
Whats New in NIST Cybersecurity Framework CSF Version 2.0?
Whats new in version 2 0 of the nist cybersecurity framework csf – What’s new in version 2.0 of the NIST Cybersecurity Framework (CSF)? That’s the burning question on every cybersecurity professional’s mind! This update isn’t just a minor tweak; it’s a significant overhaul designed to make the framework more adaptable, user-friendly, and relevant to the ever-evolving threat landscape. We’re diving deep into the key changes, exploring the improvements to core functions, implementation tiers, and the crucial focus on supply chain security and emerging technologies.
Get ready to upgrade your cybersecurity knowledge!
This post breaks down the major updates in Version 2.0, comparing it to Version 1.1 and showing you how these changes impact your organization’s cybersecurity strategy, regardless of size. We’ll look at the enhanced core functions, the refined implementation tiers, and the critical additions focusing on supply chain resilience and the challenges presented by emerging technologies like AI and IoT.
Think of this as your essential guide to navigating the new and improved NIST CSF.
Overview of NIST CSF Version 2.0 Changes
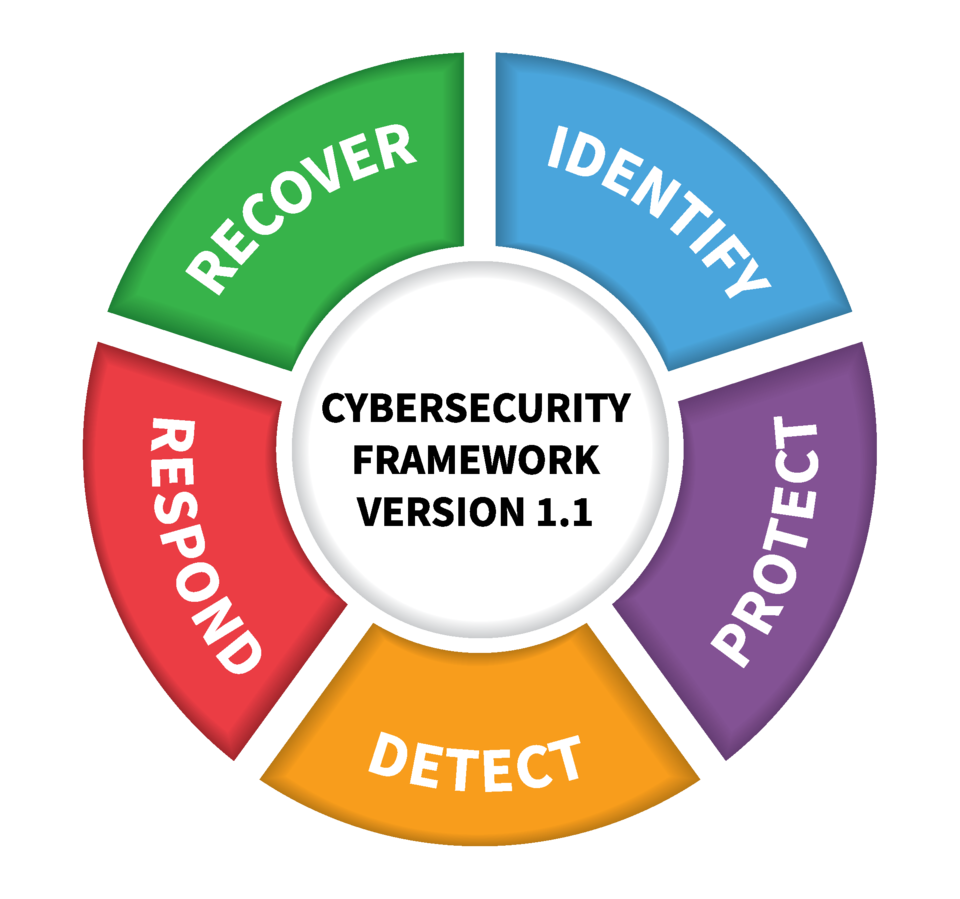
The NIST Cybersecurity Framework (CSF) Version 2.0 represents a significant evolution in cybersecurity guidance, addressing the increasingly complex and dynamic threat landscape. This revision isn’t just a minor update; it’s a response to the growing need for a more adaptable, user-friendly, and comprehensive framework capable of guiding organizations of all sizes and sectors in effectively managing their cybersecurity risks.
