UK Says No to Ransom Passwords Admin 123456 & Qwerty
Uk says no to ransom passwords such as admin 123456 and qwerty – UK Says No to Ransom Passwords: Admin 123456 & Qwerty – that’s the headline, and it’s a pretty serious one. We’ve all seen those headlines about massive data breaches, and often, the culprit is shockingly simple: laughably weak passwords. This isn’t just about annoying pop-ups telling you to use a stronger password; it’s about protecting your personal information, your business, and frankly, the whole internet.
Let’s dive into why the UK government is cracking down on passwords like “admin 123456” and “qwerty” and what you can do to protect yourself.
The UK government is taking a firm stance against the use of easily guessable passwords, citing the significant security risks they pose. These weak passwords are incredibly vulnerable to hacking, leading to data breaches, identity theft, and financial losses. The government’s rationale is clear: strong passwords are a fundamental element of cybersecurity, and failing to use them is simply irresponsible.
The consequences can range from personal inconvenience to catastrophic financial damage for businesses. We’ll look at real-world examples of how these weak passwords have led to devastating consequences.
The UK Government’s Stance on Weak Passwords
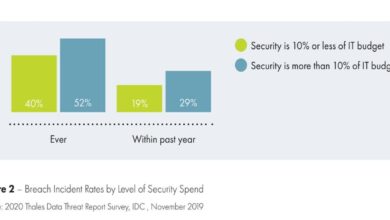
The UK government actively discourages the use of easily guessable passwords, emphasizing the critical need for robust online security. This stance isn’t just a recommendation; it’s a reflection of the significant risks posed by weak passwords to individuals and the nation’s digital infrastructure. The government’s position is driven by a commitment to protecting citizens and businesses from cyber threats.The use of passwords like “admin 123456” or “qwerty” exposes individuals and organizations to a wide range of cyberattacks.
These passwords are easily cracked by automated tools and readily available on lists of commonly used credentials. Successful attacks can lead to identity theft, financial loss, data breaches, and reputational damage. For organizations, the consequences can be far-reaching, including hefty fines for non-compliance with data protection regulations like GDPR, loss of customer trust, and disruption to operations.
Rationale Behind the Government’s Disapproval
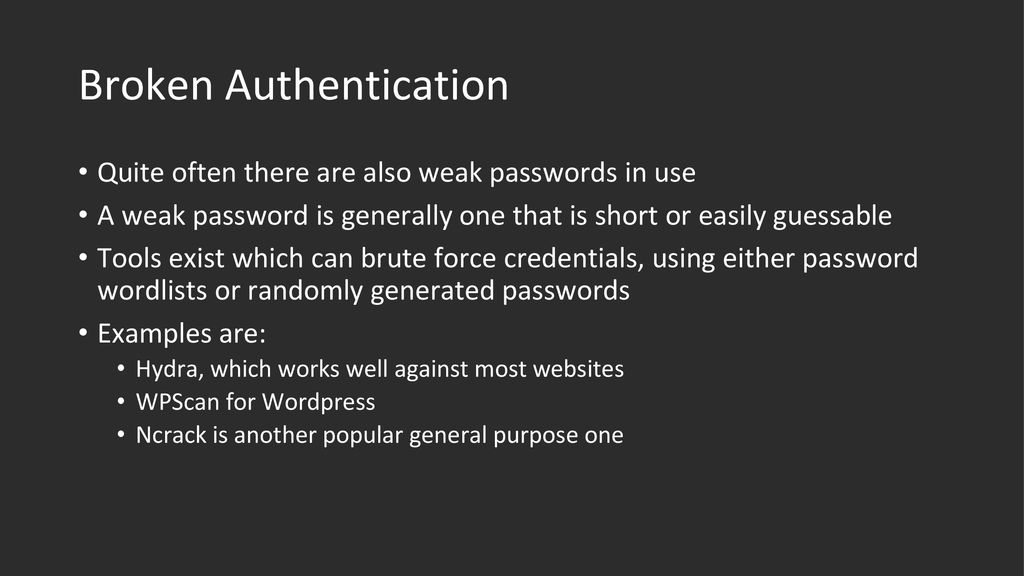
The government’s disapproval stems from the inherent vulnerabilities associated with weak passwords. These passwords offer minimal protection against sophisticated cyberattacks and brute-force methods. The ease with which these passwords can be guessed or cracked makes them a prime target for malicious actors seeking to gain unauthorized access to sensitive information. This is further compounded by the widespread reuse of passwords across multiple online accounts.
