
Toshiba and Orange Offer Quantum Secure Data Transmission
Toshiba and Orange offer quantum secure data transmission with utmost security – a game-changer in the world of data protection! Forget everything you thought you knew about encryption; this isn’t your grandpappy’s digital lock. We’re diving into the fascinating world of quantum key distribution (QKD), where the laws of quantum mechanics are leveraged to create an unbreakable shield against cyber threats.
Prepare to be amazed by the potential of this revolutionary technology and its implications for everything from financial transactions to healthcare records.
This collaboration between Toshiba and Orange promises unparalleled security, utilizing the principles of quantum mechanics to create encryption keys that are virtually impossible to crack. We’ll explore the technology’s core components, compare it to traditional methods, and examine its potential impact on various industries. Get ready for a deep dive into the future of secure communication!
Toshiba and Orange’s Quantum Secure Data Transmission Technology
The collaboration between Toshiba and Orange marks a significant step forward in secure data transmission, leveraging the principles of quantum key distribution (QKD) to achieve unprecedented levels of security. This technology offers a compelling alternative to traditional encryption methods, promising enhanced protection against increasingly sophisticated cyber threats.
Fundamental Principles of Toshiba and Orange’s QKD
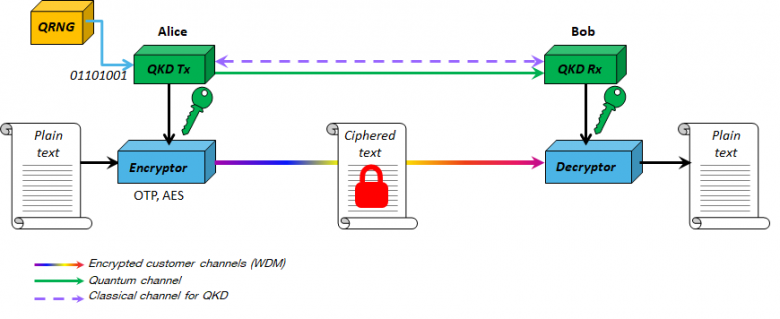
Toshiba and Orange’s system relies on the fundamental principles of quantum mechanics to generate and distribute encryption keys. Specifically, it utilizes the properties of photons – individual particles of light – to create a secure communication channel. The core idea is that any attempt to intercept or measure the photons during transmission will inevitably alter their quantum state, alerting the sender and receiver to the presence of an eavesdropper.
This “quantum uncertainty” forms the basis of the system’s security. The keys are generated using a process where random polarization states of photons are transmitted. The shared secret key is then derived from the agreement on the polarization states, making it computationally impossible to break.
Hardware and Software Components
The system’s hardware components include specialized quantum key distribution devices installed at both the sender and receiver ends. These devices generate, transmit, and receive the photons, typically using fiber optic cables. Sophisticated detectors measure the polarization states of the received photons. The software components manage the key generation, distribution, and integration with existing communication infrastructure. The software protocols ensure secure key management, authentication, and error correction, guaranteeing the integrity and confidentiality of the transmitted data.
It also handles the reconciliation process, where the sender and receiver compare a subset of their measurements to verify the integrity of the key. The post-processing involves error correction and privacy amplification to enhance the security of the final key.
Comparison with Traditional Encryption Methods
Traditional encryption methods, such as AES and RSA, rely on complex mathematical algorithms to encrypt data. While these methods are widely used and generally secure, they are vulnerable to attacks from sufficiently powerful quantum computers. Quantum-secure data transmission, in contrast, leverages the laws of physics to guarantee security, making it inherently resistant to attacks from even future quantum computers.
However, QKD systems are currently more expensive and complex to implement than traditional encryption methods, and their transmission range is limited by the properties of the optical fiber used. They also require specialized hardware and expertise for installation and maintenance.