Motivations Behind the NIST CSF Revision
The primary drivers behind the revision were the need for enhanced clarity, improved usability, and increased flexibility to accommodate the evolving nature of cyber threats and technologies. Version 1.1, while impactful, lacked the granularity and adaptability required for organizations facing diverse challenges, from supply chain vulnerabilities to the rise of artificial intelligence and machine learning. The feedback received from numerous organizations using Version 1.1 highlighted areas needing improvement, particularly in the framework’s implementation and application across various contexts.
The updated framework aims to address these shortcomings and provide more tailored guidance.
Major Structural Changes in Version 2.0
Version 2.0 retains the core structure of the previous version – Identify, Protect, Detect, Respond, and Recover (the five functions) – but introduces significant refinements. The most notable change is the introduction of implementation tiers that are now more descriptive and provide more context. Instead of simply assigning a tier (Partial, Risk Informed, etc.), Version 2.0 provides more detailed descriptions for each tier, making it easier to assess an organization’s current cybersecurity posture and determine the appropriate level of implementation.
Additionally, Version 2.0 incorporates a more robust approach to supply chain risk management and clarifies the roles and responsibilities of various stakeholders. The framework’s profile is now more flexible, allowing organizations to tailor it to their specific needs and circumstances more effectively.
Improvements in Clarity and Usability
Version 2.0 prioritizes clarity and usability through several key improvements. The revised framework employs clearer language and more concise explanations, making it more accessible to a wider range of users, including those without extensive cybersecurity expertise. The updated implementation tiers provide a more nuanced understanding of maturity levels, facilitating better communication and collaboration among stakeholders. The enhanced guidance on incorporating the framework into existing organizational structures and processes simplifies implementation and integration.
Furthermore, the framework now offers improved guidance on integrating various cybersecurity standards and best practices, fostering a more holistic approach to cybersecurity management.
Comparison of Key Features: NIST CSF Version 1.1 vs. 2.0
The following table highlights the key differences between Version 1.1 and Version 2.0:
| Feature | Version 1.1 Description | Version 2.0 Description | Key Differences |
|---|---|---|---|
| Implementation Tiers | Broad, categorical descriptions (Partial, Risk Informed, etc.) | More detailed, descriptive tiers providing clearer guidance on implementation levels. | Increased granularity and improved clarity in defining maturity levels. |
| Framework Core | Five functions (Identify, Protect, Detect, Respond, Recover) | Same five functions, but with more detailed subcategories and guidance. | Enhanced clarity and improved guidance within each function. |
| Supply Chain Risk Management | Limited guidance | Expanded guidance and integration of supply chain risk management considerations. | Significant improvement in addressing supply chain vulnerabilities. |
| Usability and Clarity | Room for improvement in clarity and accessibility. | Improved language, more concise explanations, and enhanced user experience. | Enhanced accessibility and user-friendliness. |
Enhanced Core Functions and Profiles
NIST CSF Version 2.0 significantly enhances its core functions and profiles, offering organizations greater flexibility and customization in aligning their cybersecurity posture with their specific risk profiles. This improved framework allows for a more nuanced and effective approach to cybersecurity, moving beyond a one-size-fits-all model. The changes directly address the need for adaptable cybersecurity strategies in today’s dynamic threat landscape.
Enhancements to the Five Core Functions
Version 2.0 refines the five core functions—Identify, Protect, Detect, Respond, and Recover—providing clearer guidance and more granular detail. The improvements aim to help organizations better understand their unique cybersecurity needs and develop tailored strategies to address them effectively.
- Identify: This function now emphasizes the importance of understanding the organization’s assets, their value, and the associated risks. The updated framework provides more detailed guidance on asset discovery, inventory management, and risk assessment methodologies, encouraging a more comprehensive understanding of the organization’s overall risk posture.
