Secure Domino with Certmgr & Lets Encrypt
Tutorial how to secure domino using certmgr task letsencrypt – Tutorial how to secure Domino using Certmgr task and Let’s Encrypt: Ever felt the chill of an insecure Domino server? This isn’t just about ticking security boxes; it’s about protecting your valuable data and maintaining user trust. We’ll navigate the sometimes-tricky world of SSL/TLS certificates, harnessing the power of Let’s Encrypt’s free certificates and the automation magic of Certmgr to secure your Domino environment.
Get ready to ditch those nagging security warnings and embrace a more robust, secure system.
This guide walks you through the entire process, from understanding the vulnerabilities of an unsecured Domino server to configuring automated certificate renewal using Certmgr. We’ll cover obtaining a Let’s Encrypt certificate, integrating it with your Domino server, and establishing a proactive security monitoring strategy. We’ll even tackle common troubleshooting issues, so you’ll be confident in managing your Domino security long-term.
Understanding Domino and its Security Needs
Domino servers, while powerful collaborative platforms, are vulnerable to various attacks if not properly secured. Leaving a Domino server exposed can lead to significant data breaches, service disruptions, and reputational damage. Understanding the inherent risks and implementing robust security measures is paramount for any organization relying on Domino for critical business functions.Domino’s security relies heavily on the proper configuration of its various components and the implementation of strong security protocols.
A lack of security can expose sensitive data, compromise application integrity, and even allow for complete server takeover by malicious actors.
Unsecured Domino Server Vulnerabilities
Unsecured Domino servers face a multitude of threats. These include unauthorized access to sensitive data, malware infections, denial-of-service attacks, and exploitation of known vulnerabilities in the Domino server software itself. Weak or default passwords, insufficient access controls, and a lack of regular security updates significantly increase the risk of successful attacks. For example, an attacker could exploit a known vulnerability to gain unauthorized access, potentially leading to data theft or the installation of ransomware.
Another scenario could involve a brute-force attack on weak passwords, granting an attacker complete control of the server. The consequences can range from minor inconveniences to catastrophic business disruptions.
The Importance of SSL/TLS Certificates for Domino Security
SSL/TLS certificates are fundamental for securing Domino server communications. They enable encrypted connections between the Domino server and clients, protecting sensitive data transmitted during sessions. Without SSL/TLS, all data exchanged between the server and clients, including passwords and confidential documents, is transmitted in plain text, making it easily accessible to eavesdroppers. Implementing SSL/TLS ensures data confidentiality, integrity, and authentication, providing a crucial layer of security against various attacks.
This is achieved through the use of encryption algorithms that scramble the data, making it unreadable without the appropriate decryption key.
Certificate Authority (CA) Comparison
Several Certificate Authorities (CAs) offer SSL/TLS certificates. Choosing a reputable CA is critical. Factors to consider include the CA’s reputation, the level of validation offered (e.g., Domain Validation, Organization Validation, Extended Validation), and the certificate’s lifespan. Well-known CAs like Let’s Encrypt (for free certificates), DigiCert, and Sectigo offer varying levels of trust and validation. Let’s Encrypt, while free, provides Domain Validation certificates, while others offer higher levels of validation with more rigorous verification processes.
The choice depends on the specific security needs and budget of the organization. For instance, a high-security environment might require an Extended Validation certificate from a well-established CA, while a smaller organization might opt for a Domain Validation certificate from Let’s Encrypt.
Best Practices for Securing Domino Applications
Securing Domino applications requires a multi-layered approach. This includes regularly updating the Domino server software and applying security patches to address known vulnerabilities. Implementing strong password policies, restricting access to the server and its applications based on the principle of least privilege, and regularly backing up data are crucial. Additionally, enabling auditing and logging capabilities allows for monitoring of server activity and detection of suspicious behavior.
Regular security assessments and penetration testing can identify potential weaknesses and vulnerabilities before they can be exploited by malicious actors. Furthermore, implementing robust access control lists (ACLs) to restrict access to specific databases and documents within the Domino environment is essential. Finally, educating users about security best practices, such as phishing awareness and password hygiene, is a vital aspect of overall security.
Introduction to Certmgr and Let’s Encrypt
Securing your Domino server with SSL/TLS certificates is crucial for protecting sensitive data and maintaining user trust. This section dives into the tools we’ll use to achieve this: the Certmgr task scheduler and the Let’s Encrypt certificate authority. We’ll explore their functionalities, advantages, and potential challenges in a Domino environment.Certmgr, short for Certificate Manager, is a powerful task scheduler built into Domino.
