the ever-evolving threat landscape.
Get ready to trade sleepless nights for a confident, secure future.
Introducing the Concept of “Zen Cybersecurity”
In today’s hyper-connected world, cybersecurity threats are a constant, looming presence. The pressure to stay ahead of attackers, coupled with the potential consequences of a breach, can lead to a state of perpetual stress and anxiety. But what if we approached cybersecurity with a different mindset, one rooted in calm, mindfulness, and a long-term perspective? This is the essence of “Zen Cybersecurity.” It’s about cultivating a balanced approach that prioritizes proactive strategies, mindful decision-making, and a resilient response to inevitable challenges, rather than succumbing to reactive panic.Zen Cybersecurity draws inspiration from Zen Buddhism’s emphasis on mindfulness, acceptance, and a focus on the present moment.
Instead of reacting to every alert with alarm, a Zen approach encourages a measured, thoughtful response. This involves understanding the broader context of each threat, assessing its potential impact, and implementing appropriate countermeasures without unnecessary panic. By cultivating a calm and focused state of mind, we can make more effective security decisions, reducing the likelihood of errors and improving our overall security posture.
Mindfulness and Calm Improve Cybersecurity Practices
Mindfulness practices, such as meditation and deep breathing, can significantly enhance our ability to handle cybersecurity challenges. When faced with a security incident, a calm and focused mind allows for clearer thinking and more effective problem-solving. Instead of being overwhelmed by the urgency of the situation, a mindful approach enables a systematic assessment of the threat, identification of vulnerabilities, and implementation of remediation strategies.
This contrasts sharply with the reactive, often panicked, response that can lead to hasty and potentially ineffective decisions. For example, rushing to disable a system without fully understanding the impact could lead to greater disruption than the initial threat. A mindful approach would prioritize careful investigation and analysis before taking action.
Stress and Anxiety Negatively Impact Security Decision-Making
Conversely, stress and anxiety can severely impair our ability to make sound security judgments. Under pressure, we are more likely to make mistakes, overlook critical details, and succumb to impulsive actions. Imagine a security analyst facing a complex, multi-faceted attack while simultaneously dealing with the pressure of impending deadlines and a looming performance review. Their heightened stress levels could cloud their judgment, leading them to overlook crucial indicators or implement flawed countermeasures.
This can significantly increase the risk of a successful breach and exacerbate the overall damage. Furthermore, chronic stress can lead to burnout, reducing vigilance and increasing susceptibility to errors. A study by the American Psychological Association, for instance, highlights the link between stress and impaired cognitive function, directly impacting decision-making capabilities.
BigFix as a Tool for Achieving Cybersecurity Peace of Mind

In today’s complex threat landscape, achieving true cybersecurity peace of mind requires more than just point solutions. A comprehensive, proactive approach is essential, and that’s where BigFix shines. This powerful platform offers a unified approach to endpoint management and security, providing organizations with the visibility and control needed to effectively mitigate risks and prevent breaches.BigFix’s strength lies in its ability to automate and streamline critical security processes, reducing the burden on IT teams and minimizing the window of vulnerability.
By integrating vulnerability management, patch deployment, and endpoint security into a single platform, BigFix offers a level of efficiency and effectiveness that traditional, siloed security solutions simply can’t match.
BigFix’s Capabilities in Vulnerability Management and Remediation
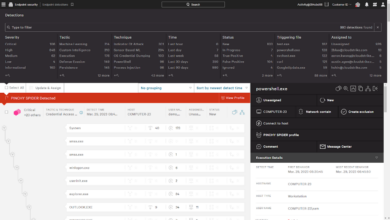
BigFix excels at identifying and addressing vulnerabilities across an organization’s entire endpoint landscape. Its comprehensive scanning capabilities detect missing patches, outdated software, and misconfigurations, providing a clear picture of the organization’s security posture. Once vulnerabilities are identified, BigFix automates the remediation process, deploying patches and updates efficiently and consistently across all managed endpoints. This automated approach significantly reduces the time it takes to address vulnerabilities, minimizing the organization’s attack surface and reducing the risk of successful exploitation.
The platform’s reporting and analytics capabilities further enhance its effectiveness, providing valuable insights into the organization’s vulnerability landscape and the effectiveness of remediation efforts. This allows for continuous improvement of security posture and proactive mitigation of emerging threats.
BigFix Case Studies Demonstrating Effectiveness in Preventing Security Breaches
While specific details of security incidents are often kept confidential for competitive and security reasons, the effectiveness of BigFix in preventing breaches is consistently highlighted in industry reports and anecdotal evidence. For example, imagine a scenario where a critical vulnerability in a widely used application is publicly disclosed. With BigFix, organizations can quickly identify all affected endpoints, deploy the necessary patches, and verify successful remediation within a matter of hours, significantly reducing the window of opportunity for attackers.
