Unlocking BigFix 11 & CyberFocus Security Analytics Power
Unlocking the power of BigFix 11 and CyberFocus security analytics is like getting a superpower for your IT security. Imagine a world where patching is automated, vulnerabilities are identified before they’re exploited, and incident response is swift and precise. This isn’t science fiction; it’s the reality this powerful duo offers. We’ll dive into how these tools work together to create a robust, proactive security posture, from vulnerability management to streamlined incident response and comprehensive reporting.
This post will explore the core functionality of BigFix 11, detailing its improvements over previous versions and showcasing its capabilities in patch management, custom action creation, and endpoint hardening. We’ll then delve into the synergistic relationship between BigFix 11 and CyberFocus Security Analytics, examining how their integration enhances threat detection, accelerates incident response, and simplifies compliance reporting. Prepare to be amazed by the level of control and visibility this combination provides!
BigFix 11 Core Functionality
BigFix 11 represents a significant leap forward in endpoint management, offering enhanced capabilities and streamlined workflows compared to its predecessors. This powerful platform provides a unified approach to patch management, software distribution, and endpoint security, all while improving operational efficiency and reducing the overall attack surface. This post delves into the core functionalities of BigFix 11, highlighting its key features and providing practical examples of its application.
Key Features and Improvements in BigFix 11
BigFix 11 boasts several key improvements over previous versions. These include a redesigned user interface for enhanced usability, improved performance and scalability to handle larger deployments, and enhanced reporting and analytics capabilities for better insights into endpoint health and security posture. The platform also benefits from strengthened security features, including enhanced authentication and authorization mechanisms, and improved integration with other IBM security products.
These advancements collectively contribute to a more robust and efficient endpoint management experience.
Efficient Patch Management and Software Distribution with BigFix 11
BigFix 11 streamlines patch management and software distribution through its automated processes and centralized control. The system allows administrators to create and deploy patches and software updates to large numbers of endpoints simultaneously, minimizing downtime and ensuring consistent software versions across the organization. This is achieved through the creation of targeted deployment packages, which can be filtered based on various criteria, such as operating system, application version, or geographic location.
Real-time monitoring capabilities provide visibility into the deployment progress and allow for immediate intervention in case of issues. For example, a critical security patch for a specific application can be deployed to all vulnerable endpoints within minutes, significantly reducing the organization’s exposure to threats.
Creating and Deploying Custom Actions in BigFix 11
BigFix 11 empowers administrators to create and deploy custom actions tailored to specific organizational needs. This involves developing custom scripts or using pre-built actions to perform various tasks on managed endpoints, such as configuring security settings, installing custom applications, or collecting diagnostic information. The process typically involves creating a Fixlet, which is a set of instructions that defines the action to be performed.
This Fixlet is then deployed to the target endpoints through the BigFix console. For instance, a custom action could be created to automatically disable specific services or ports on all endpoints, enhancing the overall security posture. The flexibility of custom actions allows for automation of complex tasks, improving efficiency and reducing manual intervention.
BigFix 11 for Endpoint Security Hardening
BigFix 11 plays a critical role in endpoint security hardening by providing the tools to enforce security policies and configurations across the entire endpoint landscape. This includes capabilities to deploy and manage security software, configure firewalls and other security settings, and monitor for vulnerabilities and malware. For example, BigFix 11 can be used to enforce strong password policies, disable unnecessary services, and deploy endpoint detection and response (EDR) solutions.
By automating these security tasks, BigFix 11 helps to reduce the risk of successful cyberattacks and strengthens the organization’s overall security posture. The platform’s ability to proactively identify and remediate vulnerabilities is crucial in a constantly evolving threat landscape.
Integrating BigFix 11 with Existing IT Infrastructure
Integrating BigFix 11 with an existing IT infrastructure typically involves several steps. First, the BigFix server needs to be installed and configured. This includes defining the network settings, user accounts, and the desired reporting and alerting mechanisms. Next, the BigFix client needs to be deployed to all managed endpoints. This can be done manually or through automated deployment methods.
