Why Offer Monthly Security Reports?
Why offer monthly security reports? Because in today’s digital landscape, proactive security isn’t just a good idea—it’s a necessity. Imagine the peace of mind knowing you’re consistently monitoring for vulnerabilities, addressing threats before they become major incidents, and building unshakeable trust with your clients. This isn’t just about ticking boxes; it’s about forging stronger relationships, saving money in the long run, and ultimately, protecting your business and your clients’ data.
Regular security reports offer a powerful way to demonstrate your commitment to robust security. They showcase your proactive approach, allowing you to identify and mitigate risks before they escalate into costly breaches. This transparency builds confidence, fostering stronger client relationships and showcasing your expertise. The data presented—from vulnerability assessments to incident response times—provides concrete evidence of your dedication to security, all while enabling continuous improvement and compliance with industry standards.
Business Value Proposition of Monthly Security Reports
Regular security reports offer a proactive approach to cybersecurity, shifting the focus from reactive damage control to preventative risk mitigation. This proactive strategy not only reduces financial losses but also significantly enhances client trust and overall business resilience. By providing a clear and concise overview of your security posture, monthly reports empower businesses to make informed decisions and stay ahead of potential threats.
The tangible benefits of receiving monthly security reports are numerous. Improved risk management is paramount. These reports provide a detailed snapshot of your security landscape, highlighting vulnerabilities and potential threats before they can be exploited. This allows for timely remediation, minimizing the impact of any security incidents. For example, a monthly report might reveal an outdated software version posing a significant vulnerability.
Addressing this proactively prevents a potential breach, saving time, money, and reputational damage.
Enhanced Client Trust and Confidence
Regular reports demonstrate a commitment to robust security practices. Transparency builds trust. Clients appreciate the proactive approach and the detailed information provided, fostering confidence in the organization’s ability to protect sensitive data. Knowing that their data is actively monitored and protected reassures clients and strengthens business relationships. This enhanced trust can lead to increased client retention and improved business opportunities.
For instance, a financial institution regularly providing security reports to its clients can demonstrate its commitment to data privacy and compliance, thus retaining and attracting high-value clients.
Case Study: Proactive Threat Mitigation
A mid-sized e-commerce company implemented monthly security reports. One report highlighted a suspicious increase in login attempts from an unusual geographic location. This anomaly, quickly identified through the report’s detailed logging analysis, triggered an immediate investigation. The investigation revealed a sophisticated phishing campaign targeting employee credentials. By proactively addressing this threat, the company prevented a data breach, avoided significant financial losses, and protected its customers’ personal information.
The timely response, facilitated by the monthly report, prevented a potentially catastrophic security incident.
Cost Comparison: Reactive vs. Proactive Security
The cost-effectiveness of proactive security measures, as facilitated by monthly security reports, is undeniable. Reactive measures, taken after a breach occurs, are significantly more expensive. The following table illustrates this:
| Measure | Reactive Cost | Proactive Cost (with monthly reports) | Cost Savings |
|---|---|---|---|
| Incident Response | $50,000 – $1,000,000+ (depending on severity) | $500 – $2,000 (per month) | Significant reduction in potential losses |