A single compromised weak password can provide access to a cascade of sensitive data.
Examples of Security Breaches Attributed to Weak Passwords
Numerous high-profile security breaches have been directly attributed to the use of weak passwords. While specific details are often kept confidential for security reasons, publicly available reports consistently highlight the prevalence of weak passwords as a contributing factor. For instance, the 2017 Equifax breach, which exposed the personal data of millions of individuals, was partially attributed to the exploitation of a vulnerable web application that had a weak password.
Similarly, countless smaller-scale attacks on businesses and individuals are routinely traced back to the use of easily guessable credentials. The sheer volume of data breaches linked to weak passwords underscores the critical need for improved password hygiene and security practices.
The Prevalence of Weak Passwords
The pervasiveness of weak passwords in the UK is a significant cybersecurity concern, contributing to a large number of successful breaches and data thefts. While precise, publicly available statistics specific to UK password weaknesses across all platforms are limited due to privacy concerns and the proprietary nature of data held by companies, available research paints a concerning picture.
The problem isn’t just about the sheer number of weak passwords; it’s also about the patterns and predictable nature of those choices.It’s difficult to pinpoint exact figures for the UK alone, but global studies provide a strong indication of the scale of the problem. Research consistently shows that a substantial portion of online users employ easily guessable passwords.
This is mirrored in anecdotal evidence from security breaches, where a significant proportion of compromised accounts are attributable to weak password choices. The implications are severe, leading to identity theft, financial loss, and damage to reputation.
Common Patterns and Trends in Weak Password Choices
Common weak password choices frequently involve easily guessable sequences, such as “password123,” “qwerty,” or variations on names and dates. Many users rely on simple numerical sequences or easily derived personal information like birthdays or pet names. The trend towards using the same password across multiple accounts significantly exacerbates the risk. If one account is compromised using a weak password, the attacker gains access to potentially all the user’s other accounts using that same password.
This highlights the critical need for unique and strong passwords for each online service.
Psychological Factors Contributing to Predictable Password Choices
Several psychological factors contribute to the widespread use of weak passwords. Convenience is a primary driver. Users often prioritize ease of remembering over security, opting for simple, easily recalled passwords. This is compounded by password fatigue—the frustration associated with managing numerous unique and complex passwords across multiple accounts. Cognitive biases also play a role; users may overestimate their ability to create strong passwords or underestimate the likelihood of a successful attack.
The complexity of strong password requirements can also feel overwhelming, leading users to opt for simpler, less secure options.
The UK’s crackdown on weak passwords like “admin123456” is a great step, but it highlights the need for robust security in all systems. This is especially true when you consider the rapid development happening in application building, as seen in the exciting advancements described in this article on domino app dev the low code and pro code future.
Strong password policies are just one piece of the puzzle; secure app development practices are equally vital to preventing breaches and keeping those weak passwords out of the equation.
Comparison of Security Risks: Weak vs. Strong Passwords
| Password Type | Cracking Difficulty | Vulnerability to Attacks | Mitigation Strategies |
|---|---|---|---|
| Weak Password (e.g., “password123”) | Very Low; easily cracked using brute-force or dictionary attacks. | Extremely High; susceptible to various attacks, including phishing and credential stuffing. | Use a password manager, employ strong and unique passwords, enable multi-factor authentication (MFA). |
| Strong, Unique Password (e.g., complex alphanumeric string with symbols) | Very High; resistant to brute-force and dictionary attacks. | Low; significantly reduces the risk of successful attacks. | Regularly update passwords, use a password manager to generate and store strong passwords, enable MFA. |
Security Measures to Prevent Weak Password Usage
So, we’ve established that weak passwords are a major security risk. But how do we actually stop people from using them? It’s a multi-pronged approach, requiring technological solutions and a hefty dose of user education. Let’s delve into the practical steps organizations can take to bolster password security.
The fight against weak passwords isn’t just about technology; it’s about changing behaviour. A layered approach combining technical controls with robust training is the most effective strategy. This ensures that even if one layer fails, others are in place to mitigate the risk.
