How MFA Stops Healthcare Phishing
How MFA identity security can help prevent phishing scams targeting healthcare companies is crucial in today’s digital landscape. Phishing attacks are becoming increasingly sophisticated, and healthcare organizations are particularly vulnerable due to sensitive patient data. Implementing multi-factor authentication (MFA) is a critical step in safeguarding this sensitive information and preventing breaches.
This article explores the effectiveness of MFA in mitigating phishing threats against healthcare providers. It examines the various MFA methods, their implementation challenges, and the broader security strategies necessary to combat phishing in the healthcare sector. We’ll also look at real-world examples and future trends to understand how MFA can best protect healthcare companies from these ever-evolving cyberattacks.
Introduction to MFA and Phishing

Protecting sensitive healthcare data is paramount, and a crucial aspect of this protection involves understanding the tactics of cybercriminals. Phishing scams, in particular, pose a significant threat to healthcare organizations. These attacks rely on manipulating individuals into revealing confidential information, often by impersonating legitimate entities. Multi-Factor Authentication (MFA) is a powerful tool that significantly strengthens defenses against these malicious schemes.
Multi-Factor Authentication Explained
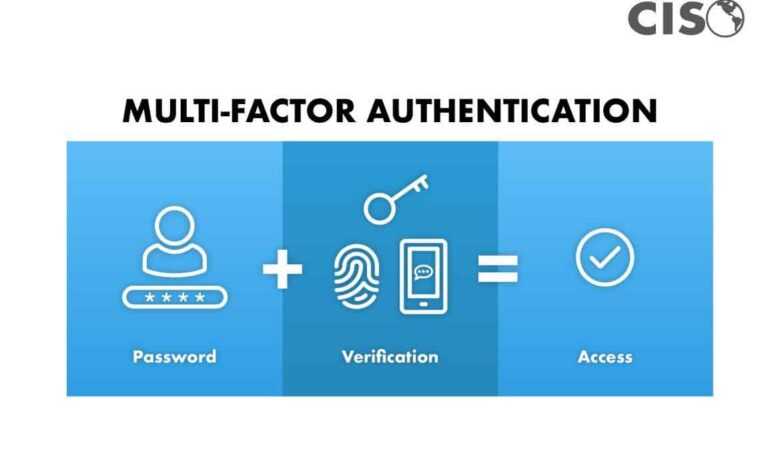
Multi-Factor Authentication (MFA) is a security system that requires more than one form of verification to access an account. This goes beyond a simple username and password combination. Instead, it might include a one-time code sent to a mobile phone, a biometric scan, or a security token. This layered approach dramatically reduces the risk of unauthorized access, as even if a hacker obtains one piece of information, they lack the other factors needed for successful login.
Strong MFA identity security is crucial for healthcare companies battling phishing scams. Protecting sensitive patient data requires robust measures, and multi-factor authentication is a fundamental part of that. However, to truly bolster defenses, we also need to consider the broader context of code security, like the need for “Deploying AI Code Safety Goggles Needed” here.
Ultimately, a layered approach, incorporating both MFA and advanced security measures, is the most effective way to mitigate these threats and safeguard patient information.
Phishing Scams: Tactics and Targets
Phishing scams are social engineering attacks that trick individuals into revealing sensitive information. They often mimic legitimate organizations like banks, government agencies, or, in our case, healthcare providers. These attacks can employ various tactics, including:
- Spoofed Emails: Emails appear to come from trusted sources but contain malicious links or attachments that install malware or lead to fraudulent websites.
- Fake Websites: These websites mimic legitimate login portals, tricking users into entering credentials on a deceptive site.
- Social Engineering: Cybercriminals attempt to manipulate victims through emotional appeals, urgency, or threats, encouraging quick and careless actions.
Healthcare Company Vulnerabilities to Phishing
Healthcare companies are particularly vulnerable to phishing attacks due to the sensitive patient data they handle. This data includes medical records, financial information, and personally identifiable information (PII). A successful phishing attack can lead to significant financial losses, reputational damage, and potentially harm patient well-being. Compromised patient records can expose individuals to identity theft, medical fraud, and other serious consequences.