After deployment, the clients will begin reporting their status and inventory information to the BigFix server. Finally, policies and actions can be created and deployed to manage the endpoints. Proper integration requires careful planning and consideration of network infrastructure, security protocols, and existing IT systems. Successful integration results in a unified and centralized management system for all endpoints.
BigFix 11 Feature Comparison
| Feature | BigFix 11 | Competitor A (Example: Microsoft Intune) | Comparison |
|---|---|---|---|
| Patch Management | Automated patch deployment, targeted patching, vulnerability scanning | Automated patch deployment, targeted patching, vulnerability scanning | Both offer robust patch management; specific strengths may vary based on OS and application support. |
| Software Distribution | Automated software deployment, version control, rollback capabilities | Automated software deployment, version control, rollback capabilities | Similar functionality; BigFix may offer more granular control over deployment. |
| Endpoint Security | Security policy enforcement, vulnerability assessment, endpoint detection and response integration | Security policy enforcement, Mobile Threat Defense integration, Conditional Access | BigFix excels in server-centric security management; Intune focuses on mobile and cloud security. |
| Reporting and Analytics | Comprehensive reporting, custom dashboards, real-time monitoring | Comprehensive reporting, custom dashboards, real-time monitoring | Both offer strong reporting; the specific metrics and visualizations might differ. |
| Scalability | Handles large numbers of endpoints efficiently | Handles large numbers of endpoints efficiently | Both are scalable; performance under extreme load might vary. |
CyberFocus Security Analytics Integration
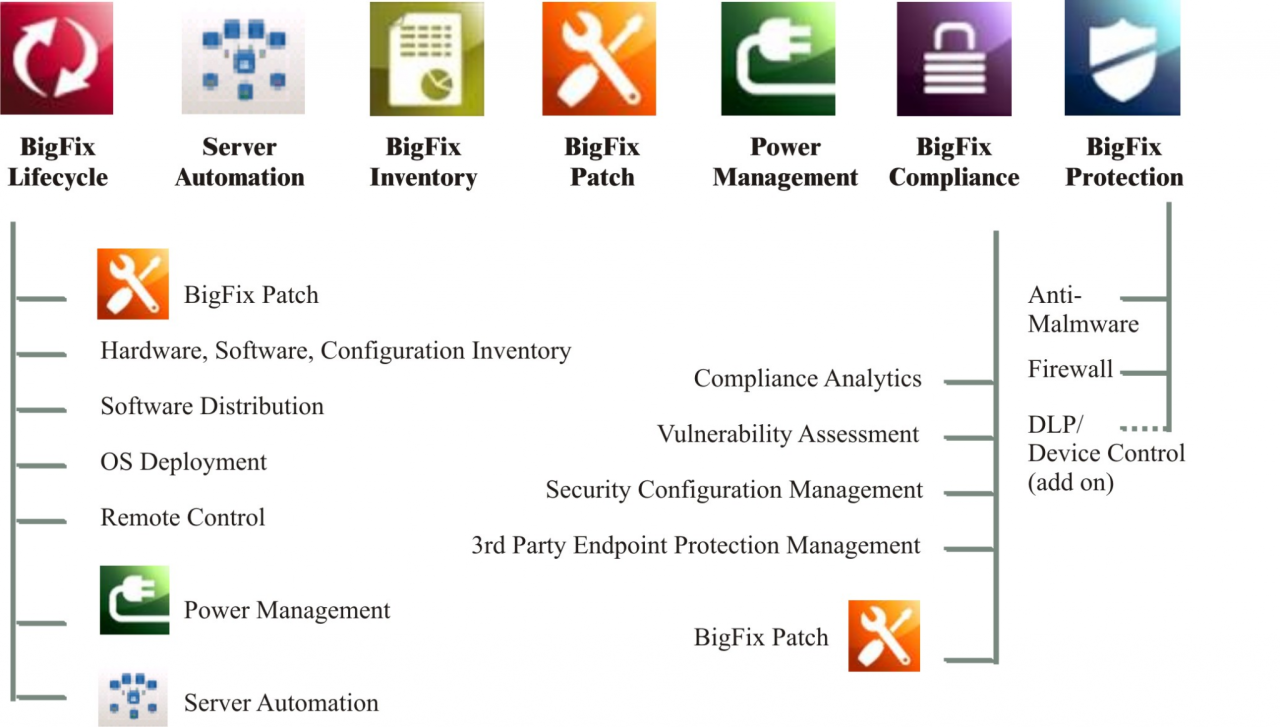
Integrating CyberFocus Security Analytics with BigFix 11 creates a powerful, proactive security posture. This combination leverages BigFix’s endpoint management capabilities with CyberFocus’s advanced threat detection and analysis, providing a comprehensive solution for identifying, responding to, and mitigating security risks across your entire IT infrastructure. The synergy significantly enhances visibility and reduces the time it takes to address critical security issues.CyberFocus enhances threat detection and response by correlating BigFix’s endpoint data with its own security intelligence.
