Why Patch Management Is Important and How to Get It Right
Why patch management is important and how to get it right? It’s a question every tech-savvy individual, and especially every business owner, should be asking. In today’s interconnected world, neglecting regular patching is like leaving your front door unlocked – inviting trouble. This post dives into the critical importance of patch management, exploring the devastating consequences of ignoring it and outlining a practical strategy to ensure your systems remain secure and your data protected.
We’ll look at real-world examples, explore different tools, and address common challenges you might face along the way. Get ready to bolster your digital defenses!
From understanding the types of vulnerabilities patches address to implementing a robust patch management strategy, we’ll cover everything you need to know to protect your systems from cyber threats. We’ll discuss the financial implications of security breaches, delve into the lifecycle of vulnerabilities, and examine the role of patch management in meeting industry compliance standards. We’ll also explore the various tools and technologies available to simplify the process, and provide tips for overcoming common challenges like resistance to patching and dealing with legacy systems.
The Importance of Patch Management
Patch management is often overlooked, yet it’s a cornerstone of robust cybersecurity. Failing to implement a comprehensive patch management strategy leaves your systems vulnerable to a wide range of threats, from minor inconveniences to catastrophic data breaches. Understanding the potential consequences and implementing effective strategies is crucial for any organization, regardless of size.
Potential Consequences of Neglecting Patch Management
Neglecting patch management exposes your systems to known vulnerabilities. These vulnerabilities are essentially open doors for malicious actors, allowing them to gain unauthorized access to sensitive data, disrupt operations, and potentially cripple your entire infrastructure. This can range from simple malware infections to sophisticated attacks exploiting zero-day vulnerabilities before patches are even available. The consequences can extend beyond technical issues, impacting reputation, legal compliance, and ultimately, your bottom line.
Financial Impact of Security Breaches
The financial repercussions of a security breach stemming from inadequate patch management can be staggering. Costs include not only the direct expenses of remediation—such as hiring cybersecurity experts, restoring data, and notifying affected individuals—but also indirect costs like lost productivity, reputational damage leading to customer churn, legal fees, and potential fines for non-compliance with regulations like GDPR or CCPA.
The average cost of a data breach continues to rise annually, highlighting the critical need for proactive patch management. A single breach can cost millions, potentially bankrupting smaller organizations.
Real-World Incidents Caused by Inadequate Patch Management
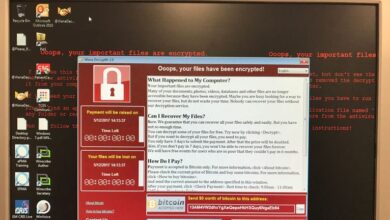
Numerous high-profile incidents demonstrate the devastating consequences of neglecting patch management. The NotPetya ransomware attack in 2017, for instance, spread rapidly through unpatched systems, causing billions of dollars in damage globally. Similarly, the WannaCry ransomware attack in 2017 exploited a known vulnerability in older versions of Microsoft Windows, crippling hospitals and other organizations worldwide. These events highlight the far-reaching and potentially catastrophic impact of failing to apply timely security updates.
Prioritizing Patches Based on Criticality and Risk
Effective patch management isn’t just about applying every patch as soon as it’s released; it’s about prioritizing them based on their potential impact. A risk-based approach involves assessing the criticality of each vulnerability and the likelihood of exploitation. Patches addressing critical vulnerabilities that could lead to significant data breaches or system outages should be prioritized over less critical ones.
Factors to consider include the severity of the vulnerability, the likelihood of exploitation, the value of the affected asset, and the potential impact of a successful attack.
Cost Comparison: Patching vs. Security Breaches
The following table compares the cost of proactive patching with the potential cost of a security breach resulting from neglecting patch management. These figures are estimates and can vary widely depending on factors like the size and type of organization, the nature of the breach, and the regulatory landscape.
| Cost Category | Proactive Patching | Security Breach (Low Impact) | Security Breach (High Impact) |
|---|---|---|---|
| Software/Tools | $5,000 – $20,000 per year | $50,000 – $100,000 | $1,000,000 – $5,000,000+ |
| Personnel | $10,000 – $50,000 per year | $100,000 – $500,000 | $500,000 – $10,000,000+ |
| Downtime | Minimal | $10,000 – $100,000 | $100,000 – $1,000,000+ |
| Legal/Regulatory | Negligible | $10,000 – $50,000 | $500,000 – $10,000,000+ |
| Reputation Damage | Negligible | $20,000 – $200,000 | $1,000,000 – $50,000,000+ |
Vulnerabilities and Exploits
Software vulnerabilities are weaknesses in the design, implementation, operation, or internal controls of a system. These weaknesses can be exploited by attackers to gain unauthorized access, disrupt services, or steal data. Understanding these vulnerabilities and how they’re exploited is crucial for effective patch management.