It automates the process of obtaining, installing, and renewing SSL/TLS certificates, freeing you from manual intervention and ensuring your server’s security remains up-to-date. Its capabilities extend beyond simple certificate installation; it can also handle certificate revocation and other related tasks. By scheduling these actions, Certmgr minimizes downtime and ensures continuous security.
Certmgr Task Scheduler Functionality
Certmgr’s primary function is to automate certificate lifecycle management. This includes obtaining certificates from a Certificate Authority (CA), installing them on the Domino server, and automatically renewing them before they expire. The scheduler allows you to define precise timings for these actions, ensuring seamless operation. Furthermore, it can be configured to handle various certificate types and configurations, offering a flexible and robust solution for managing SSL/TLS certificates within a Domino environment.
The ability to monitor certificate status and trigger alerts upon expiration or other critical events enhances its usefulness in proactive security management.
Advantages of Using Let’s Encrypt
Let’s Encrypt is a free, automated, and open certificate authority (CA). Its primary advantage is the cost savings; obtaining and renewing certificates is completely free. This contrasts sharply with commercial CAs, which often charge substantial fees, particularly for multi-year certificates or those with advanced features. Beyond the cost savings, Let’s Encrypt offers a streamlined and automated process, simplifying the task of certificate management, particularly beneficial for organizations with numerous servers.
The open nature of Let’s Encrypt also fosters trust and transparency within the community.
Comparison of Certmgr with Other Certificate Management Tools
While Certmgr provides robust certificate management within the Domino ecosystem, other tools exist for broader certificate management needs. Dedicated certificate management systems offer centralized control across various platforms and technologies, going beyond the scope of just Domino. These systems typically provide features such as automated certificate discovery, centralized key management, and comprehensive reporting and auditing capabilities. However, these tools often come with a higher price tag and may require more complex integration efforts compared to the native Certmgr solution within Domino.
The choice between Certmgr and a more comprehensive system depends on the organization’s specific needs and scale of operations.
Potential Challenges When Using Let’s Encrypt with Domino
While Let’s Encrypt offers significant advantages, certain challenges may arise when integrating it with Domino. One common challenge is the requirement for HTTP-01 or DNS-01 validation methods. HTTP-01 validation necessitates placing a verification file on the web server, which may require additional configuration and potentially expose the server to vulnerabilities if not properly secured. DNS-01 validation, while generally more secure, requires access to the DNS records for the domain, necessitating collaboration with the DNS administrator.
Furthermore, Let’s Encrypt certificates typically have a shorter validity period (90 days), requiring more frequent renewals compared to commercial certificates. This increased renewal frequency necessitates careful monitoring and configuration of the Certmgr task to ensure uninterrupted service. Proper planning and configuration are crucial to mitigate these challenges.
Obtaining a Let’s Encrypt Certificate: Tutorial How To Secure Domino Using Certmgr Task Letsencrypt
Let’s Encrypt is a fantastic free, automated, and open certificate authority (CA) that makes obtaining SSL/TLS certificates incredibly easy. We’ll leverage their ACME (Automatic Certificate Management Environment) protocol and DNS validation to secure our Domino server. This process avoids the complexities of manual certificate requests and simplifies the entire security workflow.This section details the process of obtaining a Let’s Encrypt certificate using the ACME protocol, specifically focusing on DNS validation.
We’ll then walk through generating a Certificate Signing Request (CSR) and finally installing the certificate within Domino.
DNS Validation for Let’s Encrypt
DNS validation is a common method Let’s Encrypt uses to verify your domain ownership. It works by requiring you to prove you control the DNS records for your domain. Let’s Encrypt will create a temporary DNS record (typically a TXT record) that you need to add to your DNS zone. Once Let’s Encrypt confirms the record’s presence, they’ll issue your certificate.
This method is preferred because it doesn’t require any software installation on your Domino server itself, reducing potential complications. The specific steps involved depend on your DNS provider, but the general principle remains the same. You’ll typically use your DNS provider’s control panel or command-line tools to add and later remove the validation record.
Generating a Certificate Signing Request (CSR)
Before requesting a certificate from Let’s Encrypt, you need to generate a Certificate Signing Request (CSR). This CSR contains information about your organization and your Domino server’s public key. This is a crucial step as it ties your identity to the certificate. Domino’s own tools can generate this CSR, ensuring compatibility. The CSR includes information such as your common name (typically your server’s fully qualified domain name), your organization’s details, and your location.
This information will appear within the certificate itself. Incorrect information here can lead to certificate validation problems. Ensure accuracy.
