Google Mobile Security Alert for Huawei Users
Google mobile security alert for Huawei users is raising eyebrows in the tech world. This alert signals potential vulnerabilities for Huawei device owners, prompting a crucial discussion about security practices, user impact, and Google’s response. The implications extend beyond individual users, affecting the entire tech industry and prompting questions about trust and safety in mobile devices.
The alert system, designed to flag potential threats, highlights different levels of severity and the types of security issues it addresses, from phishing to malware. This post delves into the specifics of Huawei-related concerns, examining potential vulnerabilities and contrasting Huawei’s security posture with other Android manufacturers. We’ll also explore the impact on users, Google’s solutions, alternative perspectives, and future predictions.
Overview of Google Mobile Security Alert
Google’s mobile security alert system is a crucial tool for protecting users from evolving online threats. It proactively identifies and flags potential vulnerabilities affecting mobile devices, ensuring users are informed about and protected against malicious activities. This system is vital in mitigating risks and enabling users to take necessary precautions to maintain their digital safety.The system operates by constantly monitoring and analyzing reported security threats, and then providing users with relevant alerts.
This real-time monitoring allows users to address issues before they escalate into major problems. The alert system is a critical component of a holistic approach to mobile security, encompassing both technical and user-centric strategies for defense.
Types of Security Threats Addressed
Google’s alert system is designed to address a wide array of security threats. These threats can range from straightforward phishing attempts to sophisticated malware infections, impacting user data and device functionality. A critical component of the system is its ability to identify and flag threats in a timely manner, allowing users to respond effectively.
Severity Levels of Security Alerts
Security alerts are categorized by severity, providing users with clear understanding of the potential impact of a threat. This categorization enables users to prioritize their response based on the level of risk. Understanding the severity levels is crucial for users to effectively mitigate potential harm.
- Critical: These alerts signify the highest risk, indicating immediate threats to user data or device functionality. Examples include ransomware attacks, which encrypt user files and demand payment for their release, or critical vulnerabilities that could be exploited by malicious actors to take control of the device.
- High: High-severity alerts indicate significant risks that could lead to data loss or compromise. Examples include phishing attempts that try to steal sensitive information, or malware infections that may compromise personal data or device functionality.
- Medium: Medium-severity alerts point to potential risks, such as suspicious apps or links that might contain malware or lead to unauthorized access. This level alerts users to potential problems but does not necessarily represent immediate danger.
- Low: Low-severity alerts identify less critical issues, such as minor vulnerabilities or minor security misconfigurations. These alerts help maintain device security but may not pose a significant threat in the short term.
Examples of Security Vulnerabilities
Numerous vulnerabilities can trigger security alerts. Examples include outdated operating systems, which might contain known exploits, or the installation of malicious applications, which could secretly transmit user data. The alert system’s effectiveness relies on users’ awareness and proactive actions to address potential security breaches.
Alert Categories and Descriptions
The table below provides a summary of various alert categories and their corresponding descriptions. This structured overview aids in understanding the different types of security threats and how they are categorized.
| Alert Category | Description |
|---|---|
| Phishing | Attempts to trick users into revealing sensitive information, such as passwords or credit card details, by masquerading as a trustworthy entity. |
| Malware | Malicious software designed to damage, disrupt, or gain unauthorized access to a user’s device or data. |
| Suspicious App | Applications that exhibit suspicious behavior or have been flagged for potential security risks. |
| Unverified Links | Links that might lead to malicious websites or downloads. |
| Outdated Software | Software that is no longer supported or updated, making it more vulnerable to security exploits. |
Huawei-Specific Concerns

Huawei’s rise as a major player in the mobile market has been accompanied by persistent security concerns. These concerns, often stemming from the company’s close ties to the Chinese government, have led to a significant debate about the trustworthiness of Huawei devices. Understanding these concerns is crucial for consumers considering purchasing or using Huawei products.
Potential Security Risks
Huawei devices, like other Android phones, are susceptible to vulnerabilities. However, the potential for access by third parties, especially those with government backing, is a unique concern. This potential access raises questions about the integrity and security of data stored on or transmitted through Huawei devices.
