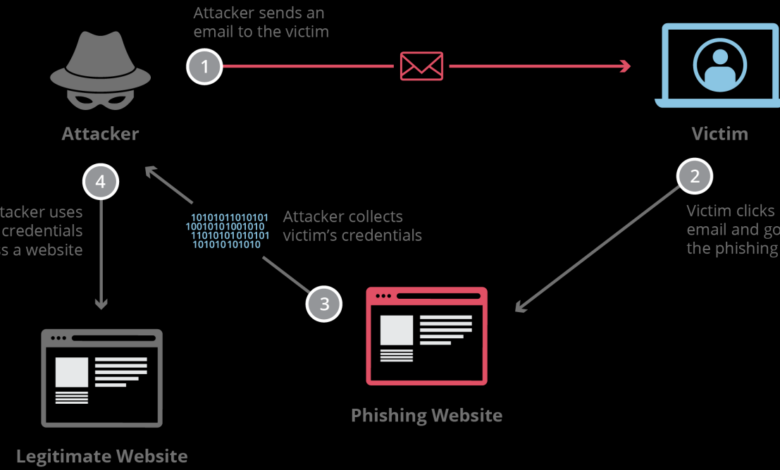
What is Simulated Phishing?
What is simulated phishing? It’s essentially a controlled attack used to test your organization’s security awareness and preparedness. Unlike real phishing, which aims to steal data, simulated phishing aims to educate and strengthen defenses. Think of it as a security fire drill – a planned disruption to identify weaknesses before a real threat exploits them. This allows companies to proactively shore up vulnerabilities and improve employee training, ultimately reducing the risk of successful real-world phishing attacks.
By simulating various types of phishing attacks—from deceptive emails and SMS messages to convincing fake websites—organizations can gauge their employees’ susceptibility to social engineering tactics. The results reveal critical vulnerabilities, highlighting areas needing improvement in security awareness training and internal policies. This proactive approach saves companies significant time, money, and reputational damage in the long run.
Definition of Simulated Phishing
Simulated phishing, also known as phishing simulations or mock phishing attacks, are controlled exercises designed to assess the vulnerability of an organization’s employees to real-world phishing attempts. Unlike real phishing attacks which aim to steal data or install malware, simulated phishing tests the effectiveness of security awareness training and existing security measures. The goal isn’t to cause harm, but to identify weaknesses and improve overall security posture.Simulated phishing differs significantly from real phishing attacks in its intent and consequences.
While real phishing is malicious and aims to compromise systems or steal sensitive information, simulated phishing is a controlled, ethical test. The attacker is known, the impact is minimal, and the primary goal is to learn from the results to improve security. A key characteristic is the pre-planned nature of the attack; the recipients are aware (or should be) that a test is taking place, albeit often unaware of the precise timing or method.
Goals of Simulated Phishing Exercises
The primary goal of conducting simulated phishing exercises is to identify vulnerabilities within an organization’s security awareness training and employee behavior. By observing which employees fall for the simulated phishing attempt, organizations can better understand the effectiveness of their current training programs and identify areas for improvement. Secondary goals include assessing the effectiveness of security controls such as email filters and security awareness training programs, measuring the overall level of employee awareness and susceptibility to phishing attacks, and providing data-driven insights for improving security practices.
For example, a high click-through rate on a simulated phishing email might indicate a need for more comprehensive training on identifying phishing attempts.
Comparison of Simulated and Real-World Phishing Attacks
| Feature | Simulated Phishing | Real-World Phishing |
|---|---|---|
| Intent | Assess employee awareness and security controls | Steal data, install malware, compromise systems |
| Attacker | Known, internal security team | Unknown, malicious actor |
| Impact | Minimal, no data breach | Potentially severe, data breach, financial loss, reputational damage |
| Notification | Employees may be informed beforehand or after the test | Employees are unaware of the attack |
| Consequences | Improved security awareness and training | Data loss, financial losses, legal repercussions |
| Example | A simulated email mimicking a bank asking for login credentials | A malicious email appearing to be from a trusted source, leading to malware installation |
Types of Simulated Phishing Attacks
Simulated phishing attacks are crucial for security awareness training. Understanding the different types helps organizations prepare realistic and effective training programs that mirror real-world threats. These simulations allow employees to experience firsthand the subtle tactics used by phishers, improving their ability to identify and report suspicious activity.
