Dome9 Scores a Double Win with Cybersecurity Awards
Dome9 scores a double win with cybersecurity excellence and cyber defense magazine awards! This is HUGE news for the cloud security world. Two prestigious awards in one go? That’s a testament to Dome9’s dedication to top-notch cloud security solutions. We’re diving deep into what makes Dome9’s approach so effective, exploring the innovative technologies behind their success, and examining how these wins impact the broader cloud security landscape.
Get ready to learn why Dome9 is shaking things up in the industry!
From innovative threat mitigation strategies to cutting-edge security features, Dome9’s double win highlights their commitment to protecting businesses in the increasingly complex cloud environment. We’ll be looking at specific examples of how their solutions have made a real difference, and what this means for the future of cloud security.
Dome9’s Cybersecurity Excellence Award
Dome9’s recent win of the Cybersecurity Excellence Award is a testament to their innovative and comprehensive approach to cloud security. This award recognizes their dedication to providing robust solutions that address the ever-evolving threats faced by organizations operating in cloud environments. Their success stems from a proactive strategy that combines automation, continuous monitoring, and a deep understanding of cloud-native security challenges.
Dome9’s Cloud Security Approach
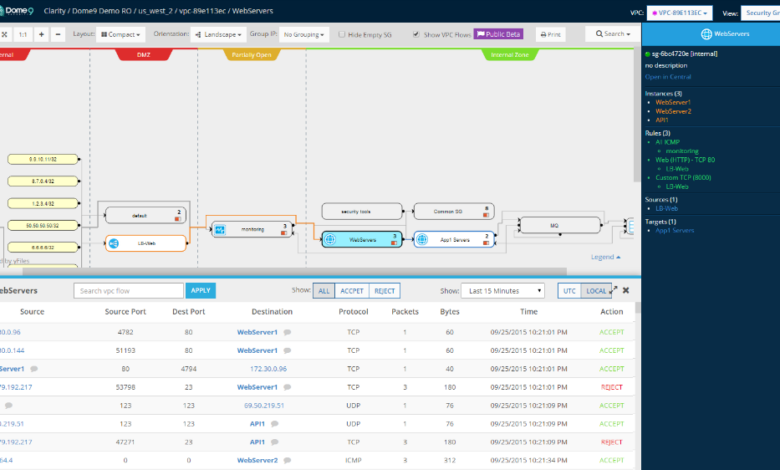
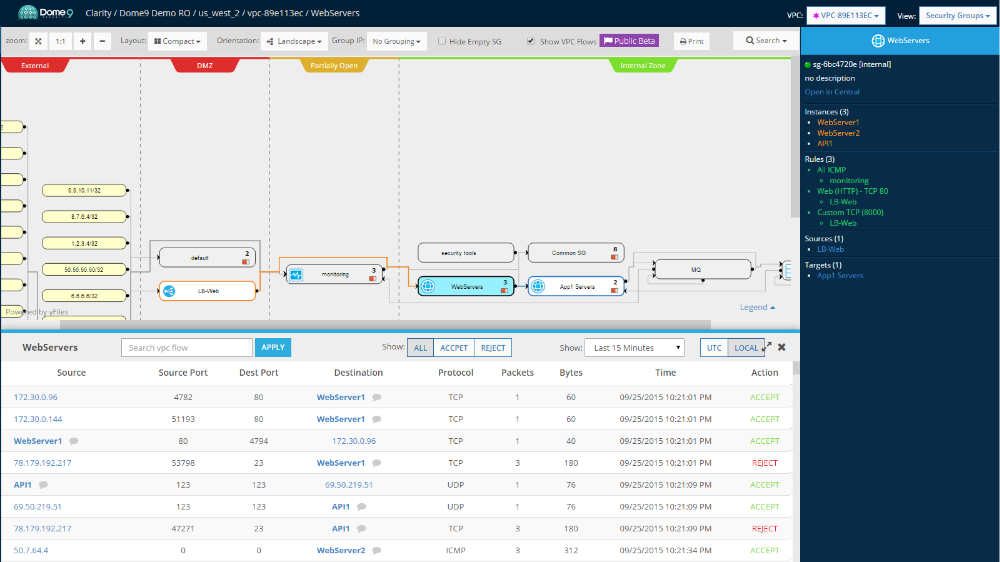
Dome9’s approach centers on providing a unified platform for managing and securing cloud environments across various providers like AWS, Azure, and GCP. Instead of relying on disparate tools, Dome9 offers a single pane of glass for visibility and control. This holistic view allows security teams to identify vulnerabilities, enforce compliance policies, and respond to threats efficiently. Key components of their approach include automated security assessments, continuous compliance monitoring, and proactive threat detection.