- Protect: Version 2.0 strengthens the guidance on implementing security controls, emphasizing the need for a layered approach to security. This includes more robust guidance on access control, data security, and system hardening, aligning with best practices and industry standards.
- Detect: Improvements focus on enhancing the ability to identify cybersecurity incidents promptly and accurately. The framework provides more detailed guidance on implementing security monitoring tools, threat intelligence integration, and incident detection methodologies.
- Respond: This function is strengthened by providing a more structured approach to incident response planning and execution. The updated framework emphasizes the importance of having well-defined procedures, pre-defined roles and responsibilities, and the ability to effectively contain and mitigate the impact of security incidents.
- Recover: Version 2.0 highlights the importance of having a robust recovery plan to restore systems and data after a security incident. The updated framework provides more detailed guidance on recovery strategies, data backups, and disaster recovery planning, ensuring business continuity and resilience.
Improved Profile Flexibility and Customization
The updated profiles in Version 2.0 offer significantly enhanced flexibility and customization, allowing organizations to tailor their cybersecurity strategies to their specific needs and risk environments. This contrasts with the previous version, which offered less granularity in profile selection. The framework now allows for the creation of custom profiles that reflect the organization’s unique characteristics, industry, and risk tolerance.
Examples of Tailored Profiles
A large financial institution might create a profile emphasizing stringent data protection measures and robust incident response capabilities due to the sensitive nature of its data and the potential impact of a breach. Conversely, a small non-profit organization might prioritize basic security controls and incident awareness training, focusing on cost-effectiveness and simplicity.
Hypothetical Profile for a Small Business
Let’s consider “Acme Coffee,” a small coffee shop with a basic point-of-sale (POS) system and Wi-Fi network.
Their hypothetical profile might include:
- Identify: Inventory of key assets (POS system, customer data, financial records). Basic risk assessment focusing on common threats like malware and phishing.
- Protect: Strong passwords, basic firewall on the Wi-Fi router, regular software updates for the POS system, employee security awareness training.
- Detect: Basic intrusion detection system alerts on the router, monitoring of POS system logs for unusual activity. Simple monitoring of network traffic for suspicious patterns.
- Respond: A simple incident response plan outlining steps to take in case of a security breach, including contact information for IT support and law enforcement if necessary.
- Recover: Regular data backups to an external drive, a basic disaster recovery plan outlining steps to restore operations if the POS system fails.
The rationale is to implement cost-effective measures to mitigate common threats, focusing on protecting customer data and ensuring business continuity. This profile reflects a pragmatic approach to cybersecurity for a small business with limited resources.
Improved Implementation Tiers
NIST CSF Version 2.0 significantly refines its implementation tiers, moving beyond simple labels to provide a more nuanced understanding of organizational cybersecurity maturity. The revised tiers offer a clearer pathway for organizations to improve their cybersecurity posture, regardless of their starting point. This improved granularity allows for better self-assessment and targeted improvement planning.The revised tiers – Partial, Risk-Informed, Repeatable, and Adaptive – better reflect the diverse capabilities and maturity levels found across organizations.
They provide a more accurate representation of an organization’s cybersecurity journey, moving away from a purely binary “compliant/non-compliant” model to a more progressive and adaptable framework. This allows for a more realistic and effective approach to cybersecurity improvement.
Implementation Tier Descriptions
The following points Artikel the key characteristics of each implementation tier. Understanding these distinctions is crucial for organizations seeking to assess their current state and plan for future improvements.
- Partial: Organizations at this tier demonstrate foundational cybersecurity practices but lack comprehensive coverage across all functions. Security activities are often reactive and inconsistent. They may have implemented some basic security controls but lack a cohesive strategy or integrated approach. An example might be a small business with basic antivirus software but lacking a formal incident response plan or regular security assessments.
- Risk-Informed: Organizations at this tier have a more comprehensive understanding of their cybersecurity risks and prioritize their resources accordingly. They have established a risk management process and align their security controls with identified threats and vulnerabilities. They perform regular risk assessments and incorporate risk-based decision-making into their security practices. A mid-sized company with a dedicated security team conducting regular vulnerability scans and penetration testing, prioritizing remediation based on risk levels, would fall into this category.