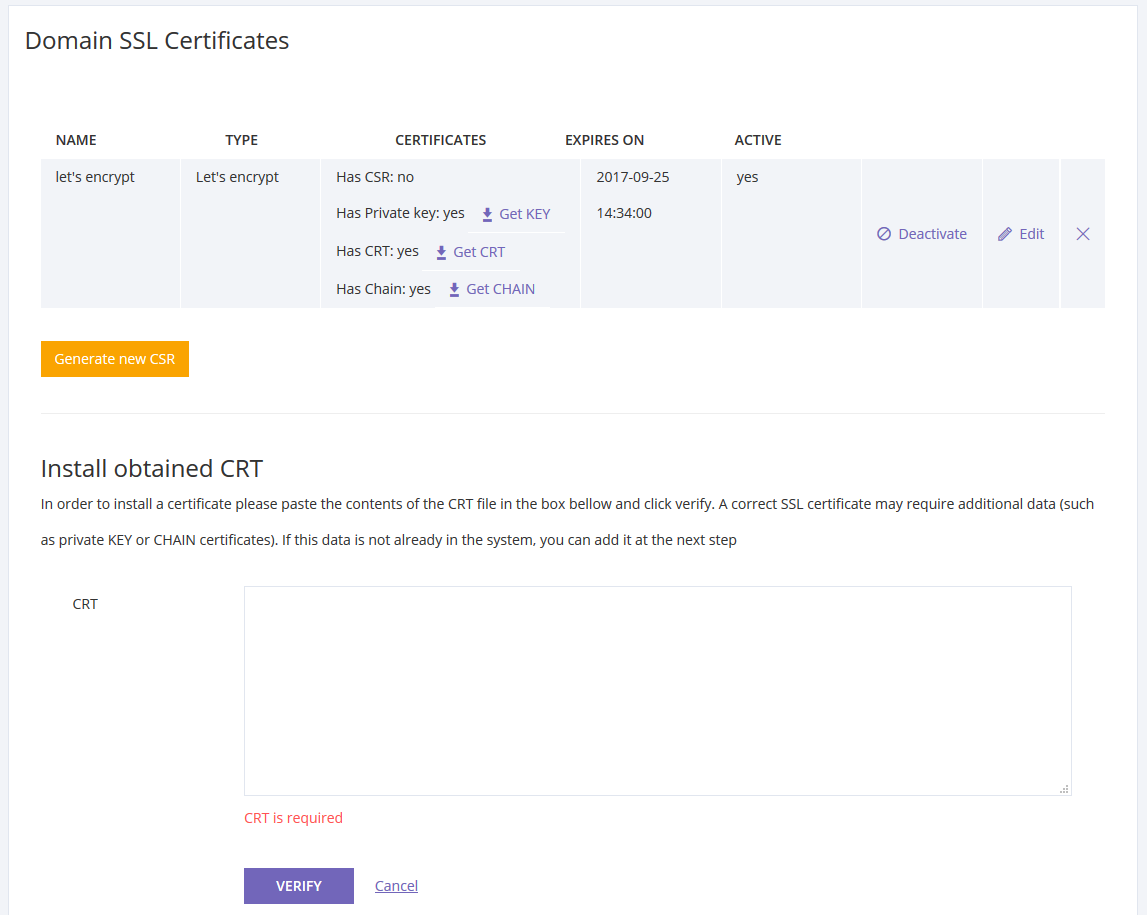
Installing the Let’s Encrypt Certificate in Domino, Tutorial how to secure domino using certmgr task letsencrypt
Once you’ve obtained your certificate and its private key from Let’s Encrypt, the final step is installing them into your Domino server. This involves importing the certificate into the Domino server’s certificate store. Domino provides a straightforward interface for managing certificates, allowing you to import the certificate chain (including intermediate and root certificates). Remember, you need both the certificate file (.crt or .pem) and the private key file (.key or .pem).
Improper installation can lead to SSL/TLS errors. Double-check your settings and paths before proceeding. After installation, restart your Domino server to ensure the changes take effect. You should then be able to access your Domino server securely using HTTPS.
Integrating Let’s Encrypt with Certmgr for Automated Renewal
Automating the renewal of your Let’s Encrypt certificates is crucial for maintaining the security of your Domino server. Manual renewal is tedious and prone to error, potentially leaving your server vulnerable. Using Certmgr, Domino’s built-in certificate management tool, allows for seamless integration with Let’s Encrypt’s automated renewal process, ensuring your certificates are always up-to-date. This section will guide you through the configuration process.