This proactive approach minimizes the risk of a successful breach, protecting sensitive data and maintaining business continuity. The speed and efficiency of BigFix’s automated remediation process are key factors in preventing successful exploitation of vulnerabilities. Many organizations have reported significantly reduced mean time to remediation (MTTR) after implementing BigFix, demonstrating its effectiveness in preventing breaches.
Comparison of BigFix to Traditional Security Solutions
Traditional security solutions often rely on a patchwork of disparate tools, leading to inefficiencies and security gaps. BigFix, on the other hand, provides a unified and integrated approach. The following table highlights the key differences:
| Feature | BigFix | Traditional Solution | Advantages of BigFix |
|---|---|---|---|
| Vulnerability Management | Automated discovery and remediation of vulnerabilities across all endpoints. | Manual processes, often involving multiple tools and significant manual effort. | Increased efficiency, reduced MTTR, improved accuracy. |
| Patch Management | Automated patch deployment and verification across all endpoints. | Manual or semi-automated processes, often resulting in inconsistent patching and delayed remediation. | Improved consistency, reduced risk, enhanced security posture. |
| Endpoint Security | Integrated endpoint security capabilities, including malware detection and prevention. | Separate endpoint security tools, requiring integration and management challenges. | Simplified management, reduced complexity, improved visibility. |
| Reporting and Analytics | Comprehensive reporting and analytics, providing insights into security posture and remediation effectiveness. | Limited reporting capabilities, often requiring manual data aggregation and analysis. | Improved visibility, data-driven decision-making, proactive risk management. |
Practical Application of BigFix for Enhanced Security
BigFix, with its powerful capabilities, transcends the theoretical realm of cybersecurity and delves into practical, impactful solutions. Its ability to automate tasks, centralize management, and provide real-time insights makes it a cornerstone for organizations seeking robust and efficient security. This section explores how BigFix can be leveraged for enhanced security, focusing on patching automation, endpoint detection and response (EDR), and a step-by-step implementation guide.BigFix’s automation capabilities dramatically improve security posture by streamlining crucial tasks and reducing the human error factor often associated with manual processes.
This automation translates to faster response times to vulnerabilities, minimized downtime, and improved overall security hygiene.
Automating Patching and Updates Across Various Systems
BigFix excels at automating the deployment of patches and updates across a diverse range of systems, from Windows and macOS endpoints to Linux servers and even embedded devices. This eliminates the inconsistencies and delays inherent in manual patching processes. A centralized dashboard provides a clear view of patch compliance across the entire infrastructure, allowing administrators to identify and remediate vulnerabilities proactively.
For example, a company with hundreds of Windows machines can use BigFix to automatically deploy critical security updates, ensuring all systems are patched within a defined timeframe. This reduces the window of vulnerability and significantly lowers the risk of successful cyberattacks exploiting known vulnerabilities. The automated reporting capabilities further streamline compliance audits, providing evidence of timely patching.
BigFix for Endpoint Detection and Response (EDR)
While not a dedicated EDR solution in the same vein as standalone EDR products, BigFix can significantly enhance an organization’s endpoint detection and response capabilities. Its ability to collect real-time data from endpoints, coupled with its robust scripting capabilities, enables proactive threat hunting and incident response. By deploying custom scripts and leveraging BigFix’s reporting functionalities, administrators can monitor for suspicious activities, such as unusual file executions or network connections, and quickly respond to potential threats.
For instance, BigFix can be configured to alert administrators if malware is detected on an endpoint, allowing for immediate isolation and remediation. This proactive approach, combined with its comprehensive system inventory and vulnerability assessment features, gives BigFix a significant role in an overall EDR strategy.
Implementing BigFix within a Hypothetical Organization: A Step-by-Step Guide
Implementing BigFix requires a strategic approach. The following steps Artikel a phased rollout for a hypothetical organization:
- Assessment and Planning: Begin by assessing the organization’s current IT infrastructure, identifying all endpoints and servers needing management. Define clear objectives, such as reducing vulnerability exposure or improving patch compliance rates. This stage also involves selecting appropriate hardware and software resources for the BigFix server and relays.
- Installation and Configuration: Install the BigFix server and configure it according to best practices. This includes setting up appropriate network access, security policies, and user accounts.
- Endpoint Enrollment: Enroll all endpoints into the BigFix infrastructure. This typically involves installing a client agent on each endpoint, which communicates with the BigFix server to receive instructions and report its status.
- Policy Creation and Deployment: Create and deploy policies for patching, software distribution, and other security-related tasks. These policies dictate the actions BigFix will perform on enrolled endpoints. This includes scheduling regular scans for vulnerabilities and automatically deploying patches when available.
- Monitoring and Reporting: Establish a robust monitoring system to track the health of the BigFix infrastructure and the compliance status of endpoints. Regularly review reports to identify potential security issues and proactively address them.