Comparison of Key Features
| Feature | Toshiba/Orange QKD | AES-256 | RSA-2048 |
|---|---|---|---|
| Security Level | Theoretically unbreakable (against quantum and classical attacks) | High, but vulnerable to future quantum computers | High, but vulnerable to future quantum computers |
| Speed | Relatively slower than traditional methods | High | Moderate |
| Cost | High initial investment and ongoing maintenance costs | Low | Low |
| Scalability | Currently limited by infrastructure requirements and distance limitations | Highly scalable | Highly scalable |
Security Aspects of Quantum-Secure Data Transmission
Toshiba and Orange’s collaboration on quantum-secure data transmission represents a significant leap forward in protecting sensitive information in the digital age. Traditional encryption methods, while effective, are vulnerable to increasingly powerful computational attacks, particularly from quantum computers. This new technology aims to address these vulnerabilities by leveraging the principles of quantum mechanics to achieve unparalleled security.Quantum key distribution (QKD) is the core of this enhanced security.
It utilizes the fundamental laws of quantum physics to generate and distribute encryption keys that are virtually impossible to intercept or compromise without detection. This makes the system significantly more resistant to the threats posed by both classical and quantum computing power.
Quantum Key Distribution (QKD) and Enhanced Security, Toshiba and orange offer quantum secure data transmission with utmost security
QKD leverages the properties of photons, the fundamental particles of light, to create a secure communication channel. The process involves encoding cryptographic keys onto individual photons, which are then transmitted between the communicating parties. Any attempt to intercept or measure these photons alters their quantum state, instantly alerting the sender and receiver to the presence of an eavesdropper. This “no-cloning theorem” of quantum mechanics, which prevents perfect copying of an unknown quantum state, forms the basis of QKD’s security.
The shared secret key, once verified as secure, is then used to encrypt the actual data transmitted via a classical channel. This two-step process ensures that even if the classical channel is compromised, the confidentiality of the data remains protected because the key itself is secure. This contrasts sharply with traditional methods where a compromised key renders the entire communication vulnerable.
For example, imagine a bank transferring funds; with QKD, the key used to encrypt the transaction details is inherently secure against eavesdropping, even by a sophisticated quantum computer.
Potential Vulnerabilities and Weaknesses
While QKD offers significantly enhanced security, it is not impervious to all attacks. One potential vulnerability lies in the imperfections of real-world quantum systems. Detectors may not be perfectly efficient, and imperfections in the photon sources can introduce loopholes that a sophisticated attacker might exploit. Side-channel attacks, which target information leaked through unintended channels like power consumption or electromagnetic radiation, also pose a threat.
Furthermore, the physical infrastructure required for QKD, such as fiber optic cables, can be susceptible to tampering or sabotage. A successful attack might involve manipulating the quantum signals or accessing the classical channel used for data transmission after the key exchange. The complexity of QKD systems also introduces potential vulnerabilities through software flaws or hardware malfunctions. Regular audits and rigorous testing are therefore essential to maintain the system’s integrity.
Hypothetical Attack Scenario and Mitigation
Imagine a scenario where an attacker attempts a “photon number splitting” attack. This involves splitting the incoming photons and measuring their polarization to gain partial information about the key. While QKD protocols are designed to detect such attacks, a highly sophisticated attacker might try to circumvent detection by carefully adjusting the splitting ratio or employing advanced signal processing techniques.
Mitigation strategies include employing decoy states, which are photons with known properties, interspersed within the key distribution process. By analyzing the detection rates of these decoy states, the legitimate parties can detect any attempt to split or measure the photons without revealing the actual key information. Another mitigation strategy would be to employ advanced error correction and privacy amplification techniques to further enhance the resilience of the system against such attacks.
Moreover, robust physical security measures, including secure facilities and regular inspection of the fiber optic cables, are crucial to prevent tampering and sabotage.
Practical Applications and Use Cases
The development of Toshiba and Orange’s quantum-secure data transmission technology represents a significant leap forward in data protection. Its ability to offer unparalleled security against future quantum computing threats opens doors to numerous practical applications across various sectors previously vulnerable to sophisticated cyberattacks. This technology isn’t just a theoretical advancement; it’s poised to revolutionize how sensitive information is handled and transmitted.The inherent security offered by quantum key distribution (QKD) makes it particularly valuable for industries handling highly sensitive data where breaches could have catastrophic consequences.
The impact on data security will be felt across the board, but certain sectors stand to gain the most immediate and substantial benefits.
Financial Sector Applications
The financial sector, with its constant flow of sensitive transactions and personal data, is a prime candidate for quantum-secure communication. Implementing QKD can protect against eavesdropping on high-value financial transactions, ensuring the integrity and confidentiality of sensitive data like customer accounts, trading information, and payment details. This technology could drastically reduce the risk of financial fraud and data breaches, leading to increased trust and confidence in online banking and financial services.
