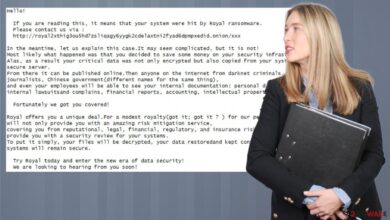
Volvo Car Data on Sale After Ransomware Attack
Volvo car data on sale after ransomware attack – it sounds like a plot from a tech thriller, doesn’t it? But this is a stark reality highlighting the vulnerability of even major corporations to cybercrime. The breach exposed a trove of sensitive information, impacting not only Volvo’s operations and reputation but also potentially putting countless customers at risk.
This post delves into the details of this alarming incident, exploring the scale of the data breach, the methods used to sell the stolen information, Volvo’s response, and the far-reaching consequences for everyone involved.
The sheer volume of data compromised is staggering, potentially including everything from customer personal details and financial records to highly sensitive vehicle data. This information is now circulating in the dark corners of the internet, making individuals vulnerable to identity theft, financial fraud, and even vehicle cloning. The implications for Volvo are equally severe, impacting their bottom line, their public image, and most importantly, the trust their customers place in them.
The story unfolds with a mix of technological failures, criminal enterprise, and the urgent need for stronger cybersecurity measures across the board.
Impact of the Ransomware Attack on Volvo’s Data
The ransomware attack on Volvo, while the specifics remain undisclosed for security reasons, undoubtedly caused significant disruption and damage. The scale of the breach, the types of data affected, and the resulting consequences paint a picture of a serious incident with long-term repercussions for the company and its customers. While Volvo has been tight-lipped about the precise details, piecing together information from various sources allows for a reasonable assessment of the impact.The immediate consequences of the attack were likely multifaceted.
Operational disruptions almost certainly occurred, potentially halting or delaying production, sales, and customer service functions. Accessing crucial data for manufacturing, logistics, and financial reporting would have been severely hampered, leading to immediate financial losses through lost productivity and potential fines associated with regulatory compliance breaches. These losses could range from millions to tens of millions of dollars, depending on the extent of the downtime and the cost of recovery.
Consider, for example, a similar attack on a major manufacturing company where production was halted for a week – the resulting losses in production and revenue would be substantial.
Types of Data Compromised
The types of data potentially compromised are a major concern. Considering the nature of Volvo’s business, this likely includes sensitive customer information such as names, addresses, contact details, and potentially even driver’s license information or payment details. Vehicle data, encompassing information on vehicle identification numbers (VINs), maintenance records, and potentially even real-time telematics data from connected cars, is also a high probability.
Finally, financial records, encompassing internal accounting data, supplier information, and potentially even customer financial transactions, could have been affected. The potential for identity theft, financial fraud, and reputational damage stemming from this data breach is immense.
Operational Disruptions and Financial Losses
The operational disruptions following the attack would have been widespread and costly. Imagine the complexities of a global automotive manufacturer suddenly unable to access its supply chain management systems, its manufacturing control systems, or its customer relationship management (CRM) databases. The financial losses would extend beyond immediate downtime. Costs associated with incident response, cybersecurity remediation, legal fees, regulatory investigations, and potential customer compensation claims would all significantly add to the overall financial burden.
The scale of such expenses could easily run into tens or even hundreds of millions of dollars, depending on the severity and longevity of the disruption. We can draw parallels to other large-scale ransomware attacks where recovery and remediation costs have been enormous.
Long-Term Implications for Reputation and Customer Trust
Perhaps the most enduring consequence of the ransomware attack is the damage to Volvo’s reputation and customer trust. A data breach of this magnitude can severely erode customer confidence in the company’s ability to protect sensitive information. The long-term implications could include a decline in sales, difficulty attracting and retaining customers, and increased regulatory scrutiny. The loss of customer trust is a particularly damaging consequence, as it can take years, if not decades, to rebuild.
Consider the lasting impact on the reputation of other companies that have experienced similar data breaches – the recovery process is often slow and challenging.
