What is the difference between an MSP and an MSSP for cybersecurity?
What is the difference between an msp and a mssp for cybersecurity – What is the difference between an MSP and an MSSP for cybersecurity? This is a question many businesses grapple with, especially as they navigate the increasingly complex landscape of digital threats. Understanding the nuances between a Managed Service Provider (MSP) and a Managed Security Service Provider (MSSP) is crucial for making informed decisions about protecting your valuable data and infrastructure.
This post will break down the key differences, helping you determine which type of provider best suits your organization’s needs and budget.
Essentially, an MSP handles your overall IT infrastructure, acting as your outsourced IT department. They manage things like servers, networks, and help desks. An MSSP, however, specializes in cybersecurity. They build upon the foundation laid by an MSP, focusing on proactive threat detection, incident response, and security compliance. Think of it like this: an MSP is the general contractor for your IT, while an MSSP is the specialized security expert ensuring your building is protected from intruders.
Defining MSP and MSSP

Choosing the right IT support partner is crucial for any business, regardless of size. But with terms like MSP and MSSP floating around, it can be confusing to understand the differences and which one best suits your needs. Let’s clarify these often-interchangeable terms and explore their distinct service offerings.
Managed Service Provider (MSP) Core Functions
MSPs provide comprehensive IT management services to businesses. Their core function is to handle the day-to-day operations of a client’s IT infrastructure, freeing up internal IT staff to focus on strategic initiatives or eliminating the need for an in-house IT department altogether. This includes tasks such as network management, server maintenance, help desk support, and software updates. Essentially, MSPs act as an outsourced IT department, providing a range of services tailored to a client’s specific requirements and budget.
They often employ a proactive approach, monitoring systems for potential problems and addressing them before they impact business operations.
Managed Security Service Provider (MSSP) Cybersecurity Focus, What is the difference between an msp and a mssp for cybersecurity
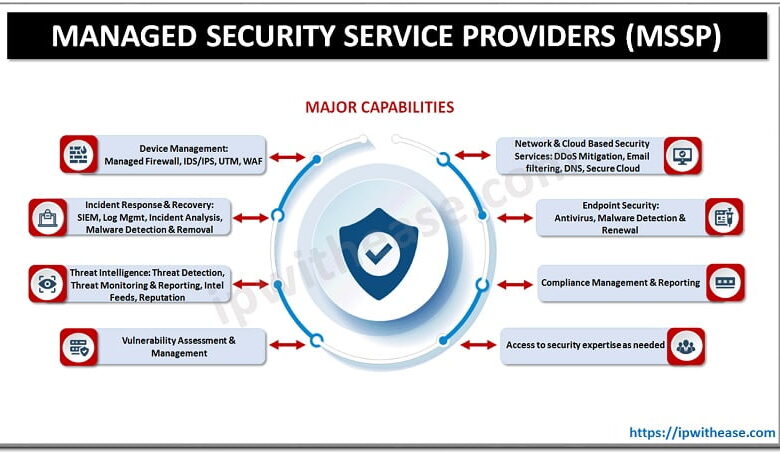
MSSPs are a specialized subset of MSPs. While MSPs handle the broader IT landscape, MSSPs concentrate solely on cybersecurity. Their expertise lies in protecting clients from cyber threats, including malware, phishing attacks, ransomware, and data breaches. This involves implementing and managing security solutions like firewalls, intrusion detection systems, antivirus software, and security information and event management (SIEM) systems.
MSSPs also provide security awareness training, vulnerability assessments, incident response planning, and penetration testing to identify and mitigate security risks. Their focus is on proactive threat prevention and reactive incident response.
Comparing MSP and MSSP Service Offerings
While there’s overlap, the core difference lies in the scope of services. An MSP offers a broader range of IT services, encompassing network management, server maintenance, help desk support, and more. An MSSP, on the other hand, focuses exclusively on cybersecurity aspects, offering services like threat detection, incident response, vulnerability management, and security awareness training. A business might utilize both; an MSP for general IT management and an MSSP for specialized cybersecurity needs.
Consider a small business needing help with their network and email – an MSP would be sufficient. However, a larger organization with sensitive data and stringent compliance requirements would likely benefit from both an MSP and an MSSP.
