Top 7 Ecommerce Cybersecurity Threats & Avoidance Tips
Top 7 Ecommerce Cybersecurity Threats and tips to avoid them – that’s a scary-sounding title, right? But don’t panic! Running an online store means navigating a digital minefield of potential threats. From sneaky phishing scams to devastating denial-of-service attacks, the risks are real. This post dives deep into seven common ecommerce cybersecurity threats, breaking down how they work and, more importantly, how to protect your business and your customers’ data.
We’ll explore practical strategies to bolster your defenses and keep your online shop safe and secure.
Understanding these threats is the first step towards building a robust security posture. We’ll cover everything from securing your database against SQL injection attacks to implementing multi-factor authentication to prevent weak credentials from becoming a major vulnerability. By the end, you’ll have a clearer picture of the risks and the actionable steps you can take to mitigate them. Let’s get started!
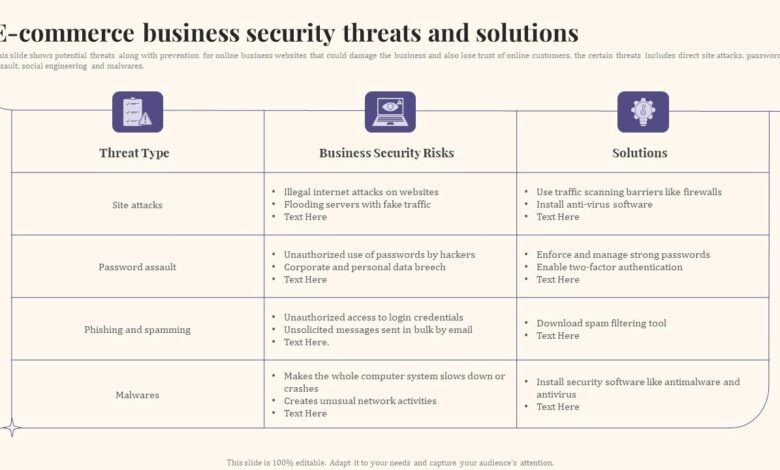
Phishing Attacks
Phishing attacks are a significant threat to e-commerce businesses, aiming to steal sensitive customer data and financial information. These attacks leverage social engineering techniques to trick victims into revealing their credentials or downloading malicious software. Understanding the mechanics and tactics behind these attacks is crucial for implementing effective preventative measures.Phishing attacks against e-commerce businesses typically involve deceptive emails, websites, or text messages that mimic legitimate entities.
These fraudulent communications lure victims into providing personal information, such as usernames, passwords, credit card details, and addresses, which are then used for fraudulent transactions or identity theft. The attackers often exploit brand reputation and urgency to increase the likelihood of success.
Common Phishing Tactics in E-commerce
Attackers employ various tactics to make their phishing attempts convincing. These include creating realistic-looking emails that appear to be from trusted sources like banks, payment processors, or the e-commerce platform itself. They might include urgent requests for account verification, password resets, or notifications about suspicious activity. The use of spoofed email addresses and websites, coupled with carefully crafted messaging, significantly enhances the deception.
Moreover, attackers frequently leverage current events or create a sense of urgency to pressure victims into acting quickly without verifying the legitimacy of the communication.
Examples of Phishing Emails and Websites
A common example might involve an email appearing to come from a popular online retailer, informing the recipient of a supposed shipping delay or a problem with their order. The email contains a link to a fake website that looks identical to the legitimate retailer’s site. Once the user clicks the link and enters their login credentials, the information is captured by the attacker.
Another example could be a text message claiming a prize or a discount, urging the user to click a link to claim their reward, which leads to a malicious website designed to steal financial information. These websites are meticulously crafted to mimic the look and feel of authentic e-commerce platforms, making them difficult to distinguish from the real thing.