This means that instead of relying solely on signature-based detection, the integrated solution can identify anomalies and suspicious activities based on behavioral patterns and contextual information gathered from across your endpoints. This proactive approach allows for faster identification of threats before they can cause significant damage.
Enhanced Threat Detection and Response Capabilities
The combined power of BigFix 11 and CyberFocus allows for a more comprehensive and efficient approach to security. BigFix provides detailed information about the software and hardware configurations of each endpoint, while CyberFocus analyzes network traffic and endpoint activity to identify potential threats. This combined data allows for the creation of detailed threat profiles, leading to more accurate and timely responses.
For example, a suspicious process detected by CyberFocus can be immediately investigated by examining the associated endpoint’s configuration and software inventory within BigFix, enabling faster triage and remediation.
Examples of Effectively Addressed Security Incidents, Unlocking the power of bigfix 11 and cyberfocus security analytics
Consider a scenario where CyberFocus detects a significant increase in outbound network traffic from a specific endpoint. By integrating with BigFix, security teams can quickly determine the affected machine’s operating system, installed software, and user activity. This information might reveal that the machine is running outdated software with known vulnerabilities, leading to the immediate deployment of patches via BigFix to mitigate the risk.
Similarly, a ransomware attack could be quickly contained by identifying infected machines via CyberFocus and isolating them from the network using BigFix’s remote control capabilities. The ability to quickly isolate infected systems and analyze the attack vector is critical to minimizing damage.
Key Metrics and Dashboards
The integrated platform enables the creation of informative dashboards visualizing critical security metrics. For example, a dashboard could display the number of high-risk vulnerabilities identified by BigFix, correlated with the number of suspicious activities detected by CyberFocus on machines with those vulnerabilities. Another dashboard could track the mean time to detect (MTTD) and mean time to respond (MTTR) for various types of security incidents, providing valuable insights into the effectiveness of the security operations.
Visualizations of endpoint compliance, threat trends, and incident response times offer a holistic view of the organization’s security posture.
Workflow for Investigating and Remediating a Security Breach
A typical workflow might begin with CyberFocus detecting anomalous behavior, such as a significant increase in failed login attempts or unusual file access patterns. This triggers an alert, providing the affected endpoint’s identifier. Security personnel then use BigFix to gather detailed information about the affected endpoint, including its software inventory, running processes, and user activity logs. Based on this information, they can determine the nature of the threat and take appropriate action, such as isolating the endpoint, deploying patches, or initiating a full forensic analysis.
BigFix’s remote control capabilities allow for real-time intervention, minimizing downtime and damage. Finally, the remediation process is tracked and analyzed, improving future response strategies.
