Whos Responsible for Securing Open Source Software?
Whos responsible for securing the open source software organizations used to build all applications – Who’s responsible for securing the open source software organizations used to build all applications? It’s a question that keeps me up at night! We rely on open-source software for practically everything, from the apps on our phones to the websites we visit daily. But who’s actually ensuring these foundational building blocks are safe and secure? It’s not a simple answer, and it involves a complex web of developers, maintainers, users, and even funding bodies.
This post dives into the shared responsibility model, exploring the roles and responsibilities of each player in this crucial ecosystem.
The reality is that securing open source is a collaborative effort, not a single entity’s burden. From the initial coding and rigorous testing to the ongoing maintenance and patching of vulnerabilities, many hands are needed to keep the digital world safe. We’ll explore the various stages of this process, looking at how each stakeholder contributes (or sometimes fails to contribute!) to the overall security posture.
We’ll also discuss the legal and ethical implications, as well as the crucial role of funding and community support in maintaining a secure open-source landscape.
The Role of Open Source Software Organizations

Open source software (OSS) organizations play a vital role in the development and maintenance of the software that underpins much of the modern digital world. They represent a diverse range of structures and governance models, all united by the principle of collaborative development and open access to source code. Understanding their function is crucial to grasping the complexities of software security in the modern age.
Open Source Software Organization Structure and Governance
OSS organizations vary significantly in their structure, from informal collaborations around a single project to large, established foundations with dedicated staff and complex governance mechanisms. Some are centered around a specific project, while others act as umbrellas for multiple projects. Governance models are equally diverse, ranging from a benevolent dictator (BDFL) model, where a single individual makes key decisions, to more distributed models involving committees, voting systems, or consensus-based decision-making.
The Apache Software Foundation, for example, uses a meritocratic system where contributors earn commit access based on their contributions and adherence to the foundation’s guidelines. The Linux Foundation, on the other hand, employs a more formalized structure with various projects and working groups under its umbrella. Choosing the right governance model depends on the project’s size, goals, and community dynamics.
Types of Contributions to Open Source Projects
Contributing to an OSS project isn’t limited to writing code. While code contributions are essential, they represent only one piece of the puzzle. A healthy OSS project relies on a diverse range of contributions, including: code development (writing new features, fixing bugs), documentation (writing user manuals, tutorials, and API documentation), testing (writing unit tests, integration tests, and user acceptance tests), design (creating user interfaces and improving the overall user experience), community management (moderating discussions, answering questions, and welcoming new contributors), and translation (making the software accessible to a wider audience).
Each of these contributions is vital for the success and sustainability of the project.
Responsibilities of Maintainers and Project Leaders, Whos responsible for securing the open source software organizations used to build all applications
Maintainers and project leaders in OSS projects bear significant responsibility for the health and security of the software. Maintainers are typically responsible for reviewing code contributions, merging changes, addressing bug reports, and responding to user inquiries. Project leaders, often a subset of maintainers, have broader responsibilities, including strategic planning, community management, resource allocation, and ensuring the project aligns with its goals.
They often play a crucial role in fostering a healthy and inclusive community, attracting new contributors, and managing conflicts. Effective leadership is critical for the long-term success and security of an OSS project. The maintainers act as gatekeepers, ensuring code quality and security before it’s integrated into the main codebase.
Security Responsibilities of Stakeholders in Open Source Projects
The security of an OSS project is a shared responsibility, not solely the domain of maintainers. Different stakeholders have varying levels of responsibility depending on their role and involvement.
| Stakeholder | Responsibility | Level of Responsibility | Example |
|---|---|---|---|
| Developers | Writing secure code, following secure coding practices, participating in code reviews | High | Using parameterized queries to prevent SQL injection vulnerabilities. |
| Users | Reporting security vulnerabilities, updating software promptly, using secure configurations | Medium | Reporting a cross-site scripting (XSS) vulnerability found on the project’s website. |
| Maintainers | Reviewing code for security flaws, addressing security vulnerabilities promptly, releasing security updates | High | Patching a critical vulnerability identified in a recent security audit. |
| Funding Bodies | Providing resources for security audits, bug bounty programs, and security training | Medium | Funding a security audit of a critical OSS project used in a government system. |
Identifying Security Vulnerabilities in Open Source Software: Whos Responsible For Securing The Open Source Software Organizations Used To Build All Applications
Open-source software (OSS) powers a significant portion of the modern digital landscape, from the operating systems on our computers to the libraries underpinning countless applications. However, its very nature – publicly available source code – presents unique security challenges. Understanding the types of vulnerabilities present, how they’re discovered, and how to mitigate them is crucial for both developers and users.