Comparison of Phishing Attack Types
The effectiveness of a phishing attack depends on various factors, including the sophistication of the attack, the target audience, and the methods employed. Here’s a comparison of different types:
| Attack Type | Target | Method | Success Rate (Estimate) |
|---|---|---|---|
| Spear Phishing | Specific individuals or businesses | Highly personalized emails or messages | High (15-30%) |
| Clone Phishing | Customers of a specific e-commerce site | Mimics legitimate emails or websites | Medium (5-15%) |
| Whaling | High-profile individuals or executives | Sophisticated and targeted attacks | High (20-40%)
|
| Deceptive Website Phishing | Online shoppers | Fake websites mimicking legitimate e-commerce sites | Medium (10-20%) |
*Note: Success rates are estimates based on various industry reports and may vary depending on factors like target audience and attack sophistication.*
Malware and Viruses
E-commerce platforms, with their vast databases of customer information and financial transactions, are prime targets for malware and viruses. These malicious programs can wreak havoc, leading to data breaches, financial losses, and reputational damage, ultimately impacting customer trust and business viability. Understanding the different types of malware and how they infiltrate systems is crucial for effective prevention.Malware and viruses affect e-commerce platforms in several significant ways.
They can steal sensitive customer data like credit card details, addresses, and personally identifiable information (PII). This stolen data can be used for identity theft, fraudulent transactions, or sold on the dark web. Furthermore, malware can disrupt operations, leading to website downtime and loss of sales. In extreme cases, ransomware can encrypt critical data, holding it hostage until a ransom is paid.
This can cripple an online business, leading to significant financial losses and potentially forcing closure. The damage extends beyond direct financial impact; it severely erodes customer trust, making it difficult to recover lost business.
Types of Malware Targeting E-commerce Sites
Ransomware, spyware, and trojans are among the most prevalent malware strains targeting e-commerce sites. Ransomware encrypts files, rendering them inaccessible until a ransom is paid. Spyware secretly monitors user activity, stealing sensitive information like login credentials and browsing history. Trojans disguise themselves as legitimate software, gaining access to the system to perform malicious actions, often acting as a backdoor for further attacks.
For example, a recent attack on a major online retailer involved ransomware that encrypted customer order databases, demanding a substantial ransom for decryption. The incident resulted in significant downtime, frustrated customers, and substantial financial losses. Another example involves spyware targeting e-commerce platforms that stole customer payment information, leading to fraudulent transactions and massive financial losses for both the business and its customers.
Methods of Malware Injection
Malware can infiltrate e-commerce systems through various methods. Phishing emails containing malicious attachments or links are a common vector. Exploiting vulnerabilities in outdated software and plugins is another popular method. Hackers often target known vulnerabilities to gain unauthorized access. Compromised third-party applications or integrations can also serve as entry points for malware.
Finally, SQL injection attacks can directly target the database, potentially compromising sensitive customer data. Imagine a scenario where a hacker successfully exploits a vulnerability in a poorly maintained e-commerce plugin, gaining access to the backend system and installing malware that steals customer credit card information. This scenario highlights the importance of regular security updates and proactive vulnerability management.
Preventative Measures Against Malware and Virus Infections
Implementing robust security measures is crucial to mitigate the risk of malware and virus infections.
- Regularly update software and plugins to patch known vulnerabilities.
- Implement a strong firewall to block unauthorized access attempts.
- Use robust anti-malware and antivirus software and keep it updated.
- Educate employees about phishing scams and other social engineering tactics.
- Regularly back up data to a secure offsite location.
- Employ multi-factor authentication (MFA) to enhance security.
- Conduct regular security audits and penetration testing to identify vulnerabilities.
- Implement strong password policies and enforce regular password changes.
- Restrict access to sensitive data based on the principle of least privilege.
- Monitor system logs for suspicious activity.
SQL Injection Attacks
SQL injection is a serious threat to e-commerce websites, allowing attackers to manipulate database queries and potentially steal or modify sensitive customer data. This type of attack exploits vulnerabilities in how web applications handle user inputs, particularly those interacting directly with a database. Understanding how these attacks work and implementing preventative measures is crucial for maintaining the security and integrity of your online store.SQL injection attacks leverage the fact that many web applications directly incorporate user-supplied data into SQL queries.
If these inputs aren’t properly sanitized or validated, an attacker can inject malicious SQL code into the query, altering its intended behavior. This can lead to unauthorized access to data, modification of records, or even complete database compromise. The consequences can be devastating, ranging from financial losses to reputational damage and legal repercussions.
