Top 5 PCI Compliance Mistakes and How to Avoid Them
Top 5 PCI Compliance Mistakes and How to Avoid Them: Navigating the complex world of PCI compliance can feel like a minefield. One wrong step, one overlooked detail, and your business could be facing serious consequences. This isn’t just about hefty fines; it’s about protecting your customers’ sensitive data and maintaining the trust that’s crucial for your success.
Let’s dive into the five most common pitfalls and arm ourselves with the knowledge to avoid them.
From insufficient access controls leaving your systems vulnerable to attacks, to neglecting crucial security awareness training for your employees, we’ll cover it all. We’ll explore the importance of regular patching, vulnerability scanning, and security audits – the cornerstones of a robust PCI DSS compliance program. Get ready to strengthen your security posture and safeguard your business.
Insufficient Access Control
Insufficient access control is a major vulnerability in any system, and PCI DSS compliance demands robust measures to mitigate the risks. Weak or improperly configured access controls leave sensitive cardholder data exposed to unauthorized individuals or processes, potentially leading to data breaches, financial losses, and reputational damage. Failing to properly manage access significantly increases the likelihood of a successful attack.
The consequences of inadequate access control can be severe. Unauthorized users might gain access to sensitive data, leading to data theft, fraud, or identity theft. This can result in significant financial penalties, legal repercussions, and a loss of customer trust. Furthermore, a breach caused by insufficient access control can damage a company’s reputation, leading to a decline in business and customer loyalty.
Best Practices for Implementing Strong Access Controls
Implementing strong access controls involves a multi-layered approach. This includes assigning least privilege access, regularly reviewing and updating access rights, and employing robust authentication mechanisms. Least privilege ensures that users only have access to the data and systems absolutely necessary for their job functions. This minimizes the potential damage from a compromised account. Regular reviews and updates ensure that access rights remain appropriate and that terminated employees no longer have access.
Multi-factor authentication adds an extra layer of security, making it significantly harder for unauthorized individuals to gain access.
Multi-Factor Authentication
Multi-factor authentication (MFA) requires users to provide multiple forms of authentication to verify their identity before accessing systems or data. Common methods include passwords, one-time codes generated by authenticator apps (like Google Authenticator or Authy), security tokens, or biometric authentication (fingerprint or facial recognition). By requiring more than one factor, MFA significantly reduces the risk of unauthorized access, even if one factor is compromised.
For example, even if a password is stolen, an attacker would still need access to the second factor (e.g., a one-time code) to gain entry. This dramatically increases the security posture of the system.
Regular Review and Update of Access Rights
Regularly reviewing and updating access rights is crucial for maintaining a secure environment. This process should involve identifying users who no longer require access to certain systems or data, removing or modifying their access privileges accordingly, and ensuring that access is granted only to authorized individuals based on their job roles and responsibilities. This process should be documented and conducted at least annually, or more frequently if there are significant changes within the organization.
For example, when an employee leaves the company, their access should be immediately revoked.
Access Control Methods and Effectiveness
| Access Control Method | Description | Effectiveness | Vulnerabilities |
|---|---|---|---|
| Password-based authentication | Users authenticate using a username and password. | Low to Moderate (easily compromised) | Susceptible to phishing, brute-force attacks, and password reuse. |
| Multi-factor authentication (MFA) | Users authenticate using multiple factors (e.g., password + one-time code). | High | Can be bypassed if all factors are compromised, user experience may be slightly decreased. |
| Role-Based Access Control (RBAC) | Access is granted based on user roles and responsibilities. | Moderate to High | Requires careful role definition and management; vulnerabilities exist if roles are not properly defined or managed. |
| Attribute-Based Access Control (ABAC) | Access is granted based on attributes of the user, resource, and environment. | High | Complex to implement and manage; requires a robust policy engine. |
Inadequate Security Awareness Training
Failing to adequately train employees on cybersecurity best practices is a major contributor to PCI DSS non-compliance. Even the strongest technical security measures are vulnerable if employees are unaware of phishing scams, social engineering tactics, or simply best practices for handling sensitive data. A robust security awareness program is crucial for building a strong security culture and mitigating human error, a leading cause of data breaches.A comprehensive security awareness training program goes beyond a single, annual compliance training session.
It should be an ongoing process that adapts to evolving threats and reinforces best practices. Regular training, coupled with engaging methods, is far more effective than infrequent, dry lectures.
Developing a Comprehensive Security Awareness Training Program, Top 5 pci compliance mistakes and how to avoid them
Creating a successful program requires a multi-faceted approach. It should incorporate various learning styles and methods to ensure information is effectively absorbed. This includes using a mix of interactive modules, videos, quizzes, and real-world scenarios to keep employees engaged and actively involved in their learning. The program should also be tailored to different roles and responsibilities within the organization, acknowledging that a cashier’s training needs will differ from those of a network administrator.
