Zen Edge Data Management A New Era
Zen Edge Data Management: Imagine a world where data processing happens right where it’s created – at the edge of your network. This isn’t just about faster speeds; it’s about unlocking entirely new possibilities for real-time insights, improved efficiency, and enhanced security. We’re diving deep into this transformative approach, exploring its core principles, architectural considerations, and the revolutionary impact it’s having across various industries.
From understanding the fundamental differences between Zen Edge Data Management and traditional cloud-based systems to navigating the complexities of data governance and compliance at the edge, this exploration will equip you with a comprehensive understanding of this cutting-edge technology. We’ll also examine practical examples, best practices, and potential pitfalls to help you harness the power of Zen Edge Data Management effectively.
Defining Zen Edge Data Management
Zen Edge Data Management represents a paradigm shift in how we handle data, moving away from centralized cloud-based systems and embracing a more distributed, intelligent approach. It’s about bringing data processing and analysis closer to the source, minimizing latency and maximizing efficiency, all while maintaining data security and governance. This approach is particularly relevant in today’s increasingly data-driven world, where real-time insights are critical for many applications.Core Principles of Zen Edge Data Management hinge on several key concepts: proximity, autonomy, and intelligence.
Proximity refers to processing data as close to its origin as possible – at the “edge” of the network, whether that’s a sensor, a machine, or a remote location. Autonomy means that edge devices can operate independently, making decisions and acting on data without constant communication with a central server. Finally, intelligence involves leveraging advanced analytics and machine learning at the edge to extract meaningful insights from raw data in real-time.
This trifecta empowers faster response times, reduced bandwidth consumption, and enhanced operational efficiency.
Key Differentiators from Traditional Data Management
Traditional data management often relies on centralized data centers or cloud platforms. This approach can introduce significant latency, especially when dealing with high-volume, real-time data streams. Zen Edge Data Management, in contrast, prioritizes decentralized processing, reducing latency and improving responsiveness. Another key differentiator is the increased focus on data security. By processing sensitive data closer to its source, the risk of data breaches during transmission is minimized.
Furthermore, edge devices can operate even with limited or intermittent connectivity, ensuring operational continuity in challenging environments. Traditional approaches typically struggle with such scenarios. Finally, Zen Edge Data Management fosters greater agility and adaptability. The decentralized nature allows for easier scaling and integration of new data sources and analytical tools.
Comparison with Cloud-Based Data Management
While cloud-based data management offers scalability and centralized access, it often suffers from latency issues, particularly when dealing with time-sensitive data from geographically dispersed sources. Zen Edge Data Management complements cloud-based approaches by handling real-time processing at the edge, reducing the load on the cloud and improving response times. Consider a smart city application: cloud-based systems might handle long-term trend analysis, while edge processing would manage real-time traffic flow optimization based on sensor data from traffic lights and cameras.
This hybrid approach leverages the strengths of both methodologies. The cloud retains its strengths in long-term storage and centralized analytics, while the edge handles immediate actions and processing. The key difference lies in the location of data processing: cloud-based systems centralize processing, whereas Zen Edge Data Management distributes it to the edge devices.
Industries Benefiting from Zen Edge Data Management
Zen Edge Data Management finds particular application in industries that generate and process large volumes of real-time data. The manufacturing sector, for example, can leverage edge computing for predictive maintenance, analyzing sensor data from machines to anticipate failures and schedule maintenance proactively. This minimizes downtime and optimizes production efficiency. Similarly, in the healthcare sector, edge devices can process medical images and patient data at the point of care, enabling faster diagnosis and treatment.
Autonomous vehicles rely heavily on edge computing for real-time decision-making based on sensor data, ensuring safe and efficient navigation. Finally, the energy sector utilizes edge computing for smart grid management, optimizing energy distribution and reducing waste. These are just a few examples of how Zen Edge Data Management is revolutionizing various industries by enabling faster, more efficient, and more secure data processing.
Architectural Considerations
Designing a robust and efficient Zen Edge Data Management system requires careful consideration of its architecture. A well-structured architecture ensures data integrity, minimizes latency, and maximizes the benefits of edge computing. The following sections delve into the key architectural components, their roles, and the challenges inherent in this approach.