- Repeatable: Organizations at this tier have established repeatable processes and procedures for managing cybersecurity risks. Their security controls are well-documented, consistently implemented, and regularly monitored. They have implemented a robust incident response plan and conduct regular security awareness training. A large enterprise with a mature security operations center (SOC) that consistently monitors and responds to security incidents, along with established change management processes, would be an example.
- Adaptive: Organizations at this tier demonstrate a high level of cybersecurity maturity. They proactively anticipate and respond to emerging threats and vulnerabilities. They continuously improve their security posture through ongoing monitoring, assessment, and adaptation. They leverage advanced technologies and techniques, such as threat intelligence and automated security controls. A leading technology company with a highly sophisticated security program, employing advanced threat hunting and machine learning for proactive security, would exemplify this tier.
Focus on Supply Chain Security
The NIST Cybersecurity Framework (CSF) Version 2.0 significantly enhances its approach to supply chain risk management, recognizing the increasingly interconnected nature of modern organizations and the pervasive threat posed by vulnerabilities within the supply chain. This isn’t just about protecting your own systems; it’s about understanding and managing the risks introduced by the numerous third-party vendors and suppliers that support your operations.
Version 2.0 provides more concrete guidance and tools to effectively address these complex challenges.Version 2.0 strengthens supply chain security by integrating risk management considerations throughout the framework’s core functions. It moves beyond simply identifying vulnerabilities to incorporating proactive risk assessment and mitigation strategies across the entire lifecycle of relationships with third-party vendors. This includes due diligence during vendor selection, ongoing monitoring of their security posture, and incident response planning that accounts for the impact of supply chain disruptions.
Supply Chain Risk Management Enhancements in Version 2.0
The improvements are multifaceted. The framework now explicitly addresses the need for robust vendor risk management programs, including the assessment of their cybersecurity practices, incident response capabilities, and overall security posture. The updated guidance emphasizes the importance of contractual agreements that clearly define cybersecurity responsibilities and expectations for vendors. Furthermore, Version 2.0 encourages organizations to utilize a risk-based approach to managing their supply chains, focusing resources on the most critical vendors and the highest-impact risks.
This includes considering the potential impact of a compromise on the organization’s operations, reputation, and financial stability.
Assessing and Mitigating Third-Party Vendor Risks
The CSF helps organizations assess and mitigate third-party vendor risks by providing a structured approach to identifying, analyzing, and responding to potential threats. This involves establishing clear criteria for vendor selection, conducting thorough due diligence, and regularly monitoring their security performance. The framework’s Identify function guides organizations in understanding their dependencies on third-party vendors and mapping out their supply chain relationships.
The Protect, Detect, Respond, and Recover functions then provide a roadmap for implementing appropriate security controls and incident response plans to address the risks associated with these relationships. For example, a thorough risk assessment might involve questionnaires, security audits, and penetration testing of critical vendors. The results of these assessments can then inform the development of appropriate mitigation strategies, such as requiring specific security controls or implementing monitoring mechanisms.
Integrating Supply Chain Security into an Organization’s Cybersecurity Strategy
Integrating supply chain security considerations into an overall cybersecurity strategy requires a holistic approach. It starts with identifying all critical vendors and dependencies, then assessing the associated risks. This assessment should consider the potential impact of a compromise on the organization’s operations, reputation, and financial stability. The results inform the development of a risk mitigation plan, which might involve contractual agreements, security requirements, and regular monitoring.
This plan should be integrated into the organization’s broader cybersecurity strategy, ensuring alignment with its overall security objectives and risk tolerance. Regular review and updates to the plan are crucial to adapt to changing threats and business needs. For example, a financial institution might prioritize vendors handling sensitive customer data, implementing stricter security controls and more frequent audits for those providers.