Regular assessments and feedback mechanisms help gauge the effectiveness of the program and identify areas needing improvement. For instance, tracking the completion rates of modules and the scores on quizzes provides valuable data. This allows for targeted interventions and adjustments to the training materials to improve comprehension and retention.
The Importance of Regular Phishing Simulations and Security Awareness Testing
Regular phishing simulations are invaluable tools for assessing employee vulnerability to social engineering attacks. These simulated attacks expose weaknesses in employee awareness and provide an opportunity for immediate remediation. For example, a simulated phishing email could be sent, and employee responses tracked. Those who click on malicious links or reveal sensitive information receive immediate feedback and further training.
Beyond phishing, broader security awareness testing can include quizzes, scenario-based exercises, and even tabletop exercises that simulate real-world security incidents. These tests provide a measure of the effectiveness of the training and highlight areas requiring reinforcement. For instance, a scenario might involve an employee receiving a suspicious phone call requesting sensitive data. The employee’s response and ability to identify and handle the situation are then evaluated.
Key Elements of Employee Training Materials
Effective training materials should be clear, concise, and relevant to employees’ daily tasks. They should avoid technical jargon and focus on practical application. Engaging visuals, such as short videos and infographics, can significantly improve comprehension and retention. The use of relatable scenarios and real-world examples makes the training more impactful and memorable. For instance, a video showing the consequences of a data breach, including financial losses and reputational damage, can be significantly more effective than a simple bullet-point list of policies.
Finally, regular reinforcement and refresher training are essential to maintain awareness and prevent complacency.
Topics Covered in Security Awareness Training
A comprehensive security awareness training program should cover a range of topics, including:
- Understanding PCI DSS requirements and their importance
- Recognizing and avoiding phishing scams and social engineering attacks
- Creating and managing strong passwords
- Protecting sensitive data, including credit card information
- Safeguarding physical security and access control
- Reporting security incidents and vulnerabilities
- Proper use of company devices and networks
- Understanding and adhering to company security policies
- Data encryption and its importance
- The consequences of security breaches and non-compliance
Failure to Regularly Patch Systems and Applications

Failing to regularly patch your systems and applications is a major PCI DSS compliance vulnerability. Unpatched systems are essentially open doors for cybercriminals, inviting attacks that can compromise sensitive cardholder data and lead to hefty fines and reputational damage. This oversight is a frequent cause of data breaches, making it a critical area to address for any organization handling payment card information.Unpatched systems expose organizations to a wide range of vulnerabilities.
These vulnerabilities can range from relatively minor bugs to critical security flaws that allow attackers to gain complete control of the system. For example, outdated software might contain known exploits that allow attackers to inject malicious code, steal data, or launch denial-of-service attacks. These exploits are often publicly available, making it easier for even less sophisticated attackers to compromise vulnerable systems.
Understanding the top 5 PCI compliance mistakes, like weak access controls and insufficient encryption, is crucial for any business handling cardholder data. Building secure applications is key, and that’s where exploring modern development approaches like those discussed in this insightful article on domino app dev the low code and pro code future can really help. By leveraging these advancements, you can create robust, secure applications that minimize your PCI compliance risks, ultimately protecting your business and your customers.
Specifically, unpatched systems can leave your organization susceptible to malware infections, remote code execution, privilege escalation, and data exfiltration. The consequences can be severe, including financial losses, legal repercussions, and damage to brand reputation.
Robust Patch Management Processes
A robust patch management process is crucial for mitigating the risks associated with outdated software. This process involves identifying, testing, and deploying security updates to all systems and applications in a timely manner. A well-defined process ensures that all systems are up-to-date with the latest security patches, reducing the attack surface and minimizing the risk of successful breaches. A successful patch management program requires careful planning, comprehensive documentation, and ongoing monitoring.
Key elements include regular vulnerability scanning, a prioritized patching schedule, and a system for tracking patch deployments and verifying their effectiveness. Failing to implement a robust process leaves your organization vulnerable to attack.
Implementing an Effective Patching Strategy: A Step-by-Step Guide
Implementing an effective patching strategy requires a structured approach. Here’s a step-by-step guide:
1. Vulnerability Assessment
Regularly scan your systems for vulnerabilities using automated tools and manual checks. This helps identify outdated software and potential weaknesses. Prioritize vulnerabilities based on their severity and the potential impact on your systems.
2. Patch Prioritization
Prioritize patching based on risk. Critical vulnerabilities that could lead to immediate data breaches should be addressed first. Consider factors such as the severity of the vulnerability, the likelihood of exploitation, and the potential impact of a successful attack.