Attackers constantly seek out these vulnerabilities to compromise systems. They use a variety of techniques, ranging from simple automated scans to sophisticated, targeted attacks. The success of these attacks often hinges on whether or not the software in question has been patched to address known vulnerabilities.
Common Software Vulnerabilities
Many types of software vulnerabilities exist, each posing different risks. Patches are designed to mitigate these risks by fixing the underlying code flaws. Ignoring these patches leaves your systems vulnerable to attack.
- Buffer Overflow: Occurs when a program attempts to write data beyond the allocated buffer size, potentially overwriting adjacent memory regions and leading to crashes or arbitrary code execution. This is a classic vulnerability.
- SQL Injection: Allows attackers to inject malicious SQL code into database queries, potentially granting access to sensitive data or allowing modification of database structures. This is often exploited through poorly sanitized user inputs.
- Cross-Site Scripting (XSS): Enables attackers to inject malicious scripts into websites viewed by other users. This can lead to session hijacking, data theft, or redirection to malicious websites.
- Cross-Site Request Forgery (CSRF): Tricks users into performing unwanted actions on a website they’re already authenticated to. This can be used to perform actions like transferring funds or changing account settings without the user’s knowledge.
- Denial of Service (DoS): Overwhelms a system with traffic, rendering it unavailable to legitimate users. Distributed Denial of Service (DDoS) attacks use multiple compromised systems to amplify the attack.
- Remote Code Execution (RCE): Allows an attacker to execute arbitrary code on a target system, often granting complete control.
Exploitation of Unpatched Systems
Attackers actively search for unpatched systems using automated tools and intelligence gathering. Once a vulnerability is identified, various techniques are employed to exploit it.
The Vulnerability Lifecycle
Understanding the lifecycle of a vulnerability is key to proactive patch management. It typically involves:
- Discovery: A vulnerability is identified, either by a security researcher, a penetration tester, or an attacker.
- Disclosure: The vulnerability is reported to the vendor (responsible party) – often privately initially.
- Patch Development: The vendor develops and tests a patch to address the vulnerability.
- Release: The patch is released to the public.
- Deployment: Organizations deploy the patch to their systems.
- Exploitation: Attackers may attempt to exploit the vulnerability before or after a patch is released.
Common Vulnerability Types and Associated Risks
The table below summarizes different vulnerability types and their associated risks. Understanding these risks is crucial for prioritizing patching efforts.
| Vulnerability Type | Risk Level | Impact | Example |
|---|---|---|---|
| SQL Injection | High | Data breach, data modification | Compromised database credentials, data theft |
| Cross-Site Scripting (XSS) | Medium to High | Session hijacking, data theft, phishing | Malicious script execution in a web browser |
| Remote Code Execution (RCE) | Critical | Complete system compromise | Unrestricted access and control of the system |
| Denial of Service (DoS) | Medium to High | Service disruption, loss of availability | Website or application becomes inaccessible |
Implementing a Patch Management Strategy
Successfully patching your systems requires more than just downloading and installing updates. A robust strategy is crucial for minimizing vulnerabilities and ensuring business continuity. This involves careful planning, execution, and ongoing monitoring to effectively manage the patching lifecycle across your entire IT infrastructure.
A well-defined patch management process is the cornerstone of a secure IT environment. It streamlines the process of identifying, testing, deploying, and verifying software updates, reducing the window of vulnerability and minimizing the risk of exploitation. This section Artikels the key components of such a process and the steps involved in its successful implementation.
Key Components of a Robust Patch Management Process
Several critical elements contribute to a robust patch management process. These elements work together to ensure that your systems are consistently protected against known vulnerabilities. A lack in any one area can significantly weaken the overall effectiveness of your strategy.
- Vulnerability Scanning and Assessment: Regularly scanning your systems for vulnerabilities is the first step. This identifies which patches are needed and prioritizes them based on severity and risk.
- Patch Prioritization: Not all patches are created equal. Prioritization is crucial, focusing on critical vulnerabilities first, those with known exploits or those impacting essential systems.
- Patch Testing and Staging: Before widespread deployment, thoroughly test patches in a controlled environment (e.g., a staging server) to identify and resolve any unforeseen issues or conflicts.