Password Strength Meters and Complexity Rules
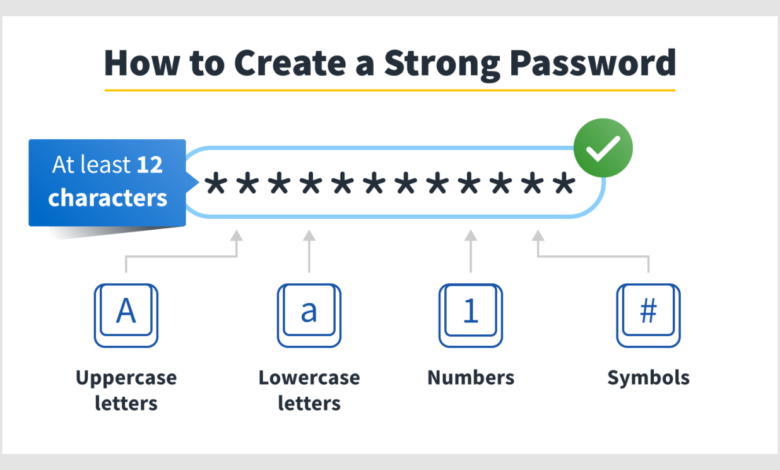
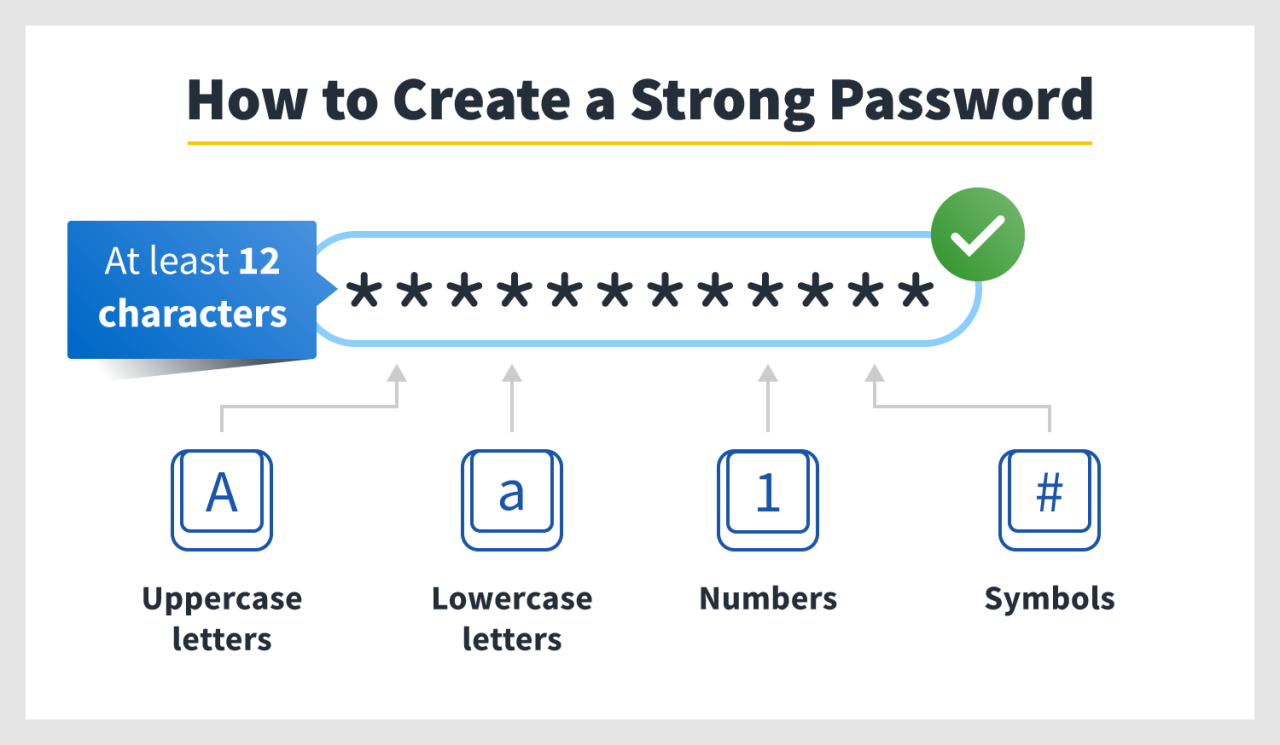
Password strength meters provide immediate feedback to users as they create a password. These tools analyze the password’s length, character variety (uppercase, lowercase, numbers, symbols), and check against common password lists. A strong password typically scores high on these metrics. Enforced password complexity rules go a step further, setting minimum requirements that passwords must meet before they’re accepted.
