Unraveling the Differences Hashing, Salting, and Encryption Explained
Unraveling the differences hashing salting and encryption explained – Unraveling the differences hashing, salting, and encryption explained – it sounds like a techy puzzle, right? But understanding these core concepts is crucial for anyone concerned about online security, from protecting your passwords to safeguarding sensitive data. Think of it like this: hashing is like creating a one-way street, salting adds a detour to make it even harder to follow, and encryption is building a fortress around your data.
Let’s dive in and explore each one!
This post will break down the fundamentals of hashing, salting, and encryption, comparing and contrasting their methods and applications. We’ll explore different algorithms, discuss their strengths and weaknesses, and examine real-world examples of how they’re used to protect our information. By the end, you’ll have a much clearer understanding of how these essential security tools work and why they’re so important in today’s digital world.
Introduction to Hashing, Salting, and Encryption
In the world of cybersecurity, hashing, salting, and encryption are fundamental techniques used to protect sensitive data. Understanding their differences and individual strengths is crucial for implementing robust security measures. While all three involve transforming data, they achieve this through distinct methods and serve different purposes. This introduction will clarify the core concepts of each, highlighting their unique roles in data security.Hashing, salting, and encryption are like three different locks on a door.
Hashing is like a one-way lock – you can lock it, but you can’t unlock it without the key (which doesn’t exist in this case). Salting adds an extra layer of complexity to this one-way lock, making it even harder to pick. Encryption, on the other hand, is like a two-way lock – you can lock it and unlock it with the correct key.
Hashing
Hashing is a one-way cryptographic function that transforms any input data (regardless of size) into a fixed-size string of characters called a hash. The core purpose of hashing is data integrity verification. It’s designed so that even a tiny change in the input data results in a completely different hash value. This makes it ideal for checking if a file has been altered since it was last hashed.
For example, many software download sites provide checksums (hashes) alongside their downloads, allowing users to verify the integrity of the downloaded file. A mismatch between the calculated hash and the provided hash indicates file corruption or tampering. Common hashing algorithms include SHA-256 and MD5.
Salting
Salting enhances the security of password hashing by adding a random string of characters (the “salt”) to the password before hashing it. The primary purpose of salting is to protect against rainbow table attacks. Rainbow tables are pre-computed tables of hashes for common passwords. By adding a unique salt to each password before hashing, the attacker needs to create a separate rainbow table for each unique salt, significantly increasing the computational cost of cracking passwords.
The salt is typically stored alongside the hashed password, allowing for proper verification during login attempts.
Encryption, Unraveling the differences hashing salting and encryption explained
Encryption is a two-way cryptographic process that transforms readable data (plaintext) into an unreadable format (ciphertext) using an encryption key. The core purpose of encryption is confidentiality. Only someone with the correct decryption key can convert the ciphertext back into the original plaintext. Encryption is widely used to protect sensitive data at rest (e.g., data stored on a hard drive) and in transit (e.g., data transmitted over a network).
Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses separate keys for each process (a public key for encryption and a private key for decryption). Examples of encryption algorithms include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Hashing
Hashing is a fundamental cryptographic technique used to transform data of arbitrary size into a fixed-size string of characters, known as a hash value or digest. This process is one-way, meaning it’s computationally infeasible to reverse the hash to obtain the original data. This one-way property is crucial for many security applications.
The One-Way Nature of Hashing Algorithms
The irreversibility of hashing is its defining characteristic. While you can easily hash any input, recovering the original input from its hash is practically impossible for strong hashing algorithms. This is due to the complex mathematical functions employed within these algorithms. Even a tiny change in the input data results in a drastically different hash value, making it impossible to predict the original input based solely on the hash.
This property is vital for ensuring data integrity and for applications like password storage.
Common Hashing Algorithms
Several hashing algorithms exist, each with its own strengths and weaknesses. Two widely known examples are SHA-256 and MD5. SHA-256 (Secure Hash Algorithm 256-bit) is a more secure and widely used algorithm than MD5. MD5 (Message Digest Algorithm 5), while historically popular, is now considered cryptographically broken due to vulnerabilities that allow for collision attacks (finding two different inputs that produce the same hash).