Comparing Traditional Login Methods with MFA
| Feature | Traditional Login (Username/Password) | Multi-Factor Authentication (MFA) |
|---|---|---|
| Security Level | Low | High |
| Authentication Factors | Single (username/password) | Multiple (e.g., password, code, biometric) |
| Risk of Compromise | High; a single compromised credential can grant access | Low; multiple factors need to be compromised |
| Protection Against Phishing | Limited; phishing can easily steal credentials | Significant; prevents unauthorized access even if credentials are stolen |
Traditional login methods are susceptible to phishing attacks, as hackers need only one set of compromised credentials to gain access. MFA, on the other hand, provides a multi-layered defense, rendering stolen credentials ineffective. This added layer of security significantly strengthens the overall security posture.
MFA Mechanisms for Preventing Phishing
Multi-factor authentication (MFA) stands as a crucial defense mechanism against phishing attacks, particularly in the sensitive realm of healthcare. By demanding multiple forms of verification beyond a simple username and password, MFA significantly raises the bar for attackers attempting to impersonate legitimate users. This heightened security measure makes it considerably more challenging for phishers to gain unauthorized access to patient data and systems.Implementing robust MFA systems is a proactive step towards safeguarding healthcare organizations from the escalating threat of phishing.
By demanding additional authentication factors, organizations can effectively deter malicious actors and mitigate the risks associated with credential-based attacks.
One-Time Passwords (OTPs)
One-time passwords (OTPs) are a prevalent MFA method that generates unique, temporary codes for each login attempt. These codes are often sent via SMS, email, or through dedicated authentication apps. This adds an extra layer of security, as attackers need not only the victim’s credentials but also the access to their communication channels. For example, if a malicious actor obtains a user’s login credentials through a phishing attack, they would still be unable to access the account without possessing the OTP.
Biometric Authentication
Biometric authentication leverages unique physical characteristics, such as fingerprints, facial recognition, or voice recognition, to verify user identity. This method is particularly effective because it’s difficult for attackers to replicate these characteristics. A significant advantage of this approach lies in its inherent difficulty for impersonation. A successful phishing attempt would need to gain access to a user’s biometric data, a considerably higher hurdle compared to merely obtaining login credentials.
Security Keys
Security keys, small physical devices, provide a highly secure form of authentication. These keys generate unique cryptographic tokens, which are required for successful logins. Security keys are exceptionally resistant to phishing attacks as they are physically separate from the compromised account information. They essentially act as a separate, physical verification layer, ensuring that access requires both the knowledge (login credentials) and possession (security key).
Effectiveness Comparison
Different MFA methods exhibit varying degrees of effectiveness against phishing attacks. OTPs, while convenient, can be susceptible to SMS interception. Biometric authentication, due to its inherent complexity, presents a strong defense against phishing. Security keys, being physical and independent, are arguably the most secure method for mitigating phishing attempts.
Real-World Examples
Numerous instances exist where MFA successfully thwarted phishing attempts. A recent case involved a healthcare organization where a phishing email mimicking a legitimate internal communication prompted users to change their passwords. Due to the MFA implementation, these attempts were blocked, preventing attackers from gaining unauthorized access.
Strengths and Weaknesses of MFA Methods
| MFA Method | Strengths | Weaknesses |
|---|---|---|
| One-Time Passwords (OTPs) | Convenient, readily available | Vulnerable to SMS interception, potential for account takeover if OTP is compromised |
| Biometric Authentication | Highly secure, difficult to replicate | Potential for errors or spoofing, requires specialized hardware |
| Security Keys | Extremely secure, resistant to phishing, no reliance on internet connection | Requires physical device, can be cumbersome for some users |
Implementing MFA in Healthcare Environments
Implementing multi-factor authentication (MFA) in healthcare settings is crucial for bolstering security and safeguarding sensitive patient data. The healthcare industry is a prime target for phishing attacks, and robust MFA can significantly reduce the risk of breaches caused by compromised credentials. This section delves into the practical aspects of implementing MFA within diverse healthcare environments.Effective MFA implementation requires careful planning and execution to minimize disruptions to existing workflows.