Vulnerability Management and Remediation
BigFix 11, coupled with CyberFocus Security Analytics, offers a powerful solution for proactive vulnerability management and efficient remediation. This combination allows for the identification, prioritization, and patching of vulnerabilities across your entire IT infrastructure, significantly reducing your organization’s attack surface. The integration of these two tools provides a comprehensive approach, moving beyond simple vulnerability scanning to a more strategic and informed security posture.BigFix 11’s Vulnerability Identification and PrioritizationBigFix 11 utilizes a comprehensive database of known vulnerabilities, regularly updated to reflect the latest threat landscape.
It leverages this database to scan your endpoints and identify vulnerabilities present on each system. This process goes beyond simple identification; BigFix 11 assesses the severity of each vulnerability based on factors like CVSS scores and the potential impact on your business operations. This allows for prioritization, focusing remediation efforts on the most critical vulnerabilities first. The reporting capabilities within BigFix 11 provide clear visualizations of your vulnerability landscape, enabling informed decision-making.
Patch Deployment and Updates
Once vulnerabilities are identified and prioritized, BigFix 11 facilitates the streamlined deployment of patches and updates. The platform’s robust task management system allows administrators to create and deploy remediation tasks targeted at specific vulnerabilities or groups of systems. This targeted approach ensures efficient patch distribution and minimizes disruption to end-user operations. BigFix 11 also provides detailed reporting on patch deployment status, allowing administrators to monitor progress and identify any issues that may arise.
Automated deployment capabilities ensure that systems are patched promptly, reducing the window of vulnerability.
Comparison with Other Solutions
Compared to other vulnerability management solutions, BigFix 11 stands out due to its integrated approach. Many solutions require separate tools for vulnerability scanning, patch management, and reporting. BigFix 11 consolidates these functions into a single platform, streamlining the entire process. This integrated approach improves efficiency, reduces complexity, and lowers the overall cost of ownership. Furthermore, the depth of its endpoint management capabilities allows for granular control and targeted remediation, which is often lacking in less comprehensive solutions.
While some competitors offer similar features, the combination of powerful endpoint management with robust reporting and integration capabilities differentiates BigFix 11.
CyberFocus Security Analytics Contextualization
CyberFocus Security Analytics enhances BigFix 11’s vulnerability management capabilities by providing crucial context. By integrating data from various sources, CyberFocus can correlate vulnerabilities identified by BigFix 11 with other security events and indicators of compromise (IOCs). This allows security teams to understand the potential impact of a vulnerability within the broader security context of the organization. For instance, if a vulnerability is discovered on a system that has recently exhibited suspicious network activity, CyberFocus can highlight this connection, prioritizing remediation efforts.
This contextual information is crucial for effective risk management and incident response.
Automated Vulnerability Remediation Procedure
Automating vulnerability remediation is key to minimizing risk. A robust procedure combining BigFix 11 and CyberFocus can significantly enhance your organization’s security posture.
- Identify Vulnerabilities: Utilize BigFix 11 to scan endpoints and identify vulnerabilities, prioritizing based on severity and impact.
- Contextualize Findings: Integrate CyberFocus Security Analytics to analyze the identified vulnerabilities within the broader security context of the organization. This step helps prioritize the most critical and potentially exploited vulnerabilities.
- Create Remediation Tasks: In BigFix 11, create targeted remediation tasks to deploy patches or other fixes to address the identified vulnerabilities. These tasks should be tailored to specific systems or groups based on the contextual information from CyberFocus.
- Deploy and Monitor: Deploy the remediation tasks using BigFix 11. Monitor the deployment progress and address any issues that may arise. BigFix 11’s reporting capabilities provide real-time visibility into the remediation process.
- Verify Remediation: After deploying the patches, re-scan the systems with BigFix 11 to verify that the vulnerabilities have been successfully remediated.
- Continuous Monitoring: Continuously monitor your systems using BigFix 11 and CyberFocus to identify and address new vulnerabilities as they emerge. This proactive approach is essential for maintaining a strong security posture.
Incident Response and Forensics
BigFix 11 and CyberFocus Security Analytics form a powerful combination for efficient incident response and forensic investigations. Their integrated capabilities allow for rapid identification of compromised systems, collection of crucial evidence, and swift remediation, minimizing the impact of security breaches. This synergy streamlines the entire incident response lifecycle, from initial detection to post-incident analysis.BigFix 11’s ability to remotely execute commands on endpoints is invaluable for collecting forensic data.