For example, a major international bank could use QKD to secure its high-frequency trading systems, ensuring the integrity and confidentiality of crucial market data. The resulting reduction in fraud and improved operational efficiency would represent a substantial return on investment.
Healthcare Data Protection
The healthcare industry handles vast quantities of extremely sensitive patient data, subject to stringent privacy regulations. Quantum-secure communication can protect patient medical records, genomic data, and other sensitive information transmitted between hospitals, clinics, and research institutions. This ensures compliance with regulations like HIPAA and GDPR, while also preventing unauthorized access to sensitive patient information. Consider the secure transmission of patient scans and medical records between a hospital and a remote diagnostic center.
QKD would guarantee the confidentiality and integrity of this data, protecting patient privacy and maintaining the highest standards of care.
Government and National Security
Government agencies and national security organizations deal with highly sensitive information requiring the utmost protection. Quantum-secure communication is crucial for protecting classified data, communications between government agencies, and sensitive infrastructure. The use of QKD can significantly enhance national security by preventing unauthorized access to critical information and safeguarding against sophisticated cyberattacks from state-sponsored actors or other malicious entities.
For instance, secure communication between government agencies involved in national defense could utilize QKD to prevent eavesdropping and ensure the integrity of strategic information.
Potential Use Cases: A Summary
The following list summarizes potential use cases, highlighting specific advantages:
- Secure Banking Transactions: Protecting against eavesdropping and ensuring the confidentiality of financial transactions.
- Healthcare Data Exchange: Securing patient data transmitted between hospitals and clinics, ensuring HIPAA and GDPR compliance.
- Government Communications: Protecting classified information and communication between government agencies.
- Critical Infrastructure Protection: Securing communication networks for power grids, transportation systems, and other vital infrastructure.
- Cloud Data Security: Protecting sensitive data stored in and transmitted to cloud environments.
- Supply Chain Security: Securing communication and data exchange throughout the supply chain, reducing the risk of counterfeiting and theft.
Technological Challenges and Future Developments
Quantum secure data transmission, while promising unparalleled security, faces significant technological hurdles before widespread adoption becomes a reality. The current state of the technology requires overcoming limitations in scalability, cost-effectiveness, and integration with existing infrastructure. Ongoing research focuses on addressing these challenges and paving the way for a future where quantum-secured communication is commonplace.
One of the primary challenges lies in the distance limitations of current quantum key distribution (QKD) systems. Photons, the carriers of quantum information, are susceptible to loss and noise during transmission, limiting the effective range of secure communication. This necessitates the use of quantum repeaters, a complex technology still under development, to extend the reach of QKD networks.
Another significant obstacle is the high cost associated with the specialized equipment needed for QKD, including single-photon detectors, lasers, and secure communication protocols. These costs currently restrict its use to high-security applications where the cost is justified by the need for absolute protection. Finally, seamlessly integrating QKD into existing telecommunication infrastructure presents a significant engineering challenge. This requires compatibility with current network protocols and standards, which often lack the features necessary for quantum-secured communication.
Quantum Repeater Development
Significant research efforts are underway to develop efficient and reliable quantum repeaters. These devices are crucial for extending the range of QKD systems beyond current limitations. Researchers are exploring various approaches, including using entangled photons and quantum memories to overcome the limitations of photon loss and noise during transmission. Successful development of quantum repeaters will be a pivotal moment in the widespread adoption of QKD technology.
For example, the European Union’s Quantum Flagship initiative is funding numerous projects focused on quantum repeater development, aiming to achieve significant breakthroughs within the next decade. Specific examples include research into novel materials for quantum memories and the development of advanced entanglement distribution protocols.
Cost Reduction Strategies
Reducing the cost of QKD systems is vital for broader adoption. This involves developing more cost-effective components, such as single-photon detectors and lasers, and simplifying the overall system design. Researchers are exploring new materials and manufacturing techniques to reduce the cost of these components. Furthermore, efforts are focused on developing more efficient and robust QKD protocols that require less complex and expensive equipment.