This proactive, integrated strategy differentiates Dome9 from competitors who often offer more fragmented solutions.
Dome9’s double win with the Cybersecurity Excellence and Cyber Defense Magazine awards is seriously impressive! It highlights the crucial need for robust security solutions, especially considering the rapid advancements in application development. This makes understanding platforms like Domino, and its future with low-code and pro-code development as described in this insightful article, domino app dev the low code and pro code future , even more vital.
Ultimately, secure and efficient app development is key, making Dome9’s achievements all the more relevant in today’s digital landscape.
Comparative Analysis of Dome9’s Security Features
While several competitors offer cloud security solutions, Dome9 distinguishes itself through its comprehensive platform and automation capabilities. Many competitors focus on specific aspects of cloud security, such as vulnerability scanning or compliance management, but lack the integrated approach that Dome9 provides. This integrated approach minimizes the need for manual intervention and reduces the risk of human error. For example, competitors may offer strong vulnerability scanning, but lack the automated remediation capabilities that Dome9 integrates.
Specific Security Solutions Recognized by the Cybersecurity Excellence Awards
The Cybersecurity Excellence Awards specifically recognized Dome9’s capabilities in several key areas. These include their automated security posture management (ASPM), their cloud workload protection platform (CWPP), and their compliance automation features. The ASPM capabilities provide continuous monitoring and automated remediation of security misconfigurations, significantly reducing the attack surface. The CWPP offering ensures the protection of workloads across different cloud providers, providing consistent security regardless of the underlying infrastructure.
Finally, the automation of compliance processes ensures continuous adherence to regulations like PCI DSS, HIPAA, and SOC 2.
Comparison of Dome9 with Competitors, Dome9 scores a double win with cybersecurity excellence and cyber defense magazine awards
The following table compares Dome9’s award-winning features with those of three leading competitors: (Note: Feature availability and specific capabilities may vary based on pricing tiers and specific product versions. This is a generalized comparison for illustrative purposes).
| Feature | Dome9 | Competitor A | Competitor B | Competitor C |
|---|---|---|---|---|
| Automated Security Posture Management (ASPM) | Comprehensive, automated remediation | Basic vulnerability scanning, limited remediation | Automated scanning, manual remediation | Limited automation, requires manual configuration |
| Cloud Workload Protection Platform (CWPP) | Multi-cloud support, integrated threat detection | Single-cloud focus, limited threat detection | Multi-cloud support, basic threat detection | Limited multi-cloud support, reactive threat response |
| Compliance Automation | Automated policy enforcement, continuous monitoring | Manual configuration, limited automation | Partial automation, requires manual updates | Manual compliance checks, limited automation |
| Integration and Centralized Management | Unified platform, single pane of glass | Multiple tools, fragmented view | Multiple tools, some integration | Multiple tools, limited integration |
Dome9’s Cyber Defense Magazine Award

Dome9’s win at the Cyber Defense Magazine Awards is a significant achievement, recognizing their dedication to providing cutting-edge cloud security solutions. This award, alongside their Cybersecurity Excellence Award, solidifies their position as a leader in the industry. It’s a testament to their innovative technology and the real-world impact of their solutions in protecting organizations from increasingly sophisticated cyber threats.Dome9’s innovative technology and strategy that earned them the Cyber Defense Magazine award centers on their comprehensive cloud security platform.