Vulnerabilities in E-commerce Databases Susceptible to SQL Injection
E-commerce databases store a wealth of sensitive information, making them prime targets for SQL injection. Vulnerabilities often arise in forms, search bars, and other input fields where users provide data that directly influences database queries. For instance, a poorly designed login system might directly incorporate a username provided by the user into a SQL query without proper validation.
Similarly, a search function that doesn’t sanitize user input could be vulnerable. Essentially, any point where user input directly affects a database query represents a potential entry point for an SQL injection attack. Failing to parameterize queries, relying on dynamic SQL construction without proper escaping, and inadequate input validation are all major contributors to these vulnerabilities.
How SQL Injection Attacks Compromise Customer Data and Sensitive Information
A successful SQL injection attack can grant an attacker complete control over the targeted database. They can retrieve customer data, including names, addresses, credit card information, passwords, and order history. They might modify existing data, deleting orders, altering prices, or even creating fraudulent accounts. In some cases, attackers can even gain control of the entire server hosting the e-commerce platform.
The impact on customer trust and the financial implications of such breaches can be catastrophic. Consider a scenario where an attacker retrieves a list of customer credit card numbers – the resulting financial and reputational damage could be immense.
Examples of SQL Injection Code and Their Effects on an E-commerce Database
Let’s imagine a login form where the username is directly inserted into a SQL query:
SELECTFROM users WHERE username = 'userinput';
A malicious user could input:
' OR '1'='1
This would modify the query to:
SELECTFROM users WHERE username = '' OR '1'='1';
Since ‘1’=’1′ is always true, the query would return all user records from the database. Another example involves altering data:
UPDATE users SET password = 'newpassword' WHERE username = 'userinput';
An attacker could inject code to update multiple user passwords at once, creating widespread chaos.
Methods for Preventing SQL Injection Vulnerabilities in E-commerce Applications
The most effective way to prevent SQL injection is to avoid directly embedding user input into SQL queries. Instead, use parameterized queries or prepared statements. These methods treat user input as data, not as executable code, preventing the injection of malicious SQL commands. Input validation is also critical. Sanitize and validate all user input before using it in any database query.
This involves checking data types, lengths, and formats, and removing or escaping any potentially harmful characters. Regular security audits and penetration testing can identify and address vulnerabilities before they can be exploited. Finally, utilizing a web application firewall (WAF) can provide an additional layer of protection by filtering out malicious traffic. Keeping your database software and applications up-to-date with security patches is also crucial to mitigating known vulnerabilities.
Denial-of-Service (DoS) Attacks

Denial-of-Service (DoS) attacks are a significant threat to e-commerce businesses, aiming to disrupt online services and make them unavailable to legitimate users. These attacks can cripple an online store, leading to lost sales, damaged reputation, and frustrated customers. The impact extends beyond immediate revenue loss; a prolonged outage can erode customer trust and make it difficult to regain market share.DoS attacks flood a target server with malicious traffic, overwhelming its resources and preventing it from responding to legitimate requests.
This effectively renders the website inaccessible, halting online transactions and preventing customers from browsing products or completing purchases. The severity of the impact depends on the duration and intensity of the attack, as well as the e-commerce platform’s resilience and mitigation strategies. A short, low-intensity attack might cause only minor disruptions, while a sustained, high-volume attack could bring an entire online store to its knees for hours or even days.
Types of DoS Attacks
DoS attacks manifest in various forms, each employing different techniques to disrupt service. Understanding these variations is crucial for implementing effective countermeasures.
- Volumetric Attacks: These attacks aim to overwhelm the target’s bandwidth by flooding it with massive amounts of traffic from numerous sources. Common examples include UDP floods (sending large numbers of UDP packets), ICMP floods (using ping requests to overload the network), and HTTP floods (sending numerous HTTP requests). The sheer volume of traffic consumes network bandwidth, preventing legitimate requests from reaching the server.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols to disrupt communication. Examples include SYN floods (exploiting the TCP three-way handshake to exhaust server resources) and Smurf attacks (amplifying the attack by exploiting network devices to reflect traffic back to the target).