Designing a Certmgr Task for Automated Renewal
A Certmgr task needs to be carefully designed to execute the Let’s Encrypt renewal script correctly. This involves specifying the correct script location, any necessary parameters, and ensuring the task has the appropriate permissions to access the necessary files and directories. The task should be configured to run regularly, ideally before the certificate’s expiration date to avoid any service disruptions.
Failure to properly configure the task can result in certificate expiration and potential security breaches.
Organizing the Task Schedule for Optimal Certificate Renewal
Scheduling the Certmgr task is vital for successful automated renewal. The frequency should be less than the certificate’s validity period (typically 90 days for Let’s Encrypt certificates), allowing for ample time before expiration. A common approach is to schedule the task to run weekly or bi-weekly. Consider scheduling the task during off-peak hours to minimize any potential impact on server performance.
For example, scheduling the task at 3 AM on a Wednesday would ensure renewal occurs outside of typical business hours. The exact schedule will depend on your server’s usage patterns and operational requirements. It is important to test the task after scheduling to confirm it functions as expected.
Configuring the Certmgr Task to Handle Certificate Renewal
The configuration of the Certmgr task involves specifying the command line to execute the Let’s Encrypt client (certbot or similar) and providing any necessary parameters. This includes the domain name(s) for which the certificate is issued and potentially the path to a configuration file. The task must be configured to run under a user account with sufficient privileges to execute the Let’s Encrypt client and manage the Domino certificate store.
The command might look something like this (replace placeholders with your actual values): "C:\Program Files\Certbot\certbot-auto renew --non-interactive --agree-tos --post-hook \"C:\path\to\your\domino\script.bat\"". The post-hook script is crucial; it handles the import of the renewed certificate into the Domino server’s certificate store. This script would typically use the `certmgr` command-line tool to import the new certificate.
Troubleshooting Common Issues During Automated Renewal
Several issues can arise during automated renewal. One common problem is insufficient permissions. Ensure the user account running the Certmgr task has the necessary permissions to access the Let’s Encrypt client, the Domino certificate store, and any relevant directories. Another common issue is incorrect path specifications in the Certmgr task’s command line. Verify all paths are accurate and point to the correct files and directories.
Network connectivity problems can also prevent renewal; ensure the server has reliable internet access. Finally, problems with the Let’s Encrypt client itself might occur. Check the client’s logs for any errors that may indicate configuration issues or challenges with the Let’s Encrypt servers. Regularly reviewing the task logs will aid in early detection and resolution of problems.
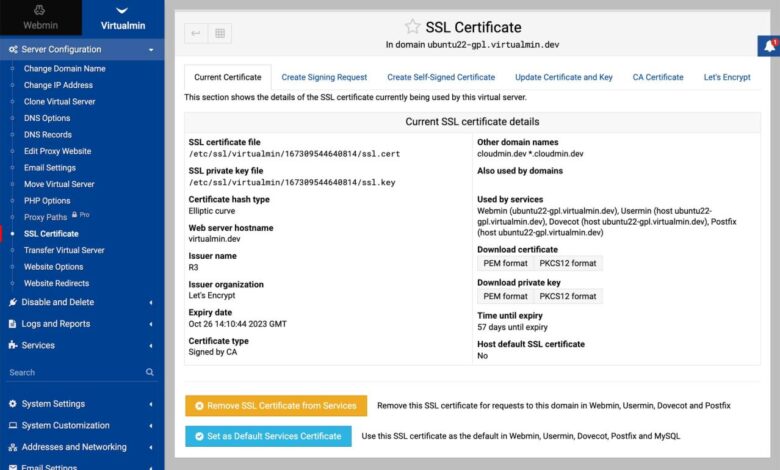
Securing Domino using the Obtained Certificate
Now that we’ve successfully obtained a Let’s Encrypt certificate using Certmgr, it’s time to integrate it into our Domino server to secure our applications and data. This process involves configuring Domino to recognize and utilize the new certificate, enabling SSL/TLS on the appropriate ports, and potentially setting up client authentication for enhanced security. Let’s walk through the steps.
Domino Server Configuration for Let’s Encrypt Certificate
The core of securing Domino involves configuring the server to trust and use the newly acquired Let’s Encrypt certificate. This typically involves importing the certificate into the Domino server’s keystore and then associating it with the relevant Domino services (like HTTP and HTTPS). The exact steps may vary slightly depending on your Domino version, but generally involve using the Domino Administrator client to manage certificates.