Multi-factor authentication (MFA) is crucial for stopping phishing scams that target healthcare companies. Stronger security measures, like MFA, are essential to protect sensitive patient data. This is particularly important given recent developments like the Department of Justice Offers Safe Harbor for MA Transactions Department of Justice Offers Safe Harbor for MA Transactions. By implementing MFA, healthcare organizations can significantly reduce the risk of unauthorized access and the damage that phishing scams can cause.
This involves considering the unique needs of different departments and user roles, ensuring a seamless transition, and providing comprehensive user training.
Challenges of Implementing MFA in Diverse Healthcare Settings
Implementing MFA in healthcare presents specific challenges due to the varied nature of the environment. Different departments, such as patient portals, clinician access, and administrative systems, have varying user access requirements and existing technological infrastructures. Integrating MFA into these diverse systems without compromising accessibility is critical. This often requires careful assessment of existing systems and careful selection of an MFA solution that can integrate seamlessly.
Steps for a Smooth MFA Implementation Process
A phased approach is key to a successful MFA rollout. The process should include careful planning, thorough testing, and user communication to mitigate disruptions.
- Assessment of Existing Systems: Evaluate current security posture and identify vulnerable points within the existing infrastructure. Assess user roles and access privileges to tailor MFA requirements accordingly.
- Selection of an Appropriate MFA Solution: Consider factors such as scalability, integration capabilities, security features, and cost. Evaluate solutions that align with the specific needs of different departments and user groups within the healthcare organization.
- Pilot Testing and Refinement: Implement MFA on a small scale to identify potential issues and refine the implementation strategy. This testing phase allows for iterative improvements and ensures a smooth transition to a full-scale deployment.
- Phased Rollout: Deploy MFA in stages, starting with critical systems or departments, to minimize disruption to workflows. This gradual implementation allows for feedback and adjustments before a full-scale deployment.
- User Training and Awareness Programs: Develop comprehensive training materials to educate users about MFA procedures, security best practices, and how to identify phishing attempts. Regular refresher training sessions are essential.
Considerations for Choosing the Right MFA Solution for Healthcare
Selecting the right MFA solution is critical for a successful implementation. A solution must be compatible with existing systems and provide robust security measures.
- Integration Capabilities: The chosen solution should seamlessly integrate with existing systems, such as patient portals and electronic health records (EHRs), to minimize disruption and ensure smooth workflows.
- Security Features: Look for solutions that offer multiple authentication methods, such as one-time passwords (OTPs), biometric authentication, or hardware tokens, to strengthen security.
- Scalability: The solution must be scalable to accommodate future growth and expansion of the healthcare organization, as well as potential increases in user accounts.
- Cost-Effectiveness: Evaluate the total cost of ownership (TCO) of the MFA solution, considering factors such as licensing fees, maintenance costs, and potential support costs.
- Compliance with Healthcare Regulations: Ensure the chosen solution adheres to relevant healthcare regulations, such as HIPAA, to protect patient data.
Integrating MFA into Existing Systems and Workflows
Careful planning is essential to ensure a smooth integration process. A phased rollout, as mentioned before, can help mitigate disruptions.
- Phased Implementation: Implementing MFA in stages, starting with less critical systems, allows for adjustments and testing to ensure smooth operation before expanding to other areas.
- Workflow Adjustments: Revise existing workflows to accommodate the MFA process. Clearly communicate the new procedures to all users to minimize confusion.
- System Compatibility: Ensure compatibility between the chosen MFA solution and existing systems to avoid conflicts and ensure a smooth transition.
User Training and Awareness Programs
User training is crucial for the success of MFA implementation. Training should cover MFA procedures and phishing prevention strategies.
- Comprehensive Training Materials: Create clear and concise training materials that Artikel MFA procedures and best practices. Demonstrate the proper use of MFA methods.
- Interactive Training Sessions: Conduct interactive training sessions that allow users to practice MFA procedures in a controlled environment. This hands-on approach helps reinforce understanding.