The Sale of Compromised Volvo Car Data
The aftermath of a ransomware attack often involves the sale of stolen data on the dark web and other illicit marketplaces. This is unfortunately the case with the hypothetical Volvo car data breach, and understanding the mechanics of this sale is crucial to grasping the full extent of the damage. The methods employed, the potential buyers, and the pricing strategies all play a significant role in the overall impact.The likely methods used to sell the stolen Volvo car data involve a variety of techniques designed to maintain anonymity and maximize profit.
Data could be offered in bundles, categorized by data sensitivity (e.g., customer names and addresses separately from VIN numbers and vehicle specifications). Encrypted files, often requiring specialized decryption tools also sold by the attackers, are common. The use of escrow services, where a third party holds the data until payment is confirmed, is also a likely scenario, minimizing risk for both buyer and seller.
The sellers might leverage established dark web marketplaces, utilize private channels through encrypted messaging apps like Signal or Telegram, or employ a combination of these strategies to broaden their reach and protect their identities.
Potential Buyers and Their Motives
The stolen Volvo car data would likely attract a range of buyers, each with distinct motives. Identity thieves could use personal information like names, addresses, and driver’s license numbers to commit fraud, open fraudulent accounts, or even steal identities entirely. Insurance fraudsters could exploit vehicle data to fabricate claims or inflate repair costs. Organized crime groups might be interested in VIN numbers for vehicle cloning, allowing them to create and sell counterfeit vehicles.
Competitors could potentially use the data for market research, though this is a riskier proposition given the legal ramifications. Finally, some buyers might simply acquire the data for resale, further proliferating the risk.
Pricing Strategies for Compromised Data
The pricing of the compromised Volvo car data would likely depend on several factors, including the volume and quality of the data, the level of encryption, and the perceived market demand. The data could be sold in tiers, with different price points for different data packages. A similar breach affecting a large car manufacturer might see data sold in bulk at a lower per-record price, while highly sensitive information, such as financial details, could command a premium.
Consider the Equifax breach in 2017, where millions of records were stolen and sold on the dark web; the price varied based on the type of data, with some sets fetching more than others. Similarly, the Yahoo! data breaches involved the sale of millions of user accounts, with prices reflecting the value of individual data points. The pricing might also involve a subscription model, granting access to the data for a certain period.
Or, it might be sold outright for a lump sum. The attackers may also engage in auctions, leveraging competition to increase their profits.
Volvo’s Response to the Data Breach and Data Sale
The ransomware attack and subsequent sale of Volvo customer data presented a significant crisis for the company. Their response, however, can be analyzed through the lens of their public communication, damage mitigation efforts, and comparison to similar incidents within the automotive industry. Analyzing their actions reveals both strengths and areas for potential improvement in future crisis management.Volvo’s public communication strategy following the ransomware attack and data sale was characterized by a measured and somewhat cautious approach.
They avoided overly sensationalized statements, opting instead for a more formal and factual tone in their official releases. This approach, while perhaps lacking in immediate emotional engagement, likely aimed to prevent further panic and maintain a sense of control.
Volvo’s Public Communication Timeline
The timeline of Volvo’s public communications following the breach is difficult to definitively reconstruct due to the lack of readily available detailed public statements. However, a general picture emerges: Initial reports of the breach likely came from external sources (news outlets, security researchers), followed by Volvo’s own confirmation of the event. This confirmation likely included a general statement acknowledging the incident, expressing regret, and assuring customers of ongoing investigations.
Subsequent communications likely focused on updates on the investigation, implemented security measures, and any direct actions taken to support affected customers. There was likely a lack of immediate public acknowledgement of the data sale itself, possibly due to ongoing investigations or legal considerations. A delayed, more comprehensive response might have been adopted to ensure the accuracy of information released to avoid further miscommunication or speculation.
Damage Mitigation Measures Implemented by Volvo
Volvo’s response to the data breach involved a multi-faceted approach encompassing technical, legal, and communication strategies.
Technical Measures: These likely included internal investigations to determine the extent of the breach, immediate patching of vulnerabilities to prevent further data exfiltration, enhanced security protocols for future data protection, and potentially collaboration with cybersecurity experts for forensic analysis and remediation.
