
Malware Induction Windows & macOS via ISP
Malware induction into Windows and macOS devices via ISP is a chilling reality, a stealthy attack vector that leverages the very infrastructure we rely on for internet access. Imagine your internet provider, unknowingly or otherwise, becoming a conduit for malicious code to silently infiltrate your devices. This isn’t science fiction; it’s a sophisticated threat that exploits vulnerabilities in our networks and systems, leaving users vulnerable to data breaches, ransomware, and a host of other cybercrimes.
This post delves into the techniques used, the impact on different operating systems, and crucially, how you can protect yourself.
We’ll explore how DNS spoofing, compromised routers, and other sneaky methods are used to deliver malware. We’ll examine the different types of malware deployed – from ransomware crippling your files to spyware silently tracking your every keystroke. We’ll also compare the vulnerabilities of Windows and macOS systems, outlining the unique challenges each presents to attackers. Finally, we’ll equip you with practical steps to mitigate these threats and secure your digital life.
Vulnerability Vectors
ISP-level malware delivery represents a significant threat, exploiting the trust users place in their internet service providers. Attackers leverage the infrastructure’s reach and the inherent difficulties in securing vast networks to compromise numerous devices simultaneously. This approach often bypasses traditional endpoint security measures, making it particularly insidious.
DNS Spoofing and Redirection
DNS spoofing and redirection are among the most prevalent methods employed by malicious actors. By manipulating DNS records, attackers can redirect users to malicious websites, even if they type the correct URL. This works by poisoning the DNS cache of the user’s device or by intercepting DNS requests at the ISP level. For instance, an attacker might replace the legitimate DNS record for “example.com” with a malicious one, directing users to a site hosting malware instead of the intended website.
This often goes unnoticed by the user, as the URL in the browser address bar might appear correct. The effectiveness relies on the attacker gaining control of a DNS server or compromising the security of the DNS resolution process within the ISP network.
Compromised Routers and Network Equipment
Compromised routers and other network equipment within the ISP’s network provide a crucial foothold for attackers. Once a router is compromised, the attacker can monitor all traffic passing through it, inject malicious code into legitimate network traffic, and even redirect users to malicious sites. This is especially effective because routers often have less robust security measures compared to individual devices.
The scale of the compromise can be massive, affecting thousands of users simultaneously. A compromised router could, for example, silently install a keylogger on all connected devices, capturing sensitive information such as passwords and banking details.
Injection of Malicious Code into Legitimate Traffic
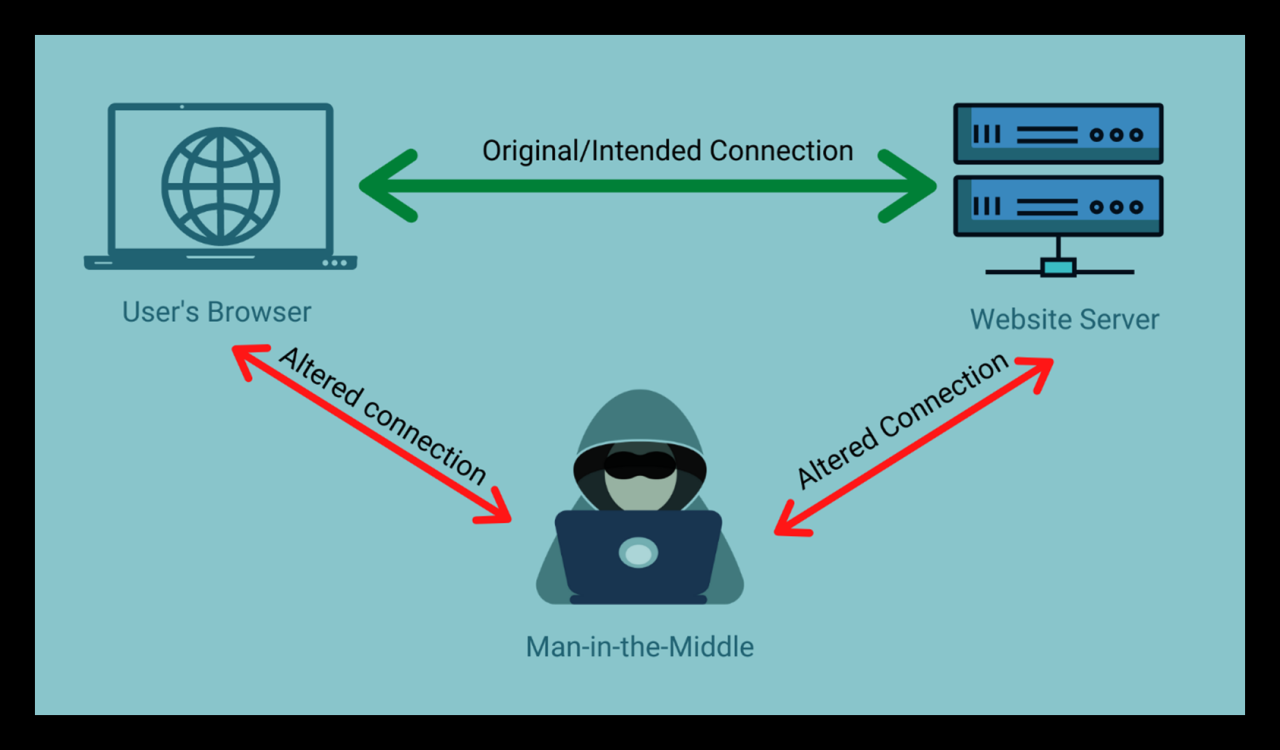
Several techniques exist for injecting malicious code into seemingly legitimate network traffic. One method involves using man-in-the-middle attacks to intercept and modify traffic between the user and the intended destination. This could involve altering web pages, inserting malicious JavaScript code, or replacing downloaded files with infected versions. Another method is to leverage vulnerabilities in network protocols to inject malicious packets into the data stream.