Zen Edge Data Management System Architecture
The conceptual architecture below Artikels the key components of a Zen Edge Data Management system. This design prioritizes data locality, security, and scalability.
| Component | Function | Location (Edge/Cloud) | Security Considerations |
|---|---|---|---|
| Edge Gateway | Collects, preprocesses, and filters data from various edge devices. Acts as a secure entry point. | Edge | Firewall, intrusion detection, data encryption (both in transit and at rest), access control lists. Regular security audits and firmware updates are crucial. |
| Edge Data Store | Stores processed data locally for immediate access by edge applications. | Edge | Data encryption at rest, access control, regular backups to cloud storage, robust physical security for the hardware housing the data store. |
| Edge Application Server | Hosts applications that process data locally, minimizing latency and bandwidth consumption. | Edge | Secure containerization of applications, regular security patching, and access control to prevent unauthorized access or modification. |
| Cloud Data Hub | Aggregates, analyzes, and stores data from multiple edge locations. Provides centralized management and long-term storage. | Cloud | Data encryption at rest and in transit, robust authentication and authorization mechanisms, intrusion detection and prevention systems, regular security assessments and penetration testing. |
| Centralized Management Console | Provides a single pane of glass for monitoring, managing, and configuring all components of the system. | Cloud | Multi-factor authentication, role-based access control, secure communication channels, regular software updates, and intrusion detection systems. |
The Role of Edge Computing in Optimizing Data Management
Edge computing plays a vital role in optimizing data management by processing and analyzing data closer to its source. This reduces latency, bandwidth consumption, and reliance on cloud connectivity, enabling real-time insights and faster response times. For example, in a manufacturing setting, edge computing allows for immediate analysis of sensor data to detect anomalies and prevent equipment failures, optimizing production efficiency and reducing downtime.
This local processing also reduces the volume of data transmitted to the cloud, lowering costs and improving overall system performance.
Data Security and Privacy Challenges in a Zen Edge Architecture
The distributed nature of a Zen Edge architecture presents unique data security and privacy challenges. The increased attack surface across multiple edge locations necessitates robust security measures at each layer. Data breaches at the edge could have severe consequences, potentially compromising sensitive information. Ensuring data privacy compliance with regulations like GDPR and CCPA requires careful consideration of data access control, encryption, and anonymization techniques at all stages of the data lifecycle.
The challenge lies in maintaining a balance between enabling efficient data processing at the edge and safeguarding sensitive data.
Data Transfer and Processing Bottlenecks and Solutions
Potential bottlenecks in data transfer and processing at the edge include limited bandwidth, processing power constraints on edge devices, and network latency. Solutions include employing efficient data compression techniques, optimizing data filtering and preprocessing at the edge to reduce data volume, and leveraging more powerful edge devices with enhanced processing capabilities. Implementing a tiered edge architecture, with progressively more powerful processing capabilities at higher tiers, can also address this.
Load balancing across multiple edge devices and intelligent routing of data can further improve performance and prevent congestion. Finally, utilizing technologies like fog computing, which extends cloud capabilities to the edge, can provide additional processing power and storage when needed.
Data Processing and Analytics at the Edge

Processing data at the edge is crucial for applications requiring real-time responses and reduced bandwidth consumption. The closer data processing happens to its source, the faster insights can be generated and acted upon, leading to significant efficiency gains and improved decision-making. This section explores various methods for edge data processing and analytics, highlighting their use cases and comparing different edge computing platforms.
Methods for Edge Data Processing
Several methods exist for processing data at the edge, each tailored to different latency requirements and data volumes. Simple methods might involve pre-processing data before transmission to the cloud, while more complex methods leverage powerful edge devices for advanced analytics. Real-time requirements often dictate the choice of method. For instance, autonomous vehicles rely on extremely low-latency processing at the edge to avoid accidents, while less time-sensitive applications, such as inventory management in a warehouse, can tolerate slightly higher latencies.