| Data Recovery | $10,000 – $50,000+ | Minimal (proactive backups and mitigation) | Near-total avoidance of recovery costs |
| Reputational Damage | Priceless (loss of customers, legal fees) | Reduced (proactive measures build trust) | Significant reduction in reputational damage |
| Regulatory Fines | Varies widely (potentially millions) | Reduced risk of non-compliance | Significant reduction in potential fines |
Demonstrating Proactive Security Posture with Reports
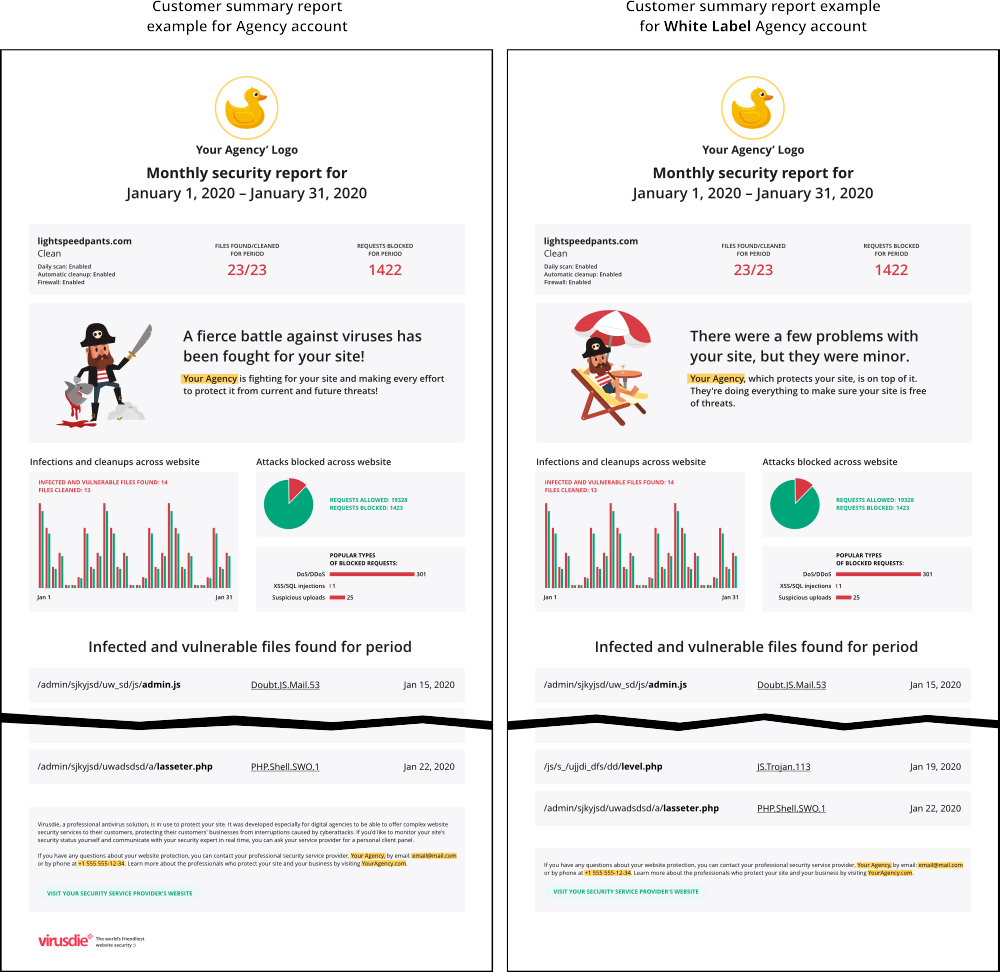
Monthly security reports aren’t just about reacting to breaches; they’re a powerful tool for showcasing your organization’s proactive approach to cybersecurity. By consistently delivering these reports, you demonstrate a commitment to ongoing risk mitigation and a robust security posture to stakeholders, clients, and even potential investors. This proactive stance builds trust and confidence in your organization’s ability to handle security challenges.Regular, comprehensive security reports are the cornerstone of demonstrating a proactive security posture.
They offer concrete evidence of your commitment to identifying and mitigating risks before they escalate into significant incidents. The information presented needs to be clear, concise, and easily understandable, even for those without a deep technical background. This allows you to communicate the effectiveness of your security measures in a way that resonates with a broad audience.
Key Elements of a Comprehensive Monthly Security Report
A truly effective monthly security report goes beyond simply listing incidents. It should provide a holistic view of your security landscape, including key metrics, proactive measures undertaken, and any vulnerabilities identified and addressed. This allows stakeholders to gauge the overall health of your security infrastructure and the effectiveness of your security team. The report should be structured for easy navigation and comprehension, perhaps using clear visuals like charts and graphs to present complex data.
It should also include an executive summary highlighting the most important findings and actions taken.
Presentation of Vulnerability Assessments and Penetration Testing Results
Vulnerability assessments and penetration testing are crucial proactive measures. The monthly report should clearly present the findings of these assessments, detailing the number of vulnerabilities identified, their severity (using a standardized scale like CVSS), and the timeline for remediation. A summary table showing the number of critical, high, medium, and low-severity vulnerabilities discovered during the month, along with the percentage remediated, provides a quick overview of progress.
For penetration testing, the report should highlight any successful exploits and the associated risks, along with the implemented countermeasures. This transparency showcases your organization’s commitment to rigorous security testing and its ability to respond effectively to potential threats.
Sample Report Section: Vulnerability Explanation and Remediation
Let’s imagine a vulnerability was discovered in a web application. A section of the report might look like this:
| Vulnerability | Severity | Description | Remediation Steps | Status |
|---|---|---|---|---|
| SQL Injection Vulnerability | Critical | A flaw in the input validation of a user registration form allows malicious SQL code to be executed, potentially leading to database compromise. | Implemented parameterized queries and input sanitization. Updated the application’s security framework. Performed post-remediation testing. | Remediated |
This structured approach provides a clear and concise overview of the identified vulnerability, its severity, the actions taken to address it, and the current status.
Regularly Monitored Security Threats
The following security threats are regularly monitored and reported on:
The report’s threat monitoring section offers valuable insight into the ever-evolving threat landscape and the organization’s proactive efforts to stay ahead of potential attacks. This demonstrates a commitment to staying informed and adapting security measures to counter emerging threats.