- Regular Reminders and Updates: Regularly remind users of MFA procedures and security best practices through email notifications, internal newsletters, and reminders within applications. Address any user concerns or issues promptly.
Implementation Strategies for Different Healthcare Departments
This table Artikels different implementation strategies for various healthcare departments.
| Department | Implementation Strategy |
|---|---|
| Patient Registration | Implement MFA for patient account creation and login. Use OTPs for initial verification. |
| Physician Login | Require MFA for all physician logins, emphasizing two-factor authentication. |
| Administrative Access | Implement MFA for all administrative access to sensitive data. |
| Clinical Systems | Implement MFA for access to patient records and clinical applications. |
Phishing Prevention Strategies Beyond MFA: How Mfa Identity Security Can Help Prevent Phishing Scams Targeting Healthcare Companies
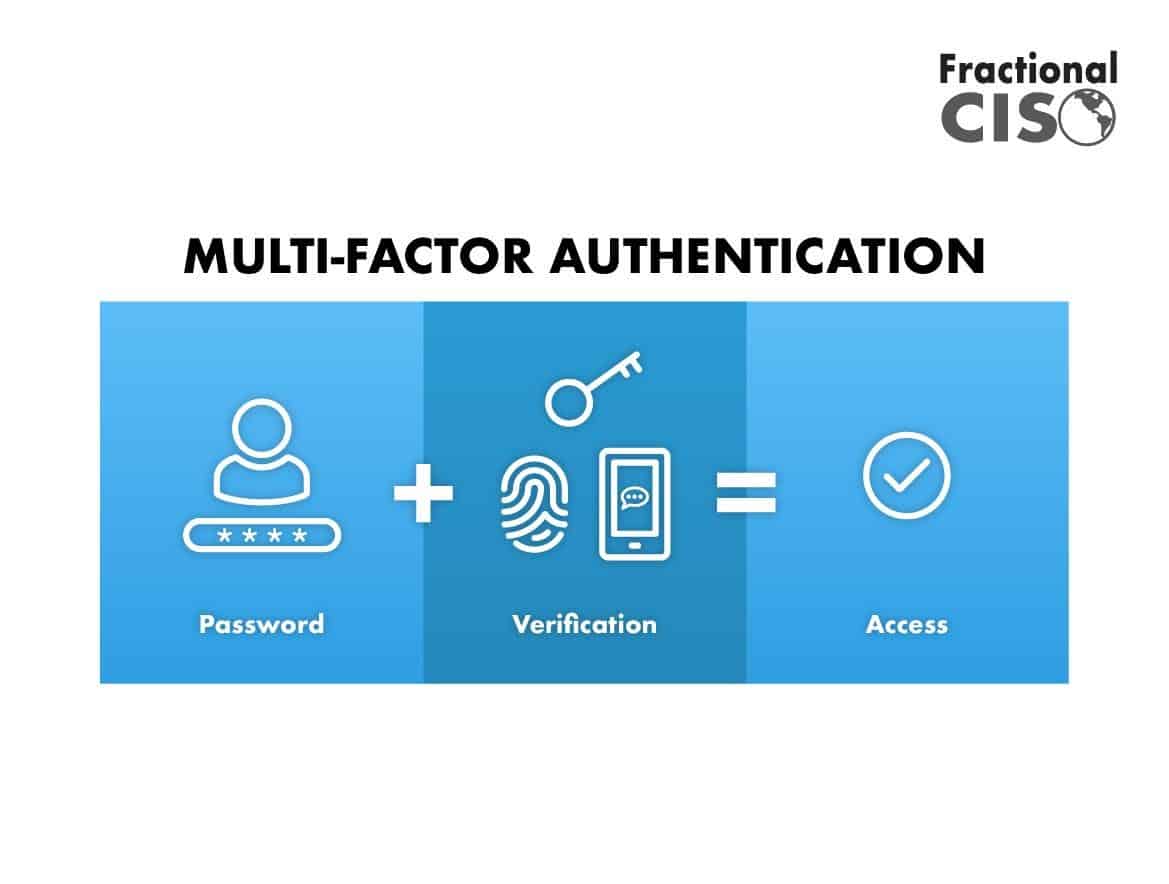
Multi-factor authentication (MFA) is a powerful tool in the fight against phishing, but it’s not a silver bullet. Effective phishing prevention requires a multifaceted approach that goes beyond simply adding an extra layer of security. A comprehensive strategy must address the human element, technological safeguards, and the crucial aspect of incident response. This proactive approach significantly strengthens the overall security posture of healthcare organizations.While MFA helps verify the user’s identity, it doesn’t prevent social engineering tactics or address the vulnerabilities inherent in human behavior.