For example, an attacker might exploit a vulnerability in a specific protocol used by the ISP to inject a small payload containing malware into the user’s connection. This often remains undetected because it blends seamlessly with legitimate traffic.
Comparison of Attack Vectors
The success rate and mitigation strategies vary greatly depending on the specific attack vector.
| Attack Vector | Success Rate (Estimate) | Mitigation Strategies |
|---|---|---|
| DNS Spoofing/Redirection | High (dependent on DNS security) | DNSSEC, robust DNS filtering, use of secure DNS protocols (e.g., DoH, DoT) |
| Compromised Routers/Equipment | Moderate to High (dependent on router security) | Regular firmware updates, strong router passwords, intrusion detection systems within the ISP network |
| Malicious Code Injection | Low to Moderate (dependent on vulnerability exploitation) | Regular software updates, strong endpoint security, network intrusion detection/prevention systems |
Malware Types and Payload Delivery
ISP compromise opens a dangerous pathway for malware delivery, affecting both Windows and macOS systems. Understanding the types of malware deployed, their concealment methods, and activation triggers is crucial for effective defense. This section details the prevalent malware categories, their delivery mechanisms, and the infection process.
Malware delivered through compromised ISPs often leverages the trust inherent in the internet connection. Attackers exploit this trust to deliver payloads disguised within seemingly benign traffic, making detection difficult for standard security software. The payloads themselves can range from relatively simple information stealers to sophisticated ransomware and botnet components.
Prevalent Malware Types
Several malware categories are frequently delivered via compromised ISPs. Ransomware, designed to encrypt user data and demand a ransom for its release, is a major threat. Spyware, which secretly monitors user activity and steals sensitive information, is another common type. Botnets, networks of compromised computers controlled remotely by attackers, are often established through this method, used for various malicious activities like DDoS attacks or spam distribution.
These malicious programs are often tailored to exploit specific vulnerabilities in operating systems or applications.
Concealment of Malware Payloads
Attackers employ various techniques to hide malware within legitimate-looking traffic. One common method is to embed malicious code within seemingly harmless files, such as images or documents. Another technique involves using encrypted or obfuscated code, making it difficult for security software to identify the malicious content. The malware might also be hidden within seemingly legitimate websites, exploiting vulnerabilities to execute the payload without user interaction (drive-by downloads).
Traffic shaping and tunneling techniques might also be used to mask the malicious nature of the communication.
Malware Activation on Windows and macOS Devices
Once delivered, malware activation varies depending on the type and sophistication of the payload. Some malware may activate automatically upon download, while others require user interaction, such as opening a malicious attachment or clicking a malicious link. Exploit kits, collections of exploits targeting known vulnerabilities, are often used to automatically execute malware without user intervention. On Windows, this might involve exploiting vulnerabilities in Internet Explorer or other applications.