Progress in this area is expected to come from advancements in integrated photonics, which allows for the miniaturization and integration of various components onto a single chip. This will lead to smaller, more efficient, and potentially cheaper QKD systems. Several startups are already focusing on this area, aiming to make QKD commercially viable for a wider range of applications.
Integration with Existing Infrastructure
Seamless integration of QKD with existing telecommunication infrastructure is essential for large-scale deployment. This requires developing protocols and standards that are compatible with current network technologies while ensuring the security provided by QKD. Research focuses on adapting QKD to existing fiber optic networks and exploring methods for integrating it with other communication protocols. This involves creating hybrid systems that combine QKD with classical communication techniques to maximize efficiency and compatibility.
The standardization of QKD protocols and interfaces is crucial for interoperability and wider adoption. Several organizations, including the International Telecommunication Union (ITU), are working on developing such standards.
Projected Milestones
Predicting precise timelines for technological advancements is inherently challenging, but based on current research progress, a reasonable projection of milestones for quantum-secure data transmission can be made. These are estimations, subject to breakthroughs and unforeseen challenges.
| Milestone | Projected Timeline | Rationale |
|---|---|---|
| Significant improvements in quantum repeater technology, enabling QKD over distances exceeding 1000km. | 2028-2032 | Based on current research funding and progress in areas like quantum memory development. |
| Cost reduction of QKD systems, making them commercially viable for a wider range of applications (e.g., financial institutions, government agencies beyond high-security applications). | 2025-2030 | Driven by advancements in integrated photonics and the development of more efficient QKD protocols. |
| Widespread standardization of QKD protocols and interfaces, ensuring interoperability between different vendors and network providers. | 2025-2035 | Dependent on collaborative efforts from industry players and standardization bodies like the ITU. |
| Integration of QKD into mainstream telecommunication networks, enabling widespread adoption of quantum-secured communication. | 2030-2040 | This depends on the successful completion of the previous milestones and the acceptance of quantum-secured communication by the wider telecommunications industry. |
Economic and Societal Implications: Toshiba And Orange Offer Quantum Secure Data Transmission With Utmost Security
The widespread adoption of Toshiba and Orange’s quantum-secure data transmission technology promises a significant shift in the global economic and societal landscape. The implications are multifaceted, ranging from substantial economic benefits to the reshaping of data privacy regulations and the introduction of both opportunities and challenges for individuals and industries alike.The potential economic impact is substantial. Increased trust in data security, facilitated by quantum-resistant encryption, will likely boost cross-border e-commerce and international collaborations.
Industries heavily reliant on secure data transmission, such as finance, healthcare, and government, will see reduced costs associated with data breaches and increased operational efficiency. The development and deployment of this technology itself will create new jobs in research, development, manufacturing, and cybersecurity. However, the initial investment required for infrastructure upgrades could pose a short-term challenge for some organizations.
Data Privacy Regulation and Policy Influence
Quantum-secure data transmission will undoubtedly influence data privacy regulations and policies. Current encryption standards, vulnerable to attacks from future quantum computers, will need to be updated. This necessitates a global effort to standardize quantum-resistant cryptographic algorithms and to establish robust legal frameworks to govern their use. The increased security offered by this technology could lead to a reassessment of existing data protection laws, potentially leading to stricter regulations in some areas while relaxing them in others, depending on the specific risk-benefit assessment.
For example, industries that previously relied on heavy data masking might find reduced compliance burdens with the implementation of this technology.
Societal Benefits and Risks
The societal benefits of quantum-secure data transmission are significant. Enhanced data privacy will empower individuals and organizations to share sensitive information with greater confidence. This will facilitate advancements in areas such as telehealth, online banking, and secure voting systems. However, the technology also presents risks. The high cost of implementation could exacerbate the digital divide, creating disparities in access to secure communication.
Furthermore, the potential for misuse by state actors or malicious entities must be carefully considered and addressed through appropriate security protocols and regulations. The potential for increased surveillance, if not properly managed, also poses a risk to civil liberties.
Job Market and Economic Effects
The impact on the job market will be a complex interplay of job creation and displacement. While new jobs will be created in the quantum technology sector, there’s a potential for displacement in industries currently reliant on less secure technologies. The transition will require retraining and upskilling initiatives to ensure a smooth adaptation. The overall economic impact will depend on the speed and scale of adoption, as well as the effectiveness of policies designed to mitigate potential negative consequences.