Assessing and Managing Supply Chain Risks Using the CSF: A Flowchart, Whats new in version 2 0 of the nist cybersecurity framework csf
The following flowchart illustrates a simplified process for assessing and managing supply chain risks using the NIST CSF. Imagine this flowchart as a visual representation of a cyclical process.[Imagine a flowchart here. The flowchart would begin with “Identify Critical Vendors and Dependencies.” This would lead to “Assess Vendor Risk (using NIST CSF functions)”. This would then branch to “Develop Mitigation Strategies (based on risk assessment)”.
Next would be “Implement and Monitor Controls”. Finally, there would be a loop back to “Assess Vendor Risk,” representing the continuous monitoring and reassessment of vendor security.] The flowchart would visually represent the iterative nature of the process, showing the continuous loop of risk assessment, mitigation, implementation, monitoring, and reassessment. The boxes would represent the key steps, and arrows would indicate the flow of the process.
The NIST CSF functions (Identify, Protect, Detect, Respond, Recover) would be integrated into the assessment and mitigation steps.
Addressing Emerging Technologies

NIST CSF Version 2.0 recognizes the rapid evolution of technology and its impact on cybersecurity. The framework’s updated guidance directly addresses the challenges posed by emerging technologies, providing a flexible and adaptable approach to risk management in increasingly complex digital environments. This ensures organizations can effectively protect their assets regardless of the technologies they utilize.The updated framework offers specific guidance on integrating security considerations into the design, development, and deployment phases of emerging technologies, rather than treating security as an afterthought.
This proactive approach is crucial for mitigating risks and maintaining a strong security posture.
Cloud Security Guidance
Version 2.0 provides enhanced guidance on securing cloud environments. It emphasizes the importance of a shared responsibility model, clarifying the roles and responsibilities of both cloud providers and organizations using their services. The framework encourages organizations to leverage cloud-native security tools and services while maintaining visibility and control over their data and systems. This includes detailed considerations for various cloud deployment models, such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
For example, an organization adopting a PaaS model needs to focus on securing the applications and data deployed within the platform, while the provider handles the underlying infrastructure. Similarly, for SaaS, the focus shifts to secure configuration and data access management.
Securing AI and IoT Systems
The framework offers practical advice for managing the unique risks associated with Artificial Intelligence (AI) and Internet of Things (IoT) systems. For AI, this includes guidance on securing AI models and datasets from unauthorized access or manipulation. This is critical given the increasing reliance on AI for decision-making across various sectors. For IoT, the framework highlights the need for secure device management, firmware updates, and data encryption to mitigate risks from vulnerabilities and potential attacks on interconnected devices.
Consider, for example, a smart city deploying numerous IoT sensors for traffic management. The framework guides the city on securing these sensors against unauthorized access and ensuring the integrity of the data collected. Failing to do so could lead to traffic disruption or even safety hazards.
Adaptability to Future Advancements
A key strength of the NIST CSF Version 2.0 is its inherent adaptability. The framework is not designed to be a static document; instead, it provides a flexible foundation that can be adjusted to accommodate future technological advancements. This adaptability is achieved through its core functions and implementation tiers, which can be tailored to specific contexts and emerging technologies.
The framework’s focus on risk management principles ensures its continued relevance, even as the threat landscape evolves. For example, the emergence of quantum computing presents significant risks to existing cryptographic systems. While the framework doesn’t specifically address quantum computing, its flexible nature allows organizations to incorporate new guidance and best practices related to post-quantum cryptography as they become available.
Examples of Risk Management with Emerging Technologies
Organizations can utilize the NIST CSF Version 2.0 to manage risks associated with specific emerging technologies through a risk-based approach. This involves identifying assets, threats, and vulnerabilities associated with each technology, and then implementing appropriate safeguards. For instance, an organization deploying an AI-powered system for fraud detection needs to consider the security of the training data, the model itself, and the infrastructure it runs on.
Similarly, a healthcare provider implementing IoT devices for patient monitoring must ensure the confidentiality, integrity, and availability of patient data transmitted through these devices. By following the framework’s guidance, organizations can develop a comprehensive security program that addresses the unique risks posed by these technologies, minimizing their impact and ensuring business continuity.