You’ll need to navigate to the server’s certificate management section, import the certificate chain (including the certificate and any intermediate certificates), and then assign it to the appropriate Domino services. Remember to restart the server after making these changes for the configuration to take effect. Failure to restart the server will prevent the changes from being applied.
Enabling SSL/TLS on Domino HTTP and HTTPS Ports
Enabling SSL/TLS on your Domino server’s HTTP and HTTPS ports ensures that all communication is encrypted. This is crucial for protecting sensitive data transmitted between clients and the Domino server. Within the Domino Administrator, you’ll find settings to enable SSL for both HTTP and HTTPS ports. This typically involves selecting the appropriate certificate from the keystore (the Let’s Encrypt certificate we just imported) and specifying the ports to be secured.
You might need to configure specific server tasks or services to use the secured ports, depending on your Domino setup. For instance, you’ll likely need to configure your web server to listen on the HTTPS port and redirect HTTP traffic to HTTPS.
Configuring Client Authentication
Client authentication adds an extra layer of security by verifying the identity of clients connecting to your Domino server. This prevents unauthorized access and strengthens overall security. Domino allows for configuring client authentication using certificates. You can require clients to present a valid certificate before granting access to specific resources or functionalities. This involves setting up the appropriate authentication settings within the Domino Administrator, specifying which certificates are accepted and how authentication is handled (e.g., mutual authentication).
Proper configuration ensures only authorized clients can access the Domino server’s resources. It’s important to carefully plan and manage client certificates to avoid hindering legitimate users.
Best Practices for Securing Domino’s Web Server
Beyond the basic certificate integration, several best practices should be implemented to maximize the security of your Domino web server. These include regularly updating the Domino server software and all related components to patch security vulnerabilities. Furthermore, implementing strong password policies for all Domino user accounts and administrative accounts is essential. Regular security audits and penetration testing can identify and address potential weaknesses in your security posture.
Finally, consider using a web application firewall (WAF) to protect against common web attacks such as SQL injection and cross-site scripting (XSS). These measures collectively contribute to a robust and secure Domino environment.
Monitoring and Maintaining Domino Security
Securing your Domino environment with Let’s Encrypt certificates via Certmgr is a significant step, but ongoing monitoring and maintenance are crucial for sustained security. This section Artikels best practices for ensuring your certificates remain valid and your Domino server remains protected. Regular checks and proactive strategies are key to preventing security issues and ensuring business continuity.
Certificate Validity and Renewal Monitoring
Regular monitoring of certificate validity and renewal status is paramount. Overlooking this can lead to service disruptions and security vulnerabilities. A proactive approach is essential.
The following checklist provides a framework for effective monitoring:
- Daily Check: Implement a daily automated script or task to check the validity period of all Domino server certificates. This script should alert administrators via email or other notification systems if a certificate is nearing expiry (e.g., within 30 days).
- Weekly Review: Conduct a weekly manual review of the certificate status, checking for any warnings or errors reported by the Certmgr task. This allows for human oversight and the identification of potential problems not caught by automated checks.
- Monthly Audit: Perform a more thorough monthly audit of all certificates, including verifying the certificate chain, checking for revocation status, and reviewing the certificate’s subject and issuer information to ensure they match expectations.
- Log Monitoring: Regularly review the Certmgr and Domino server logs for any errors or warnings related to certificate management. This provides valuable insights into potential issues and facilitates timely intervention.
Handling Certificate Renewal Failures
Even with automated renewal, failures can occur. Having a robust strategy in place to handle these failures is vital to minimizing downtime and maintaining security.
A multi-layered approach is recommended:
- Automated Retries: Configure Certmgr to automatically retry certificate renewal a set number of times in case of temporary failures. This can handle transient network issues or temporary problems with the Let’s Encrypt servers.
- Alerting System: Implement a comprehensive alerting system that notifies administrators immediately of any certificate renewal failures. This allows for prompt investigation and resolution of the problem.
- Manual Intervention Procedure: Establish a clear procedure for manual intervention in case automated retries fail. This procedure should include steps for troubleshooting the issue, obtaining a new certificate manually if necessary, and updating the Domino server with the new certificate.
- Backup and Recovery: Regularly back up your Domino server’s configuration and certificates. This allows for quick recovery in the event of a catastrophic failure or data loss.
Domino Server Security Auditing
Regular security audits are essential for identifying vulnerabilities and ensuring the ongoing security of your Domino environment.
A comprehensive security audit should include:
- Access Control Reviews: Regularly review and update access control lists (ACLs) for all Domino databases and applications to ensure only authorized users have access.