- Deployment and Rollout: Implement a phased rollout strategy, starting with pilot deployments to a small subset of systems before wider deployment to minimize disruption and allow for rapid identification of problems.
- Verification and Reporting: After deployment, verify that the patches have been successfully applied and generate reports to track the progress and effectiveness of your patch management efforts.
- Change Management: Formal change management processes are essential to ensure that patch deployments are properly documented, approved, and tracked, minimizing the risk of unintended consequences.
Steps Involved in Deploying Patches Across a Network, Why patch management is important and how to get it right
Deploying patches effectively requires a structured approach. This minimizes downtime and ensures consistent application across all systems. A poorly planned rollout can lead to significant disruption and security risks.
- Identify and Prioritize Patches: Use vulnerability scanning tools to identify critical vulnerabilities and prioritize patches accordingly.
- Test Patches in a Staging Environment: Simulate a real-world environment to check for compatibility and potential issues before deploying to production systems.
- Schedule Deployment: Plan deployments during off-peak hours to minimize disruption to users and business operations.
- Deploy Patches Using Automated Tools: Employ automated tools (e.g., SCCM, Puppet, Chef) for efficient and consistent deployment across multiple systems.
- Monitor Deployment Progress: Track the deployment status in real-time and address any issues that may arise during the process.
- Verify Patch Installation: After deployment, confirm successful installation and address any failed deployments promptly.
Methods for Testing Patches Before Widespread Deployment
Testing patches before full deployment is crucial for minimizing the risk of unforeseen problems. This includes functional testing and impact analysis to ensure the patch doesn’t negatively affect other systems or applications.
- Pilot Deployment: Deploy the patch to a small group of systems to identify and resolve any issues before widespread rollout.
- Sandbox Testing: Test the patch in a completely isolated environment that mirrors the production environment to ensure compatibility and functionality without affecting live systems.
- Regression Testing: Verify that the patch doesn’t introduce new bugs or negatively impact the functionality of existing systems or applications.
The Importance of Communication and Training for Successful Patch Management
Effective communication and training are essential for a successful patch management program. Keeping stakeholders informed and ensuring staff are adequately trained minimizes disruptions and maximizes adoption.
- Communicate Patch Schedules: Inform users about planned downtime and patch deployments in advance to manage expectations and minimize disruption.
- Provide Training on Patch Management Procedures: Train IT staff on the patch management process, including vulnerability scanning, patch testing, and deployment techniques.
- Establish Clear Communication Channels: Set up communication channels for reporting issues and receiving updates during and after patch deployments.
Patch Management Lifecycle Flowchart
Start –> Vulnerability Scanning –> Patch Identification & Prioritization –> Patch Testing –> Deployment Approval –> Patch Deployment –> Verification & Reporting –> Documentation & Archiving –> End
Tools and Technologies for Patch Management: Why Patch Management Is Important And How To Get It Right

Effective patch management relies heavily on the right tools and technologies. Choosing the appropriate solution can significantly impact your organization’s security posture and operational efficiency. The market offers a wide range of options, from simple, manual approaches to sophisticated, automated systems. Understanding the features and capabilities of different solutions is crucial for making an informed decision.
Patch Management Software Solutions Comparison
Several vendors offer patch management software, each with its own strengths and weaknesses. These solutions vary in their approach, scalability, and integration capabilities. Some focus on specific operating systems or applications, while others offer broader coverage. Factors like the size of your IT infrastructure, budget constraints, and the level of automation desired will influence your choice. For example, a small business might find a simpler, less expensive solution sufficient, while a large enterprise with a complex IT environment would likely require a more robust and scalable system.
Key differences lie in the breadth of supported systems (Windows, Linux, macOS, network devices, applications), reporting capabilities, and the level of automation offered.
Features to Look for in Patch Management Tools
When evaluating patch management tools, several key features should be considered. Robust reporting and analytics are essential for tracking patch deployment progress, identifying vulnerabilities, and demonstrating compliance. Centralized management simplifies the process of patching numerous devices and systems from a single console. Automated patching reduces the risk of human error and significantly speeds up the deployment process.
Integration with existing IT infrastructure, such as ticketing systems and monitoring tools, streamlines workflows and improves overall efficiency. Strong security features, including encryption and access controls, are critical to protecting sensitive data. Finally, the ability to schedule patches to minimize disruption during peak operating hours is a valuable feature.