Simulated phishing attacks can take many forms, leveraging various communication channels and social engineering techniques. By understanding these variations, organizations can tailor their training to address the specific threats they face. The key is to make the simulations as realistic as possible, without actually compromising security.
Email Simulated Phishing Attacks
Email remains a primary vector for phishing attacks. Simulated email phishing attacks mimic the look and feel of legitimate emails from known organizations, often using spoofed addresses and compelling subject lines. These simulations can include malicious links leading to fake login pages or attachments containing malware.
For example, a simulated phishing email might appear to be from a company’s IT department, requesting users to update their passwords by clicking a link. The link would lead to a fake login page designed to capture user credentials. The impact of a successful attack could range from compromised accounts to data breaches and financial losses. A successful simulation, however, strengthens employee vigilance against these types of attacks.
SMS Simulated Phishing Attacks (Smishing)
Smishing, or SMS phishing, uses text messages to deliver malicious links or requests for sensitive information. These attacks often create a sense of urgency, prompting quick action from the recipient before they can critically assess the message’s authenticity.
An example might be a text message claiming that a user’s bank account has been compromised and requires immediate action to prevent account closure. The message would include a link to a fake website designed to steal banking credentials. The potential impact of a successful smishing attack is similar to email phishing, including financial loss, identity theft, and reputational damage.
A well-designed simulation helps employees recognize and avoid these types of threats.
Website Simulated Phishing Attacks
Website-based simulated phishing attacks involve creating convincing replica websites of legitimate organizations. These fake websites often mirror the design and functionality of the real site, making it difficult for users to distinguish them from the authentic version.
For instance, a simulated phishing website might mimic a popular online retailer’s login page. Users who enter their credentials on this fake site will unknowingly provide their information to the attacker. The impact could be significant, resulting in stolen credit card information, account takeovers, and potential identity theft. Through realistic simulations, employees can learn to identify the subtle differences between legitimate and fraudulent websites.
| Type | Method | Example | Potential Impact |
|---|---|---|---|
| Email Phishing | Spoofed email address, malicious link, malware attachment | Email from “IT Department” requesting password reset via link to fake login page. | Compromised accounts, data breaches, financial loss. |
| SMS Phishing (Smishing) | Urgent text message with malicious link | Text message claiming bank account compromise, prompting users to click a link to a fake banking website. | Financial loss, identity theft, reputational damage. |
| Website Phishing | Replica website mimicking a legitimate site | Fake login page for a popular online retailer, designed to steal user credentials. | Stolen credit card information, account takeovers, identity theft. |
Methods and Techniques Used in Simulated Phishing

Crafting realistic simulated phishing emails requires a keen understanding of how real phishing attacks operate. Success hinges on mimicking legitimate communications to trick unsuspecting recipients into revealing sensitive information. This involves careful consideration of various elements, from the sender’s address and subject line to the email’s body text and any included links. The goal is to create a convincing illusion of authenticity, thereby increasing the likelihood of a successful “phish.”
Simulated phishing leverages a combination of technical and psychological techniques to achieve its aims. Technically, this includes employing sophisticated email spoofing techniques to mask the true sender’s identity and creating convincing landing pages that mirror legitimate websites. Psychologically, the attacks rely heavily on social engineering principles to manipulate the recipient’s emotions and behaviors, exploiting their trust and desire to comply with perceived authority.
Realistic Email Creation Techniques
Creating realistic simulated phishing emails involves meticulous attention to detail. Subject lines are crucial; they often use urgency (“Urgent Security Alert!”), fear (“Your Account Has Been Compromised”), or curiosity (“You Have a New Message”) to entice recipients to open the email. The body text should be grammatically correct and stylistically consistent with the organization being impersonated. It’s common to include personalized details, such as the recipient’s name or account number, gleaned from publicly available information or previous data breaches.
Links within the email are often disguised, appearing to lead to legitimate websites but actually redirecting to malicious pages designed to capture login credentials or other sensitive information. The overall tone and style should aim for plausibility; poorly written or overly aggressive emails are more likely to be detected as fraudulent.
Social Engineering Tactics in Simulated Phishing
Social engineering forms the core of successful simulated phishing attacks. These tactics exploit human psychology to manipulate individuals into divulging information or taking actions they wouldn’t normally take. Common techniques include:
- Authority: The email might claim to be from a trusted source, such as a bank, government agency, or well-known company, creating a sense of urgency and obligation to comply.