Comparison with Other Android Manufacturers
Comparing Huawei’s security practices to those of other major Android manufacturers reveals some distinctions. Samsung, Google Pixel, and other prominent players often prioritize open-source components and independent security audits. Huawei, on the other hand, has faced criticism for potentially less transparent security practices, particularly regarding the use of proprietary components and the potential for backdoors. The differing approaches to security and the potential for government influence highlight the importance of evaluating security practices on a case-by-case basis.
Historical Context of Security Concerns
The historical context of Huawei’s relationship with the Chinese government is crucial to understanding the ongoing security concerns. The company’s presence in critical infrastructure, alongside its involvement in 5G technologies, raises concerns about potential access points for espionage or manipulation. This historical context has fueled anxieties about the potential for data breaches or manipulation of communications.
Role of Government Regulations and Policies
Government regulations and policies significantly influence perceptions of security. Restrictions on the use of Huawei equipment in certain countries, alongside allegations of data sharing requirements, have further fueled the debate around Huawei’s trustworthiness. These regulations, and the perceived potential for manipulation, directly impact consumers’ choices and perceptions of risk.
Specific Vulnerabilities
Specific vulnerabilities potentially affecting Huawei devices are often linked to the use of proprietary components and the lack of transparency in security audits. While these vulnerabilities are not unique to Huawei, the lack of comprehensive and independent audits has created an environment of suspicion. The use of closed-source code and potential government influence make the identification and mitigation of these vulnerabilities more complex.
Security Posture Comparison: Google vs. Huawei
| Feature | Huawei | |
|---|---|---|
| Open-Source Codebase | Primarily open-source, allowing for wider scrutiny | Mix of open-source and proprietary code, leading to less transparency |
| Security Audits | Regular independent security audits | Less transparent audit processes, often criticized for lack of independence |
| Government Influence | Generally perceived as less influenced by government pressures | Perceived as more susceptible to government influence, particularly in China |
| Data Security Practices | Emphasizes user data security and privacy | Concerns exist regarding potential government access to user data |
| Transparency | Generally more transparent regarding security practices | Often criticized for lack of transparency in security practices |
This table highlights key differences in security posture between Google and Huawei, illustrating the concerns surrounding Huawei’s practices. The differences in these aspects directly impact the perceived security risks associated with using Huawei devices.
Impact on Huawei Users
Security alerts regarding Huawei devices can lead to a range of potential consequences for users, impacting their device functionality and overall trust in the brand. Understanding these potential issues and proactive steps to mitigate them is crucial for Huawei users. The severity of these consequences varies depending on the nature of the alert and the user’s specific setup.
Potential Disruptions and Risks
Huawei users might experience varying degrees of disruption due to security alerts. Examples include compromised data privacy, unexpected device shutdowns, or restricted access to certain applications or services. In more severe cases, vulnerabilities exploited by malicious actors could result in the complete loss of data or device control. Furthermore, the constant need to update and patch devices could lead to performance slowdowns and occasional incompatibility issues with specific software or applications.
The constant stream of security alerts, even if minor, can be disruptive to users who rely on their devices for productivity or personal use.
Steps to Mitigate Risks
Proactive measures are key to minimizing the impact of security alerts. Users should prioritize regularly updating their Huawei devices with the latest security patches. These updates often address vulnerabilities identified in the alerts, thus bolstering device protection. Furthermore, implementing strong passwords and enabling multi-factor authentication for accounts accessed through the device adds another layer of security. Using a reputable antivirus application, if available for the device, can help detect and block malicious software.
Preventative Measures
A proactive approach is essential for minimizing the risks associated with security alerts. A list of preventative measures includes:
- Regular Device Updates: Huawei regularly releases security updates to address potential vulnerabilities. Staying current with these updates is crucial for maintaining device security.
- Strong Passwords: Using complex and unique passwords for accounts accessed through the device enhances security. Avoid using easily guessable passwords.
- Multi-Factor Authentication: Enabling multi-factor authentication (MFA) adds an extra layer of security to sensitive accounts.
- Antivirus Software: Consider installing reputable antivirus software on your device to detect and block malware.
- Data Backup: Regularly backing up important data provides a safeguard in case of device compromise or data loss.
- Be Cautious of Downloads: Exercise caution when downloading applications or files from unknown sources. Verify the source’s legitimacy before installing anything.