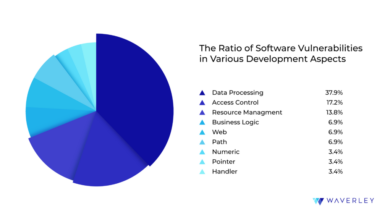
Common Types of Security Vulnerabilities in Open Source Software
Open-source projects, while benefiting from community scrutiny, are still susceptible to a range of security flaws. These vulnerabilities often stem from coding errors, outdated dependencies, or insufficient security testing. Common categories include buffer overflows, SQL injection flaws, cross-site scripting (XSS) vulnerabilities, and insecure authentication mechanisms. Buffer overflows, for example, occur when a program attempts to write data beyond the allocated buffer size, potentially leading to crashes or arbitrary code execution.
SQL injection attacks exploit vulnerabilities in database interactions to execute malicious SQL commands. XSS attacks inject malicious scripts into websites, potentially stealing user data or redirecting users to phishing sites. Insecure authentication mechanisms, such as weak passwords or lack of multi-factor authentication, can allow unauthorized access to systems.
Examples of Real-World Security Incidents Involving Open Source Components
Numerous high-profile incidents highlight the potential risks associated with vulnerabilities in open-source components. The infamous Heartbleed vulnerability in OpenSSL, discovered in 2014, allowed attackers to steal sensitive data, including private keys and passwords, from millions of servers. Similarly, the Equifax data breach in 2017 was partly attributed to the exploitation of a known vulnerability in the Apache Struts framework.
These incidents underscore the far-reaching consequences of unpatched vulnerabilities in widely used open-source components, emphasizing the importance of timely updates and robust security practices. The Log4j vulnerability (CVE-2021-44228), discovered in late 2021, impacted a vast number of applications due to its widespread use in logging libraries and demonstrated the cascading effect of vulnerabilities in seemingly minor components.
So, who’s ultimately on the hook for securing the open-source components that underpin nearly every application? It’s a complex question, involving everyone from the original developers to the organizations using the software. This responsibility becomes even more critical when considering the rapid evolution of application development, as highlighted in this insightful article on domino app dev the low code and pro code future , which underscores the need for robust security practices throughout the entire software lifecycle.
Ultimately, shared responsibility is key to mitigating risks associated with open-source software vulnerabilities.
Methods for Identifying and Reporting Security Vulnerabilities in Open Source Projects
Several methods exist for identifying and reporting vulnerabilities in open-source projects. Static analysis tools automatically scan code for potential vulnerabilities without executing the code. Dynamic analysis tools, on the other hand, analyze the running application to identify vulnerabilities during runtime. Penetration testing simulates real-world attacks to identify weaknesses in the system. Community-driven vulnerability scanning initiatives, such as those run by various security research groups, also play a vital role in uncovering vulnerabilities.
Reporting vulnerabilities responsibly is crucial; many open-source projects have established vulnerability disclosure programs that guide researchers on how to report issues securely and responsibly, minimizing the risk of exploitation before a fix is implemented.
A Process for Vulnerability Disclosure and Remediation in an Open-Source Project
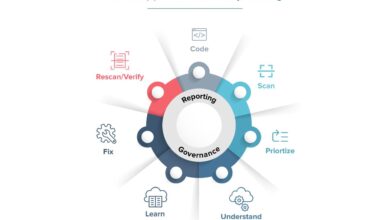
A robust vulnerability disclosure process is essential for effectively addressing security flaws in open-source projects. This process typically involves: 1) A clear vulnerability reporting mechanism (e.g., a dedicated email address or a bug tracking system); 2) A coordinated vulnerability assessment and verification process; 3) A secure communication channel between the reporter and the development team; 4) A timeline for remediation and patch release; 5) Public disclosure of the vulnerability and the fix after remediation.
This structured approach ensures responsible disclosure, minimizes the impact of vulnerabilities, and fosters trust among users and contributors. Transparency is key; keeping the community informed about vulnerabilities and their fixes helps build confidence in the project’s security posture.