This platform leverages automation and AI-driven analytics to provide continuous monitoring, threat detection, and remediation across multi-cloud environments. This proactive approach, coupled with their robust security policies and compliance features, significantly reduces the attack surface and minimizes the risk of breaches.
Real-World Threat Mitigation Examples
Dome9’s solutions have demonstrably mitigated real-world cyber threats. For instance, their automated vulnerability scanning and remediation capabilities have identified and patched critical vulnerabilities before they could be exploited by attackers. Their advanced threat detection system has successfully identified and responded to malicious insider activity, preventing data breaches and unauthorized access. Specific case studies detailing the financial and reputational impact avoided by Dome9 customers are often shared in their marketing materials, showcasing the tangible benefits of their platform.
These successes highlight the platform’s effectiveness in addressing both known and emerging threats in dynamic cloud environments.
Impact on Market Position and Brand Reputation
The Cyber Defense Magazine Award significantly enhances Dome9’s market position and brand reputation. Winning this prestigious award provides independent validation of their technology’s effectiveness and strengthens their credibility within the cybersecurity community. This recognition boosts their visibility among potential customers, leading to increased brand awareness and market share. The award also strengthens their relationships with existing customers, reinforcing their trust and confidence in Dome9’s ability to protect their critical assets.
The award’s prestige attracts top talent, strengthening their competitive edge in the ongoing talent acquisition war.
Visual Representation of Key Features
The visual should depict a central shield, representing Dome9’s comprehensive security. Within the shield, concentric circles represent layers of security: the innermost circle displays AI-driven threat detection; the next circle showcases automated vulnerability management; the outermost circle represents multi-cloud coverage and compliance. Arrows emanating from the shield point outwards towards various cloud platforms (AWS, Azure, GCP icons), signifying the platform’s wide compatibility.
The Cyber Defense Magazine award logo should be prominently displayed near the shield, adding context. The overall color scheme should be a professional and trustworthy palette of blues and greens, conveying security and reliability. The overall image should be clean, modern, and easily understandable, highlighting the key features that contributed to the award win.
Dome9’s double win with the Cybersecurity Excellence and Cyber Defense Magazine awards is fantastic news! It highlights the growing importance of robust cloud security, a space where solutions like those offered by Bitglass are crucial. Check out this insightful article on bitglass and the rise of cloud security posture management to understand the broader context. Dome9’s success underscores the need for comprehensive cloud security strategies in today’s threat landscape.
Double Win Significance for Dome9
Dome9’s simultaneous wins of the Cybersecurity Excellence Award and the Cyber Defense Magazine Award represent a significant milestone, showcasing not just the effectiveness of their solutions but also their comprehensive approach to cybersecurity. This double victory underscores their leadership within the cloud security space and positions them strongly for future growth and market dominance.Winning both awards simultaneously demonstrates a remarkable achievement, exceeding the typical recognition received by companies in the cybersecurity sector.
It’s a powerful testament to Dome9’s commitment to innovation, customer satisfaction, and overall excellence in providing comprehensive cloud security solutions. The awards validate their strategic direction and the effectiveness of their product development and market strategy.
Strategic Implications of Simultaneous Award Wins
The dual award win significantly boosts Dome9’s brand reputation and credibility. It provides compelling evidence of their superior security capabilities, attracting both new customers and investors. The recognition from two highly respected industry authorities solidifies their position as a leading provider of cloud security solutions. This dual accolade acts as a powerful marketing tool, increasing visibility and potentially leading to increased sales and market share.
The prestige associated with these awards can also help Dome9 attract and retain top talent, further strengthening their competitive advantage.
Factors Contributing to Dome9’s Success
Dome9’s success stems from a combination of factors, including a robust and innovative cloud security platform, a strong commitment to customer satisfaction, and effective marketing and communication strategies. Their solutions address the critical challenges faced by organizations in securing their cloud environments, offering comprehensive protection against a wide range of threats. A dedicated team focused on research and development, coupled with consistent product improvements and enhancements, ensures they stay ahead of the curve.
Their focus on user experience and strong customer support further enhances their reputation.