For example, a policy might mandate a minimum length of 12 characters, including at least one uppercase letter, one lowercase letter, one number, and one special character. While these measures can be effective in deterring the use of simple passwords, they’re not foolproof; determined attackers can still crack complex passwords through brute-force attacks or other methods.
Password Management Techniques
Password managers are software applications that securely store and manage users’ passwords. They generate strong, unique passwords for each account and automatically fill in login credentials, eliminating the need for users to remember numerous complex passwords. This dramatically reduces the risk of password reuse, a common vulnerability. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before granting access.
This could involve something they know (password), something they have (phone, security token), or something they are (biometric scan). MFA significantly increases the difficulty for attackers to gain unauthorized access, even if they obtain a password. For example, even if a hacker obtains your password through phishing, they’ll still need access to your phone to complete the authentication process.
Security Awareness Training Programs
Security awareness training programs play a crucial role in educating users about password security best practices. These programs typically involve interactive modules, videos, and quizzes that cover topics such as password complexity, phishing awareness, and the importance of MFA. Regular training sessions and simulated phishing attacks can reinforce good habits and help users identify and avoid potential threats. Effective training goes beyond simply providing information; it aims to change user behavior and create a security-conscious culture within the organization.
Regular refresher courses are vital to ensure that knowledge remains current and practices remain effective.
Best Practices for Creating Strong Passwords
Creating strong, memorable passwords is a balancing act. Here’s a list of best practices:
Creating strong and memorable passwords is essential for personal and organizational security. These passwords should be unique to each account and difficult to guess, but also easy for the user to remember. Avoid common patterns and leverage password managers to aid in this process.
- Use a password manager to generate and store your passwords.
- Create passwords that are at least 12 characters long.
- Include a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoid using personal information (birthdays, names, etc.) in your passwords.
- Don’t reuse passwords across different accounts.
- Regularly update your passwords, especially for sensitive accounts.
- Use a passphrase, a longer, more memorable phrase that incorporates random words.
The Role of Technology in Combating Weak Passwords
The fight against weak passwords isn’t just about educating users; it’s also about leveraging technology to make stronger password practices easier and more effective. This involves a multi-pronged approach, from sophisticated encryption techniques to innovative authentication methods. By understanding and implementing these technological solutions, we can significantly improve online security for everyone.Password hashing and salting are fundamental techniques that drastically improve password security.
They transform easily guessable passwords into complex, one-way encrypted strings, making them virtually impossible to reverse engineer even if a database is compromised.
Password Hashing and Salting
Hashing algorithms take a password as input and produce a unique, fixed-size string of characters, the hash. Even a tiny change in the password results in a completely different hash. Salting adds a random string of characters to the passwordbefore* hashing. This means that even if two users choose the same password, the resulting hashes will be different because of the unique salt added to each.
This prevents attackers from using pre-computed tables of common password hashes (rainbow tables) to crack passwords. For example, the bcrypt algorithm is a widely used and robust hashing algorithm incorporating salting. It’s computationally expensive, making brute-force attacks significantly harder.
Automated Password Checking Tools
Automated password checking tools play a crucial role in preventing weak passwords from being used. These tools, often integrated into password management software or web forms, instantly analyze passwords as they are entered, checking them against lists of common passwords, easily guessable variations, and known compromised passwords. They provide immediate feedback to users, suggesting stronger alternatives and highlighting potential vulnerabilities.
For instance, a tool might flag “password123” as weak and suggest a more secure combination of uppercase, lowercase, numbers, and symbols. This real-time feedback significantly improves user awareness and reduces the risk of weak passwords entering systems.
Comparison of Password Security Protocols, Uk says no to ransom passwords such as admin 123456 and qwerty
Different online services employ various password security protocols, with varying levels of robustness. Some services might use older, less secure hashing algorithms, while others employ more advanced techniques like key stretching. A comparison would reveal differences in the strength of encryption, the frequency of password changes enforced, and the implementation of multi-factor authentication (MFA). For example, a comparison might show that Service A uses SHA-1 hashing (now considered insecure), while Service B employs bcrypt with regular security audits.