Security Practices in Open Source Development
Open source software (OSS) relies heavily on community contributions, making security a shared responsibility. Robust security practices are crucial not only for the integrity of individual projects but also for the broader ecosystem’s trust and stability. Neglecting security can lead to vulnerabilities exploited by malicious actors, impacting millions of users and damaging the reputation of the project and its contributors.Secure coding practices are paramount in mitigating security risks within open-source projects.
These practices involve implementing coding standards and techniques that minimize vulnerabilities from the outset. This proactive approach is far more efficient and cost-effective than addressing vulnerabilities after they’ve been discovered.
Secure Coding Best Practices
Secure coding in open source necessitates a multi-faceted approach. Developers should prioritize using secure libraries and frameworks, regularly updating dependencies to patch known vulnerabilities, and implementing input validation to prevent injection attacks (like SQL injection or cross-site scripting). Furthermore, adhering to coding style guides and utilizing static analysis tools can significantly reduce the likelihood of introducing vulnerabilities during the development process.
Employing secure coding principles like least privilege and defense in depth are also vital. For example, limiting the permissions a program has access to and implementing multiple layers of security checks can make it harder for attackers to exploit any single weakness.
Code Reviews and Automated Security Testing
Code reviews provide a critical layer of defense against security vulnerabilities. Having multiple developers examine code before merging it into the main branch allows for the identification of potential weaknesses that might have been missed by the original author. Automated security testing complements this process by automatically scanning code for known vulnerabilities and enforcing coding standards. Tools like SonarQube or static analysis plugins within IDEs can automatically detect common vulnerabilities such as buffer overflows or insecure handling of sensitive data.
Regular automated testing as part of the Continuous Integration/Continuous Delivery (CI/CD) pipeline ensures that security checks are consistently applied, even with frequent code changes.
Security Audits and Penetration Testing
While code reviews and automated testing are valuable, comprehensive security audits and penetration testing provide a more thorough evaluation of a project’s security posture. Independent security audits involve expert review of the codebase, design, and architecture to identify potential weaknesses. Penetration testing simulates real-world attacks to assess the effectiveness of security controls and identify vulnerabilities that might be missed by static analysis.
These rigorous assessments provide a clear understanding of the project’s overall security risks and help prioritize remediation efforts. For instance, a recent audit of a popular open-source project revealed a critical vulnerability in its authentication system, highlighting the importance of these comprehensive reviews.
Essential Security Tools and Technologies
A robust security posture requires leveraging various tools and technologies. The selection will depend on the project’s specific needs and resources, but a combination of the following is generally beneficial:
- Static Application Security Testing (SAST) tools: These tools analyze source code to identify potential vulnerabilities without actually executing the code. Examples include SonarQube, Coverity, and FindBugs.
- Dynamic Application Security Testing (DAST) tools: These tools test running applications to identify vulnerabilities during runtime. Examples include OWASP ZAP and Burp Suite.
- Software Composition Analysis (SCA) tools: These tools analyze project dependencies to identify known vulnerabilities in open-source libraries. Examples include Snyk and Black Duck.
- Secret management tools: These tools help securely store and manage sensitive information like API keys and database credentials. Examples include HashiCorp Vault and AWS Secrets Manager.
- Vulnerability databases: These databases track known vulnerabilities and provide information on how to remediate them. The National Vulnerability Database (NVD) is a key example.
The Responsibility of End-Users and Integrators
The security of applications built using open-source components isn’t solely the responsibility of the open-source projects themselves. End-users and, critically, the developers who integrate these components into their applications bear a significant burden. Failing to properly manage and secure these dependencies can lead to serious vulnerabilities, exposing entire systems to attack. This section explores the crucial role end-users and integrators play in maintaining a secure software ecosystem.Developers integrating open-source components into their applications are responsible for vetting those components, understanding their functionality and potential risks, and implementing secure integration practices.
This involves more than just downloading and dropping the code; it requires a thorough understanding of the component’s security posture and how it interacts with the surrounding application. Neglecting this responsibility can lead to vulnerabilities being introduced directly into the application itself, regardless of the security of the open-source component in isolation.