Thinking about how easily malware can sneak onto Windows and macOS devices through compromised ISPs got me pondering security at a higher level. It’s a scary thought, but building robust, secure applications is crucial, which is why I’ve been researching the advancements in application development, like what’s discussed in this article on domino app dev, the low-code and pro-code future.
Understanding these development methodologies might help create more secure apps, ultimately helping to combat the threat of malware infiltration via ISPs.
On macOS, vulnerabilities in older versions of Safari or other applications might be exploited. After activation, the malware establishes persistence, ensuring it remains active even after a reboot. This often involves adding registry entries (Windows) or launching agents at login (macOS).
Payload Delivery Methods
Drive-by downloads, where malware is automatically downloaded and executed without user interaction, are a common delivery method. This often involves exploiting vulnerabilities in web browsers or plugins. Exploit kits, pre-packaged collections of exploits, automate the process of finding and exploiting vulnerabilities. Phishing emails, containing malicious attachments or links, are also frequently used to deliver malware. Malicious advertisements on compromised websites can also lead to drive-by downloads.
The attackers might use various techniques to make these appear legitimate, such as mimicking trusted brands or creating convincing social engineering tactics.
Steps in a Typical Malware Infection Chain
The infection process through a compromised ISP typically follows a series of steps:
- Compromised ISP Infrastructure: Attackers gain access to the ISP’s network infrastructure, potentially through vulnerabilities in their systems or through insider threats.
- Traffic Manipulation: Attackers manipulate network traffic to inject malicious code into legitimate data streams or redirect users to malicious websites.
- Malware Delivery: The malware payload is delivered to the victim’s device, often disguised within seemingly legitimate traffic or through a drive-by download.
- Payload Execution: The malware is activated, either automatically or through user interaction, exploiting vulnerabilities in the operating system or applications.
- Malware Installation and Persistence: The malware installs itself on the victim’s device and establishes persistence, ensuring it remains active even after a reboot.
- Malicious Activity: The malware performs its malicious actions, such as encrypting files (ransomware), stealing data (spyware), or joining a botnet.
Impact on Windows and macOS Systems
ISP-based malware attacks pose significant threats to both Windows and macOS systems, although the specific vulnerabilities and manifestations differ. Understanding these differences is crucial for effective mitigation and protection. This section will explore how malware impacts each operating system, focusing on vulnerabilities, symptoms, mitigation strategies, and the resulting impact on user data and privacy.
While both operating systems are susceptible to various attack vectors, their inherent architectures and security models lead to differing vulnerabilities and responses to malware infections. Windows, with its larger market share, historically has been a more frequent target, resulting in a larger body of malware specifically designed to exploit its weaknesses. macOS, while generally considered more secure, is not immune and is increasingly becoming a target as its user base expands.
Windows System Vulnerabilities and Malware Manifestations
Windows systems, due to their broader market share and historical legacy, often face a wider range of malware threats. Vulnerabilities can range from outdated software and unpatched security flaws to user error, such as clicking malicious links or downloading infected files. Malware manifests in various ways, including file corruption (rendering documents or programs unusable), system slowdown (making the computer sluggish and unresponsive), and unauthorized access to sensitive data.
Malicious processes may consume significant system resources, leading to crashes or freezes. Furthermore, some malware can install keyloggers, capturing keystrokes and potentially stealing passwords and other sensitive information. Windows Defender, along with third-party antivirus solutions, attempts to mitigate these threats through real-time scanning, behavioral analysis, and automatic updates. However, sophisticated malware can often evade detection and exploit vulnerabilities before patches are applied.
macOS System Vulnerabilities and Malware Manifestations
macOS, while generally considered more secure than Windows, is not invulnerable to malware attacks. Although the number of macOS-specific malware strains is lower than for Windows, the increasing popularity of macOS makes it an increasingly attractive target for cybercriminals. Vulnerabilities often stem from users downloading and installing malicious software from untrusted sources or clicking on phishing links. Malware manifestations on macOS can include similar symptoms to Windows, such as file corruption, system slowdown, and unauthorized access to data.
However, the nature of the malware and the methods of infection might differ. macOS’s built-in security features, such as Gatekeeper and XProtect, along with third-party security software, provide some level of protection. However, zero-day exploits and sophisticated malware can still bypass these defenses.