Automated Versus Manual Patch Management
The choice between automated and manual patch management depends largely on your organization’s resources and risk tolerance. Manual patching, while less expensive upfront, is time-consuming, error-prone, and often leads to delayed patch deployment, increasing vulnerability exposure. Automated systems, on the other hand, offer significant advantages in terms of speed, efficiency, and consistency. They can automatically scan for vulnerabilities, download patches, and deploy them to target systems with minimal human intervention.
While the initial investment in automated solutions is higher, the long-term benefits in terms of reduced risk and improved efficiency often outweigh the costs. The reduction in human error alone justifies the investment for larger organizations.
Successful Patch Management Implementations
Successful patch management implementations are characterized by a well-defined strategy, appropriate tools, and consistent execution. In the healthcare industry, for example, automated patch management is critical for protecting sensitive patient data and complying with HIPAA regulations. Financial institutions rely on robust patch management to safeguard customer information and prevent fraud. Similarly, in the manufacturing sector, secure patch management is vital for maintaining operational continuity and preventing disruptions caused by cyberattacks.
These successful implementations demonstrate the importance of integrating patch management into a broader cybersecurity strategy.
Comparison of Patch Management Tools
| Feature | ManageEngine Patch Manager Plus | Microsoft Endpoint Manager | Ivanti Patch My PC |
|---|---|---|---|
| Operating Systems Supported | Windows, Linux, macOS | Windows, macOS, iOS, Android | Windows |
| Automation Capabilities | High | High | Medium |
| Reporting & Analytics | Comprehensive | Comprehensive | Good |
| Pricing | Subscription-based, tiered pricing | Subscription-based, tiered pricing | Subscription-based, tiered pricing |
Compliance and Auditing
Patch management isn’t just about keeping your systems secure; it’s a crucial component of meeting various industry regulations and demonstrating responsible IT practices. Failing to maintain a robust patch management program can lead to hefty fines, legal repercussions, and reputational damage. Effective auditing ensures your efforts are not only meeting but exceeding expectations.Effective patch management plays a vital role in ensuring compliance with numerous industry standards and regulations.
A well-documented and consistently applied patch management strategy provides verifiable evidence of your organization’s commitment to security, a key requirement for many compliance frameworks. Regular audits help identify weaknesses in your processes and ensure continuous improvement.
Industry Compliance Standards and Patch Management
Many compliance frameworks explicitly address the importance of vulnerability management, which is intrinsically linked to patch management. Meeting these standards often requires demonstrating a proactive approach to identifying, assessing, and mitigating vulnerabilities through timely patching. Failure to do so can result in non-compliance and potential penalties.
Methods for Auditing Patch Management Effectiveness
Auditing your patch management effectiveness involves a multi-faceted approach. This includes regularly reviewing patch deployment logs, comparing them against vulnerability scan results, and assessing the overall time taken to deploy critical patches. Automated tools can greatly assist in this process, providing detailed reports and highlighting areas needing improvement. Manual spot checks should also be performed to verify the accuracy of automated reports and identify any potential gaps.
Maintaining Accurate Records of Patch Deployments
Maintaining accurate and detailed records of patch deployments is paramount for both security and compliance. These records serve as crucial evidence during audits, demonstrating your adherence to security policies and regulatory requirements. The records should include the date and time of deployment, the specific patches applied, the systems affected, and any encountered issues. This information should be readily accessible and easily searchable.
Examples of Compliance Regulations Related to Patch Management
- HIPAA (Health Insurance Portability and Accountability Act): Requires robust security measures to protect patient health information, including timely patching of systems handling such data.
- PCI DSS (Payment Card Industry Data Security Standard): Mandates regular vulnerability scanning and patching of systems processing credit card information.
- GDPR (General Data Protection Regulation): While not explicitly mentioning patching, GDPR emphasizes data security, and timely patching is a crucial aspect of maintaining data integrity and confidentiality.
- NIST Cybersecurity Framework: Provides a voluntary framework for improving cybersecurity, with patching being a key element of its identify, protect, detect, respond, and recover functions.
Creating a Patch Deployment Status and Compliance Report
A comprehensive report should summarize the status of your patch deployments and demonstrate your compliance with relevant regulations. This report should be easily understandable by both technical and non-technical audiences.
Patch Deployment Status Report – October 26, 2024
Total Systems: 500
Systems Fully Patched: 485 (97%)
Systems Partially Patched: 10 (2%)
Systems Requiring Attention: 5 (1%)
Critical Patches Applied (within 24 hours of release): 100%
High-Severity Patches Applied (within 72 hours of release): 98%
Average Patch Deployment Time: 12 hours
Compliance Status: Compliant with PCI DSS and HIPAA requirements. Further investigation required for systems requiring attention.