Improved Communication and Collaboration: Whats New In Version 2 0 Of The Nist Cybersecurity Framework Csf
Version 2.0 of the NIST Cybersecurity Framework significantly enhances communication and collaboration among stakeholders, a crucial aspect often overlooked in cybersecurity implementation. The updated framework provides a common language and structured approach, fostering better information sharing and coordinated responses to cybersecurity threats. This improved communication not only streamlines efforts but also strengthens an organization’s overall cybersecurity posture.Improved communication and collaboration are facilitated through several key enhancements in the framework.
The clearer articulation of roles and responsibilities, coupled with the emphasis on shared understanding of risk and priorities, significantly reduces ambiguity and potential for miscommunication. This leads to more efficient resource allocation and more effective response to incidents.
Enhanced Information Sharing Mechanisms
Version 2.0 promotes information sharing through a more robust and structured approach. The framework now explicitly encourages organizations to participate in Information Sharing and Analysis Centers (ISACs) and other relevant collaborative platforms. This structured approach, coupled with the improved clarity of the framework itself, allows for easier identification of shared threats and vulnerabilities. For example, an organization experiencing a phishing attack can more easily communicate the details and learn from the experiences of others within their industry’s ISAC, potentially preventing similar attacks on other organizations.
The increased transparency and standardized reporting facilitated by the framework improve the quality and speed of information exchange.
Streamlined Collaboration Across Organizational Boundaries
The revised framework encourages collaboration not only within an organization but also across organizational boundaries, particularly within supply chains. The increased focus on supply chain security in Version 2.0 necessitates more robust communication and collaboration with vendors and partners. This collaborative approach involves establishing clear communication channels, defining roles and responsibilities for security, and implementing mechanisms for information sharing and incident response.
For instance, a manufacturing company can use the framework to establish clear communication protocols with its component suppliers regarding security vulnerabilities and remediation efforts. This helps to mitigate risks throughout the entire supply chain.
A Communication Plan for Implementing Version 2.0
Implementing Version 2.0 effectively requires a well-defined communication plan. This plan should identify key stakeholders, establish communication channels, and Artikel a schedule for disseminating information.
Key Stakeholders: This includes executive leadership, IT staff, security personnel, legal counsel, vendors, and potentially customers depending on the organization’s industry and risk profile. For a financial institution, for example, regulatory bodies would also be a key stakeholder.
Communication Methods: A multi-faceted approach is recommended, utilizing methods such as regular meetings, email updates, training sessions, and potentially a dedicated internal communication portal or wiki. Regular updates on progress, challenges, and successes are crucial for maintaining engagement and buy-in from all stakeholders.
Communication Schedule: A phased approach, aligned with the implementation timeline of Version 2.0, is recommended. Initial communications should focus on raising awareness and explaining the benefits of the upgrade. Subsequent communications should focus on specific implementation steps, timelines, and required actions from different stakeholder groups. Finally, ongoing communication is necessary to address any issues, share lessons learned, and maintain momentum.
Final Thoughts
The NIST Cybersecurity Framework Version 2.0 isn’t just an update; it’s a significant step forward in cybersecurity preparedness. By enhancing clarity, improving flexibility, and addressing the realities of modern threats, including those posed by emerging technologies and complex supply chains, Version 2.0 empowers organizations of all sizes to build a more robust and resilient cybersecurity posture. Don’t get left behind – embrace these changes and elevate your organization’s security game! Let’s get started on implementing these updates.
Clarifying Questions
What’s the biggest change in NIST CSF Version 2.0?
The most significant change is the increased focus on flexibility and adaptability. Version 2.0 allows for greater customization to suit different organizational needs and risk profiles.
How does Version 2.0 address supply chain risks?
Version 2.0 provides more explicit guidance on assessing and mitigating risks from third-party vendors and throughout the entire supply chain, recognizing its importance in overall security.
Is the new framework harder to implement?
While more comprehensive, Version 2.0 aims for improved clarity and usability, making implementation easier through clearer guidance and improved structure.
What about the cost of implementing Version 2.0?
The cost varies greatly depending on the organization’s size and existing security infrastructure. However, the improved clarity and focus should streamline implementation, potentially reducing overall costs in the long run.