3. Testing
Before deploying patches to production systems, thoroughly test them in a controlled environment to ensure they don’t introduce new problems or disrupt functionality. This testing phase should mimic real-world scenarios to identify potential conflicts.
4. Deployment
Deploy patches in a controlled and staged manner, starting with non-critical systems and gradually moving to production systems. Monitor system performance closely after each deployment to detect and address any issues promptly.
5. Verification
After deployment, verify that the patches have been successfully applied and that the vulnerabilities have been resolved. Regularly review the patch management process to ensure its effectiveness.
6. Documentation
Maintain comprehensive documentation of all patches applied, including the date, time, system affected, and any issues encountered during the process. This documentation is crucial for auditing and troubleshooting.
Delayed Patching vs. Immediate Patching: Risk Assessment
The decision to immediately patch or delay patching depends on a careful risk assessment. Delayed patching increases the window of vulnerability, leaving systems exposed to potential attacks. Immediate patching, while reducing risk, might disrupt operations if not properly planned and tested. The risk of delayed patching is significantly higher than the disruption caused by a well-planned and tested immediate patching strategy.
A carefully considered risk assessment, factoring in the severity of the vulnerability and the potential impact of a breach, is crucial in making this decision. For critical vulnerabilities, immediate patching is generally recommended, even if it requires temporary downtime. For less critical vulnerabilities, a more measured approach, involving thorough testing and potentially scheduled downtime, might be suitable.
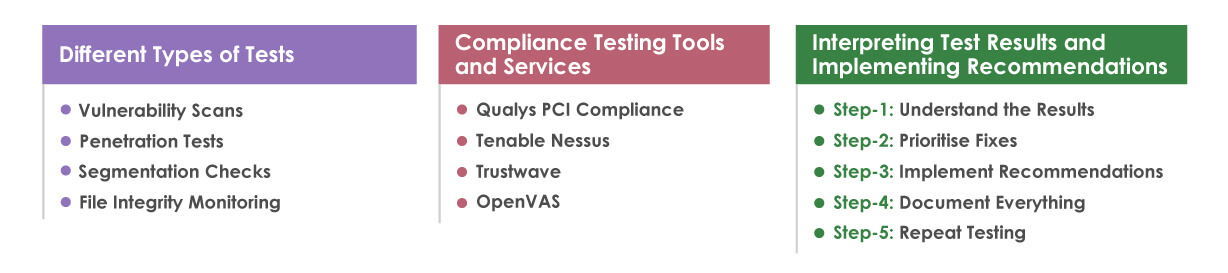
Lack of Vulnerability Scanning and Penetration Testing
Regular vulnerability scanning and penetration testing are critical components of a robust PCI DSS compliance program. Ignoring these crucial security measures leaves your organization exposed to significant risks, including data breaches, financial penalties, and reputational damage. By proactively identifying and addressing vulnerabilities, you can significantly reduce your attack surface and strengthen your overall security posture.Vulnerability scanning and penetration testing, while related, offer distinct benefits.
Vulnerability scanning automatically identifies potential weaknesses in your systems and applications, providing a comprehensive overview of your security posture. Penetration testing, on the other hand, simulates real-world attacks to assess the effectiveness of your security controls and identify exploitable vulnerabilities that automated scans might miss. Together, these processes provide a layered approach to security assessment, ensuring a more complete understanding of your organization’s vulnerabilities.
Types of Vulnerability Scans and Penetration Testing Methodologies
Vulnerability scans can be categorized into several types, each with its strengths and weaknesses. Network scans examine your network infrastructure for common vulnerabilities, while application scans focus on identifying vulnerabilities within specific software applications. Database scans assess the security of your databases, and web application scans target vulnerabilities in web applications, a critical area for PCI DSS compliance.
Penetration testing methodologies vary, but common approaches include black-box testing (testers have no prior knowledge of the system), white-box testing (testers have full knowledge of the system), and gray-box testing (testers have partial knowledge of the system). Each approach offers a different perspective and helps identify vulnerabilities from various angles.
Comparison of Vulnerability Scanning Tools
Choosing the right vulnerability scanning tool is crucial. The following table compares some popular options, highlighting their strengths and weaknesses:
| Tool | Pros | Cons | Price Model |
|---|---|---|---|
| Nessus | Comprehensive vulnerability scanning, extensive plugin library, detailed reporting | Can be complex to configure, requires significant expertise to interpret results | Subscription |
| OpenVAS | Open-source, cost-effective, regularly updated | Requires technical expertise to install and configure, reporting might be less user-friendly | Free (open-source) |
| QualysGuard | Cloud-based, easy to use, integrated vulnerability management platform | Can be expensive, reliance on a cloud service | Subscription |
| Acunetix | Specialized in web application vulnerability scanning, accurate and detailed reports | Primarily focused on web applications, might not cover other areas as comprehensively | Subscription |
Vulnerability Remediation Process
Once vulnerabilities have been identified through scanning and penetration testing, a systematic remediation process is crucial. This process typically involves:
- Prioritization: Categorize vulnerabilities based on severity (critical, high, medium, low) and potential impact. Focus on addressing critical vulnerabilities first.