Impact on User Trust and Confidence
Security alerts can have a significant impact on user trust and confidence in Huawei devices. Negative publicity surrounding security breaches can lead to hesitations among potential buyers and a decline in user loyalty. Huawei needs to proactively address these alerts, demonstrating a commitment to user security and providing clear communication to build trust.
Troubleshooting Security Alerts
The following table provides steps for troubleshooting common security alert issues.
| Alert Type | Troubleshooting Steps |
|---|---|
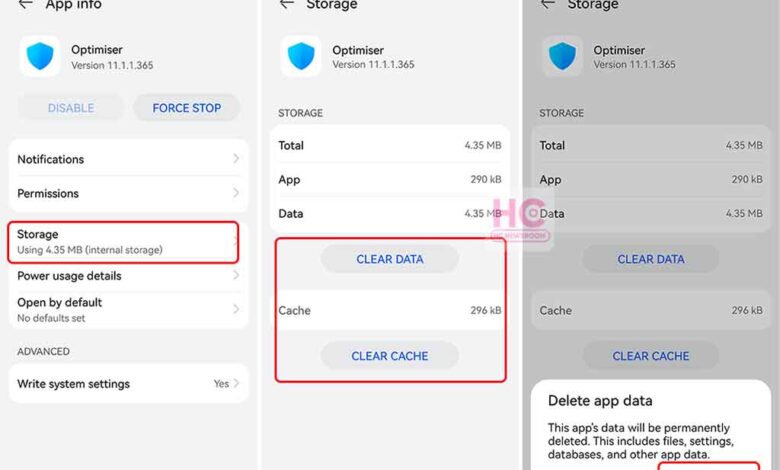
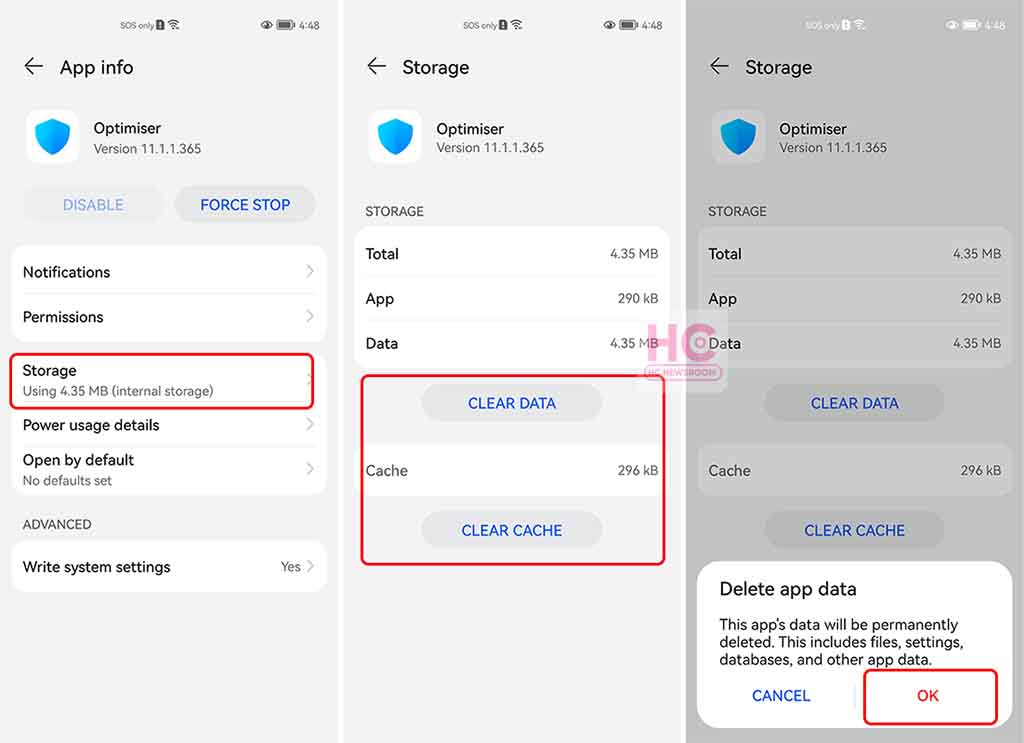
| Device Lock-up | Check for pending updates. Reboot the device. If the issue persists, contact Huawei support. |
| App Errors | Update the affected application. Clear the app cache and data. If the problem persists, uninstall and reinstall the application. |
| Data Loss Warnings | Verify the data backup status. Restore from the last backup if possible. Contact Huawei support for further assistance. |
| Unauthorized Access Attempts | Change passwords for all affected accounts. Enable two-factor authentication. Monitor your accounts for suspicious activity. |
Google’s Response and Solutions
Google’s approach to security concerns regarding Huawei devices emphasizes proactive measures and user empowerment. Recognizing the sensitivity surrounding the topic, Google prioritizes transparent communication and readily available support to ensure users feel safe and secure. Their response extends beyond simply acknowledging the issue, focusing on practical solutions and continuous improvement in their security protocols.Google actively monitors and assesses potential vulnerabilities across its ecosystem, including its relationship with Huawei.