- Application-Layer Attacks: These attacks target specific applications or services running on the server. They often exploit vulnerabilities in the application’s code to consume server resources or disrupt its functionality. Examples include HTTP slowloris attacks (sending slow HTTP requests to tie up server resources) and slow POST attacks (similar to slowloris, but using POST requests).
Mitigation and Prevention Techniques
Protecting against DoS attacks requires a multi-layered approach combining preventative measures and reactive strategies.
- Network-Level Mitigation: Implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and content delivery networks (CDNs) can help filter malicious traffic and distribute the load across multiple servers, making it more difficult for attackers to overwhelm the system. CDNs, in particular, are effective at absorbing large volumes of traffic by caching content closer to users.
- Server-Level Mitigation: Employing load balancers to distribute traffic across multiple servers, optimizing server configurations for efficiency, and implementing rate limiting to restrict the number of requests from a single IP address can enhance resilience. Regularly updating server software and patching vulnerabilities is also critical.
- Application-Level Mitigation: Implementing robust input validation and sanitization to prevent application-layer attacks, using web application firewalls (WAFs) to filter malicious requests, and regularly conducting security audits and penetration testing can identify and address vulnerabilities before attackers exploit them.
- Cloud-Based Solutions: Leveraging cloud-based DDoS mitigation services can provide scalable protection against large-scale attacks. These services often incorporate advanced techniques to identify and filter malicious traffic, providing a robust defense against sophisticated attacks.
DoS Attack Flowchart, Top 7 ecommerce cybersecurity threats and tips to avoid them
Imagine a flowchart depicting a typical DoS attack against an e-commerce website. The flowchart would begin with the attacker identifying the target website. Next, the attacker selects a DoS attack method (e.g., volumetric, protocol). Then, the attacker launches the attack, sending a massive volume of malicious traffic to the target server. This flood of traffic overwhelms the server’s resources, causing it to become unresponsive and unavailable to legitimate users.
Finally, the attack continues until the attacker stops or the target mitigates the attack. The flowchart would visually represent this sequence of events, clearly showing the steps involved in a typical DoS attack. The visual representation would emphasize the attacker’s actions and the resulting impact on the e-commerce website’s availability.
Cross-Site Scripting (XSS) Attacks
Cross-site scripting (XSS) attacks are a serious threat to e-commerce websites, exploiting vulnerabilities to inject malicious scripts into otherwise trusted websites. These scripts can then steal sensitive user data, redirect users to phishing sites, or deface the website itself, causing significant damage to both the business and its customers. Understanding how these attacks work and implementing effective mitigation strategies is crucial for maintaining a secure online shopping environment.XSS attacks leverage weaknesses in how a web application handles user-supplied data.
Essentially, an attacker injects malicious code into a website’s input fields (such as search bars, comment sections, or even profile updates). When a legitimate user views the compromised page, their browser executes the injected script, granting the attacker access to the user’s session, cookies, and potentially other sensitive information. The consequences can range from minor inconveniences to catastrophic data breaches.
Consequences of XSS Attacks
Successful XSS attacks can have severe repercussions for both e-commerce businesses and their customers. For customers, the immediate risk is the theft of personal information like login credentials, credit card details, and addresses. This can lead to identity theft, financial losses, and significant personal distress. For businesses, the consequences include reputational damage, loss of customer trust, legal liabilities (especially concerning data breaches), and financial losses due to lost sales, refunds, and the costs associated with remediation and security upgrades.
A single successful XSS attack can severely impact a company’s bottom line and its long-term viability.
Examples of XSS Attacks in E-commerce
Imagine a scenario where an attacker injects malicious JavaScript into the “comment” field of a product review page. When other users view the page, the injected script might steal their session cookies, allowing the attacker to access their shopping cart and purchase items using the victim’s account. Another example could involve an attacker injecting a script into a login page’s username field.
Upon successful login, the script might redirect the user to a fake login page designed to capture their credentials. These attacks can be subtle and difficult to detect, making them particularly dangerous.