- Ongoing Maintenance and Optimization: Continuously monitor and optimize BigFix policies and configurations to ensure optimal performance and effectiveness. This includes regular updates to the BigFix server and client agents.
Building a Proactive Security Posture with BigFix
BigFix, with its powerful patching, configuration management, and endpoint security capabilities, allows organizations to move beyond reactive security measures and establish a robust, proactive defense. Instead of constantly playing catch-up with emerging threats, BigFix empowers you to anticipate and mitigate risks before they can exploit vulnerabilities. This proactive approach significantly reduces your attack surface and strengthens your overall security posture.BigFix’s strength lies in its ability to automate tasks that would otherwise require significant manual effort.
This automation is key to a proactive security strategy, enabling rapid deployment of patches, consistent enforcement of security policies, and real-time monitoring of endpoint health. By leveraging these capabilities, organizations can effectively prevent many common security incidents.
Preventative Security Strategy Using BigFix
A preventative security strategy using BigFix centers around automating the deployment and enforcement of security controls across your entire IT infrastructure. This involves regularly updating software, configuring security settings consistently, and monitoring for deviations from established baselines. BigFix enables the creation of automated remediation workflows, ensuring that identified vulnerabilities are addressed swiftly and efficiently. For instance, BigFix can automatically deploy critical security patches to all endpoints as soon as they are released, minimizing the window of vulnerability.
Furthermore, it can enforce consistent security configurations, such as disabling unnecessary services or strengthening password policies, across all devices. Regular vulnerability scans integrated within the BigFix framework allow for proactive identification of weaknesses, enabling immediate remediation.
BigFix and Compliance with Industry Security Standards
BigFix significantly contributes to compliance with various industry security standards, such as NIST Cybersecurity Framework, ISO 27001, and HIPAA. By automating the deployment and enforcement of security policies, BigFix provides auditable evidence of compliance. For example, demonstrating compliance with PCI DSS regarding regular vulnerability scanning and patching becomes significantly easier with BigFix’s automated reporting and logging capabilities. The ability to track and report on software updates, security configurations, and vulnerability remediation efforts offers a comprehensive audit trail, essential for demonstrating adherence to regulatory requirements.
BigFix’s centralized management console simplifies the process of generating compliance reports, saving significant time and resources compared to manual processes.
Challenges in Integrating BigFix and Mitigation Strategies
Integrating BigFix into an existing IT infrastructure can present certain challenges. One common challenge is the initial complexity of configuring and deploying BigFix across a large and diverse network. This can be mitigated through a phased rollout approach, starting with a pilot program on a smaller subset of endpoints before expanding to the entire organization. Another potential challenge is the need for skilled personnel to manage and maintain the BigFix system effectively.
Addressing this requires investing in training and development for IT staff or engaging external expertise during the initial implementation phase. Finally, integrating BigFix with existing security tools and systems may require careful planning and customization to ensure seamless data exchange and automated workflows. This can be streamlined by utilizing BigFix’s extensive API and leveraging pre-built integrations wherever possible.
The Human Element in Cybersecurity
Achieving true cybersecurity peace of mind isn’t solely about technology; it’s fundamentally about people. Even the most robust BigFix implementation will be vulnerable if employees aren’t trained and motivated to practice safe cybersecurity habits. A security-conscious culture is the bedrock of a truly secure organization.A proactive approach to security awareness is crucial. This isn’t a one-time training session; it’s an ongoing commitment to educating and empowering employees to be the first line of defense.
By fostering a culture of security awareness, we minimize the human error that often exploits vulnerabilities in even the most advanced systems.
Strategies for Fostering a Security-Conscious Culture
Building a security-conscious culture requires a multifaceted approach. It involves clear communication, consistent reinforcement, and engaging employees at all levels. This isn’t just about compliance; it’s about making security a shared responsibility. A successful strategy integrates security into daily operations, making it a natural part of the work environment rather than an afterthought.
Best Practices for Employee Training and Awareness
Effective training goes beyond simply checking boxes. It needs to be engaging, relevant, and tailored to the specific roles and responsibilities of employees. This involves using various methods – interactive modules, simulations, real-world examples, and gamification – to make learning memorable and impactful. Regular refresher courses and updates on emerging threats are also vital to maintain a high level of awareness.
Employees should be encouraged to report suspicious activity without fear of reprisal, creating a culture of open communication around security concerns.
A Successful Security Awareness Program: A Visual Representation
Imagine a multi-layered pyramid. The base, the largest section, represents ongoing, regular training modules delivered through various methods (e.g., short videos, interactive quizzes, simulated phishing attacks). These modules cover topics such as password security, phishing awareness, malware prevention, and social engineering tactics. The next layer depicts regular security newsletters and announcements, highlighting current threats and best practices. This layer keeps employees informed and reinforces the training.