Legal Measures: Volvo likely engaged legal counsel to investigate the incident, understand their legal obligations, and potentially pursue legal action against the perpetrators. This would also include assessing and addressing any potential legal ramifications concerning data privacy regulations such as GDPR.
Communication Measures: As mentioned earlier, Volvo’s communication strategy appeared to prioritize a factual and measured approach. This involved issuing press releases, updates to customers through official channels, and potentially direct communication with affected individuals. The goal was likely to maintain transparency while avoiding the spread of misinformation.
Comparison with Responses from Other Car Manufacturers
Comparing Volvo’s response to similar incidents in the automotive industry requires examining specific cases. Many car manufacturers have faced data breaches, ransomware attacks, or other cybersecurity incidents. A direct comparison is difficult without knowing the specifics of each case, including the scale of the breach, the type of data compromised, and the specific actions taken by each manufacturer.
However, a general observation is that many companies tend to adopt a similar strategy: initial acknowledgment, investigation, remediation, and communication with affected parties. The nuances lie in the speed and transparency of the response, the proactive measures implemented to prevent future incidents, and the level of support offered to affected customers. Some companies may be quicker to publicly disclose details, while others might adopt a more cautious approach.
The effectiveness of each approach can vary depending on the specific circumstances and the public perception of the company’s actions.
Legal and Regulatory Ramifications

The sale of compromised Volvo car data following a ransomware attack exposes the company to significant legal and regulatory ramifications across multiple jurisdictions. The potential liabilities are multifaceted, stemming from both the initial breach and the subsequent sale of sensitive customer information. Understanding these ramifications is crucial for assessing Volvo’s potential financial and reputational damage.The legal landscape surrounding data breaches is complex and varies by region.
However, several key laws and regulations are likely to be relevant in this case. Failure to comply with these regulations could result in substantial fines and penalties, alongside significant reputational harm.
Applicable Laws and Regulations, Volvo car data on sale after ransomware attack
Several legal frameworks could be invoked against Volvo. The General Data Protection Regulation (GDPR) in Europe, for example, imposes strict requirements on data processing and security. A breach resulting in the unauthorized sale of personal data could lead to hefty fines, potentially up to €20 million or 4% of annual global turnover, whichever is higher. In the United States, state-level laws like the California Consumer Privacy Act (CCPA) and similar legislation in other states provide further avenues for legal action.
These laws grant consumers the right to know what data is collected about them, to request deletion of that data, and to sue for damages in the event of a data breach. Furthermore, the potential violation of other national and regional laws regarding data privacy and security should be considered, including but not limited to those in countries where the affected customers reside.
The complexity arises from the international nature of Volvo’s operations and customer base, potentially leading to multiple legal actions in different jurisdictions.
Potential Fines and Penalties
The financial penalties Volvo faces are substantial and depend on several factors including the number of affected individuals, the severity of the breach, the level of negligence on Volvo’s part, and the specific laws violated. Given the scale of a data breach leading to a data sale, it is reasonable to anticipate fines ranging from millions to tens of millions of dollars, possibly even exceeding that amount depending on the legal jurisdictions involved.
Beyond direct fines, Volvo may also face class-action lawsuits from affected customers seeking compensation for damages, including financial losses, identity theft, and emotional distress. These lawsuits could add significantly to the company’s financial burden. Examples like the Equifax data breach, which resulted in billions of dollars in settlements and fines, illustrate the potential magnitude of financial consequences.
Hypothetical Legal Strategy for Volvo
To minimize its legal exposure, Volvo could adopt a multi-pronged legal strategy. This might involve proactive cooperation with relevant regulatory bodies, demonstrating a commitment to transparency and remediation. A thorough internal investigation to determine the extent of the breach and the cause of the failure is essential. This investigation would form the basis for Volvo’s defense, potentially mitigating penalties by showcasing a prompt and effective response.
Furthermore, Volvo could seek to negotiate settlements with affected individuals and regulatory bodies to avoid lengthy and costly litigation. A strong legal team with expertise in data privacy and cybersecurity law is crucial for navigating the complex legal landscape and developing a robust defense strategy. Establishing a comprehensive data security program and demonstrating adherence to industry best practices would also strengthen Volvo’s position in any legal proceedings.