This proactive approach allows them to address security threats effectively, safeguarding user data and maintaining the integrity of its services.
Google’s Approach to Addressing Security Alerts
Google’s strategy involves a multi-faceted approach to addressing security alerts, including those related to Huawei devices. This approach focuses on comprehensive testing, regular updates, and clear communication to users. Google aims to minimize disruption and maintain the reliability of its services while safeguarding user data.
Security Measures Employed by Google
Google employs a variety of methods to protect users from security threats. These methods include continuous security audits of its Android operating system and applications, including those used on Huawei devices. They also implement robust security protocols for data transmission and storage, ensuring data integrity and user privacy.
- Regular Updates: Google releases frequent security updates for Android, addressing vulnerabilities as they are discovered. These updates often include patches specific to Huawei devices, mitigating potential risks related to those platforms.
- Enhanced Security Audits: Google performs rigorous security audits on its entire Android ecosystem, including components integrated with Huawei devices. This proactive approach identifies and resolves potential security weaknesses before they can be exploited.
- Data Encryption: Google employs advanced encryption techniques to protect user data during transmission and storage. This ensures that sensitive information remains confidential, even if a security breach occurs.
Examples of Security Measures Taken by Google
Google’s response to specific incidents often involves swift action to mitigate the impact on users. For instance, if a vulnerability is identified in a component used by Huawei devices, Google may release an immediate patch to address the issue and prevent potential exploitation. They often communicate these actions transparently to users, keeping them informed about the steps taken to protect their data.
Google’s recent mobile security alert for Huawei users is a bit concerning, isn’t it? It’s definitely got me thinking about data security in general. Fortunately, there’s a potential silver lining, as the Department of Justice Offers Safe Harbor for MA Transactions here. This new policy could potentially offer some reassurance for consumers regarding their transactions.
However, I’m still keeping a close eye on Google’s mobile security alert for Huawei users to see how things unfold.
Google’s Resources and Support for Users
To support users affected by security alerts, Google provides various resources and support channels. This includes detailed information about the specific vulnerabilities, guidance on how to update their devices, and access to support teams for assistance. Google prioritizes user understanding and prompt resolution to any issues.
Google’s recent mobile security alert for Huawei users highlights the crucial need for robust security measures in our digital world. The constant evolution of threats necessitates proactive steps, and that includes adopting advanced security solutions. This underscores the importance of deploying AI code safety tools, like those discussed in Deploying AI Code Safety Goggles Needed , to safeguard software development.
Ultimately, this proactive approach to security is essential to ensure the safety of Huawei mobile users and all those relying on digital platforms.
Google’s Support Channels and Contact Information
Google offers a variety of support channels to address user concerns and provide assistance.
| Support Channel | Contact Information |
|---|---|
| Google Help Center | google.com/help |
| Android Support Forums | support.google.com/android |
| Google Play Store Help | support.google.com/googleplay |
Alternative Perspectives and Considerations
The Google Mobile Security Alert regarding Huawei devices has sparked a wide range of reactions and interpretations. Different stakeholders, from consumers to governments, perceive the situation through various lenses, leading to diverse perspectives on the severity and implications of these security concerns. This section explores these alternative viewpoints, highlighting the complexities surrounding Huawei’s security posture.This discussion delves into the varying viewpoints surrounding Huawei’s security practices, the broader industry implications of these alerts, and the crucial role of independent audits in maintaining trust and transparency.