- Scarcity: The email may create a sense of urgency by implying a limited-time offer or a threat of account suspension, prompting immediate action without critical thinking.
- Urgency: Similar to scarcity, urgency tactics leverage time pressure to bypass rational decision-making, leading to impulsive actions.
- Intimidation: Threatening legal action or account closure can pressure recipients into revealing information quickly.
- Curiosity: Intriguing subject lines or vague, yet attention-grabbing messages can pique curiosity, leading to the opening of potentially malicious emails.
Example Simulated Phishing Email
Subject: Urgent Security Alert: Your PayPal Account Requires Immediate AttentionBody: Dear [Recipient Name],We have detected unusual activity on your PayPal account. To prevent unauthorized access, please verify your account details immediately by clicking the link below:[Malicious Link disguised as a legitimate PayPal URL]Failure to verify your account within 24 hours may result in the suspension of your account.Sincerely,The PayPal Security TeamThis email employs urgency and intimidation to pressure the recipient into clicking the malicious link.
The personalized greeting adds to its believability. The link, however, would lead to a fake PayPal login page designed to capture the user’s credentials. The effectiveness of this email stems from its plausible subject line, personalized greeting, and the creation of a sense of urgency and fear.
Best Practices for Designing Effective Simulated Phishing Campaigns, What is simulated phishing
Designing effective simulated phishing campaigns requires a strategic approach. Here are some best practices:
- Target specific user groups: Tailor the phishing emails to resonate with the specific knowledge and expectations of the targeted group.
- Use A/B testing: Experiment with different subject lines, body text, and calls to action to optimize campaign effectiveness.
- Track key metrics: Monitor click-through rates, login attempts, and successful compromises to assess campaign success and identify areas for improvement.
- Maintain legal and ethical compliance: Ensure all simulated phishing activities are conducted within legal and ethical boundaries, obtaining necessary permissions and adhering to relevant regulations.
- Use realistic and up-to-date templates: Employ current branding and design elements to increase the credibility of the simulated phishing emails.
- Combine technical and social engineering techniques: Leverage a multi-layered approach to maximize the effectiveness of the simulated phishing campaign.
Benefits of Simulated Phishing Exercises
Simulated phishing exercises offer a powerful and proactive approach to bolstering an organization’s cybersecurity defenses. By mimicking real-world attacks, these exercises provide invaluable insights into employee vulnerability and offer a controlled environment to test and improve security protocols. The benefits extend far beyond simply identifying susceptible individuals; they contribute to a more robust and resilient security posture across the entire organization.Simulated phishing campaigns are instrumental in improving employee awareness and significantly enhancing an organization’s overall security posture.
Through realistic simulations, employees learn to identify and report suspicious emails, links, and attachments, thereby reducing the likelihood of successful phishing attacks. This heightened awareness translates directly into fewer compromised accounts and a decreased risk of data breaches. The training effect is invaluable, transforming employees from potential vulnerabilities into active participants in the organization’s security efforts.
Improved Employee Awareness
Regular simulated phishing campaigns effectively train employees to recognize and respond appropriately to phishing attempts. The interactive nature of these exercises allows for immediate feedback and reinforcement of best practices. For example, an employee who clicks on a malicious link in a simulated phishing email will receive immediate training on why that action was unsafe and what steps to take in the future.
This immediate, personalized feedback is far more effective than a passive security awareness training session. This iterative process of training and feedback consistently strengthens employee awareness and improves their ability to identify and avoid future threats.
Enhanced Security Measures Based on Campaign Results
The data collected from simulated phishing campaigns provides critical insights into vulnerabilities within an organization’s security infrastructure. Analyzing the results reveals which employees are most susceptible, which types of phishing techniques are most effective, and which departments require additional training. For example, if a significant portion of employees fall victim to a specific type of phishing email (e.g., those impersonating a trusted vendor), the organization can then implement targeted training or improve security controls to address this specific weakness.
This data-driven approach allows for a more effective allocation of resources and ensures that security measures are tailored to the specific needs of the organization. This might involve enhancing email filtering systems, implementing multi-factor authentication, or updating employee training materials.