Edge Analytics Use Cases and Benefits
Edge analytics unlocks powerful capabilities across various sectors. Consider predictive maintenance in manufacturing. Sensors on machinery continuously monitor vibrations, temperature, and other parameters. Edge devices process this data in real-time, identifying anomalies that predict potential failures. This allows for proactive maintenance, minimizing downtime and reducing repair costs.
In smart agriculture, edge analytics can analyze sensor data from soil moisture sensors, weather stations, and cameras to optimize irrigation, fertilization, and pest control, leading to increased crop yields and reduced resource consumption. Another example is real-time fraud detection in financial transactions. Edge devices can analyze transaction data immediately, flagging suspicious activity for immediate investigation.
Comparison of Edge Computing Platforms
Choosing the right edge computing platform is vital for successful edge data management. The optimal platform depends on factors such as scalability requirements, data volume, processing needs, and budget.
- AWS Greengrass: Offers a comprehensive suite of tools for building, deploying, and managing edge applications. It excels in scalability and integration with other AWS services. However, it might be overkill for simpler applications.
- Azure IoT Edge: Provides a similar functionality to Greengrass, integrating seamlessly with Azure services. It’s well-suited for organizations already invested in the Microsoft ecosystem.
- Google Cloud IoT Edge: Focuses on secure data processing and management at the edge, offering strong security features and integration with Google Cloud services.
- Local Edge Devices (e.g., Raspberry Pi, NVIDIA Jetson): These offer cost-effective solutions for smaller-scale deployments with less demanding processing requirements. However, managing and scaling these can be more challenging.
Generating and Utilizing Real-Time Data Insights
Real-time data insights are the ultimate goal of edge data management. Imagine a smart city using edge analytics to optimize traffic flow. Sensors embedded in roads and traffic lights collect data on vehicle speed, density, and accidents. Edge devices process this data, dynamically adjusting traffic light timings to minimize congestion and improve emergency vehicle response times. Similarly, in a retail setting, real-time data from point-of-sale systems and customer tracking systems can be analyzed to optimize staffing levels, personalize promotions, and improve inventory management.
This immediate feedback loop allows for agile responses to changing conditions and improved operational efficiency.
Data Governance and Compliance
Implementing robust data governance and ensuring compliance are paramount in a Zen Edge Data Management system. The distributed nature of edge computing introduces unique challenges, requiring a proactive and comprehensive approach to data security and regulatory adherence. This necessitates a clearly defined framework that addresses data quality, access control, and regulatory compliance across all edge locations.
Data Governance Framework
A successful data governance framework for a Zen Edge Data Management system needs to be built on several key pillars. First, a clear data ownership model must be established, specifying responsibilities for data creation, management, and security at each edge location. This includes defining roles and responsibilities for data access and modification. Second, comprehensive data catalogs are essential for tracking data lineage, location, and quality.
This allows for efficient data discovery and ensures that data is consistently managed and updated across all edge nodes. Finally, standardized data quality rules and procedures should be implemented to ensure data accuracy, completeness, and consistency. Regular audits and data quality checks are vital to maintaining these standards. These procedures must include mechanisms for detecting and resolving data quality issues promptly, ideally with automated alerts and workflows.
Data Quality and Consistency Procedures
Maintaining data quality and consistency across geographically dispersed edge locations requires a multi-faceted approach. Data validation at the point of ingestion is crucial; this involves implementing checks to ensure that data conforms to pre-defined standards and rules before it is stored. Real-time data synchronization across edge locations is necessary to prevent data inconsistencies and ensure that all edge nodes have access to the most up-to-date information.
This could involve using technologies like distributed ledgers or message queues to facilitate data replication and consistency. Finally, regular data reconciliation and cleanup procedures are essential to address inconsistencies and errors that may arise over time. This may involve automated processes that identify and correct discrepancies, along with manual intervention for complex issues.
Compliance with Data Privacy Regulations
Adherence to data privacy regulations, such as GDPR and CCPA, is critical in an edge computing environment. Data minimization principles should be strictly followed, limiting the collection and processing of personal data only to what is absolutely necessary. Data encryption, both in transit and at rest, is essential to protect sensitive information from unauthorized access. Furthermore, access control mechanisms should be implemented to restrict data access to authorized personnel only, with rigorous authentication and authorization procedures in place.