Keeping Open-Source Components Up-to-Date
Regularly updating open-source components with the latest security patches is paramount. Outdated components are prime targets for attackers, as known vulnerabilities often remain unpatched in older versions. This is especially true for widely used components, where attackers are incentivized to exploit known weaknesses. For example, a failure to update a widely used logging library could expose sensitive information to unauthorized access.
A proactive patching strategy, coupled with automated update mechanisms, is crucial for mitigating this risk. Delaying updates increases the window of vulnerability and the potential impact of a successful attack.
Best Practices for Securely Integrating Open-Source Components
Securely integrating open-source components involves several key practices. First, thoroughly vet the components you choose. Look for projects with active maintenance, a strong community, and a history of addressing security issues promptly. Second, carefully review the component’s code, looking for potential vulnerabilities or unexpected behavior. While a full code audit might not always be feasible, a basic security assessment can identify significant risks.
Third, minimize the component’s privileges within your application. Grant only the necessary permissions, preventing it from accessing sensitive data or performing actions it doesn’t need. Finally, thoroughly test the integration before deploying it to a production environment. This testing should include both functional testing and security testing, to ensure that the integration doesn’t introduce new vulnerabilities.
Utilizing Dependency Management Tools
Dependency management tools are invaluable for improving the security of open-source integrations. These tools help track dependencies, manage versions, and automatically update components when security patches are released. Popular examples include npm for JavaScript, Maven for Java, and pip for Python. Using these tools significantly reduces the risk of using outdated or vulnerable components. For instance, a tool like npm can automatically identify and install the latest version of a package, including any security updates.
Furthermore, many dependency management tools offer features like vulnerability scanning, which can proactively alert developers to potential security issues within their dependencies. By streamlining the process of updating and managing dependencies, these tools drastically reduce the human error that often contributes to security vulnerabilities.
Legal and Ethical Considerations
The widespread adoption of open-source software (OSS) has introduced a complex interplay of legal and ethical responsibilities for developers, users, and distributors. Understanding these considerations is crucial for mitigating risks and fostering a sustainable ecosystem. Failure to do so can lead to significant legal liabilities and ethical dilemmas.
Legal Liabilities Associated with OSS
Using and distributing OSS involves several potential legal liabilities. License compliance is paramount; violating the terms of a license, such as the GPL or MIT license, can result in legal action. This includes improper attribution, unauthorized modification for commercial purposes contrary to the license, or failure to comply with distribution requirements. Furthermore, the incorporation of OSS into a commercial product might expose the user to liability if the OSS contains vulnerabilities that cause harm.
This is particularly relevant in contexts like medical devices or critical infrastructure where software failures can have severe consequences. Finally, intellectual property rights, including patents, must be carefully considered; using OSS that infringes on existing patents can lead to legal challenges.
Ethical Responsibilities of OSS Developers and Users
Beyond legal obligations, ethical considerations play a vital role in the OSS community. Developers have an ethical responsibility to disclose known vulnerabilities promptly and to actively participate in the maintenance and security updates of their projects. This proactive approach fosters trust and reduces the risk of exploitation. Users, in turn, have an ethical duty to report vulnerabilities they discover responsibly to the developers, rather than exploiting them for personal gain.
This collaborative approach is crucial for maintaining the integrity and security of the OSS ecosystem. Furthermore, the ethical use of OSS includes avoiding its deployment in projects that could cause harm or violate ethical principles, regardless of legal permissibility.
Legal Frameworks Governing OSS Across Jurisdictions
The legal landscape surrounding OSS varies significantly across jurisdictions. While many countries recognize the validity of open-source licenses, the specific interpretation and enforcement of these licenses can differ. For instance, the recognition of copyright and the remedies available for infringement may vary. Additionally, data protection laws, such as GDPR in Europe, impose specific requirements on how personal data is handled, impacting the use of OSS in data-processing applications.
Navigating these differences requires careful consideration of the applicable laws in each relevant jurisdiction. The lack of a unified global legal framework presents challenges for international collaborations and the consistent application of OSS licensing.
Scenario: Conflict Between Legal and Ethical Responsibilities
Imagine a developer discovers a critical vulnerability in a widely used open-source library. Legally, the developer might be obligated to report this to the copyright holder or the project maintainers, depending on the license. However, the developer might also ethically feel pressured to disclose this vulnerability publicly immediately to warn a large user base potentially affected by a major security flaw.