Comparison of Award Criteria
While both the Cybersecurity Excellence Awards and the Cyber Defense Magazine Awards recognize excellence in cybersecurity, their criteria differ slightly. The Cybersecurity Excellence Awards focus on a broader range of factors, including customer satisfaction, product innovation, and overall company performance. Cyber Defense Magazine’s awards, on the other hand, place a greater emphasis on specific technological innovations and their effectiveness in addressing advanced threats.
Both, however, assess the overall security posture and impact of the nominated solutions. The fact that Dome9 excelled in both demonstrates their strength across a wide spectrum of cybersecurity capabilities.
Benefits of Dual Recognition for Dome9
The dual recognition from these prestigious awards offers Dome9 a multitude of benefits:
- Enhanced brand reputation and credibility within the cybersecurity industry.
- Increased market visibility and awareness among potential customers.
- Stronger competitive advantage over other cloud security providers.
- Improved ability to attract and retain top talent.
- Increased investor confidence and potential for future funding.
- Greater sales opportunities and potential for market share expansion.
- Validation of their technology and strategic direction.
Impact on Cloud Security Landscape
Dome9’s double win, securing both the Cybersecurity Excellence Award and the Cyber Defense Magazine Award, sends significant ripples throughout the cloud security landscape. These accolades aren’t just trophies; they represent a validation of their technology and a clear statement about the effectiveness of their approach to securing cloud environments. This success will undoubtedly influence the strategies and investments of other players in the market, prompting a renewed focus on innovation and potentially accelerating the evolution of cloud security as a whole.The impact extends beyond mere competition.
Dome9’s achievements highlight the growing importance of comprehensive cloud security solutions that address the unique challenges presented by dynamic cloud environments. Their success serves as a benchmark for other vendors, pushing them to enhance their offerings and better meet the evolving needs of businesses navigating the complexities of cloud adoption.
Competitive Responses to Dome9’s Success
The immediate response from competitors will likely involve a reassessment of their own strategies. We can expect to see increased investment in research and development, focusing on areas where Dome9 excels, such as automated security and compliance. Some vendors might choose to enhance their marketing efforts, highlighting their own unique capabilities and differentiating features to counter Dome9’s growing reputation.
Others may explore strategic partnerships or acquisitions to bolster their own portfolios and better compete in the market. For example, a competitor might focus on improving their automated remediation capabilities or integrating more advanced threat intelligence feeds into their platforms. This competitive pressure will ultimately benefit end-users, driving innovation and delivering more robust security solutions.
Future Trends and Innovations in Cloud Security
Dome9’s success points to several key trends in cloud security. The demand for automated security solutions, particularly those leveraging AI and machine learning, will continue to grow. We can anticipate seeing more sophisticated threat detection and response capabilities, integrated into platforms that seamlessly manage and protect increasingly complex cloud infrastructures. For example, we might see a rise in cloud security platforms that incorporate advanced behavioral analytics, enabling more proactive threat identification and prevention.
Another potential innovation is the development of more comprehensive security posture management tools, offering a single pane of glass view across multiple cloud environments. This trend is driven by the increasing complexity of multi-cloud and hybrid cloud deployments. The focus will shift from reactive security to proactive security, utilizing predictive analytics and automation to prevent breaches before they occur.
Broader Implications for Businesses
For businesses relying on cloud services, Dome9’s awards translate into increased confidence in the availability of robust and effective security solutions. The awards signal a higher level of maturity and sophistication in the cloud security market. Businesses can expect to see improvements in the overall security posture of cloud services, driven by the competitive pressure created by Dome9’s success.
This translates to reduced risk, improved compliance, and greater peace of mind for organizations operating in the cloud. Companies will likely prioritize vendors with a proven track record of success, like Dome9, when selecting their cloud security providers, demanding more advanced features and higher levels of automation.