- Security Setting Verification: Verify that all relevant Domino security settings are properly configured and up-to-date, including authentication methods, encryption settings, and firewall rules.
- Vulnerability Scanning: Conduct regular vulnerability scans of your Domino servers to identify and address any known security weaknesses. Tools like Nessus or OpenVAS can be used for this purpose.
- Log Analysis: Analyze Domino server logs to detect suspicious activity, such as unauthorized access attempts or unusual data access patterns. This can help identify potential security breaches before they cause significant damage.
Detecting and Responding to Security Breaches
While preventative measures are crucial, having a plan for responding to security breaches is equally important.
Effective breach response involves:
- Incident Response Plan: Develop a comprehensive incident response plan that Artikels steps for detecting, containing, eradicating, recovering from, and learning from security breaches. This plan should include roles and responsibilities for each team member.
- Security Information and Event Management (SIEM): Implement a SIEM system to collect and analyze security logs from various sources, including Domino servers, firewalls, and other network devices. This can help identify suspicious activity and provide early warning of potential breaches.
- Intrusion Detection System (IDS): Deploy an IDS to monitor network traffic for malicious activity and alert administrators to potential intrusions. This can provide an additional layer of security and help detect attacks that might otherwise go unnoticed.
- Forensic Analysis: In the event of a confirmed breach, conduct a thorough forensic analysis to determine the extent of the compromise, identify the attacker’s methods, and recover any compromised data.
Illustrative Examples
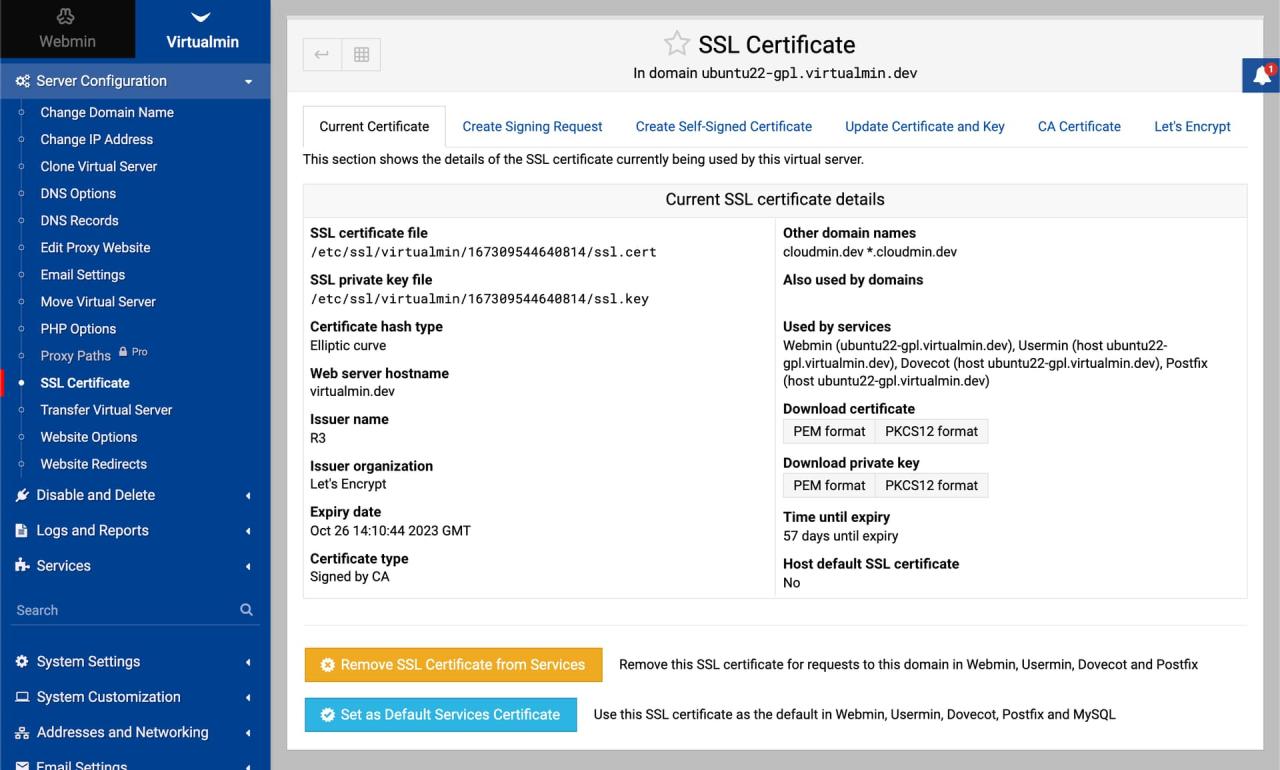
Let’s walk through a practical example of renewing your Let’s Encrypt certificate for your Domino server using Certmgr. This process is crucial for maintaining the security of your Domino environment and ensuring uninterrupted email and application access. Successful renewal hinges on properly configuring Certmgr and ensuring your Domino server can communicate with the Let’s Encrypt servers.