Finally, robust data retention policies should be established to ensure that data is deleted or anonymized when it is no longer needed, in accordance with relevant regulations. This includes implementing processes for managing data subject access requests (DSARs) efficiently and effectively. For example, a retail chain using edge computing for point-of-sale data would need to ensure compliance with GDPR and CCPA for customer data collected at each store location.
Data Breach Mitigation Strategies
Data breaches at the edge pose significant risks, given the distributed nature of the environment and the potential for vulnerabilities in individual edge devices. Implementing a multi-layered security approach is crucial. This includes network segmentation to isolate edge devices from the rest of the network, intrusion detection and prevention systems to monitor for malicious activity, and regular security audits and penetration testing to identify and address vulnerabilities.
Furthermore, robust incident response plans are essential to handle data breaches effectively, including procedures for containing the breach, notifying affected individuals, and collaborating with regulatory authorities. Consider a scenario where a manufacturing plant uses edge devices to monitor equipment performance. A breach in these devices could expose sensitive operational data, requiring swift mitigation and regulatory reporting. Regular software updates and patching are also crucial to address known vulnerabilities.
Finally, employee training on data security best practices is vital to minimizing human error, a common cause of data breaches.
Scalability and Maintainability
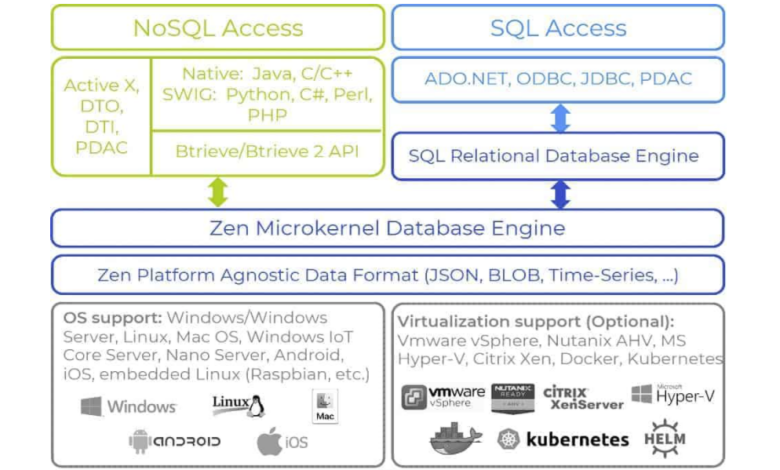
Building a truly effective Zen Edge Data Management system requires careful consideration of scalability and maintainability from the outset. A system that struggles to handle growing data volumes or becomes increasingly difficult to manage will quickly lose its value. Therefore, designing for scalability and ease of maintenance is crucial for long-term success. This involves choosing the right technologies, implementing robust monitoring, and employing automation wherever possible.Designing a scalable architecture demands a modular and distributed approach.
Instead of relying on a single, centralized system, we can leverage a distributed architecture where data processing and storage are spread across multiple edge nodes. This allows the system to handle increasing data volumes gracefully, as new nodes can be added to the network as needed. Furthermore, the modular design ensures that individual components can be upgraded or replaced without affecting the entire system.
This approach mirrors the success seen in cloud computing, where scalability is a core design principle.
Scalable Architecture Design
A key element of a scalable architecture is the ability to horizontally scale. This means adding more resources (compute, storage, network) as needed, rather than relying on vertically scaling (increasing the capacity of existing resources). In a Zen Edge Data Management system, this could involve adding more edge nodes to the network as data volumes increase. Each node could be equipped with its own processing and storage capabilities, allowing for parallel processing and distributed storage.
This horizontal scaling approach ensures that the system can adapt to fluctuating demands, maintaining performance even during peak loads. Load balancing across these nodes is critical to ensure even distribution of tasks and prevent bottlenecks.