This highlights the importance of choosing services that prioritize robust security protocols.
Biometric Authentication and Emerging Technologies
Biometric authentication, using unique biological characteristics like fingerprints or facial recognition, offers a compelling alternative to traditional passwords. It eliminates the need for remembering and managing passwords altogether, enhancing security and user convenience. Other emerging technologies include passwordless authentication methods using cryptographic keys or one-time passwords generated via authenticator apps. These technologies provide stronger security and a better user experience by removing the vulnerabilities associated with password-based systems.
For example, Google’s Titan Security Key provides a hardware-based two-factor authentication solution, adding an extra layer of protection against phishing and other attacks.
Legal and Ethical Implications
The widespread use of weak passwords presents significant legal and ethical challenges for both organizations and individuals. Failing to implement robust password security measures can lead to severe consequences, impacting not only the reputation and financial stability of companies but also the privacy and well-being of their users. This section will explore the legal ramifications of inadequate password security, ethical considerations surrounding password handling, and the impact of data breaches on individuals.
Legal Ramifications for Organizations
Organizations have a legal responsibility to protect the personal data of their users. Data protection laws, such as the UK’s Data Protection Act 2018 and the GDPR (General Data Protection Regulation) in Europe, impose strict obligations on organizations regarding data security. Failure to implement adequate password security measures, leading to a data breach, can result in substantial fines, legal action from affected individuals, and reputational damage.
For example, the ICO (Information Commissioner’s Office) in the UK has issued significant fines to organizations found to have inadequate data security practices, including those involving weak passwords. The penalties can be substantial, potentially reaching millions of pounds depending on the severity and scale of the breach. Furthermore, organizations may face class-action lawsuits from affected users seeking compensation for damages suffered as a result of the breach.
Ethical Considerations Surrounding Password Collection and Storage
The collection and storage of user passwords raise important ethical concerns. Organizations have a moral obligation to handle user data responsibly and transparently. This includes employing secure methods for storing passwords, such as hashing and salting, to prevent unauthorized access even if a breach occurs. Ethical considerations also extend to the transparency of an organization’s password policies and security practices.
Users should be informed about how their passwords are handled and what measures are in place to protect them. A lack of transparency and inadequate security measures can erode user trust and damage the organization’s reputation.
Impact of Data Breaches on Individuals’ Privacy and Data Security
Data breaches resulting from weak passwords can have devastating consequences for individuals. Stolen credentials can be used to access personal accounts, financial information, and sensitive data, leading to identity theft, financial loss, and emotional distress. The impact can be far-reaching, affecting individuals’ credit scores, employment prospects, and overall sense of security. For instance, a data breach exposing usernames and passwords could lead to fraudulent transactions, account takeovers, and phishing attacks targeting the affected individuals.
The long-term consequences of such breaches can be significant and difficult to overcome.
Both users and organizations share a collective responsibility for maintaining strong password security. Users must adopt strong, unique passwords and practice good online hygiene, while organizations must implement robust security measures, including multi-factor authentication and regular security audits, to protect user data.
Conclusive Thoughts: Uk Says No To Ransom Passwords Such As Admin 123456 And Qwerty
So, the message is loud and clear: ditch the “admin 123456” and “qwerty” passwords. The UK government’s stance reflects a growing global awareness of the critical need for robust password security. While technology plays a crucial role in enhancing security, ultimately, it all boils down to individual responsibility. By understanding the risks and adopting strong password practices, we can significantly reduce our vulnerability to cyberattacks and create a safer digital environment.
Let’s all commit to better password hygiene – it’s the simplest and most effective security measure we can take.
FAQ Overview
What are some examples of strong passwords?
Strong passwords are long (at least 12 characters), include a mix of uppercase and lowercase letters, numbers, and symbols, and are unique to each account.
What is multi-factor authentication (MFA)?
MFA adds an extra layer of security by requiring more than just a password to access an account, such as a verification code sent to your phone or email.
What happens if my organization doesn’t enforce strong password policies?
Organizations failing to implement adequate password security can face legal repercussions, including fines and reputational damage.
Are password managers safe?
Reputable password managers use strong encryption to protect your passwords, making them a safer alternative to remembering numerous weak passwords.