Comparison of Hashing Algorithms
The following table compares several hashing algorithms based on their collision resistance and speed. Collision resistance refers to the difficulty of finding two different inputs that produce the same hash value. Speed refers to the efficiency of the algorithm in generating a hash. Note that these values are approximate and can vary depending on hardware and implementation.
| Algorithm | Collision Resistance | Speed | Notes |
|---|---|---|---|
| SHA-256 | Very High | Moderate | Widely used and considered secure. |
| SHA-512 | Very High | Slower than SHA-256 | Produces a 512-bit hash, offering even greater security. |
| MD5 | Very Low | Fast | Considered broken; vulnerable to collision attacks. Should not be used for security-sensitive applications. |
| SHA-1 | Low | Moderate | Deprecated; vulnerable to collision attacks. Should not be used for security-sensitive applications. |
Salting
Salting is a crucial technique in password security that significantly enhances the robustness of hashing algorithms. By adding a random string, the salt, to a password before hashing, we create a unique hash for each instance of the same password, even if multiple users choose the same password. This seemingly simple addition dramatically improves security and mitigates various attack vectors.Salting prevents rainbow table attacks, a significant threat to password security.
Rainbow tables are pre-computed tables of hashes for common passwords. Attackers use these tables to quickly reverse-engineer a password from its hash. However, because salting adds a unique random string to each password before hashing, the resulting hash is different for each user, even if they use the same password. This renders pre-computed rainbow tables useless, forcing attackers to compute hashes individually, making the attack computationally infeasible.
Salt Generation Methods
The effectiveness of salting depends heavily on the quality of the salt itself. A poorly generated salt can still leave the system vulnerable. Therefore, the salt should be randomly generated, sufficiently long (at least 128 bits is recommended), and unique for each password.Several methods exist for generating salts. One common approach involves using a cryptographically secure random number generator (CSPRNG).
These generators produce high-quality random numbers that are statistically unpredictable, ensuring the salt’s randomness. Another method involves using a hash function itself to generate a salt from a source of randomness, such as system time or other unpredictable data. However, this approach needs careful consideration to avoid predictable patterns. The generated salt should always be stored securely alongside the hashed password, typically in a database.
Hashing a Password with a Salt: A Step-by-Step Guide
Let’s illustrate the process with a simplified example using Python and the `bcrypt` library, a popular choice for password hashing that incorporates salting automatically. Note that this is a simplified example and real-world implementations often involve more robust security measures.
1. Import the `bcrypt` library
This provides the necessary functions for hashing and verifying passwords.
2. Generate a salt
Understanding the nuances between hashing, salting, and encryption is crucial for building secure applications, especially when dealing with sensitive data. This knowledge becomes even more important when considering the rapid advancements in app development, such as those discussed in this insightful article on domino app dev the low code and pro code future , where secure coding practices are paramount.
Ultimately, mastering these security concepts helps ensure the integrity and confidentiality of your data within any application, no matter the development approach.
`bcrypt.gensalt()` automatically generates a cryptographically secure salt. The optional `rounds` parameter controls the computational cost, influencing the time it takes to verify a password. Higher rounds increase security but slow down verification.
3. Hash the password
`bcrypt.hashpw(password.encode(‘utf-8’), salt)` hashes the password using the generated salt. The password is encoded to bytes before hashing.
4. Store the salt and hash
Both the salt and the resulting hash must be stored securely. This typically involves storing them in a database, alongside the user’s account information.
5. Password Verification
To verify a password, you hash the provided password using the stored salt and compare it to the stored hash. If they match, the password is valid. `bcrypt.checkpw(password.encode(‘utf-8’), stored_hash)` performs this comparison.
Example Python code (simplified):
import bcrypt
password = “MySecretPassword”
salt = bcrypt.gensalt()
hashed = bcrypt.hashpw(password.encode(‘utf-8’), salt)
#Store salt and hashed in a database
is_valid = bcrypt.checkpw(password.encode(‘utf-8’), hashed) # True if password matches
This step-by-step process demonstrates how salting enhances password security. The random salt ensures that even identical passwords produce unique hashes, effectively neutralizing rainbow table attacks and bolstering overall system security.