Maintainability Strategies
Ensuring maintainability requires a proactive approach that prioritizes simplicity, modularity, and automation. A well-documented system with clearly defined interfaces is easier to understand and maintain. Modular design allows for independent updates and upgrades of individual components without requiring a complete system shutdown. The use of containerization technologies like Docker can further enhance maintainability by simplifying deployment and management of individual services.
Regular code reviews and automated testing are also crucial for catching potential issues early and ensuring code quality.
Automation and Orchestration
Automation is key to managing the complexity of a distributed edge system. Orchestration tools, such as Kubernetes, can automate the deployment, scaling, and management of edge resources. These tools can automate tasks such as provisioning new nodes, deploying software updates, and monitoring system health. Automation not only reduces manual effort but also improves consistency and reduces the risk of human error.
For instance, Kubernetes can automatically scale the number of pods running a particular data processing task based on the current workload.
Monitoring and Alerting
Proactive system management relies on robust monitoring and alerting mechanisms. These mechanisms provide real-time insights into the system’s health and performance. Metrics such as CPU utilization, memory usage, network bandwidth, and disk space can be monitored to identify potential bottlenecks or issues. Alerting systems can be configured to notify administrators of critical events, such as high CPU utilization or disk space exhaustion.
This allows for timely intervention and prevents minor issues from escalating into major outages. Examples include using Prometheus for metric collection and Grafana for visualization and alerting, providing a comprehensive monitoring solution. These tools can be integrated with alerting systems like PagerDuty to ensure timely notifications to the operations team.
Integration with Existing Systems
Integrating Zen Edge Data Management into your existing infrastructure is crucial for maximizing its benefits. A successful integration ensures seamless data flow between your edge devices, edge servers, and cloud systems, leveraging existing investments while enhancing overall data management capabilities. This requires careful consideration of various integration methods and potential challenges.Successfully integrating Zen Edge Data Management requires a strategic approach, considering both on-premise and cloud-based systems.
This involves selecting appropriate integration methods, managing data consistency, and ensuring interoperability across disparate systems. The ultimate goal is a unified data landscape, providing a single source of truth for decision-making.
API Integrations
API (Application Programming Interface) integrations provide a standardized way to connect Zen Edge Data Management with other systems. RESTful APIs are commonly used, allowing for easy data exchange through well-defined endpoints. For example, a manufacturing company might use APIs to integrate Zen Edge Data Management with their existing ERP (Enterprise Resource Planning) system, automatically updating inventory levels based on real-time data from edge sensors monitoring production lines.
This integration allows for automated responses to changing conditions and improves operational efficiency. Another example is a smart city project using APIs to integrate with traffic management systems, allowing for real-time analysis of traffic flow and optimization of traffic light timings based on data from edge devices. This reduces congestion and improves overall traffic flow.
Data Synchronization Strategies
Efficient data synchronization is vital for maintaining data consistency across different systems. Strategies include real-time synchronization, where data is updated instantly, and batch synchronization, where data is transferred in batches at scheduled intervals. The choice depends on factors like data volume, latency requirements, and the sensitivity of the data. Real-time synchronization is preferred for applications requiring immediate responses, such as those involving critical infrastructure monitoring.
Batch synchronization is more suitable for less time-sensitive data, such as historical logs or large datasets requiring less immediate processing. For example, a healthcare provider might use real-time synchronization for patient vital signs data, while using batch synchronization for patient medical history updates.
Challenges of Data Consistency and Interoperability
Integrating disparate systems presents challenges in maintaining data consistency and interoperability. Data formats, schemas, and data models can vary significantly, requiring data transformation and mapping to ensure compatibility. Different systems may also have varying levels of data quality, introducing potential inconsistencies. For example, integrating a legacy on-premise system with a cloud-based system might require significant data cleansing and transformation to ensure data consistency.
Addressing these challenges requires robust data governance policies and a well-defined data integration strategy. Implementing data quality checks and validation processes are also critical to ensure data accuracy and reliability throughout the system.