The global economy stands to gain from increased efficiency and trust, but strategic planning and investment are crucial to maximize benefits and minimize disruptions.
The societal implications of quantum-secure data transmission are profound. While it promises enhanced data privacy and security, creating significant economic opportunities, careful consideration must be given to potential risks such as the digital divide, misuse by malicious actors, and the need for robust regulatory frameworks to ensure equitable access and prevent the erosion of civil liberties. Proactive policy measures are essential to navigate this technological shift successfully.
Illustrative Example: A Secure Financial Transaction

Imagine a high-value international wire transfer between a London-based bank and a New York-based client. This transaction, traditionally vulnerable to interception and manipulation, is now secured using Toshiba and Orange’s quantum-secure data transmission technology.This technology leverages the principles of quantum key distribution (QKD) to establish a virtually unbreakable encryption key. The security rests on the fundamental laws of quantum mechanics, specifically the Heisenberg Uncertainty Principle and the no-cloning theorem.
These principles guarantee that any attempt to intercept the key will inevitably alter it, alerting the sender and receiver to the intrusion.
Data Transmission Process
The transaction begins with the London bank generating a random sequence of photons, each representing a bit of the encryption key. These photons are then transmitted to the New York bank via a dedicated fiber optic cable (or potentially, a satellite link for longer distances). The photons’ polarization encodes the key bits. At the receiving end, the New York bank uses specialized quantum detectors to measure the polarization of each incoming photon, reconstructing the key.
Any attempt to intercept and measure the photons during transit would alter their polarization, causing discrepancies between the sender’s and receiver’s key versions, immediately revealing the breach. This process is repeated until a shared, secure key is established.
Data Integrity and Confidentiality
Once the secure key is established, the financial transaction data – including the amount, account numbers, and other sensitive information – is encrypted using a robust encryption algorithm, such as AES-256, with the shared quantum key. This ensures that even if the encrypted data is intercepted, it remains unreadable without the correct key. Furthermore, the quantum key distribution process itself provides authentication, verifying the identity of both the sender and receiver.
The system also includes error detection and correction mechanisms to ensure data integrity throughout the transmission. Any discrepancies detected during the key exchange or data transmission trigger an alert, preventing fraudulent transactions.
Transaction Completion
With the data securely encrypted and transmitted, the New York bank decrypts the message using the shared quantum key. The transaction is then processed, and confirmation is sent back to the London bank, also secured using the same quantum key. The entire process, from key generation to transaction confirmation, is logged and monitored to maintain a complete audit trail. The quantum-secured communication ensures the utmost confidentiality, integrity, and authenticity of the financial transaction.
Toshiba and Orange’s quantum-secure data transmission is a game-changer for security, offering unprecedented protection against future threats. This level of robust security is crucial for applications built using modern development techniques, like those discussed in this insightful article on domino app dev, the low-code and pro-code future , which explores how to build secure and scalable apps. Ultimately, advancements like Toshiba and Orange’s work ensure the data within these apps remains safe.
The use of quantum mechanics guarantees that the security is not based on computational complexity (as with traditional encryption) but on the fundamental laws of physics, providing unparalleled security against even future advancements in computing power.
Last Point
The partnership between Toshiba and Orange in developing quantum-secure data transmission marks a significant leap forward in cybersecurity. While challenges remain in terms of scalability and cost, the potential benefits for securing sensitive data across various sectors are undeniable. The future of data security looks brighter, thanks to the innovative application of quantum physics. It’s a thrilling time to witness this technology emerge, and I can’t wait to see what the future holds for quantum-secured communication!
Q&A
What are the limitations of this quantum-secure technology?
Current limitations include cost, distance constraints for QKD, and the need for specialized infrastructure. Scalability is also a factor that needs ongoing improvement.
How does this technology compare to blockchain for security?
Both offer enhanced security, but they operate differently. Blockchain relies on cryptography and distributed ledger technology, while QKD uses quantum mechanics to generate unbreakable keys. They could potentially complement each other.
Is this technology truly unhackable?
While incredibly secure, no system is completely unhackable. However, QKD’s reliance on the laws of physics makes it significantly more resistant to attacks than traditional methods. Ongoing research continually improves its robustness.