Pricing Models for MSPs and MSSPs
Pricing models for both MSPs and MSSPs vary considerably depending on the service level agreements (SLAs), the size and complexity of the client’s infrastructure, and the specific services included.
| Pricing Model | MSP | MSSP |
|---|---|---|
| Per-device/user | Common; often includes basic support and monitoring. | Less common; usually focuses on specific security features per user/device. |
| Project-based | Used for specific projects like network upgrades or software implementations. | Used for penetration testing, vulnerability assessments, or incident response. |
| Tiered service levels | Offers various levels of support and response times, with pricing reflecting the level of service. | Offers varying levels of security monitoring and response capabilities, with pricing scaling accordingly. |
| Retainer-based | A fixed monthly fee for a defined set of services. | A common model; provides predictable monthly costs for ongoing security monitoring and management. |
Service Scope and Responsibilities
MSPs and MSSPs, while both focused on improving IT operations, have distinct service scopes. Understanding these differences is crucial for businesses choosing the right partner to manage their technology and security. An MSP handles the foundational IT infrastructure, while an MSSP layers on specialized cybersecurity expertise and proactive threat management.MSPs and MSSPs have clearly defined, yet often overlapping, responsibilities.
A key distinction lies in the proactive versus reactive nature of their services. MSPs primarily focus on keeping the lights on, while MSSPs focus on preventing the lights from ever going out in the first place, due to a security breach.
MSP Responsibilities in IT Infrastructure Management
MSPs typically manage the day-to-day operations of a company’s IT infrastructure. This includes tasks like network maintenance, server management, help desk support, and software updates. They ensure the smooth running of essential IT systems, enabling employees to perform their work effectively. Think of them as the general contractors of your IT world, keeping everything running smoothly. Their responsibilities often encompass:
- Network monitoring and maintenance
- Server administration and management
- Help desk and end-user support
- Software deployment and updates
- Hardware procurement and maintenance
- Data backup and recovery
MSSP Cybersecurity Services
MSSPs specialize in providing advanced cybersecurity services designed to protect against sophisticated threats. Their services extend far beyond the basic security features offered by an MSP. They actively monitor for threats, respond to incidents, and help organizations build a robust security posture. MSSPs are like specialized security guards, constantly patrolling for threats and responding quickly to any intrusions.
Key services include:
- Security Information and Event Management (SIEM): Real-time monitoring of security logs to detect and respond to threats.
- Intrusion Detection and Prevention Systems (IDPS): Identifying and blocking malicious traffic entering the network.
- Vulnerability Management: Regular scanning and patching of systems to identify and fix security weaknesses.
- Security Awareness Training: Educating employees about phishing, malware, and other social engineering attacks.
- Incident Response: Developing and executing plans to handle security breaches and minimize damage.
- Threat Intelligence: Collecting and analyzing threat data to proactively identify and mitigate risks.
MSSP Expansion of MSP Security Capabilities
An MSSP significantly enhances the security capabilities of a standard MSP. While an MSP might offer basic firewall management and antivirus software, an MSSP provides a multi-layered security approach. For example, an MSP might detect a suspicious login attempt, but an MSSP would analyze that attempt within the context of broader threat intelligence, potentially identifying it as part of a larger, coordinated attack.
The MSSP would then proactively take steps to mitigate the threat, preventing a potential breach. This proactive approach is a key differentiator.
Comparison of Security Threats Addressed
The following table highlights the types of security threats typically addressed by MSPs and MSSPs:
| Threat Type | MSP Focus | MSSP Focus | Example |
|---|---|---|---|
| Hardware Failure | High | Low | Server crash due to hardware malfunction |
| Software Vulnerabilities | Moderate | High | Unpatched software exploited by malware |
| Phishing Attacks | Low | High | Employee clicks on a malicious link in an email |
| Advanced Persistent Threats (APTs) | Low | Very High | Sophisticated, long-term attack targeting sensitive data |
Client Relationship and Management
The relationship between a client and their IT service provider is paramount, but the nature of that relationship differs significantly between a Managed Service Provider (MSP) and a Managed Security Service Provider (MSSP). While both aim for client satisfaction, their approaches, expertise levels, and incident responses are shaped by their specialized focus. MSPs prioritize overall IT functionality, while MSSPs concentrate on the security aspects.
This distinction profoundly impacts how they interact with and support their clients.MSPs and MSSPs employ different client relationship management (CRM) approaches. MSPs often foster a more general IT partnership, focusing on proactive maintenance and problem resolution across various IT systems. MSSPs, conversely, build a relationship centered around security posture, risk mitigation, and incident response capabilities. This difference in focus leads to variations in communication frequency, the type of information shared, and the overall tone of the client interaction.