Return on Investment (ROI) of a Simulated Phishing Program
The cost of a data breach can be astronomical, encompassing legal fees, regulatory fines, reputational damage, and the cost of recovering lost data. A simulated phishing program, while involving an upfront investment, offers significant cost savings by preventing these catastrophic events. Consider a hypothetical scenario: A company with 500 employees invests $5,000 annually in a simulated phishing program.
If this program prevents even one successful phishing attack that could have cost $1 million in remediation and lost productivity, the ROI is clearly substantial. The potential cost savings from prevented data breaches and compromised systems far outweigh the relatively modest investment in a comprehensive simulated phishing program. Furthermore, the intangible benefits – improved employee morale and confidence in the organization’s security posture – also contribute to a strong ROI.
Many organizations report significant reductions in successful phishing attacks following the implementation of regular simulated phishing exercises, demonstrating a clear positive correlation between proactive training and enhanced security.
Ethical Considerations and Legal Compliance

Simulated phishing exercises, while crucial for security awareness training, tread a fine line ethically and legally. Improperly conducted campaigns can damage employee morale, violate privacy laws, and even lead to legal repercussions. Understanding and adhering to ethical guidelines is paramount for the success and acceptance of any simulated phishing program.Ethical considerations in simulated phishing primarily revolve around transparency, consent, and the minimization of harm.
Legal implications often stem from violations of privacy laws, such as GDPR or CCPA, and potential defamation claims if the campaign is poorly designed or executed. Navigating these aspects requires careful planning and adherence to established best practices.
Employee Consent and Transparency
Gaining informed consent is crucial. Employees must understand the nature of the exercise, its purpose, and what data will be collected. This necessitates clear communication before the campaign begins. Transparency extends to post-campaign debriefing, explaining the results, addressing any anxieties, and reiterating the importance of security awareness. A simple email informing employees of the upcoming simulation, explaining its goals, and reassuring them that no repercussions will follow for falling victim, is a good starting point.
The communication should explicitly state that the email is a test and provide contact information for questions or concerns.
Data Privacy and Legal Compliance
Simulated phishing campaigns often involve collecting employee data, such as email addresses and potentially even responses to phishing attempts. This data must be handled in accordance with relevant data privacy regulations, such as GDPR in Europe or CCPA in California. This includes obtaining explicit consent for data processing, ensuring data minimization (collecting only necessary data), and implementing appropriate security measures to protect the collected information.
Failing to comply with these regulations can result in hefty fines and legal action. For example, a company failing to anonymize employee data collected during a simulated phishing campaign and subsequently leaking that data would face severe legal consequences under GDPR.
Minimizing Harm and Maintaining Employee Morale
While the goal is to test vulnerability, it’s vital to minimize any negative impact on employee morale. The simulation should be realistic but not overly aggressive or frightening. Avoid using alarming subject lines or content that could cause undue stress or anxiety. Following the simulation, provide positive reinforcement and emphasize the learning opportunity. A well-structured debriefing session can help alleviate any concerns and transform the experience into a valuable learning opportunity.
A poorly designed campaign, for instance, one that uses highly realistic and upsetting scenarios, could lead to decreased trust in the organization and even legal action if employees feel emotionally harmed.
Best Practices for Ethical and Legal Compliance
To ensure ethical and legal compliance, organizations should develop a comprehensive policy outlining the scope, methodology, and legal considerations of their simulated phishing programs. This policy should include clear guidelines on obtaining consent, data privacy, and communication protocols. Regular review and updates of this policy are essential to reflect changes in regulations and best practices. Consider engaging with legal counsel to ensure compliance with all relevant laws and regulations.
Moreover, maintaining detailed records of the simulated phishing exercises, including consent forms, data processing procedures, and debriefing materials, is crucial for demonstrating compliance. This documentation can be invaluable in case of any legal challenges.
Analyzing Results and Reporting
Analyzing the results of a simulated phishing campaign is crucial for understanding its effectiveness and identifying areas for improvement in your organization’s security awareness training. A thorough analysis allows you to pinpoint vulnerabilities and refine your approach to better protect against real-world phishing attacks. This process involves collecting data, interpreting the results, and presenting your findings in a clear, concise report.
The analysis process begins immediately after the simulated phishing campaign concludes. This involves gathering data from various sources, including the phishing simulation platform itself, which will typically provide detailed statistics on click rates, email opens, and successful credential compromises (if applicable). It also involves reviewing any logs or security information and event management (SIEM) data that may have captured related activity.