This allows security teams to gather critical information from compromised machines without needing physical access, saving valuable time and resources during a critical incident. CyberFocus, meanwhile, provides the crucial context needed to understand the scope and nature of the attack.
Forensic Data Collection with BigFix 11
BigFix 11 can be leveraged to collect a wide array of forensic data from compromised endpoints. This includes, but isn’t limited to, memory dumps, registry hives, log files, network connection information, and running processes. Custom scripts can be deployed to gather specific data relevant to the nature of the incident. For example, a script could be used to collect all files accessed by a suspected malicious process, or to retrieve network traffic logs from a compromised machine.
The ability to target specific endpoints or groups of endpoints ensures that only relevant data is collected, minimizing the impact on system performance and reducing the volume of data that needs to be analyzed.
Root Cause Analysis with CyberFocus Security Analytics
CyberFocus Security Analytics plays a critical role in identifying the root cause of security incidents. By correlating data from various sources, including BigFix, it can identify patterns and anomalies that indicate malicious activity. This allows security analysts to quickly understand the attack vector, the extent of the compromise, and the potential impact on the organization. For example, CyberFocus might detect a surge in failed login attempts from a specific geographic location, which, when correlated with BigFix data showing unusual activity on certain endpoints, could pinpoint the source of a targeted attack.
Containing and Remediating Security Breaches
The integrated solution facilitates rapid containment and remediation of security breaches. Once CyberFocus identifies a threat, BigFix can be used to immediately deploy countermeasures. This might involve isolating compromised systems from the network, uninstalling malicious software, or patching vulnerabilities. For example, if CyberFocus detects malware spreading through a network, BigFix can be used to deploy an anti-malware scan and quarantine affected systems.
The automated nature of this process significantly reduces the response time and minimizes the potential damage.
Key Data Points for Incident Response
A comprehensive incident response process requires the collection of several key data points. This includes system logs (event logs, security logs, application logs), network traffic data, memory dumps from affected systems, registry keys, file system changes, and user activity logs. Additionally, information about the initial compromise vector (e.g., phishing email, malicious website), the malware used (if any), and the extent of data exfiltration is crucial for a thorough investigation and effective remediation.
Collecting this data allows security teams to reconstruct the timeline of the attack, identify vulnerabilities, and prevent future incidents.
Incident Response Checklist using BigFix 11 and CyberFocus
Before initiating any actions, ensure proper authorization and escalation procedures are followed.
- Identify and contain the incident: Use CyberFocus to identify affected systems and BigFix to isolate them from the network.
- Collect forensic data: Use BigFix to collect relevant logs, memory dumps, and other artifacts from compromised endpoints.
- Analyze the data: Use CyberFocus to correlate data from various sources and identify the root cause of the incident.
- Remediate the issue: Use BigFix to deploy patches, remove malware, and restore affected systems.
- Recover affected systems: Restore data from backups and ensure system functionality.
- Document the incident: Create a detailed report of the incident, including root cause, impact, and remediation steps.
- Implement preventative measures: Review security controls and implement changes to prevent future incidents.