Types of XSS Attacks, Vectors, and Mitigation Strategies
Understanding the different types of XSS attacks and their vectors is crucial for effective mitigation. The following table Artikels common types, their methods of delivery, the impact they have, and strategies to prevent them.
| Attack Type | Vector | Impact | Mitigation |
|---|---|---|---|
| Reflected XSS | Malicious script reflected back to the user from the server in the response (e.g., in a search result). | Session hijacking, redirection to malicious sites. | Input validation and sanitization, encoding output, using HTTPOnly cookies. |
| Stored XSS (Persistent XSS) | Malicious script stored on the server (e.g., in a database, comment section). | Data theft, website defacement, long-term compromise. | Input validation and sanitization, output encoding, regular security audits. |
| DOM Based XSS | Malicious script executed within the client-side Document Object Model (DOM) without server-side interaction. | Data theft, manipulation of website functionality. | Secure coding practices, using Content Security Policy (CSP). |
Man-in-the-Middle (MitM) Attacks
Man-in-the-middle (MitM) attacks are a serious threat to e-commerce security, allowing attackers to secretly intercept communication between a customer and a website. This compromise allows them to steal sensitive information like usernames, passwords, credit card details, and other personal data, effectively eavesdropping on the entire online transaction. Understanding how these attacks work and implementing robust security measures is crucial for protecting both businesses and their customers.MitM attacks leverage various methods to intercept communication.
Attackers might create rogue Wi-Fi hotspots mimicking legitimate networks (like a coffee shop’s Wi-Fi), intercepting traffic sent over unencrypted connections. They can also exploit vulnerabilities in network infrastructure or use sophisticated techniques like DNS spoofing to redirect users to malicious websites that look identical to the legitimate site. The attacker then sits “in the middle,” reading and potentially modifying the data exchanged between the user and the server before forwarding it on.
Examples of MitM Attacks Compromising Customer Data
Imagine a customer attempting to purchase a product online. If a MitM attack is successful, the attacker could intercept the customer’s credit card details as they’re being transmitted to the e-commerce site. The attacker could then use this information to make fraudulent purchases or sell the data on the dark web. Similarly, an attacker could intercept login credentials, allowing them to access the customer’s account and steal more personal information or make unauthorized purchases.
Even if the website uses HTTPS, vulnerabilities in the server’s SSL/TLS implementation could be exploited to allow the MitM attack. For instance, a poorly configured or outdated certificate could be vulnerable to attacks. A successful MitM attack on a banking website could lead to the theft of significant financial assets.
Securing Online Transactions and Preventing MitM Attacks
The most effective way to prevent MitM attacks is to ensure all communication between the customer and the e-commerce site is encrypted using HTTPS. HTTPS encrypts the data exchanged, making it unreadable to anyone intercepting the communication. Additionally, using strong encryption protocols and regularly updating security certificates is crucial. Furthermore, employing robust security measures like multi-factor authentication (MFA) adds an extra layer of protection, making it significantly harder for attackers to gain unauthorized access even if they manage to intercept login credentials.
Educating customers about the risks of public Wi-Fi and encouraging the use of VPNs when connecting to unsecured networks is also a vital preventative measure.
Best Practices for Implementing Secure HTTPS and Using Strong Encryption
Implementing robust security requires a multi-pronged approach. Here’s a list of best practices:
- Always use HTTPS: Ensure your website uses HTTPS with a valid SSL/TLS certificate from a trusted Certificate Authority (CA).
- Use strong encryption: Employ strong cipher suites that support forward secrecy to protect against future compromises of encryption keys.
- Regularly update certificates: Replace your SSL/TLS certificates before they expire to avoid security vulnerabilities.
- Implement HTTP Strict Transport Security (HSTS): HSTS forces browsers to always use HTTPS, preventing downgrade attacks.
- Perform regular security audits: Conduct regular penetration testing and vulnerability assessments to identify and address potential weaknesses.
- Use a Web Application Firewall (WAF): A WAF can help detect and block malicious traffic before it reaches your server.
- Educate employees and customers: Train your employees about security best practices and educate your customers on how to identify and avoid phishing attempts and other social engineering tactics.
Weak or Stolen Credentials
In the world of e-commerce, where sensitive customer data and financial transactions are commonplace, weak or stolen credentials represent a significant threat. This vulnerability exposes businesses and customers to a wide range of risks, from financial losses to reputational damage and legal repercussions. Understanding the causes, consequences, and mitigation strategies for this threat is crucial for maintaining a secure online environment.Compromised user accounts can have devastating consequences for both e-commerce businesses and their customers.