This comprehensive data collection is essential for a complete understanding of the campaign’s impact.
Data Analysis Methods
Several methods can be employed to analyze the collected data. Descriptive statistics, such as calculating the percentage of employees who clicked on the phishing link or entered credentials, provide a high-level overview of the campaign’s success. More advanced statistical techniques, such as regression analysis, can be used to identify factors that correlate with higher click-through rates, such as specific departments or job roles.
This allows for a more nuanced understanding of vulnerabilities within the organization.
Report Creation and Structure
The final step is compiling a comprehensive report that summarizes the findings. This report should be clear, concise, and easily digestible for both technical and non-technical audiences. A well-structured report will typically include an executive summary, a detailed analysis of the results, and actionable recommendations. The use of visuals, such as charts and graphs, can significantly enhance the report’s clarity and impact.
Key Performance Indicators (KPIs) and Actionable Insights
A key component of the report is the presentation of key performance indicators (KPIs) and actionable insights. KPIs should quantify the success or failure of the campaign, providing a clear measure of the organization’s vulnerability to phishing attacks. Actionable insights should offer concrete steps to mitigate identified vulnerabilities. These insights should be specific, measurable, achievable, relevant, and time-bound (SMART).
| KPI | Result | Insight | Actionable Recommendation |
|---|---|---|---|
| Phishing Email Open Rate | 65% | High open rate indicates effective subject lines and sender impersonation. | Review email security policies and employee training on recognizing suspicious emails. |
| Phishing Link Click-Through Rate | 20% | Significant portion of employees clicked, highlighting vulnerability to social engineering. | Implement additional security awareness training focusing on identifying malicious links. |
| Credential Compromise Rate | 5% | A concerning number of employees entered credentials, exposing sensitive data. | Strengthen password policies and implement multi-factor authentication. |
| Departmental Click-Through Rates | Marketing: 30%; Sales: 15%; IT: 5% | Marketing department shows significantly higher vulnerability. | Provide targeted training to the Marketing department focusing on their specific vulnerabilities. |
Visual Examples of Simulated Phishing Attempts
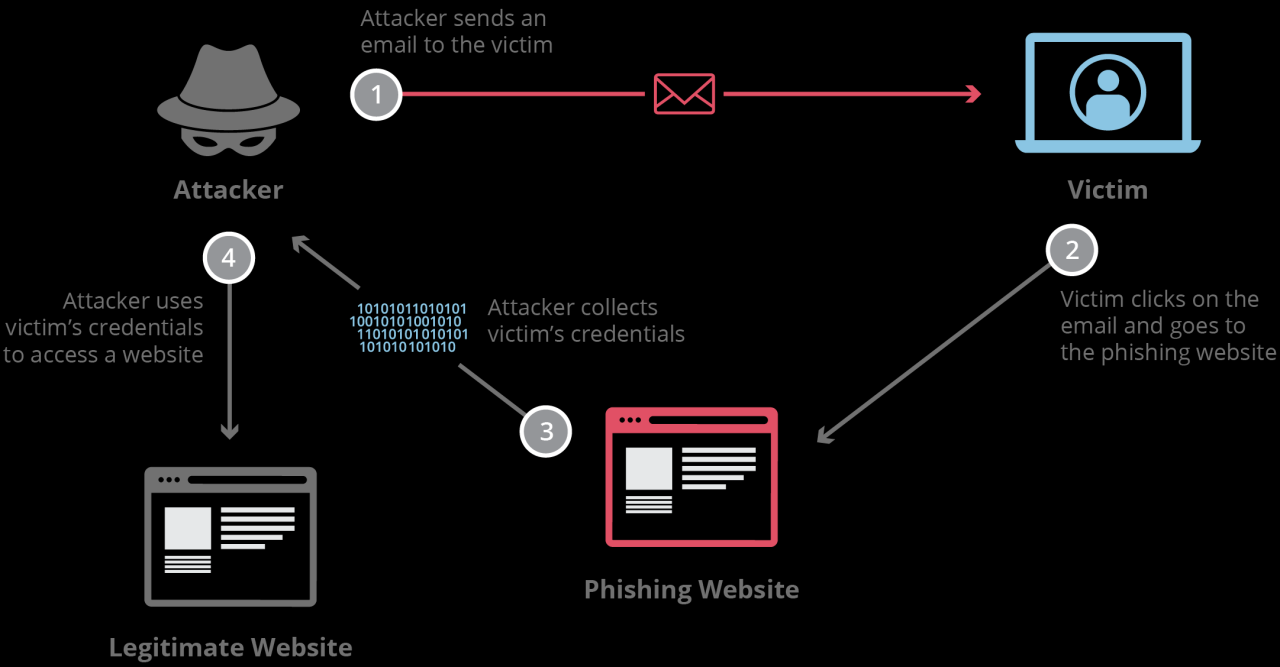
Understanding the visual aspects of simulated phishing attacks is crucial for effective training and awareness. Seeing realistic examples helps users identify potential threats and avoid falling victim to real phishing attempts. The following examples illustrate common tactics used in simulated phishing emails, SMS messages, and websites.