Operating System Response to Malicious Processes
Windows and macOS employ different approaches to handling malicious processes. Windows traditionally relies on a combination of real-time scanning, signature-based detection, and behavioral analysis to identify and terminate malicious processes. The Windows Security Center (now Windows Security) provides a centralized interface for managing security settings and monitoring system health. macOS, on the other hand, emphasizes a more proactive approach, leveraging features like Gatekeeper to restrict the execution of unsigned or untrusted applications.
XProtect, a built-in antivirus component, also scans for known malware. Both operating systems provide methods for isolating or quarantining suspicious files, but the specific mechanisms and user experience differ.
Impact on User Data and Privacy
Malware infections on both Windows and macOS systems can significantly impact user data and privacy. Malware can steal personal information, such as passwords, credit card details, and sensitive documents. It can also encrypt files, demanding ransom for their release (ransomware). Additionally, malware can track user activity, monitor browsing habits, and steal sensitive data through keyloggers or screen capture tools.
The impact on privacy can be severe, potentially leading to identity theft, financial loss, and reputational damage. The effectiveness of data protection measures varies depending on the specific malware, the user’s security practices, and the operating system’s security features.
Malware Infection Progression Flowchart
The following describes a flowchart illustrating the progression of a malware infection from ISP delivery to system compromise. Imagine a visual representation, a box-and-arrow diagram.
Box 1: Malware Delivery via ISP
-This box represents the initial stage where the malware is delivered through the compromised ISP infrastructure. This could be through manipulated DNS records, injecting malicious code into legitimate websites, or other similar techniques.
Arrow 1: User Accesses Compromised Resource
-An arrow connects Box 1 to Box 2, indicating the user interacting with the compromised resource (e.g., visiting a malicious website, opening a phishing email).
Box 2: Malware Execution
-This box shows the point where the malware code executes on the user’s system. This could be through a drive-by download, exploiting a software vulnerability, or social engineering techniques.
Arrow 2: System Compromise
-An arrow connects Box 2 to Box 3, signifying the successful installation and execution of the malware.
Box 3: Data Exfiltration/System Damage
-This final box represents the consequences of the infection, including data theft, system damage, or disruption of services.
Mitigation and Prevention Strategies
Protecting your home network and devices from ISP-based malware attacks requires a multi-layered approach. While complete immunity is impossible, significantly reducing your risk is achievable through proactive security measures and vigilant monitoring. This involves strengthening your network’s defenses, implementing robust authentication practices, and staying informed about potential threats.
Securing Home Networks and Devices
Effective home network security begins with strong passwords for your router and all connected devices. Change default router passwords immediately upon installation. Regularly update your router’s firmware to patch security vulnerabilities. Consider enabling WPA3 or WPA2 encryption on your Wi-Fi network, avoiding WEP due to its known vulnerabilities. Disable WPS (Wi-Fi Protected Setup) to prevent unauthorized access.
Furthermore, regularly scan your network for unauthorized devices using your router’s interface or dedicated network scanning tools. A firewall on your router can help block malicious traffic before it reaches your devices.
Strong Passwords and Multi-Factor Authentication
Employing strong, unique passwords is crucial. Avoid easily guessable passwords and use a password manager to generate and securely store complex passwords for each of your accounts. Multi-factor authentication (MFA) adds an extra layer of security by requiring a second form of verification, such as a one-time code from your phone or a biometric scan, in addition to your password.
Enable MFA wherever possible, especially for critical accounts like your email and online banking. This significantly hinders unauthorized access even if your password is compromised.
Up-to-Date Antivirus Software and Firewall Protection
Regularly updating your antivirus software is paramount. Ensure your software is from a reputable vendor and that the definition files are updated frequently. A robust firewall, either built into your operating system or a third-party application, monitors network traffic and blocks suspicious connections. Configure your firewall to allow only necessary traffic and block all other incoming connections.
Consider using a combination of real-time protection and scheduled scans to maintain optimal security. Regularly check your antivirus software’s logs for any suspicious activity.
Configuring Network Settings for Enhanced Security
Enabling a firewall on your devices is a critical step. This blocks unauthorized access attempts and helps prevent malware from establishing connections. Regularly review and adjust your firewall rules to ensure only necessary applications and services are permitted. Consider using a VPN (Virtual Private Network) to encrypt your internet traffic, especially when using public Wi-Fi. A VPN masks your IP address and makes it harder for attackers to track your online activity.
Disable file and printer sharing unless absolutely necessary.