Reporting and Compliance: Unlocking The Power Of Bigfix 11 And Cyberfocus Security Analytics
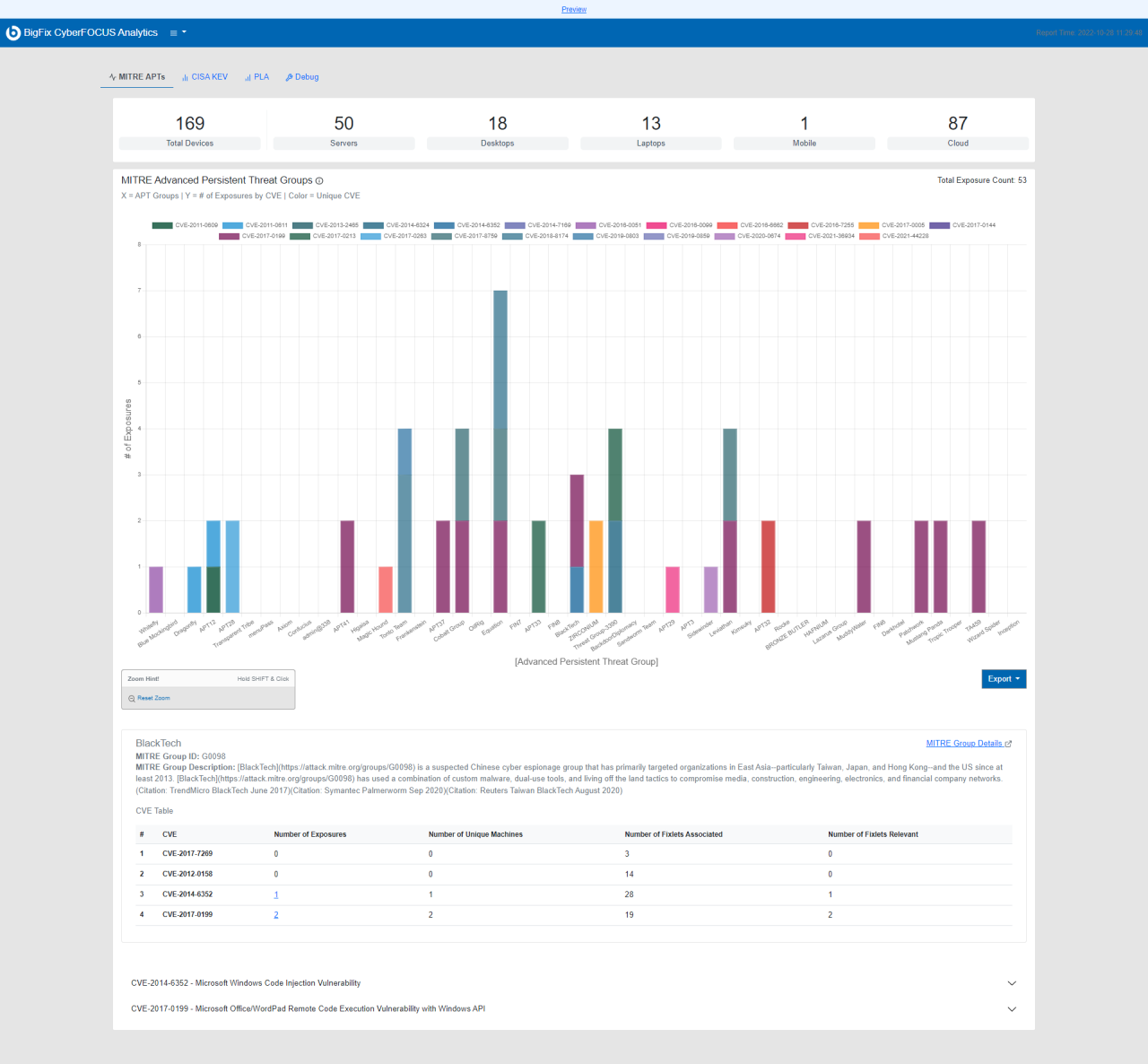
BigFix 11 and CyberFocus Security Analytics offer powerful reporting capabilities crucial for demonstrating compliance with various industry regulations and internal security policies. This combined solution provides a comprehensive view of your IT infrastructure’s security posture, allowing for proactive identification and remediation of vulnerabilities and efficient reporting on your compliance efforts. This functionality simplifies the often complex task of demonstrating compliance to auditors and stakeholders.
BigFix 11’s reporting engine leverages the extensive data collected on endpoint devices to generate customizable reports. These reports can cover a wide range of metrics, including software inventory, patch levels, security configuration compliance, and more. CyberFocus Security Analytics enhances this by providing advanced threat detection and analysis capabilities, allowing for the creation of reports that showcase the effectiveness of your security measures and the overall security posture of your organization.