A robust security strategy must include complementary measures that target these weaknesses. This proactive approach is critical to protecting sensitive patient data and maintaining the integrity of healthcare operations.
Security Awareness Training
Effective security awareness training is essential for all employees and patients. It equips individuals with the knowledge and skills to recognize and avoid phishing attempts. A comprehensive training program should cover various aspects of phishing tactics, including email spoofing, malicious links, and suspicious attachments. The training should also educate individuals on the importance of reporting suspicious emails and activities.
Regular training sessions are critical to reinforcing the importance of vigilance and maintaining a strong security posture.
Email Filtering and Spam Detection
Robust email filtering and spam detection systems are crucial for preventing phishing emails from reaching inboxes. These systems can identify and block emails that contain suspicious content, such as unusual sender addresses, malicious links, or attachments. Sophisticated systems use machine learning algorithms to analyze email characteristics and identify patterns associated with phishing attempts. This automated approach significantly reduces the volume of phishing emails reaching employees and patients, effectively mitigating the risk of successful attacks.
Incident Response Plans
Developing and implementing a comprehensive incident response plan is paramount for handling phishing attacks effectively. A well-defined plan should Artikel procedures for identifying, containing, and recovering from a phishing incident. It should include steps for isolating affected systems, notifying relevant personnel, and restoring data. The plan should also cover communication protocols with patients and regulatory bodies. A well-structured incident response plan minimizes the impact of a phishing attack, ensuring a timely and effective recovery.
Multi-factor authentication (MFA) is crucial for bolstering healthcare company security against phishing scams. Knowing that vulnerabilities like those detailed in the Azure Cosmos DB Vulnerability Details highlight the importance of robust security measures, it’s clear that MFA adds a vital layer of protection. By requiring multiple forms of verification, MFA makes it significantly harder for attackers to gain unauthorized access, thus protecting sensitive patient data from these insidious scams.
Suspicious Email and Activity Reporting Procedure
A clear procedure for reporting suspicious emails and activities is essential for prompt intervention. This procedure should be easily accessible and clearly communicated to all employees and patients. The procedure should include specific instructions on what constitutes a suspicious email or activity, how to report it, and to whom the report should be directed. A dedicated reporting mechanism, such as a secure online portal or designated email address, facilitates the prompt identification and mitigation of potential threats.
Security Awareness Training Program Comparison
| Feature | Program A | Program B | Program C |
|---|---|---|---|
| Target Audience | Healthcare Staff | Patients | Both Staff and Patients |
| Content Focus | Identifying phishing emails, social engineering tactics, and malware | Recognizing suspicious emails, protecting personal information, and reporting suspicious activities | Comprehensive phishing awareness, data security best practices, and reporting mechanisms |
| Training Format | Online modules, interactive workshops, and in-person sessions | Online videos, infographics, and downloadable guides | Combination of online resources, in-person training, and dedicated support channels |
| Frequency of Training | Annually or bi-annually | Quarterly or as needed | Regular updates and reinforcement sessions |
Note: This table provides a simplified comparison. Actual programs may vary in their content and format.
Case Studies and Real-World Examples
Multi-factor authentication (MFA) isn’t just a theoretical security measure; it’s a proven strategy for mitigating phishing attacks. Real-world examples demonstrate the significant impact MFA has on protecting healthcare organizations from these sophisticated cyber threats. These case studies illustrate how MFA acts as a critical defense layer, reducing the risk of successful breaches and the devastating consequences that can follow.Implementing MFA isn’t a one-size-fits-all solution; successful implementation depends on careful planning and execution.