Furthermore, it examines the potential economic impact of such alerts on Huawei and the broader tech sector, illustrating how different stakeholders interpret and respond to these security concerns.
Varying Perspectives on Huawei Security, Google mobile security alert for huawei users
Different actors hold contrasting views on the security of Huawei devices. Some governments and security agencies express significant concerns, citing potential vulnerabilities and national security risks. Conversely, Huawei maintains that its products are secure and that these concerns are unwarranted, highlighting its robust security measures and industry certifications. Independent security researchers play a vital role in assessing these claims, offering their own analyses and perspectives.
| Perspective | Key Concerns/Arguments | Supporting Evidence/Examples |
|---|---|---|
| Government Agencies (Specific Countries) | Potential for backdoors, data breaches, and exploitation of vulnerabilities for espionage or sabotage. Focus on national security concerns. | Past allegations of government influence on device development, specific reports on vulnerabilities in certain Huawei products, and national security briefs. |
| Huawei | Claims of a lack of credible evidence, emphasizing the robustness of its security measures, independent certifications, and adherence to industry best practices. | Huawei’s certifications, security audits conducted by independent firms, and public statements denying any backdoors or vulnerabilities. |
| Independent Security Researchers | Identify potential weaknesses and vulnerabilities, but their findings are often debated in terms of their severity and exploitability. | Published research papers, vulnerability reports, and analyses of Huawei’s software and hardware. |
| Consumers | Concern over potential data breaches and privacy violations. The perceived risk and impact on their personal data. | Past cases of data breaches and the potential impact on personal information, customer reviews, and public perception. |
Broader Implications for the Tech Industry
Security alerts regarding Huawei’s devices have broader implications for the tech industry. These alerts could potentially set precedents for future scrutiny of other manufacturers, fostering a more rigorous approach to security assessment and auditing. It also raises questions about the role of governments in regulating technology and the balance between national security concerns and technological innovation.
Role of Independent Security Audits and Assessments
Independent security audits and assessments are crucial in maintaining trust and transparency in the tech industry. They provide objective evaluations of security measures, offering insights into potential vulnerabilities and areas for improvement. These audits play a vital role in addressing security concerns and building consumer confidence. The lack of independent verification can create distrust and uncertainty.
Potential Economic Impact
The impact of security alerts can be significant, particularly for companies like Huawei. The alerts could lead to decreased sales, lost market share, and reputational damage. The economic consequences could also extend to other industries that rely on Huawei’s products, leading to disruptions in supply chains and potentially affecting global trade. Examples of similar situations in the past include other security breaches or controversies impacting specific tech companies.
Stakeholder Perceptions
Different stakeholders perceive the situation through various lenses. Governments may prioritize national security concerns, while consumers focus on the privacy implications and potential risks to their personal data. Huawei, understandably, emphasizes the robustness of its security measures and the lack of credible evidence supporting the allegations.
Future Implications and Predictions: Google Mobile Security Alert For Huawei Users
The landscape of mobile security is constantly evolving, driven by advancements in technology and the ever-increasing sophistication of cyber threats. Predicting the future is inherently challenging, but examining current trends and emerging technologies allows us to anticipate potential developments and prepare for future challenges.The evolution of mobile security is intertwined with the wider digital world. New vulnerabilities are discovered daily, and attackers are constantly innovating their methods.
Google’s recent mobile security alert for Huawei users highlights the ever-present threat of vulnerabilities in tech. Meanwhile, a recent discovery of a vulnerability in Microsoft Azure Cosmos DB is a stark reminder of the importance of constant security updates. Understanding these issues, like the one with Azure Cosmos DB, Azure Cosmos DB Vulnerability Details , is key to staying informed and proactive in securing our digital lives, and ultimately, the safety of our mobile devices like those used by Huawei users.
This necessitates a proactive and adaptive approach to security, one that anticipates emerging threats and develops robust countermeasures.