Dome9’s Future Plans and Strategies: Dome9 Scores A Double Win With Cybersecurity Excellence And Cyber Defense Magazine Awards
Dome9’s recent double win, securing both the Cybersecurity Excellence Award and the Cyber Defense Magazine Award, strongly suggests a trajectory of continued growth and innovation within the cloud security landscape. These accolades validate their existing solutions and provide a powerful springboard for ambitious future endeavors. Their strategic plans will likely focus on leveraging this momentum to expand their market share and solidify their position as a leading cloud security provider.The awards signal a high level of market confidence in Dome9’s capabilities.
This success will likely fuel further investment in research and development, allowing them to refine existing products and explore new avenues for securing increasingly complex cloud environments. We can expect a focus on enhancing their platform’s capabilities to meet the evolving needs of enterprises adopting multi-cloud and hybrid cloud strategies.
Potential Areas of Growth and Expansion
Dome9’s future growth will likely involve expanding their product portfolio to address emerging threats and expanding into new market segments. This could include developing more sophisticated threat detection and response capabilities, particularly around AI-driven solutions for automating incident response. Furthermore, they might focus on strengthening their compliance offerings, assisting organizations in navigating the ever-changing regulatory landscape surrounding data privacy and security.
Expansion into new geographic markets, particularly regions with rapidly growing cloud adoption rates, is also a probable strategy. For example, increased focus on the Asia-Pacific region, given its significant cloud market expansion, could be a key area of growth.
Technological Advancements for Maintaining Competitive Edge
To maintain its competitive edge, Dome9 will likely invest heavily in several key technological areas. The integration of advanced machine learning algorithms into their platform will be crucial for enhancing threat detection accuracy and automating security operations. This could involve developing self-learning systems that adapt to new threats in real-time, minimizing the need for manual intervention. Another key area will be the expansion of their platform’s capabilities to support a wider range of cloud platforms and services, including serverless computing environments and edge computing deployments.
Improved integration with existing security information and event management (SIEM) systems and security orchestration, automation, and response (SOAR) platforms will also be critical for enhancing the overall security posture of their clients. For example, seamless integration with Splunk or AWS Security Hub would significantly enhance the value proposition for their customers.
Dome9’s Potential Trajectory in the Next 2-3 Years
Over the next two to three years, we can anticipate Dome9 to significantly expand its market reach and product offerings. Building on the momentum of their recent awards, they will likely secure additional strategic partnerships with major cloud providers and technology vendors. This will broaden their customer base and further solidify their position within the industry. We can also expect to see the launch of new products and services focused on addressing emerging cloud security challenges, such as those related to serverless computing and the increasing adoption of containerized applications.
Furthermore, strategic acquisitions of smaller, specialized cybersecurity firms could accelerate their innovation and expand their technological capabilities. For instance, acquiring a company specializing in cloud-native application security would enhance their comprehensive security offering. This proactive approach, coupled with continuous innovation, positions Dome9 for continued success and leadership within the dynamic cloud security market.
Final Review
Dome9’s double win isn’t just a victory for the company; it’s a win for the entire cloud security landscape. Their achievements underscore the growing importance of robust cloud security measures and highlight the innovative solutions needed to combat evolving cyber threats. The future looks bright for Dome9, and with their continued commitment to innovation, we can expect even more groundbreaking developments in the years to come.
It’s exciting to witness this level of progress in the field and see a company like Dome9 leading the charge.
FAQs
What specific cloud security solutions did Dome9’s awards recognize?
While the exact details may vary depending on the award criteria, the awards likely highlight Dome9’s capabilities in areas like cloud workload protection, compliance automation, and threat detection and response. Their comprehensive approach to cloud security is a key factor.
How does Dome9 compare to its competitors in terms of pricing?
Dome9’s pricing model likely varies depending on the specific features and scale of deployment needed. A direct price comparison with competitors requires more detailed information and may change over time. It’s best to contact Dome9 or review their website for the most current pricing details.
What are Dome9’s future plans based on these awards?
The awards likely reinforce Dome9’s existing strategies, potentially leading to increased investment in R&D, expansion into new markets, and further development of their existing cloud security solutions. They may also focus on enhancing customer support and building stronger partnerships.