The following table details the steps involved in a typical Let’s Encrypt certificate renewal using Certmgr. Remember that the exact steps might vary slightly depending on your specific Certmgr configuration and Domino environment. Always consult the official documentation for both Certmgr and Let’s Encrypt for the most up-to-date instructions.
Certificate Renewal Process Using Certmgr
| Step | Action | Expected Result | Troubleshooting |
|---|---|---|---|
| 1 | Verify Certmgr is properly configured and scheduled to run the renewal task. Check the Certmgr log files for any errors. | Certmgr shows the next scheduled renewal date and no errors in the logs. | Review the Certmgr configuration files. Check for sufficient permissions. Ensure the Domino server can access the internet. Examine Certmgr log files for error messages and consult the Let’s Encrypt documentation for common issues. |
| 2 | Wait for the scheduled renewal task to execute. This usually occurs automatically based on the certificate’s expiration date. | Certmgr initiates the renewal process. The process should run silently in the background, without any user interaction required. | If the renewal doesn’t happen automatically, manually run the Certmgr task. Check the system scheduler/task manager to ensure the task is enabled and running correctly. |
| 3 | Check the Certmgr log files after the scheduled time for successful renewal confirmation. | The log files should show a successful certificate renewal, including the new certificate’s validity period. | Examine the log files for error messages. Common issues include DNS propagation delays, network connectivity problems, or incorrect Certmgr configuration. Consult the Let’s Encrypt documentation for detailed troubleshooting. |
| 4 | Verify the renewed certificate is installed and being used by Domino. Check the Domino server’s certificate details in the Domino Administrator. | The Domino server shows the renewed certificate with an updated expiration date. | If the Domino server is not using the renewed certificate, restart the Domino server. If the problem persists, check the Domino server’s configuration files to ensure it’s pointing to the correct certificate location. Consider reviewing the Certmgr and Domino server logs for further clues. |
Illustrative Examples
This section details the crucial Domino server configuration settings required to successfully implement the Let’s Encrypt certificate obtained via the Certmgr task. Proper configuration ensures seamless integration and secure communication. Remember to consult your Domino server’s documentation for specific version-related details.
Domino Server Configuration for Let’s Encrypt Certificate
The following points Artikel the essential server-side configurations needed to leverage your Let’s Encrypt certificate. These settings cover crucial aspects such as ports, protocols, and authentication, ensuring your Domino server is securely configured. Incorrect settings can lead to connection failures or security vulnerabilities.
- HTTP Port (80): This port is essential during the Let’s Encrypt certificate acquisition process. The Certmgr task uses this port to verify domain control. Ensure that your Domino server is accessible on this port, either directly or via a reverse proxy. Firewall rules must permit inbound traffic on port 80 during the certificate acquisition process. After certificate acquisition, you can disable this port if desired.
- HTTPS Port (443): This port is used for secure communication after the Let’s Encrypt certificate is installed. Domino must be configured to listen on this port and serve content securely. Firewall rules should permit inbound traffic on port 443.
- Certificate Location: Specify the location where the Let’s Encrypt certificate files (certificate.crt and privatekey.key) are stored on the Domino server. This path should be accessible to the Domino server process. The Certmgr task will typically place the files in a designated directory.
- Server Document: The server document within the Domino Directory needs to be configured to use the newly obtained certificate. This involves specifying the certificate and key file paths in the server document’s “Internet Protocols” section. The specific location of this setting may vary slightly depending on your Domino version.
- Protocols: Ensure that the server document is configured to use the HTTPS protocol. This is typically done by enabling the “Secure (HTTPS)” option within the Internet Protocols settings of the server document. The HTTP protocol may be disabled or left enabled for backwards compatibility, but this is not recommended after certificate installation.
- Authentication Settings: Depending on your security requirements, you may need to configure various authentication mechanisms. This could include SSL client authentication (requiring clients to present their own certificates), basic authentication, or other methods. The specifics depend on your Domino application and security policies.
Example Server Document Configuration (Illustrative)
While the exact interface varies slightly between Domino versions, the core configuration remains consistent. The following illustrates the crucial settings within the Server document’s Internet Protocols tab. Remember to replace placeholders with your actual paths.