- Malware infections
- Phishing attempts
- Denial-of-service (DoS) attacks
- Insider threats
- Vulnerabilities in software and hardware
- Data breaches
- Network intrusions
- Social engineering attacks
Building Client Relationships Through Transparency: Why Offer Monthly Security Reports
Regular, transparent communication is paramount in building trust and fostering strong, long-lasting client relationships. Monthly security reports offer a powerful tool for achieving this, demonstrating your commitment to their security and providing valuable insights into your proactive approach. By consistently delivering these reports, you cultivate a sense of partnership and shared responsibility for maintaining a robust security posture.Consistent communication, facilitated by monthly security reports, strengthens client relationships by providing a clear and regular update on the security landscape and your organization’s efforts to mitigate risks.
This proactive approach fosters trust and demonstrates a commitment to client well-being that extends beyond simply fulfilling contractual obligations. Clients appreciate the peace of mind that comes with knowing they’re kept informed and that their security is a top priority.
Communication Channels for Monthly Security Reports
Choosing the right communication channel is crucial for effective report delivery. Email remains a reliable option, particularly for concise summaries. However, for more detailed reports and interactive data visualization, a dedicated client portal offers significant advantages. A portal allows for secure access, version control, and the possibility of integrating additional security tools and resources. The best approach often involves a hybrid model, using email for brief updates and notifications and the portal for in-depth analysis and historical data.
Report Formats and Client Engagement
The format of your monthly security reports significantly influences client engagement. A concise summary, delivered via email, is ideal for busy clients who need a quick overview of key security events and actions taken. This format should highlight critical findings and actionable insights. A detailed analysis, accessible via a client portal, caters to clients who require a deeper dive into the data, including technical specifics and detailed explanations of vulnerabilities and mitigation strategies.
This more in-depth approach allows for a more thorough understanding and fosters a stronger sense of collaboration. For example, a concise summary might simply state “Successful mitigation of a phishing attempt targeting 15 employees,” while the detailed analysis would include specifics like the phishing technique used, the number of employees who clicked the link, and the remediation steps taken.
Tailoring Reports to Client Needs
Effective communication requires tailoring your message to your audience. Monthly security reports should be customized to reflect each client’s specific needs and technical understanding. A client with a strong internal security team might appreciate a highly technical report focusing on specific vulnerabilities and remediation efforts. In contrast, a client with limited technical expertise might benefit from a simpler report that focuses on high-level summaries and actionable recommendations.
For example, one client might receive a report detailing specific CVEs and their associated risk scores, while another might receive a report explaining the steps taken to protect their data from ransomware attacks in plain language. This personalized approach ensures that every client receives information that is both relevant and easily understandable.
Using Reports for Continuous Improvement and Compliance
Monthly security reports aren’t just snapshots of your current security posture; they’re powerful tools for continuous improvement and demonstrating compliance. By analyzing the data within these reports, you can identify emerging threats, refine your security strategies, and proactively address potential vulnerabilities before they become significant problems. This proactive approach not only strengthens your overall security but also demonstrates a commitment to best practices and regulatory adherence.Analyzing monthly reports allows for the identification of trends and patterns in security incidents, system performance, and user behavior.
This data-driven approach enables more effective resource allocation and prioritization of security improvements. For instance, a consistent spike in phishing attempts targeting a specific department might indicate a need for more focused security awareness training for that team. Similarly, a gradual increase in failed login attempts from a particular geographic location could suggest a potential brute-force attack in progress.
By tracking these trends over time, organizations can anticipate and mitigate future risks more effectively.
Compliance Demonstration with Security Reports
Monthly security reports serve as invaluable documentation for demonstrating compliance with various industry regulations and standards, such as GDPR, HIPAA, PCI DSS, and ISO 27001. These reports provide concrete evidence of your organization’s commitment to data protection, security controls, and regulatory requirements. Specific metrics and logs within the reports can be used to support audits and demonstrate adherence to specific clauses within these regulations.
For example, a report showing consistent monitoring of access logs, regular vulnerability scans, and timely patching activities can readily demonstrate compliance with access control and vulnerability management requirements mandated by various standards. The detailed nature of these reports provides the auditor with a clear picture of your security posture and the measures in place to maintain compliance.
Hypothetical Compliance Issue and Corrective Actions
Let’s imagine a scenario where a monthly security report flagged a critical vulnerability in a web application used for processing customer payments. The report highlighted that the application lacked sufficient encryption, potentially violating PCI DSS requirements. Upon investigation, the security team confirmed the vulnerability. The corrective action plan involved immediately implementing stronger encryption protocols, patching the application, and conducting thorough penetration testing to validate the fix.
The report also triggered a review of the vulnerability management process to identify any weaknesses that allowed this vulnerability to persist for so long. The subsequent monthly reports demonstrated the successful remediation of the vulnerability and the improvements made to the vulnerability management process, providing clear evidence of proactive problem-solving and a commitment to compliance.