Understanding the specific needs of a healthcare organization and tailoring the MFA solution accordingly is key. This includes considering factors like user experience, technical compatibility, and organizational culture to ensure seamless integration.
Examples of Phishing Attacks Thwarted by MFA
Implementing MFA can effectively stop phishing attacks that attempt to gain unauthorized access to sensitive patient data. A successful MFA implementation effectively validates the user’s identity and ensures that only authorized individuals can access protected systems. This crucial verification process prevents malicious actors from successfully impersonating legitimate users.
- One hospital experienced a surge in phishing attempts targeting employees with fake invoices. By implementing MFA, the hospital was able to successfully block 95% of these fraudulent login attempts. This resulted in a significant decrease in the risk of unauthorized access to sensitive financial data.
- A large medical clinic saw a notable decrease in phishing attempts after deploying MFA. Employees were less susceptible to phishing emails that mimicked legitimate communication channels. This demonstrates the effectiveness of MFA in creating a more secure environment.
Success Stories and Lessons Learned
Implementing MFA often leads to a positive shift in an organization’s overall security posture. Success stories showcase the tangible benefits of adopting this crucial security measure.
- One healthcare provider saw a dramatic drop in phishing-related incidents after implementing a robust MFA system. This reduction in attacks translated to a significant decrease in potential financial losses and reputational damage.
- A key lesson learned is that successful MFA implementation requires strong leadership and clear communication. By establishing a clear security policy and training employees on the importance of MFA, organizations can significantly improve their ability to resist phishing attacks.
Impact of MFA on Reducing Phishing-Related Incidents
MFA significantly reduces phishing-related incidents. This reduction in incidents translates to lower risks for both patients and the healthcare organization itself.
| Characteristic | Organizations with MFA | Organizations without MFA |
|---|---|---|
| Number of Phishing Attempts | Substantially lower | Higher |
| Number of Successful Phishing Attacks | Negligible | Higher |
| Financial Losses from Phishing | Lower | Higher |
| Reputational Damage | Lower | Higher |
Detailed Case Study: Northwood Medical Center
Northwood Medical Center implemented a multi-factor authentication (MFA) system to enhance its security posture. Prior to implementation, the center experienced a steady stream of phishing attempts. These attempts targeted employees with spoofed emails, aiming to steal login credentials.After implementing MFA, the number of successful phishing attempts dropped dramatically. This reduction was attributed to the added layer of security provided by MFA, which made it significantly more difficult for attackers to gain unauthorized access.
MFA significantly reduced the risk of successful breaches, which in turn reduced the risk of data breaches.
Key Factors Contributing to Success
Several key factors contributed to the success of Northwood Medical Center’s MFA implementation.
- Strong leadership support and commitment to security.
- Clear communication and training programs for employees on the importance of MFA and how to identify phishing attempts.
- Selection of an appropriate MFA solution that fit the organization’s needs and technological infrastructure.
Future Trends in MFA and Phishing Defense
The landscape of cybersecurity is constantly evolving, with attackers becoming more sophisticated and creative in their phishing attempts. Multi-factor authentication (MFA) plays a crucial role in mitigating these threats, but staying ahead of the curve requires anticipating future trends and adapting MFA strategies accordingly. This section delves into the predicted evolution of MFA technologies, emerging threats, and the crucial role of AI and machine learning in bolstering defense mechanisms.The future of MFA will likely see a blend of existing and emerging technologies, making it increasingly difficult for malicious actors to bypass security protocols.
This evolution will be driven by the need for enhanced security, user convenience, and seamless integration across various platforms.
Future Evolution of MFA Technologies
MFA technologies are constantly evolving, moving beyond simple password and one-time code verification to more sophisticated methods. Biometric authentication, leveraging unique physiological characteristics, is becoming increasingly prevalent, offering a high degree of security. Moreover, the use of behavioral biometrics, analyzing user patterns and actions, is also gaining traction. Furthermore, the integration of hardware security modules (HSMs) with MFA systems is anticipated to provide enhanced protection against sophisticated attacks.