Security Expertise Levels Offered
MSPs typically offer a broader range of IT services, including network management, help desk support, and cloud services. Their security expertise is usually integrated within these broader services, often providing basic security configurations and monitoring. MSSPs, however, specialize in cybersecurity, offering a deeper level of expertise in areas such as threat detection, incident response, vulnerability management, security awareness training, and compliance.
This specialized knowledge allows MSSPs to provide more sophisticated security solutions and strategic guidance than a typical MSP. For example, an MSP might offer basic firewall management, while an MSSP would provide advanced threat intelligence, intrusion detection, and security information and event management (SIEM) services.
Security Incident Handling
Consider a hypothetical phishing attack. An MSP might primarily focus on restoring access to compromised accounts and ensuring system functionality is restored. Their response might involve resetting passwords, quarantining infected systems, and providing basic user training. An MSSP, on the other hand, would undertake a more comprehensive investigation. They would analyze the attack vector, identify the extent of the breach, implement containment measures, and conduct a post-incident review to prevent future occurrences.
This might involve forensic analysis, malware removal, and security hardening measures, going beyond simple account restoration. The MSSP would also likely engage in proactive threat hunting and vulnerability assessments to strengthen the client’s overall security posture following the incident.
Reporting and Communication Strategies
MSPs generally provide regular reports focusing on system uptime, performance metrics, and ticket resolution times. Communication is often reactive, addressing specific issues as they arise. MSSPs, in contrast, provide more comprehensive security reports, detailing threat landscape analysis, vulnerability assessments, incident summaries, and security posture evaluations. Their communication is often proactive, providing regular security updates, threat alerts, and recommendations for improving security posture.
For instance, an MSP might send a monthly report on server uptime, while an MSSP might provide a weekly security bulletin highlighting emerging threats and vulnerabilities relevant to the client’s environment, along with recommendations for mitigation. The frequency and detail of these reports reflect the specialized nature of the MSSP’s services.
Technology and Infrastructure
MSPs and MSSPs differ significantly in their technological focus and the infrastructure they manage. While both deal with IT, the MSSP’s responsibilities extend far beyond the typical operational management handled by an MSP. Understanding these differences is crucial for businesses choosing the right partner for their specific needs.MSPs primarily focus on the day-to-day operational management of a client’s IT infrastructure.
This involves maintaining the stability and functionality of systems, ensuring uptime, and providing help desk support. MSSPs, on the other hand, build upon this foundation by incorporating proactive security measures and threat detection capabilities.
Technology Managed by MSPs
MSPs typically manage a wide range of technologies, including servers (physical and virtual), networks (routers, switches, firewalls – basic functionality), desktops, laptops, mobile devices, and cloud-based applications. Their expertise often encompasses operating systems, databases, and various productivity software. They ensure these systems are functioning correctly, performing routine maintenance, and providing support to end-users. They might also manage email servers, print servers, and other essential components of a business’s IT environment.
Think of them as the general contractors of IT, ensuring everything runs smoothly.
Specialized Security Technologies Utilized by MSSPs
MSSPs leverage a sophisticated suite of security technologies that go beyond the basic functionality of an MSP’s offerings. These include:
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources across the network, identifying potential threats and security incidents in real-time. A SIEM system, for example, might detect unusual login attempts from an unfamiliar geographic location, triggering an alert for investigation.
- Security Orchestration, Automation, and Response (SOAR): SOAR platforms automate many security tasks, such as incident response and threat hunting. This allows MSSPs to react to threats more quickly and efficiently. For instance, a SOAR system might automatically quarantine a compromised device upon detection of malware.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection and response capabilities at the endpoint level (individual computers and devices). EDR can detect and respond to malware that might evade traditional antivirus software. A real-world example would be an EDR system identifying and blocking a zero-day exploit before it can cause damage.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity, alerting administrators to potential threats or automatically blocking them. An IDS might detect a denial-of-service attack, while an IPS would actively block the malicious traffic.
Infrastructure Requirements
The infrastructure requirements for MSPs and MSSPs differ considerably. MSPs need robust infrastructure to support their operational tasks, but it doesn’t require the same level of security specialization as an MSSP. MSSPs, however, require a highly secure and resilient infrastructure to handle sensitive security data and respond effectively to incidents. This often includes dedicated security operations centers (SOCs) with redundant systems and advanced monitoring capabilities.
Think of the difference between a well-equipped workshop for general repairs (MSP) and a high-tech forensic lab (MSSP).