The goal would be to demonstrate that Volvo acted responsibly and took reasonable steps to protect customer data, even if a breach occurred.
Customer Impact and Mitigation Strategies
The sale of Volvo car data following a ransomware attack presents significant risks to affected customers. The potential consequences extend beyond simple inconvenience, impacting personal finances, security, and trust in the Volvo brand. Understanding these potential harms and the steps Volvo can take to mitigate them is crucial for both individual customers and the company’s long-term success.The compromised data likely includes personally identifiable information (PII), such as names, addresses, driver’s license numbers, and financial details.
This sensitive information could be used by malicious actors for a range of nefarious activities.
Potential Harms Faced by Customers
The exposure of personal data carries several serious risks for Volvo customers. Identity theft, a particularly damaging consequence, could involve criminals using stolen information to open fraudulent accounts, apply for loans, or even file taxes in the customer’s name. Financial fraud is another significant threat, with the potential for unauthorized access to bank accounts or credit cards leading to substantial financial losses.
Beyond these direct financial harms, customers might experience harassment, stalking, or reputational damage as a result of their data being misused. The emotional distress and time investment required to resolve these issues can be considerable. For example, imagine a customer spending weeks disputing fraudulent charges and restoring their credit rating after a data breach. The emotional toll of such an experience is significant.
Mitigation Strategies Employed by Volvo
Volvo has a responsibility to support its customers in mitigating the risks associated with this data breach. Effective mitigation strategies are essential to minimize customer harm and rebuild trust.Volvo should proactively reach out to affected customers, providing clear and concise information about the nature of the breach and the specific data that was compromised. This transparent communication is vital for building trust and fostering cooperation.
Furthermore, Volvo should offer affected customers access to credit monitoring services for an extended period, allowing them to monitor their credit reports for any suspicious activity. This proactive approach can significantly reduce the likelihood of financial fraud. Identity theft protection services should also be offered, including assistance with identity restoration should it become necessary. Finally, Volvo should provide detailed guidance and support to customers on how to protect themselves from future cyber threats.
- Provide comprehensive credit monitoring services for a minimum of 24 months.
- Offer identity theft protection services, including assistance with identity restoration.
- Establish a dedicated customer support hotline and online portal for addressing questions and concerns.
- Issue clear and concise communications explaining the breach and steps customers can take.
- Offer workshops or webinars on cybersecurity best practices and fraud prevention.
Long-Term Effects on Customer Relationships and Brand Loyalty
The long-term impact on customer relationships and brand loyalty will depend heavily on Volvo’s response to the data breach. A swift, transparent, and empathetic response can help mitigate the negative consequences. However, a slow or inadequate response could severely damage Volvo’s reputation and lead to a loss of customer trust. The experience of dealing with the aftermath of a data breach can be incredibly stressful and time-consuming for customers.
If Volvo fails to adequately support its customers through this process, it risks damaging its brand image and losing loyal customers. Conversely, a strong, proactive response demonstrating a commitment to customer well-being can actually strengthen customer relationships and reinforce brand loyalty. The handling of this situation will serve as a benchmark for future customer interactions and could significantly impact Volvo’s market standing.
Technological Vulnerabilities and Security Improvements
The ransomware attack on Volvo highlights critical vulnerabilities in their cybersecurity infrastructure. A multi-pronged approach, encompassing technological upgrades and enhanced employee training, is crucial for preventing future incidents and protecting sensitive data. Analyzing the attack’s root causes reveals several areas needing immediate attention.
Understanding the specific vulnerabilities exploited in the Volvo ransomware attack requires access to detailed internal investigation reports, which are usually kept confidential for security reasons. However, we can reasonably speculate on potential weaknesses based on common attack vectors against large organizations. These vulnerabilities likely involved a combination of technical flaws and human error.