- Analysis: Thoroughly investigate each vulnerability to understand its root cause and potential impact.
- Remediation: Implement appropriate fixes, such as patching software, configuring security settings, or updating hardware.
- Verification: After remediation, re-scan and retest to verify that the vulnerability has been successfully addressed.
- Documentation: Maintain detailed records of all identified vulnerabilities, remediation steps, and verification results.
Neglecting Regular Security Audits and Assessments: Top 5 Pci Compliance Mistakes And How To Avoid Them
Regular security audits and assessments are the cornerstone of a robust PCI DSS compliance program. They provide a critical independent evaluation of your organization’s security posture, identifying weaknesses before they can be exploited by malicious actors. Ignoring this crucial step leaves your organization vulnerable to costly breaches and reputational damage. Think of it as a regular health checkup for your IT infrastructure – preventative measures are far cheaper and less disruptive than emergency surgery.Regular security audits and assessments help organizations proactively identify and mitigate risks, ensuring ongoing compliance with PCI DSS standards and other relevant regulations.
These audits provide a clear picture of your current security state, highlighting areas for improvement and ultimately reducing your organization’s overall risk profile. This proactive approach minimizes the likelihood of data breaches and associated financial penalties.
Types of Security Audits and Assessments
Several types of security audits and assessments contribute to a comprehensive PCI DSS compliance program. These include vulnerability scans, penetration testing, and internal security audits. Vulnerability scans automatically identify known security flaws in systems and applications. Penetration testing simulates real-world attacks to assess the effectiveness of your security controls. Internal security audits involve a systematic review of policies, procedures, and controls within your organization.
A combination of these approaches provides a layered defense and a more complete picture of your security posture. For example, a vulnerability scan might reveal outdated software, which a penetration test would then attempt to exploit, illustrating the practical implications of the vulnerability. A subsequent internal audit could then assess whether appropriate patching procedures were followed.
PCI DSS Audit Checklist
A comprehensive PCI DSS audit should cover a wide range of areas. A key element is verifying the implementation of all twelve PCI DSS requirements. This includes reviewing access control measures, network security, vulnerability management, and incident response plans. Specifically, the audit should verify the effectiveness of security policies, procedures, and controls. For example, it should confirm that only authorized personnel have access to sensitive cardholder data, that systems are regularly patched, and that a robust incident response plan is in place and tested.
The checklist should also encompass physical security, employee training, and regular monitoring of network activity. A thorough review of logs and security alerts is also crucial, as is documentation of all security-related activities. The audit should examine the effectiveness of these security measures in protecting cardholder data.
Creating a Security Audit Report
A well-structured security audit report summarizes the findings and provides actionable recommendations. The report should begin with an executive summary highlighting the key findings and overall security posture. Following this, a detailed section should present the findings of the audit, organized by category (e.g., network security, access control, vulnerability management). Each finding should be clearly described, including its severity level (critical, high, medium, low) and the potential impact.
The report should also include supporting evidence, such as screenshots or log extracts. Finally, the report should provide specific, actionable recommendations for improvement, including timelines and assigned responsibilities. For example, a finding of insufficient access control might recommend implementing multi-factor authentication and providing specific training for employees on access control procedures within a given timeframe. This report should be presented to management for review and action.
Summary

Successfully navigating PCI compliance isn’t just about ticking boxes; it’s about cultivating a culture of security within your organization. By addressing these top five mistakes, implementing strong security practices, and staying vigilant, you’re not just meeting regulatory requirements – you’re building a resilient and trustworthy business. Remember, proactive security is an investment, not an expense, and the peace of mind it provides is invaluable.
Query Resolution
What happens if I fail a PCI DSS audit?
Failure can lead to fines, loss of merchant processing privileges, reputational damage, and potential legal action.
How often should I conduct vulnerability scans?
Regular scans, ideally monthly, are recommended to identify and address vulnerabilities promptly.
What are the different types of PCI DSS audits?
There are various types, including on-site audits, remote audits, and self-assessments, depending on your business size and risk profile.
Is PCI DSS compliance only for large businesses?
No, any business that processes, stores, or transmits cardholder data is subject to PCI DSS requirements, regardless of size.
How can I train my employees effectively on security awareness?
Use a mix of methods: online modules, interactive training, phishing simulations, and regular reminders to keep security top-of-mind.