Simulated Phishing Email Example
This simulated phishing email aims to steal banking credentials. The subject line reads: “Urgent Security Alert: Suspicious Activity on Your Account.” The sender address appears to be from a legitimate bank (“[email protected],” though subtly different from the real address). The email body uses fear and urgency, stating: “We have detected unusual activity on your YourBank account. To prevent account suspension, please verify your details immediately by clicking here: [link to fake login page].” The link leads to a convincing replica of the bank’s website, complete with logos and design elements.
Simulated phishing, in a nutshell, is a safe way to train employees to spot malicious emails. Understanding the security implications is crucial, and that’s where learning about efficient app development comes in. Check out this article on domino app dev the low code and pro code future to see how streamlined development can help build better security training apps.
Ultimately, effective simulated phishing relies on well-designed, easily-updated training materials.
The email might even include the recipient’s name, adding a personalized touch to increase credibility. The persuasive language focuses on immediate action and the threat of account suspension. No attachments are included; the entire attack relies on the deceptive link.
Simulated Phishing SMS Message Example
This simulated SMS phishing attack targets a user’s online shopping account. The message reads: “Your Amazon order #12345 has been delayed. To update shipping, click here: [shortened URL].” The urgency is conveyed through the message’s brevity and the implication of a delayed package. The shortened URL masks the true destination, likely a fraudulent website designed to steal login credentials or credit card information.
Deception is achieved through the use of a familiar brand name (Amazon) and the implication of a legitimate transaction.
Simulated Phishing Website Example
This simulated phishing website mimics a popular social media platform’s login page. The layout closely resembles the legitimate site, featuring the same logo, color scheme, and general structure. However, subtle differences exist: the URL might be slightly misspelled or use a different top-level domain (.net instead of .com). The website uses HTTPS to appear secure, but the certificate might be invalid or from an untrusted source.
Deceptive elements include a slightly off font, poorly aligned elements, and a login form that sends data to a malicious server instead of the legitimate social media platform. The website might also include a fake security warning or progress bar to add to its apparent legitimacy. The overall goal is to trick users into entering their login credentials, which are then captured and used for malicious purposes.
Epilogue: What Is Simulated Phishing
Understanding what is simulated phishing is crucial for bolstering your organization’s cybersecurity posture. By regularly conducting simulated phishing exercises and analyzing the results, you can proactively identify and mitigate vulnerabilities before they’re exploited by malicious actors. Remember, a well-executed simulated phishing campaign isn’t just about identifying weaknesses; it’s about empowering your employees to become the first line of defense against real-world threats.
The investment in simulated phishing translates directly to a stronger, more resilient security system.
Top FAQs
What happens if an employee fails a simulated phishing test?
Failing a simulated phishing test usually triggers additional training or awareness sessions tailored to address the specific weakness demonstrated. It’s a learning opportunity, not a punitive measure.
How often should simulated phishing exercises be conducted?
Frequency depends on your organization’s risk tolerance and industry. Quarterly or bi-annual exercises are common, but some high-risk industries may conduct them more frequently.
Are there legal implications if I don’t inform employees about simulated phishing?
Transparency is key. While the specifics vary by jurisdiction, it’s generally advisable to inform employees about the possibility of simulated phishing campaigns to avoid legal and ethical issues. Clear communication and consent are important.
What if my simulated phishing campaign causes significant disruption?
A well-designed campaign minimizes disruption. Pre-campaign communication and clear post-campaign debriefs help manage any anxiety or confusion. Focus on the learning experience and the positive impact on overall security.