Encryption
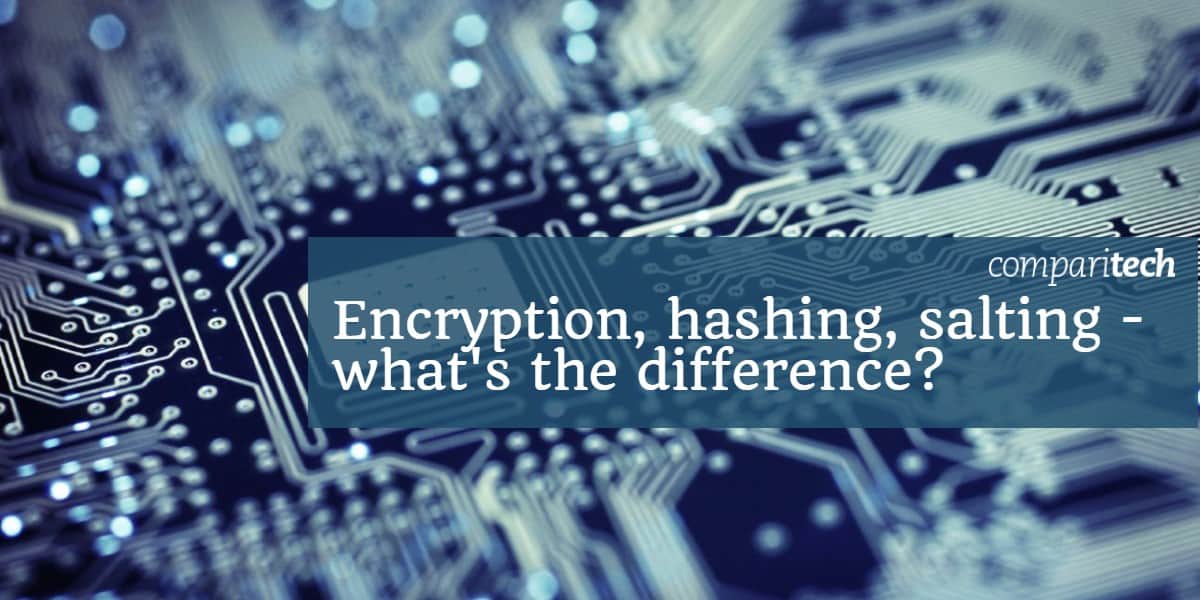
Encryption is the process of transforming readable data (plaintext) into an unreadable format (ciphertext) to protect its confidentiality. This transformation is achieved using an encryption algorithm and a key. Only those possessing the correct decryption key can revert the ciphertext back to its original form. Understanding the different types of encryption is crucial for choosing the appropriate method for securing sensitive information.
Symmetric and Asymmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption. This means the sender and receiver must both possess the same secret key. Examples include AES and DES. Asymmetric encryption, on the other hand, uses two separate keys: a public key for encryption and a private key for decryption. The public key can be widely distributed, while the private key must be kept secret.
RSA is a common example of asymmetric encryption. The key difference lies in key management; symmetric encryption requires secure key exchange, while asymmetric encryption simplifies this process by utilizing a public key.
Block and Stream Ciphers
Block ciphers operate on fixed-size blocks of data, encrypting each block independently. AES is a prime example of a block cipher, typically using 128-bit blocks. Stream ciphers, conversely, encrypt data one bit or byte at a time, creating a continuous stream of ciphertext. RC4 is a well-known example of a stream cipher, although it has fallen out of favor due to security vulnerabilities.
The main difference lies in their operational approach: block ciphers process data in chunks, while stream ciphers process it continuously.
AES Encryption and Decryption
Advanced Encryption Standard (AES) is a widely used symmetric block cipher. The process of encrypting data with AES involves several rounds of transformations on the input block. These transformations include substitution, permutation, and mixing operations, all governed by the encryption key. The number of rounds depends on the key size (128, 192, or 256 bits). Decryption is essentially the reverse process, using the same key to undo the transformations and recover the original plaintext.
For example, a 128-bit key AES encryption would involve multiple rounds of substitution and permutation operations, each controlled by a part of the key, resulting in a 128-bit ciphertext block. Decryption uses the same key and reverses these steps to retrieve the original 128-bit block.
Advantages and Disadvantages of Symmetric vs. Asymmetric Encryption
Before listing the advantages and disadvantages, it’s important to note that the choice between symmetric and asymmetric encryption often depends on the specific security needs and context. Factors like key management, performance requirements, and the number of communicating parties play a significant role in this decision.
- Symmetric Encryption:
- Advantages: Faster and more efficient than asymmetric encryption; suitable for encrypting large amounts of data.
- Disadvantages: Requires secure key exchange; key management can be complex with a large number of users.
- Asymmetric Encryption:
- Advantages: Simplifies key exchange; suitable for digital signatures and authentication.
- Disadvantages: Slower and less efficient than symmetric encryption; not ideal for encrypting large amounts of data.