Common Security Tools Used by MSSPs
MSSPs utilize a wide array of security tools to protect their clients. The selection depends on the specific needs and the threat landscape. Here are some common examples:
- Antivirus and Anti-malware Software: Provides basic protection against known threats.
- Vulnerability Scanners: Identify security weaknesses in systems and applications.
- Penetration Testing Tools: Simulate real-world attacks to identify vulnerabilities.
- Data Loss Prevention (DLP) Tools: Prevent sensitive data from leaving the network unauthorized.
- Firewall Management Systems: Manage and monitor network firewalls.
- Cloud Security Posture Management (CSPM): Assesses and manages the security of cloud environments.
Cost and Value Proposition
Choosing between an MSP and an MSSP often comes down to budget and the desired level of cybersecurity protection. While both offer valuable IT services, their pricing models and the value they deliver differ significantly. Understanding these differences is crucial for making an informed decision.The overall cost of engaging an MSP is generally lower than that of an MSSP.
MSPs typically charge based on a tiered service model, with pricing determined by the number of devices managed, the types of services required, and the level of support. This can range from a few hundred dollars per month for basic support to several thousand for more comprehensive services. MSSPs, on the other hand, usually operate on a more complex pricing structure, often incorporating hourly rates for specific security services, monthly retainer fees for ongoing monitoring and management, and potentially incident response charges.
The total cost can easily exceed that of an MSP, especially for organizations with complex IT infrastructures or heightened security needs.
MSP and MSSP Pricing Structures
Several factors influence the pricing structure for both MSPs and MSSPs. For MSPs, the number of users, devices, and applications needing support is a primary driver. The complexity of the IT environment, the level of proactive maintenance required, and the speed of response needed for incidents also significantly impact the cost. For MSSPs, the level of threat detection and response sophistication, the scope of security monitoring (e.g., 24/7 vs.
business hours), and the specific security services included (e.g., penetration testing, vulnerability assessments, security awareness training) are key factors affecting the pricing. Contract length and service level agreements (SLAs) also play a significant role in determining the final cost for both service types. For example, a small business might pay an MSP $500-$1000 per month for basic IT support, whereas a larger enterprise could pay an MSSP $10,000-$50,000 or more per month for comprehensive cybersecurity services.
Return on Investment (ROI) Analysis
The ROI for both MSPs and MSSPs is not always immediately apparent, but it’s crucial to consider the long-term benefits. For MSPs, the ROI comes from increased efficiency, reduced downtime, and improved employee productivity. By outsourcing routine IT tasks, businesses can free up internal IT staff to focus on strategic initiatives. The cost savings from avoiding costly hardware failures and software glitches can also contribute significantly to the overall ROI.
For MSSPs, the ROI is primarily driven by the prevention of costly security breaches. The cost of a data breach can be astronomical, including legal fees, regulatory fines, and reputational damage. An MSSP helps mitigate this risk by proactively identifying and responding to threats, minimizing the potential financial and operational impact of a security incident. For example, a company that avoids a $1 million data breach due to the proactive monitoring of an MSSP will easily see a positive ROI, even considering the significant MSSP costs.
Comparative Value Proposition
Imagine two scenarios: Company A uses an MSP for basic IT support, while Company B uses an MSSP. Company A experiences a ransomware attack, resulting in lost productivity, data recovery costs, and reputational damage, totaling $50,000. Company B, with its proactive security monitoring and incident response capabilities provided by the MSSP, successfully mitigates the attack before significant damage occurs, incurring only the cost of the MSSP services, say $5,000 per month.
While Company B has a higher monthly expense, their overall cost is significantly lower than Company A’s in the event of a security incident. This illustrative example clearly demonstrates that, although the initial cost of an MSSP is higher, the potential cost savings from avoiding a major security incident can significantly outweigh the investment. The value proposition for an MSP is primarily focused on operational efficiency and cost savings from reduced downtime, whereas the value proposition for an MSSP centers on minimizing the risk and financial impact of cybersecurity incidents.
Choosing the Right Provider: What Is The Difference Between An Msp And A Mssp For Cybersecurity
Selecting the right cybersecurity provider—whether an MSP (Managed Service Provider) or an MSSP (Managed Security Service Provider)—is crucial for safeguarding your business. The decision hinges on a careful assessment of your specific needs, budget, and risk tolerance. Understanding the nuances between MSP and MSSP services, as discussed previously, is the first step towards making an informed choice.The process of choosing a provider requires a methodical approach, focusing on several key factors that will ultimately determine the success of your cybersecurity strategy.