- Secure (HTTPS): Enabled
- HTTPS Port: 443
- Certificate File: /path/to/your/certificate.crt
- Private Key File: /path/to/your/privatekey.key
Illustrative Example: Certificate Installation Failure
During the process of securing your Domino server with a Let’s Encrypt certificate managed by Certmgr, several issues can arise that prevent successful installation. Understanding these potential problems and their solutions is crucial for maintaining a secure and functional system. This example will detail a common scenario and provide a step-by-step troubleshooting guide.Let’s imagine a scenario where the Certmgr task successfully obtains the Let’s Encrypt certificate but fails to install it on the Domino server.
The Domino server log shows an error indicating a problem with the certificate chain or a mismatch in the certificate’s common name (CN) and the server’s hostname. This often happens due to configuration discrepancies or incomplete certificate chain information.
Troubleshooting Certificate Installation Failures
The following steps Artikel a methodical approach to resolving certificate installation failures. Careful attention to detail is crucial during this process.
- Verify Certificate Chain Completeness: Ensure the certificate chain provided by Let’s Encrypt includes all intermediate certificates and the root certificate. A missing intermediate certificate will lead to the Domino server rejecting the certificate. Check the certificate file provided by Let’s Encrypt – it should include the certificate itself, followed by the intermediate certificates, then the root certificate. If any are missing, download them from the Let’s Encrypt website or your certificate authority and append them to the chain before reattempting installation.
- Examine Domino Server Logs for Specific Errors: The Domino server logs provide invaluable clues about the nature of the failure. Search for error messages related to certificate installation, focusing on s such as “certificate chain,” “CN mismatch,” “invalid certificate,” or “SSL error.” These messages will pinpoint the precise cause of the problem.
- Check Hostname and Certificate Common Name (CN): A common cause of installation failure is a mismatch between the server’s hostname (as used in the Domino server configuration) and the Common Name (CN) specified in the Let’s Encrypt certificate. Verify both are identical, including case sensitivity. Incorrect configuration of the server’s hostname in the Domino administration interface or DNS can cause this issue. Correct any discrepancies found.
- Review Certmgr Task Configuration: Ensure the Certmgr task is correctly configured to point to the correct certificate file and Domino server. Double-check the paths to the certificate files, the Domino server’s hostname or IP address, and any other relevant settings within the Certmgr task configuration. A typographical error in any of these settings could prevent successful installation.
- Restart Domino Server and Certmgr Task: After making any changes to the configuration, restart both the Domino server and the Certmgr task. This ensures the changes take effect and the system is refreshed. Observe the Domino server logs to see if the certificate installation was successful after the restart.
- Examine Domino Server’s Certificate Store: After a restart, manually check the Domino server’s certificate store to see if the certificate has been successfully installed. Look for the certificate in the relevant location within the Domino administration interface. If the certificate is present but still causing issues, you might need to remove it and repeat the installation process.
Example Error Message: “The certificate chain is incomplete or contains a certificate that is not trusted.” This error clearly indicates a missing intermediate or root certificate in the certificate chain.
Final Thoughts
Securing your Domino server with Let’s Encrypt and Certmgr isn’t just about compliance; it’s a foundational step towards building a resilient and trustworthy digital environment. By automating certificate renewal and proactively monitoring your security posture, you’ll significantly reduce the risk of vulnerabilities and ensure your Domino server remains a safe and reliable asset. So, take the plunge, implement these steps, and enjoy the peace of mind that comes with a well-protected Domino system!
Detailed FAQs
What if my DNS provider doesn’t support Let’s Encrypt’s DNS validation?
You might need to explore alternative validation methods, such as HTTP-01, which involves placing a file on your webserver. However, this requires your webserver to be accessible from the internet, which may not always be desirable.
How often should I check my certificate status?
While automated renewal handles most of the work, it’s good practice to periodically (e.g., weekly or monthly) check your certificate’s expiration date and ensure the renewal process is functioning correctly.
Can I use Certmgr with other certificate authorities besides Let’s Encrypt?
While this guide focuses on Let’s Encrypt, Certmgr is a flexible tool and can be adapted to manage certificates from other CAs. You’ll need to adjust the configuration accordingly to reflect the specific requirements of your chosen CA.
What happens if the automated renewal fails?
Certmgr can be configured to send email notifications upon failure. You should have a plan in place to manually renew the certificate if automation fails, and investigate the cause of the failure to prevent future issues.