The third layer, smaller than the previous two, represents annual or bi-annual security awareness workshops or conferences, offering more in-depth training and opportunities for interaction and Q&A with security professionals. The top of the pyramid, the smallest section, showcases a robust reporting system and a clearly defined process for employees to report security incidents without fear of retribution. This system ensures that any potential breaches are identified and addressed promptly.
This pyramid visualizes a program that’s comprehensive, engaging, and consistently reinforces security best practices throughout the year. The program is built on a foundation of ongoing training and communication, reinforced by periodic deep dives and a strong incident reporting mechanism.
BigFix and Future Trends in Cybersecurity
BigFix, with its robust patch management and endpoint security capabilities, is well-positioned to navigate the ever-evolving cybersecurity landscape. Its adaptability hinges on its architecture and its capacity to integrate with emerging technologies. This allows it to not only address current threats but also anticipate and mitigate future ones, contributing to a more proactive and resilient security posture.BigFix’s strength lies in its agent-based architecture, which provides granular control and visibility across diverse IT environments.
This allows for rapid response to new threats and vulnerabilities. Furthermore, its ability to integrate with various security information and event management (SIEM) systems and threat intelligence feeds ensures that it remains informed about the latest threats and can proactively address them.
BigFix’s Adaptation to Emerging Threats and Technologies
The rapid proliferation of IoT devices, cloud computing, and the increasing sophistication of cyberattacks necessitate a dynamic approach to cybersecurity. BigFix’s capacity for automation and orchestration is crucial here. For example, the platform can be configured to automatically detect and respond to newly discovered vulnerabilities in IoT devices connected to the network, implementing patches or isolating compromised devices before significant damage occurs.
Similarly, its integration with cloud-based security solutions allows for seamless protection across hybrid environments. The ability to extend BigFix’s functionality through custom scripts and actions further enhances its adaptability to unique organizational needs and emerging threats. This allows organizations to create bespoke solutions for specific vulnerabilities and rapidly respond to zero-day exploits.
BigFix and AI/Machine Learning for Enhanced Security
The integration of AI and machine learning (ML) with BigFix offers significant potential for proactive threat detection and response. ML algorithms can be trained on BigFix’s vast data set of endpoint activity to identify anomalous behavior indicative of malware or intrusions. This allows for the early detection of threats before they can cause significant damage. Furthermore, AI can automate threat response, such as automatically isolating infected systems or initiating remediation actions.
For instance, an ML model could be trained to identify patterns associated with ransomware attacks, enabling BigFix to proactively block or quarantine suspicious files before they can encrypt sensitive data. This proactive approach shifts the focus from reactive incident response to predictive threat mitigation.
BigFix’s Future Role Compared to Emerging Cybersecurity Platforms, The zen of cybersecurity bigfix and the path to peace of mind
While several emerging cybersecurity platforms utilize AI and automation, BigFix’s established presence and extensive capabilities provide a strong foundation for future growth. Unlike some newer, more specialized platforms, BigFix offers a comprehensive approach to endpoint security, encompassing patch management, vulnerability assessment, and configuration management. This breadth of functionality allows for a more holistic and integrated security strategy. While cloud-based security platforms offer scalability and accessibility, BigFix’s on-premises and hybrid deployment options provide flexibility and control for organizations with stringent data sovereignty requirements.
The key differentiator for BigFix in the future will be its ability to seamlessly integrate AI and ML capabilities within its existing framework, enhancing its existing strengths rather than replacing them. This allows for a gradual evolution of the platform, reducing disruption and maximizing the value of existing investments.
Final Wrap-Up
Achieving true cybersecurity peace of mind requires a holistic approach – a blend of powerful technology and a proactive, mindful mindset. BigFix emerges as a crucial ally in this journey, offering a practical path to a more secure and less stressful digital existence. By embracing its capabilities and fostering a culture of security awareness, organizations can move beyond reactive firefighting and into a proactive, preventative posture.
The zen of cybersecurity isn’t just a catchy phrase; it’s a tangible reality within reach, and BigFix is your key to unlocking it. So, take a deep breath, embrace the power of proactive security, and find your cybersecurity zen.
Frequently Asked Questions: The Zen Of Cybersecurity Bigfix And The Path To Peace Of Mind
What if BigFix doesn’t integrate with our existing systems?
BigFix offers a range of integration options and its team provides support to help overcome compatibility challenges.
How much does BigFix cost?
Pricing varies depending on the specific needs and scale of deployment; contact IBM for a customized quote.
Is BigFix suitable for small businesses?
Yes, BigFix offers scalable solutions, making it suitable for organizations of all sizes.
What kind of training is needed to use BigFix effectively?
IBM provides comprehensive training resources and support to help users master BigFix’s functionalities.