Report Generated: October 26, 2024
Addressing Patch Management Challenges
Implementing a robust patch management strategy isn’t always smooth sailing. Organizations frequently encounter hurdles that can hinder their efforts to maintain secure and up-to-date systems. Understanding these challenges and developing effective mitigation strategies is crucial for success. This section explores common obstacles and offers practical solutions.
Resistance to Patching
Overcoming resistance to patching is a significant challenge. This resistance stems from various sources, including fear of downtime, disruption to workflows, and a lack of understanding of the risks associated with unpatched systems. Effective communication is key. Highlighting the potential consequences of security breaches, emphasizing the importance of proactive security measures, and clearly demonstrating the minimal disruption caused by well-planned patching can significantly reduce resistance.
Furthermore, providing training and support to users can help alleviate concerns and foster a culture of security awareness. A phased rollout approach, starting with non-critical systems, can also help build confidence and demonstrate the process’s efficacy.
Patching Legacy Systems
Patching legacy systems presents unique difficulties. These systems often lack robust patching mechanisms, have limited compatibility with modern patching tools, and may require significant testing to ensure compatibility and functionality after patching. A phased approach, prioritizing critical security patches, is crucial. Consider employing virtualization or containerization to isolate legacy systems, minimizing the risk of disruption to the overall infrastructure.
Careful planning, thorough testing, and potentially engaging specialized expertise for legacy system support are essential for successful patching.
Minimizing Downtime During Patch Deployment
Minimizing downtime during patch deployment is paramount for maintaining business continuity. Strategies include employing change management processes, scheduling patches during off-peak hours, and using techniques like blue-green deployments or rolling updates. Blue-green deployments involve deploying the patched system to a separate environment (the “blue” environment) and then switching traffic to the new environment once testing is complete. Rolling updates involve patching servers sequentially, minimizing the impact on overall service availability.
Thorough testing before deployment is critical to avoid unexpected issues that can cause extended downtime. Regularly scheduled patching windows, communicated in advance, also help minimize disruption.
Common Patch Management Challenges, Causes, and Solutions
| Challenge | Cause | Solution | Example |
|---|---|---|---|
| High Downtime During Patching | Poorly planned patching schedules, insufficient testing, lack of rollback plan | Implement robust change management processes, schedule patches during off-peak hours, utilize blue-green deployments or rolling updates, thorough testing | Scheduling patches during the weekend to minimize impact on business operations. |
| Resistance from End-Users | Lack of awareness of security risks, fear of application disruption, inconvenient patching schedules | Improved communication, user training, phased rollout, clear explanation of benefits, incentivizing timely patching | Providing training on the importance of patching and offering rewards for timely compliance. |
| Difficulty Patching Legacy Systems | Lack of support for modern patching tools, incompatibility with new updates, risk of system instability | Prioritize critical patches, utilize virtualization or containerization, engage specialized expertise, thorough testing | Creating a virtualized environment for testing patches on a legacy system before deployment to the production environment. |
| Lack of Visibility into Patch Status | Inefficient patch management tools, lack of centralized reporting, insufficient monitoring | Implement a centralized patch management system, utilize automated reporting and monitoring tools, establish clear reporting processes | Implementing a dashboard that provides real-time visibility into the patch status across the entire infrastructure. |
Epilogue
Securing your digital assets is a continuous journey, not a destination. Patch management is a cornerstone of this journey, a critical step in preventing costly and damaging security breaches. By understanding the importance of patching, implementing a robust strategy, and utilizing the right tools, you can significantly reduce your risk exposure. Remember, proactive patch management isn’t just about security; it’s about peace of mind, business continuity, and protecting your valuable data.
So, take charge, implement a solid patch management plan, and sleep soundly knowing your systems are protected.
FAQ Compilation
What happens if I don’t patch my systems?
Unpatched systems are vulnerable to malware, ransomware, and other cyberattacks. This can lead to data breaches, financial losses, reputational damage, and legal consequences.
How often should I patch my systems?
The frequency depends on the system and the criticality of the patches. Critical security patches should be applied as soon as possible, while others might have a longer deployment window. A well-defined patching schedule is essential.
What if a patch breaks something in my system?
Always test patches in a non-production environment before deploying them widely. Having a rollback plan in place is crucial to mitigate potential issues.
How can I automate my patch management process?
Several automated patch management tools are available. These tools can scan for missing patches, download and install updates, and monitor the process, reducing manual effort and improving efficiency.