Practical Applications and Use Cases
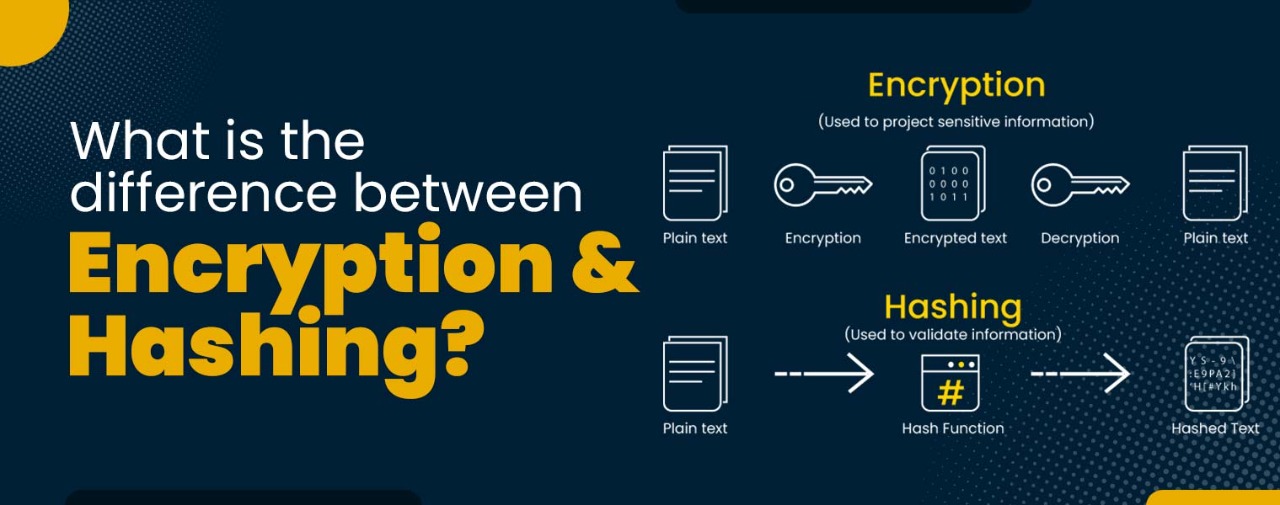
Hashing, salting, and encryption are fundamental cryptographic techniques with widespread applications in securing digital information and systems. Their proper implementation is crucial for maintaining data integrity, confidentiality, and user authentication. The choice of which technique, or combination of techniques, to employ depends heavily on the specific security requirements of the application.
Let’s explore some real-world examples demonstrating the practical use of these methods and the critical importance of selecting appropriate algorithms.
Password Security
Password storage is a prime example where hashing and salting are indispensable. Instead of storing passwords in plain text (a catastrophic security risk), websites and applications hash passwords before storing them. Salting adds a unique random string to each password before hashing, making it computationally infeasible to crack multiple passwords even if a database breach exposes the hashed values.
For instance, a common approach is to use bcrypt or Argon2, which are designed to be slow and resistant to brute-force attacks. The computational cost of these algorithms makes it difficult for attackers to try many password guesses within a reasonable timeframe. Using a weak hashing algorithm like MD5, which is now considered obsolete, would leave the system vulnerable.
Data Integrity Verification
Hashing plays a vital role in ensuring data integrity. A checksum or hash value is generated for a file or data set. Later, if the data is suspected of being altered, the hash can be recalculated and compared to the original. Any discrepancy indicates data corruption or tampering. This is used extensively in software distribution (verifying downloaded files haven’t been modified), blockchain technology (ensuring the integrity of transaction records), and file synchronization systems (detecting changes in files).
Secure Communication
Encryption is crucial for protecting sensitive information transmitted over networks. HTTPS, the secure version of HTTP, uses encryption (typically TLS/SSL) to encrypt the communication between a web browser and a server. This prevents eavesdroppers from intercepting and reading sensitive data like credit card numbers, login credentials, or personal information. The choice of encryption algorithm is critical; using outdated or weak ciphers like DES makes the communication vulnerable to attacks.
Modern protocols utilize strong, widely-vetted algorithms like AES.
Database Security
Databases often store sensitive information, requiring robust security measures. Encryption can protect data at rest (data stored on the database server) and in transit (data being transferred to and from the database). Database systems also use hashing and salting for password management and access control. Failure to properly secure databases can lead to devastating data breaches.
Digital Signatures
Digital signatures use asymmetric cryptography (a combination of public and private keys) to verify the authenticity and integrity of digital documents. Hashing is employed to create a digital fingerprint of the document. The sender then uses their private key to encrypt this hash, creating the digital signature. The recipient uses the sender’s public key to decrypt the hash and compare it to the hash of the received document.
This verifies both the integrity and the authenticity of the document, confirming it hasn’t been tampered with and originated from the claimed sender.