Identifying and Responding to Suspicious Network Activity
Be aware of unusual network behavior. This could include slow internet speeds, unexpected pop-ups, or unauthorized access to your devices. Regularly check your router’s logs for any suspicious connections or activity. If you suspect a compromise, disconnect from the internet immediately. Run a full system scan with your antivirus software and consider seeking professional help to investigate and remediate the issue.
Report any suspicious activity to your internet service provider and relevant authorities.
Case Studies and Real-World Examples

While many malware infections occur through phishing emails or malicious downloads, attacks leveraging vulnerabilities within an Internet Service Provider’s (ISP) infrastructure are less common but potentially far-reaching. These attacks often go unnoticed for extended periods, impacting a large number of users simultaneously. Examining documented cases helps highlight the methods used, the impact, and the necessary preventative measures.
The Case of the Compromised DNS Server
One documented case involved a compromised DNS server at a smaller ISP. Attackers gained unauthorized access to the server, subtly altering the DNS records for several legitimate websites. When users attempted to access these sites, they were unknowingly redirected to malicious websites hosting malware. This attack targeted both Windows and macOS users indiscriminately. The malware itself was a sophisticated information-stealer, designed to capture login credentials, financial information, and other sensitive data.
The attack went undetected for several months, impacting hundreds of subscribers before being discovered by a security researcher who noticed unusual DNS traffic patterns.
Attack Methods and Impact
The attackers utilized a combination of techniques. Initially, they exploited a known vulnerability in the outdated DNS server software. This vulnerability allowed for remote code execution, granting the attackers full control of the server. Once inside, they used their access to modify the DNS records. The impact was significant.
Users experienced credential theft, leading to identity theft and financial losses. Furthermore, the compromised systems could have been used as part of a larger botnet, potentially participating in DDoS attacks or other malicious activities. The scale of the breach was only fully understood after a thorough forensic investigation.
Remediation and Prevention
Following the discovery, the ISP immediately took several steps. They patched the vulnerability in their DNS server, updated their security protocols, and implemented stricter access controls. They also conducted a comprehensive security audit of their entire network infrastructure. For affected users, the ISP provided assistance with malware removal, password resets, and identity theft protection services. Crucially, the ISP collaborated with law enforcement to investigate the attackers and prevent future attacks.
This proactive approach highlighted the importance of regular security updates, vulnerability scanning, and incident response planning.
Comparison of Security Vulnerabilities
The primary vulnerability exploited was the outdated DNS server software. This weakness affected both Windows and macOS users equally, as the attack targeted the DNS resolution process, independent of the operating system. While the specific malware payload might have had different effects on each operating system, the initial vector – the compromised DNS server – was universal. The lack of multi-factor authentication on the DNS server also contributed significantly to the success of the attack.
A stronger authentication mechanism would have made unauthorized access significantly more difficult.
Key Findings Summary, Malware induction into windows and macos devices via isp
| Aspect | Finding |
|---|---|
| Vulnerability Exploited | Outdated DNS server software with remote code execution vulnerability |
| Attack Method | DNS record manipulation |
| Malware Type | Information stealer |
| Impact | Credential theft, financial loss, potential botnet participation |
Wrap-Up: Malware Induction Into Windows And Macos Devices Via Isp
The threat of malware delivered via your internet service provider is real, and understanding its mechanics is the first step towards effective protection. While the methods employed by attackers are constantly evolving, proactive measures such as strong passwords, up-to-date security software, and a healthy dose of online vigilance are your best defense. Remember, securing your digital life isn’t just about installing software; it’s about cultivating a proactive security mindset.
Stay informed, stay vigilant, and stay safe!
FAQ Insights
What is DNS spoofing and how does it relate to malware delivery via ISPs?
DNS spoofing is a technique where attackers manipulate DNS records to redirect users to malicious websites. If your ISP’s DNS servers are compromised, they can redirect your requests to sites hosting malware, leading to infection when you visit what you think is a legitimate site.
Can my router be compromised to deliver malware?
Absolutely. Compromised routers can be used as a gateway to deliver malware to all devices connected to your network. Attackers can install malicious firmware or exploit vulnerabilities in your router’s software to achieve this.
How can I tell if my ISP is involved in a malware attack?
It’s difficult to definitively know if your ISP is directly involved. However, unusual network activity, frequent pop-ups from unknown sources, and slow internet speeds, especially if multiple devices are affected, could be indicators. Contact your ISP if you suspect something is wrong.