Ignoring these factors can lead to inadequate protection, increased vulnerabilities, and potentially significant financial losses.
Key Factors for Provider Selection
When deciding between an MSP and an MSSP, the most important factor is your organization’s current security posture and future needs. A small business with limited IT resources might find a comprehensive MSP offering sufficient security services, while a large enterprise with complex systems and sensitive data will likely require a dedicated MSSP to manage sophisticated threat detection and response.
Consider the scale and complexity of your IT infrastructure, the sensitivity of your data, and your existing security expertise. For instance, a company handling financial transactions would need a higher level of security than a small retail shop. This assessment will dictate whether an MSP’s basic security features are sufficient or if the proactive threat hunting and incident response capabilities of an MSSP are necessary.
Provider Suitability Checklist
A structured approach to evaluating potential providers is essential. This checklist ensures a thorough examination of their capabilities and alignment with your requirements. Asking the right questions is key to identifying the best fit.
- Service Level Agreements (SLAs): Examine the SLAs closely. What are the guaranteed uptime percentages? What are the response times for security incidents? Are there penalties for non-compliance?
- Security Certifications and Compliance: Verify the provider’s certifications (e.g., ISO 27001, SOC 2) and compliance with relevant regulations (e.g., GDPR, HIPAA). These demonstrate a commitment to security best practices.
- Experience and Expertise: Assess the provider’s experience in your industry and with similar-sized organizations. Review case studies and testimonials to understand their track record.
- Technology and Infrastructure: Inquire about the technology stack used by the provider, ensuring it aligns with your current and future needs. Investigate their security monitoring tools and processes.
- Pricing and Contract Terms: Understand the pricing model (e.g., fixed fee, per-user, per-device) and the terms of the contract, including termination clauses and escalation procedures.
- Communication and Reporting: Determine how the provider will communicate with you, what types of reports will be provided, and how frequently you’ll receive updates on the security status of your systems.
Aligning Provider Capabilities with Business Needs
Simply choosing a provider with the highest certifications isn’t enough. The provider’s capabilities must directly address your specific business needs and vulnerabilities. For example, a company with a high reliance on cloud services needs a provider experienced in cloud security. A financial institution requires a provider deeply versed in regulatory compliance. Careful mapping of your business requirements to the provider’s service offerings is essential for a successful partnership.
This includes considering your current IT infrastructure, future growth plans, and the types of threats you’re most vulnerable to. For example, a company experiencing a rise in phishing attacks would benefit from a provider with strong email security expertise.
Evaluating Security Certifications and Compliance
Security certifications and compliance attestations provide independent verification of a provider’s security posture. Look for certifications like ISO 27001 (information security management systems), SOC 2 (Service Organization Control 2), and relevant industry-specific certifications. These certifications demonstrate a commitment to security best practices and adherence to established standards. Compliance with regulations like GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act) indicates the provider’s ability to handle sensitive data securely and legally.
Thoroughly reviewing these certifications and compliance reports is critical for understanding the provider’s commitment to security and risk management. For example, a SOC 2 Type II report provides a more in-depth assessment of a provider’s security controls over a longer period, providing greater assurance than a Type I report.
Last Point
Choosing between an MSP and an MSSP, or even opting for both, depends entirely on your organization’s specific security posture and risk tolerance. While an MSP provides a solid foundation for IT management, an MSSP offers the specialized expertise needed to proactively combat increasingly sophisticated cyber threats. By carefully considering your needs, budget, and risk profile, you can choose the right partner to protect your business in today’s digital world.
Don’t hesitate to ask questions and thoroughly vet potential providers to ensure a strong and secure partnership.
Expert Answers
What are some common security tools used by MSSPs?
MSSPs often utilize tools like Security Information and Event Management (SIEM) systems, Security Orchestration, Automation, and Response (SOAR) platforms, Endpoint Detection and Response (EDR) solutions, and vulnerability scanners.
Can I use both an MSP and an MSSP simultaneously?
Absolutely! Many businesses find it beneficial to use an MSP for general IT management and an MSSP for specialized security services. This allows for a comprehensive approach to IT and security.
How do I determine the right level of security for my business?
This depends on factors like your industry, the sensitivity of your data, and your risk tolerance. A thorough risk assessment can help determine the appropriate level of security measures.
What certifications should I look for in an MSSP?
Look for certifications like ISO 27001, SOC 2, and relevant industry-specific compliance certifications that demonstrate their commitment to security best practices.