Computational Cost Comparison
The computational cost varies significantly between hashing, salting, and encryption. Hashing is generally the least computationally expensive, followed by salting (which adds minimal overhead to hashing). Encryption, especially asymmetric encryption, is significantly more computationally intensive. This is why it’s crucial to select algorithms appropriately. Using computationally expensive algorithms for tasks where speed is paramount might lead to performance bottlenecks.
For example, using AES-256 encryption for every single database query might slow down the application considerably, while using it to encrypt sensitive data at rest might be perfectly acceptable.
Security Implications of Weak Algorithms
Employing weak or outdated cryptographic algorithms exposes systems to significant security risks. Algorithms like MD5 and SHA-1 for hashing, or DES for encryption, are now considered cryptographically broken due to advancements in cryptanalysis techniques. Using these obsolete algorithms can allow attackers to easily reverse the hashing process, decrypt encrypted data, or forge digital signatures, compromising data integrity and confidentiality.
Staying up-to-date with the latest cryptographic recommendations and using strong, well-vetted algorithms is paramount for robust security.
Visual Representation of the Processes: Unraveling The Differences Hashing Salting And Encryption Explained
Visual aids can significantly improve understanding of complex cryptographic processes. Let’s explore visual representations of password hashing with salting and symmetric encryption. These illustrations will help clarify the steps involved and highlight the key differences between these security mechanisms.
Password Hashing with Salting
Imagine a simple flowchart. The process begins with a user’s password, represented by a simple text box containing “MySecretPassword”. An arrow points to a box labeled “Salt Generator,” which outputs a random string of characters, visualized as a jumbled sequence of letters and numbers (“gH7$%kL2”). This salt is then concatenated with the password, represented by combining the text box contents with the salt sequence to form a single string: “MySecretPasswordgH7$%kL2”.
This combined string then enters a box labeled “Hashing Algorithm” (e.g., SHA-256). Inside this box, a complex mathematical function transforms the input string into a fixed-length string of seemingly random characters, the hash, visualized as a long, hexadecimal string (“a1b2c3d4e5f6…”). This hash is then stored in a database, represented by a database icon. The original password and the salt are not directly stored.
Only the hash is retained. During authentication, the user’s entered password is combined with the stored salt, then hashed using the same algorithm. If the resulting hash matches the stored hash, authentication is successful. If they don’t match, access is denied. The visual emphasizes the one-way nature of hashing and the crucial role of the salt in enhancing security.
Symmetric Encryption and Decryption
Our visual for symmetric encryption uses two boxes, one labeled “Plaintext” and the other “Ciphertext”. The plaintext box contains the message to be encrypted, represented by a simple sentence, “This is a secret message”. An arrow connects this box to a central box labeled “Encryption Algorithm” (e.g., AES). This box also takes as input a key, represented by a separate box containing a long, random string of characters.
Inside the encryption algorithm box, the plaintext and the key are processed through a complex mathematical function. The output, the ciphertext, is a seemingly random string of characters, which is visualized in the Ciphertext box. This ciphertext is then transmitted or stored securely. Decryption mirrors this process. The Ciphertext box is connected to a box labeled “Decryption Algorithm” (using the same algorithm as encryption, AES in this case).
This box also receives the same key as input. The decryption algorithm processes the ciphertext and the key, reversing the encryption process and producing the original plaintext message in the “Plaintext” box. The visual emphasizes the importance of keeping the key secret to ensure the security of the encrypted message. Both encryption and decryption use the same key; hence, the term “symmetric”.
Final Review

So, there you have it – a whirlwind tour through the fascinating world of hashing, salting, and encryption! While the details can get complex, the core concepts are relatively straightforward. Remember, understanding these techniques empowers you to make more informed decisions about your online security. Choosing strong passwords, utilizing reputable services, and staying updated on the latest security practices are all vital steps in protecting yourself in the digital age.
Hopefully, this post has demystified these important concepts and given you a solid foundation to build upon.
Answers to Common Questions
What’s the difference between a hash and a checksum?
While both involve creating a unique digital fingerprint, checksums primarily detect data corruption during transmission, while hashes are used for security purposes like password storage and data integrity verification. Hashes are generally more complex and computationally expensive.
Are all hashing algorithms equally secure?
No. Some algorithms, like MD5, are considered outdated and vulnerable to collisions (producing the same hash for different inputs). SHA-256 and newer algorithms are generally considered more secure.
Can encryption be broken?
Theoretically, yes, all encryption can be broken given enough time and computing power. However, strong encryption algorithms, used with proper key management, make breaking the encryption practically infeasible for most attackers.
Why is salting important for passwords?
Salting prevents attackers from using pre-computed rainbow tables to crack passwords. Each salt is unique, making it impossible to create a single table to crack multiple salted passwords.