Potential Future Developments in Mobile Security
The future of mobile security will likely see an increasing emphasis on proactive threat detection and prevention. Machine learning and artificial intelligence will play a crucial role in identifying and responding to threats in real-time. This will require a shift in the security paradigm, moving beyond reactive measures to predictive and preventative strategies. The rise of the Internet of Things (IoT) and its integration with mobile devices will also introduce new attack vectors and require enhanced security protocols to protect interconnected devices.
AI’s Role in Enhancing Mobile Security
Artificial intelligence (AI) is poised to revolutionize mobile security. AI algorithms can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity. This allows for faster threat detection and response, potentially preventing breaches before they occur. For example, AI-powered systems can monitor app behavior for suspicious activity, flag potentially harmful downloads, and automatically block malicious traffic.
Furthermore, AI can personalize security measures based on individual user behavior and device usage patterns.
Emerging Security Threats and Countermeasures
Emerging threats are constantly evolving. One significant concern is the increasing use of sophisticated malware, often designed to evade traditional security measures. Countermeasures involve developing advanced detection techniques, including machine learning algorithms trained on vast datasets of known and emerging malware. Another emerging threat is the use of social engineering techniques in conjunction with mobile devices. Countermeasures will require robust security awareness training for users and enhanced authentication protocols to prevent unauthorized access.
Potential Security Trends
- Increased reliance on AI-powered security systems: AI will play a central role in automating security tasks, such as threat detection, vulnerability analysis, and incident response.
- Emphasis on proactive security measures: Shifting focus from reactive measures to preventative strategies that identify and mitigate threats before they can cause harm.
- Enhanced user authentication and authorization: The development of more robust and user-friendly authentication methods to protect against unauthorized access, such as biometrics and multi-factor authentication.
- Integration of blockchain technology for enhanced security: Blockchain can enhance security by providing secure and transparent record-keeping, particularly in transactions and data management.
- Focus on security for IoT devices: The rise of interconnected devices requires robust security protocols and standards to prevent vulnerabilities and breaches.
The emergence of these trends will reshape the way mobile security is approached and implemented. They will drive the development of innovative technologies and strategies, equipping users and organizations with more effective defenses against emerging threats.
Projected Changes in Mobile Security Protocols
| Protocol | Current Status | Projected Changes |
|---|---|---|
| Mobile Operating System Security | Patching vulnerabilities, enhancing security features. | Increased reliance on AI for real-time threat detection, dynamic patching based on threat intelligence. |
| App Store Security | Scrutiny of apps for malware and vulnerabilities. | AI-powered automated app analysis for security and privacy risks, dynamic updates for app security. |
| User Authentication | Passwords, two-factor authentication. | Biometric authentication, advanced multi-factor authentication, adaptive authentication based on user behavior. |
| Network Security | Firewall protection, encryption. | AI-powered network traffic analysis, dynamic network segmentation to isolate threats, robust VPN protocols. |
These projected changes represent a significant evolution in mobile security protocols. They reflect a shift towards more proactive, automated, and adaptive security measures that can address the dynamic nature of cyber threats.
Ending Remarks
In conclusion, the Google mobile security alert for Huawei users underscores the ever-evolving landscape of mobile security. While Huawei faces scrutiny, the broader implications for the tech industry are undeniable. Understanding the potential risks and Google’s response is crucial for users, and ongoing vigilance is key to navigating this complex situation. Future developments in mobile security will undoubtedly be shaped by this alert, forcing companies to prioritize security and transparency.
FAQ Summary
What are the common types of security threats addressed by Google’s alert system?
Google’s alert system addresses various threats, including phishing attempts, malware infections, and potentially harmful apps. The system aims to identify and flag these threats to protect users.
How can Huawei users mitigate the risks associated with these alerts?
Huawei users can mitigate risks by regularly updating their devices’ software, being cautious about downloading apps from untrusted sources, and using strong passwords. They should also be aware of phishing scams and report any suspicious activity.
What is Google’s approach to addressing security alerts for Huawei users?
Google’s approach involves providing resources and support to Huawei users affected by alerts. This could include security patches, updates, and information on how to stay safe.
What are some alternative perspectives on the security of Huawei devices?
Alternative perspectives vary. Some might focus on Huawei’s security posture and the role of government regulations, while others may emphasize the user’s role in maintaining device security. There are diverse viewpoints and opinions on this topic.