For businesses, a data breach resulting from weak or stolen credentials can lead to significant financial losses due to fraudulent transactions, regulatory fines, and the costs associated with remediation efforts. The damage to a company’s reputation can also be substantial, leading to a loss of customer trust and impacting future sales. Customers, on the other hand, face the risk of identity theft, financial fraud, and the emotional distress associated with such breaches.
Their personal information, including addresses, credit card details, and potentially even social security numbers, could fall into the wrong hands.
Causes of Weak or Stolen Credentials
Several factors contribute to the prevalence of weak or stolen credentials in e-commerce. Many users opt for easily guessable passwords, such as “password123” or their birthdays, making their accounts vulnerable. Additionally, the reuse of passwords across multiple online platforms is a common practice that significantly increases the risk of compromise. If one platform is breached, attackers can use the stolen credentials to access other accounts using the same password.
Poor password management practices, including a lack of password updates, also play a significant role. Furthermore, phishing attacks, malware infections, and keyloggers can directly lead to the theft of usernames and passwords.
Methods Used by Attackers
Attackers employ various methods to obtain usernames and passwords. One prevalent technique is credential stuffing, where attackers use lists of stolen usernames and passwords obtained from previous data breaches to attempt logins on other websites. They systematically try these combinations until they find a successful match. Another common method is phishing, where attackers trick users into revealing their credentials through deceptive emails or websites that mimic legitimate e-commerce platforms.
Keyloggers, malicious software that records keystrokes, can also capture login information as users type it into their browsers.
Best Practices for Password Management and User Authentication
Implementing robust password management and user authentication practices is crucial for mitigating the risks associated with weak or stolen credentials. Enforcing strong password policies, requiring users to create complex passwords that meet specific length and complexity requirements, is a fundamental step. Regular password changes should also be encouraged, along with the use of unique passwords for each online account.
So, you’re diving into the crucial world of top 7 ecommerce cybersecurity threats and tips to avoid them? Building robust security is key, and that often involves choosing the right development tools. For instance, consider how streamlined development can be with the power of low-code/pro-code platforms like those discussed in this great article on domino app dev the low code and pro code future , which can help speed up secure app creation.
Ultimately, though, remember that even the best tech needs strong security practices to combat those top 7 threats effectively.
Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code sent to their mobile phone or email address. This makes it significantly more difficult for attackers to gain unauthorized access, even if they possess the user’s password. MFA significantly reduces the likelihood of successful credential stuffing attacks.
Additionally, educating users about the importance of password security and providing them with resources to create and manage strong passwords is essential. Regular security audits and penetration testing can also help identify and address vulnerabilities in the e-commerce platform’s authentication systems.
Concluding Remarks: Top 7 Ecommerce Cybersecurity Threats And Tips To Avoid Them
Securing your ecommerce business requires ongoing vigilance and a proactive approach. While there’s no foolproof solution, implementing the strategies Artikeld above – from strengthening password policies to regularly updating software – significantly reduces your vulnerability to common threats. Remember, the cost of a security breach far outweighs the investment in preventative measures. By staying informed and taking action, you can protect your business, your customers, and your peace of mind.
Stay safe out there!
Question & Answer Hub
What is credential stuffing, and how can I prevent it?
Credential stuffing is when hackers use lists of stolen usernames and passwords to try and access accounts on different websites. To prevent it, enforce strong password policies, implement multi-factor authentication, and use a reputable password manager.
How often should I update my ecommerce platform’s software?
Regularly! Software updates often include critical security patches. Aim for updating as soon as patches are released, following your platform’s recommended update schedule.
What’s the difference between a DoS and a DDoS attack?
A DoS (Denial-of-Service) attack comes from a single source, while a DDoS (Distributed Denial-of-Service) attack uses multiple sources to overwhelm a server. DDoS attacks are significantly harder to mitigate.
What are some signs that my website has been compromised?
Unusual website activity, unexpected charges on your accounts, customer complaints about suspicious emails, and changes to your website’s content are all potential red flags.