This conflict arises when the legal process for disclosure is slow or opaque, potentially leaving users vulnerable in the interim. The developer must weigh the potential legal ramifications of unauthorized disclosure against the potential harm caused by delayed notification. This scenario highlights the need for clear communication channels and efficient vulnerability disclosure processes to mitigate such conflicts.
The Role of Funding and Support
The security of open-source software (OSS) isn’t solely dependent on the coding prowess of its contributors; it’s inextricably linked to the availability of consistent funding and robust community support. A well-funded project can dedicate resources to security audits, bug bounty programs, and the development of secure coding practices, ultimately leading to a more resilient and secure software ecosystem. Conversely, underfunded projects often struggle to maintain even basic security measures, leaving them vulnerable to exploitation.Funding models significantly influence the security posture of open-source projects.
Projects relying solely on volunteer contributions often face inconsistent resource allocation, making it difficult to prioritize security improvements. In contrast, projects with diversified funding streams, including corporate sponsorships, grants, and community donations, are better equipped to address security concerns proactively. This allows for dedicated security teams, regular security audits, and prompt responses to vulnerabilities.
Funding Models and Their Impact on Security
Different funding models have varying impacts on OSS security. For example, a project funded primarily through a single corporate sponsor might be susceptible to biases or limitations imposed by that sponsor’s interests. A community-driven model, relying on numerous small donations, can offer greater independence but might lack the resources for large-scale security initiatives. A hybrid approach, combining corporate sponsorships with community contributions and grants, often proves most effective in balancing resources and maintaining project independence.
The Open Source Security Foundation (OpenSSF) exemplifies this, supporting various projects through grants and collaborations, fostering a more secure open-source landscape.
Community Support and Security Maintenance
A vibrant and engaged community is crucial for maintaining the security of OSS. Active community members can contribute to vulnerability detection and reporting, participate in security audits, and assist in the development and implementation of security best practices. A strong community fosters a culture of security awareness and encourages responsible disclosure of vulnerabilities. Projects with active and responsive communities are better positioned to quickly address security issues, mitigating potential risks before they can be exploited.
The Linux kernel, for instance, benefits from a vast and active community, enabling rapid identification and resolution of security vulnerabilities.
Organizational Contributions to Open Source Security
Organizations can significantly contribute to OSS security through various means. Direct financial support, in the form of grants or sponsorships, allows projects to hire security experts, conduct regular audits, and implement robust security measures. Organizations can also contribute by providing resources like infrastructure, expertise, or dedicated personnel. Some organizations even dedicate internal teams to work on open-source security projects, improving the overall security of the software they use and contributing to the broader community.
Companies like Google, Microsoft, and Red Hat have made substantial contributions to the security of numerous open-source projects through various funding and resource allocation strategies.
Successful Initiatives Improving Open Source Security
Several successful initiatives demonstrate the positive impact of funding and community involvement on open-source security. The Core Infrastructure Initiative (CII) provides grants and support to critical open-source projects, improving their security posture. The OpenSSF’s Alpha-Omega project focuses on automating security testing and vulnerability detection for widely used open-source projects. These initiatives highlight the power of collaborative efforts in improving the security of the open-source ecosystem.
The success of these projects underlines the importance of coordinated funding and active community engagement in enhancing the security of open-source software.
Epilogue
Ultimately, the security of open-source software is a shared responsibility. It’s not just about developers writing secure code; it’s about a collective commitment from everyone involved – developers, users, maintainers, and funders – to prioritize security at every stage of the software lifecycle. By understanding the roles and responsibilities of each stakeholder, and by fostering a culture of collaboration and transparency, we can significantly improve the security of the open-source software that underpins our digital world.
Let’s work together to build a more secure future, one line of code at a time!
Common Queries
What are the common types of vulnerabilities found in open-source software?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure authentication, and denial-of-service (DoS) attacks. Many are related to outdated libraries or insecure coding practices.
How can I contribute to open-source security?
Even without coding skills, you can contribute! Report vulnerabilities you find, participate in code reviews, donate to projects you rely on, or simply spread awareness about open-source security best practices.
What are the legal implications of using insecure open-source components?
Using insecure components can expose your organization to legal liabilities, especially if a breach occurs. It’s crucial to understand the licenses and potential risks associated with the open-source software you integrate into your applications.