This integrated approach streamlines the process of gathering evidence for compliance audits.
BigFix 11 Reporting Capabilities
BigFix 11 provides a robust reporting infrastructure. Pre-built reports are available covering key areas, such as patch compliance and software inventory. The system also allows for the creation of custom reports tailored to specific compliance requirements or internal audit needs. Users can define the scope of the report, select specific data points, and configure the report’s format (e.g., HTML, CSV, PDF).
This flexibility ensures that organizations can generate reports that precisely address their needs. Scheduled reporting functionality ensures that compliance data is consistently monitored and reported upon.
CyberFocus Security Analytics Contribution to Compliance
CyberFocus Security Analytics significantly contributes to regulatory compliance reporting by providing insights into security events and threats. Its advanced analytics capabilities help identify and analyze security incidents, allowing organizations to demonstrate their ability to detect, respond to, and recover from security breaches. This is crucial for meeting the requirements of regulations such as GDPR, HIPAA, and PCI DSS, which often mandate specific security incident response procedures and reporting mechanisms.
By integrating with BigFix 11, CyberFocus can enrich compliance reports with contextual security information, providing a more complete picture of the organization’s security posture.
Examples of Compliance Reports
The combined solution enables the generation of a variety of compliance reports. For example, a report on patch compliance might show the percentage of systems with critical patches applied, broken down by operating system and application. Another report could detail the configuration of security settings across endpoints, demonstrating adherence to security baselines. Incident response reports can showcase the effectiveness of incident detection and response procedures, documenting the timeline of events, remediation actions, and impact assessment.
These reports can be generated on demand or scheduled for regular automatic delivery.
Automatic Report Generation Configuration
Configuring BigFix 11 and CyberFocus to automatically generate reports involves scheduling tasks within each system. In BigFix 11, this is typically done through the console’s task scheduling features. Users define the report to be generated, the frequency of generation, and the recipients of the report. Similarly, CyberFocus Security Analytics offers scheduling capabilities for generating reports based on predefined queries or security event criteria.
The reports can be delivered via email, saved to a shared network location, or integrated into a centralized reporting dashboard. This automation ensures that compliance data is readily available and consistently monitored.
Sample Compliance Report
Below is a sample compliance report using hypothetical data, summarizing key compliance metrics.
| Metric | Value | Status | Notes |
|---|---|---|---|
| Critical Patch Compliance | 98% | Passing | 2% of endpoints require immediate patching. |
| Antivirus Software Up-to-date | 100% | Passing | All endpoints have the latest antivirus definitions. |
| Firewall Configuration Compliance | 95% | Warning | 5% of endpoints require firewall rule adjustments. |
| Security Event Response Time | < 1 hour | Passing | All security events were addressed within the defined SLA. |
Final Summary

BigFix 11 and CyberFocus Security Analytics, when combined, offer a truly transformative approach to IT security. By automating many tedious tasks, providing proactive threat detection, and offering unparalleled visibility into your IT infrastructure, this powerful pairing empowers you to significantly reduce your attack surface and enhance your overall security posture. It’s not just about reacting to threats; it’s about preventing them.
So, are you ready to unlock this power and take your security to the next level? Let’s get started!
FAQ Compilation
What are the system requirements for BigFix 11 and CyberFocus?
System requirements vary depending on your environment and scale. Check the official documentation for both BigFix 11 and CyberFocus for detailed specifications.
How much does the combined solution cost?
Pricing for both BigFix 11 and CyberFocus depends on factors like the number of managed endpoints and features utilized. Contact IBM or your respective vendor for accurate pricing information.
Is there a free trial available?
Contact IBM or your vendor to inquire about trial options for both BigFix 11 and CyberFocus. Trial availability may vary.
What kind of training is available for these tools?
Both IBM and CyberFocus likely offer training resources, including documentation, online courses, and potentially instructor-led training. Check their respective websites for details.