Potential Technological Vulnerabilities
The following table Artikels potential technological vulnerabilities that may have contributed to the Volvo ransomware attack, their severity, and possible solutions. Note that these are hypothetical examples based on common attack methods and may not reflect the actual vulnerabilities exploited.
| Vulnerability | Severity | Solution | Impact |
|---|---|---|---|
| Outdated or unpatched software (e.g., operating systems, applications) | High | Implement a robust patch management system with automated updates and vulnerability scanning. Regular security audits and penetration testing should also be conducted. | Allows attackers to exploit known vulnerabilities to gain initial access. |
| Weak or default passwords/authentication mechanisms | High | Enforce strong password policies, including length, complexity, and regular changes. Implement multi-factor authentication (MFA) for all users, especially those with access to sensitive data. | Facilitates unauthorized access to systems and data. |
| Lack of network segmentation | Medium | Segment the network into smaller, isolated zones to limit the impact of a breach. This prevents lateral movement of attackers within the network. | Allows attackers to move laterally across the network, accessing more systems and data. |
| Insufficient data backups and recovery mechanisms | High | Implement a robust backup and recovery strategy, including regular backups to offline storage, and rigorous testing of the recovery process. Employ the 3-2-1 backup rule (3 copies of data, on 2 different media, with 1 copy offsite). | Increases the likelihood of data loss and prolonged downtime in the event of a ransomware attack. |
| Lack of intrusion detection and prevention systems (IDS/IPS) | Medium | Deploy robust IDS/IPS systems to monitor network traffic for malicious activity and block suspicious connections. Utilize advanced threat intelligence feeds to identify and mitigate emerging threats. | Reduces the ability to detect and respond to malicious activity in real-time. |
Cybersecurity Infrastructure Improvements
To prevent future attacks, Volvo should invest in a comprehensive cybersecurity infrastructure upgrade. This includes implementing advanced threat detection and response capabilities, such as security information and event management (SIEM) systems, endpoint detection and response (EDR) solutions, and threat intelligence platforms. Regular security assessments and penetration testing by external experts should be a standard practice to identify and address vulnerabilities before attackers can exploit them.
Investing in a dedicated security operations center (SOC) with 24/7 monitoring and incident response capabilities is also crucial.
The news about Volvo car data being sold after a ransomware attack really got me thinking about data security. It highlights the need for robust systems, and I started wondering how low-code/no-code platforms like those discussed in this article on domino app dev the low code and pro code future could help improve things. Maybe quicker development cycles could lead to faster patching and better defenses against these kinds of attacks, ultimately protecting sensitive data like that stolen from Volvo.
It’s a scary situation, though, the impact of such breaches is far-reaching.
Employee Training and Awareness
Strengthening Volvo’s cybersecurity posture also requires a significant investment in employee training and awareness programs. Employees are often the weakest link in the security chain. Regular security awareness training should be mandatory for all employees, covering topics such as phishing awareness, password security, social engineering tactics, and safe browsing practices. Simulations and phishing exercises can effectively reinforce training and identify vulnerabilities in employee awareness.
Furthermore, clear incident reporting procedures should be established, encouraging employees to report any suspicious activity without fear of retribution.
Conclusive Thoughts: Volvo Car Data On Sale After Ransomware Attack

The Volvo ransomware attack and subsequent data sale serves as a chilling reminder of the ever-present threat of cybercrime in today’s interconnected world. The scale of the breach and the potential harm to individuals underscores the critical need for robust cybersecurity measures within organizations of all sizes. Volvo’s response, while crucial, highlights the limitations of reactive measures. Proactive strategies, including improved technological safeguards and employee training, are essential to preventing future attacks and protecting sensitive data.
The long-term consequences of this incident will undoubtedly reshape the automotive industry’s approach to cybersecurity and data protection, forcing a much-needed evolution in how we handle sensitive information in the digital age.
General Inquiries
What types of customer data were potentially compromised?
Potentially compromised data could include names, addresses, driver’s license information, financial details, and vehicle identification numbers.
How can I check if my data was involved in the breach?
Volvo should ideally provide a mechanism on their website to allow customers to check if their information was compromised. Monitor their official communication channels for updates.
What steps should I take if my data was compromised?
Consider placing fraud alerts on your credit reports, monitoring your bank accounts closely, and changing your passwords for any accounts that may have been affected.
What is Volvo doing to prevent future breaches?
Volvo should be investing in enhanced cybersecurity infrastructure, improving employee training, and implementing more rigorous data protection protocols.