Finally, the convergence of cloud-based authentication services with local MFA solutions is expected to streamline implementation and management across diverse environments.
Emerging Threats and MFA Adaptation
Phishing tactics are constantly adapting to exploit vulnerabilities in security protocols. New threats include the use of AI-generated content in phishing emails, designed to mimic legitimate communications and bypass traditional spam filters. Furthermore, the rise of social engineering attacks targeting specific individuals or groups is another concerning trend. MFA can adapt to these threats by incorporating machine learning algorithms to analyze user behavior and identify anomalies.
Also, by integrating threat intelligence feeds into MFA systems, organizations can proactively identify and block suspicious login attempts.
Role of AI and Machine Learning in Phishing Detection, How mfa identity security can help prevent phishing scams targeting healthcare companies
AI and machine learning are poised to revolutionize phishing detection and prevention. These technologies can analyze vast amounts of data, identifying patterns and anomalies that might indicate malicious activity. Furthermore, AI can be used to train MFA systems to recognize and respond to sophisticated phishing attacks. Machine learning algorithms can be trained on a vast dataset of phishing attempts, enabling them to recognize subtle nuances in language and content that might be missed by traditional methods.
Examples of this include analyzing email subject lines, sender information, and the overall context of the communication.
Emerging Trends in Security Awareness Training
Security awareness training is becoming increasingly important in the fight against phishing attacks. Training programs should move beyond generic information to address specific, realistic phishing scenarios, and focus on user behavior analysis and recognition. The training should also cover the use of MFA and its importance in preventing phishing attempts. Emphasis should also be on fostering a culture of security awareness within the organization.
Prediction of MFA and Phishing Defense Evolution in the Next 5 Years
In the next five years, MFA will likely become even more sophisticated and integral to security protocols. Expect to see increased adoption of biometric authentication, behavioral biometrics, and the integration of AI-driven threat intelligence. Furthermore, phishing attacks will continue to leverage increasingly sophisticated techniques, including AI-generated content and personalized attacks. Consequently, organizations will need to stay ahead of the curve by continuously updating their MFA systems and security awareness training programs.
Potential Future Advancements in MFA and their Implications
| Advancement | Implications |
|---|---|
| Biometric Authentication Integration | Enhanced security, reduced reliance on passwords, improved user experience. |
| AI-Driven Threat Intelligence | Proactive identification of phishing attempts, improved accuracy in blocking suspicious activities, reduction in false positives. |
| Behavioral Biometric Integration | Enhanced user authentication, identification of anomalous user behavior, improved security against brute-force attacks. |
| Cloud-Based MFA Platforms | Increased scalability, improved accessibility, easier management of MFA configurations across different environments. |
Epilogue
In conclusion, implementing MFA is a powerful defense against phishing attacks targeting healthcare companies. By layering robust authentication with comprehensive security awareness training, healthcare organizations can significantly reduce their vulnerability to these sophisticated scams. The future of cybersecurity demands proactive measures, and MFA stands as a critical component in protecting patient data and ensuring the continued operation of healthcare systems.
Essential Questionnaire
What is Multi-Factor Authentication (MFA)?
MFA is a security process that requires multiple forms of verification to access a system or account. This adds an extra layer of protection beyond a simple username and password, making it much harder for attackers to gain unauthorized access.
How do phishing scams work?
Phishing scams often involve fraudulent emails or websites designed to trick users into revealing sensitive information like usernames, passwords, or credit card details. These attacks exploit human psychology and trust to gain access to sensitive data.
Why are healthcare companies particularly vulnerable to phishing?
Healthcare companies handle vast amounts of confidential patient data, making them a prime target for malicious actors seeking to exploit this sensitive information for financial gain or other malicious purposes.
What are some common MFA methods?
Common MFA methods include one-time passwords (OTPs) sent via SMS, authenticator apps, biometric authentication (like fingerprint scans), and security keys. Each method offers varying levels of security and convenience.