Key Performance Indicators (KPIs) for Security Progress
Regularly tracking and reporting on key performance indicators (KPIs) is crucial for demonstrating continuous improvement in security posture. These KPIs provide quantifiable metrics that showcase progress and highlight areas requiring further attention.
The following KPIs are commonly tracked and reported:
- Number of security incidents detected and resolved
- Average time to resolve security incidents
- Number of vulnerabilities identified and remediated
- Percentage of systems patched against known vulnerabilities
- Number of successful phishing attempts
- Number of security awareness training completed by employees
- Compliance status against relevant industry standards (e.g., percentage of requirements met)
- Average time to detect and respond to security incidents
Visual Representation of Security Data in Reports
Effective communication of security data is crucial for understanding risk levels and driving proactive security measures. Monthly security reports should go beyond simply listing numbers; they need to present complex information in a clear, concise, and visually appealing manner. This allows stakeholders to quickly grasp key insights and make informed decisions.Charts and graphs are invaluable tools for achieving this.
They transform raw data into easily digestible visuals, highlighting trends and patterns that might otherwise be missed in lengthy text-based reports. The right chart type can significantly enhance understanding and engagement with the report.
Chart Types for Security Metrics
Choosing the appropriate chart type is vital for effective data representation. Different chart types are better suited for different kinds of security data. For instance, bar charts are excellent for comparing discrete values, such as the number of vulnerabilities across different systems or the count of security incidents by category. Line charts, on the other hand, are ideal for showing trends over time, such as the number of successful login attempts or the evolution of incident response times.
Pie charts effectively illustrate proportions, for example, the distribution of vulnerability severity levels. Finally, scatter plots can reveal correlations between two variables, like the relationship between the number of patches applied and the number of successful attacks.
Example: Security Incidents Over Three Months, Why offer monthly security reports
The following chart illustrates the number of security incidents detected and resolved over a three-month period (January, February, March).[Descriptive Text:] This bar chart displays the number of security incidents detected and resolved each month. The blue bars represent detected incidents, while the orange bars represent resolved incidents. A quick glance reveals a spike in detected incidents in February, followed by a successful resolution effort in March.
This visualization immediately highlights periods of higher risk and the effectiveness of incident response. The chart uses clear labels for the x-axis (Month) and y-axis (Number of Incidents), ensuring easy interpretation.“`+—————–+——-+——-+——-+| Month | Jan | Feb | Mar |+—————–+——-+——-+——-+| Incidents Detected| 10 | 25 | 15 || Incidents Resolved| 12 | 22 | 28 |+—————–+——-+——-+——-+“`(Note: This is a textual representation of a bar chart.
Imagine a bar chart where the x-axis shows Jan, Feb, Mar, and the y-axis shows the number of incidents. Two bars per month represent detected and resolved incidents, respectively. Blue bars for detected, orange bars for resolved.)
Using Color-Coding and Visual Cues
Strategic use of color-coding and visual cues significantly enhances the readability and impact of the reports. For instance, using red for critical vulnerabilities, yellow for medium, and green for low severity levels provides an immediate understanding of risk levels without needing to read lengthy descriptions. Similarly, using different shades of a color to represent different ranges of values can improve the visual clarity of charts.
Highlighting key data points with arrows or callouts can draw attention to critical information, and using clear and consistent legends helps ensure that the visual representations are easy to interpret. Furthermore, the use of icons to represent different types of security events can further improve the clarity and accessibility of the report. Consider using a consistent color scheme and font throughout the report to maintain visual consistency and enhance readability.
Summary
Ultimately, offering monthly security reports isn’t just about compliance; it’s about building a culture of proactive security that benefits both your business and your clients. By embracing transparency, showcasing your expertise, and continuously improving your security posture, you not only mitigate risk but also strengthen relationships and foster trust. The investment in proactive security, as demonstrated by these regular reports, ultimately pays for itself through cost savings and enhanced reputation.
Essential Questionnaire
What if my clients don’t understand the technical details in the report?
Tailor the reports to your clients’ technical understanding. Offer different formats – concise summaries for less technical clients and detailed analyses for those who want more in-depth information.
How often should I update the report template?
Regularly review and update your report template to reflect changes in your security practices, industry best practices, and client needs. Annual reviews are a good starting point.
What if a report reveals a significant vulnerability?
Have a clear process for addressing vulnerabilities. Prioritize critical issues immediately and communicate promptly with the client about the issue and the remediation steps being taken.
How can I measure the effectiveness of my monthly security reports?
Track key performance indicators (KPIs) like the number of vulnerabilities identified and remediated, incident response times, and client satisfaction. Regularly analyze these metrics to assess the impact of your reports and refine your approach.