Data Flow Illustration
The following description illustrates the data flow between edge devices, edge servers, and cloud infrastructure. Imagine a diagram with three main sections:* Edge Devices: Various sensors and devices collect data (e.g., temperature, pressure, images). These devices are depicted as individual boxes, each labeled with its specific function and connected to the “Edge Server” section.* Edge Server: This section represents a central processing unit at the edge.
It receives data from edge devices, performs preliminary processing (e.g., filtering, aggregation), and then forwards processed data to the cloud. This is represented as a larger box receiving input from multiple edge devices and sending output to the “Cloud Infrastructure” section.* Cloud Infrastructure: This section depicts the cloud storage and processing resources. It receives processed data from the edge server, performs further analysis, and stores the data for long-term use.
This is depicted as a cloud symbol receiving input from the edge server. Data flows between these sections are indicated by arrows. The arrows might be labeled with protocols used (e.g., MQTT, HTTP) or data transfer methods (e.g., real-time, batch). This visualization provides a clear overview of the data flow within the Zen Edge Data Management system.
Case Studies and Best Practices
Implementing Zen Edge Data Management effectively requires careful planning and execution. Learning from successful deployments and understanding common pitfalls is crucial for maximizing ROI and avoiding costly mistakes. This section explores real-world examples, best practices, and potential challenges to help you navigate the implementation process.
Successful Zen Edge Data Management implementations demonstrate significant improvements in operational efficiency, data-driven decision-making, and overall business outcomes. By analyzing these case studies, we can identify key strategies and techniques that contribute to successful deployments, while also highlighting areas where projects may encounter difficulties.
Manufacturing Case Study: Predictive Maintenance
A large manufacturing company implemented Zen Edge Data Management to improve the predictive maintenance of their assembly lines. Sensors on machinery collected real-time data on vibration, temperature, and pressure. This data was processed at the edge, identifying potential equipment failures before they occurred. The system reduced downtime by 20% and maintenance costs by 15%.
“By processing data at the edge, we eliminated the latency associated with sending data to the cloud, enabling timely intervention and preventing costly production disruptions,” said the company’s CTO.
Retail Case Study: Personalized Customer Experiences
A major retailer used Zen Edge Data Management to analyze customer purchasing patterns in real-time at individual store locations. This enabled personalized recommendations and targeted promotions, leading to a 10% increase in sales and improved customer satisfaction. The system also optimized inventory management by predicting demand more accurately.
“The ability to personalize the shopping experience based on real-time data significantly improved customer engagement and ultimately boosted sales,” noted the company’s Chief Marketing Officer.
Best Practices for Zen Edge Data Management
Successful implementation hinges on a well-defined strategy. Key best practices include:
Prioritizing data security and compliance from the outset is critical. This includes robust access control mechanisms, data encryption both in transit and at rest, and adherence to relevant regulations like GDPR or CCPA.
Choosing the right edge computing infrastructure is crucial. Factors to consider include the processing power required, network connectivity, and scalability needs. A well-defined architecture ensures efficient data processing and minimizes latency.
Developing a clear data governance strategy is essential for maintaining data quality and consistency. This includes defining data ownership, access controls, and data quality standards.
Return on Investment (ROI) of Zen Edge Data Management
The ROI of Zen Edge Data Management varies depending on the specific application and industry. However, common benefits that contribute to a positive ROI include:
- Reduced operational costs through improved efficiency and automation.
- Increased revenue through improved decision-making and enhanced customer experiences.
- Improved data security and compliance.
- Faster time to insights due to reduced latency.
For example, the manufacturing company mentioned earlier saw a combined 35% reduction in costs and downtime, representing a substantial ROI on their investment in Zen Edge Data Management.
Common Pitfalls to Avoid
Several common pitfalls can hinder the success of Zen Edge Data Management projects. These include:
- Underestimating the complexity of edge deployments and lacking a well-defined architecture.
- Ignoring data security and compliance considerations.
- Failing to properly integrate with existing systems.
- Lack of skilled personnel to manage and maintain the system.
Careful planning, robust testing, and ongoing monitoring are crucial for mitigating these risks and ensuring a successful implementation.
Epilogue: Zen Edge Data Management
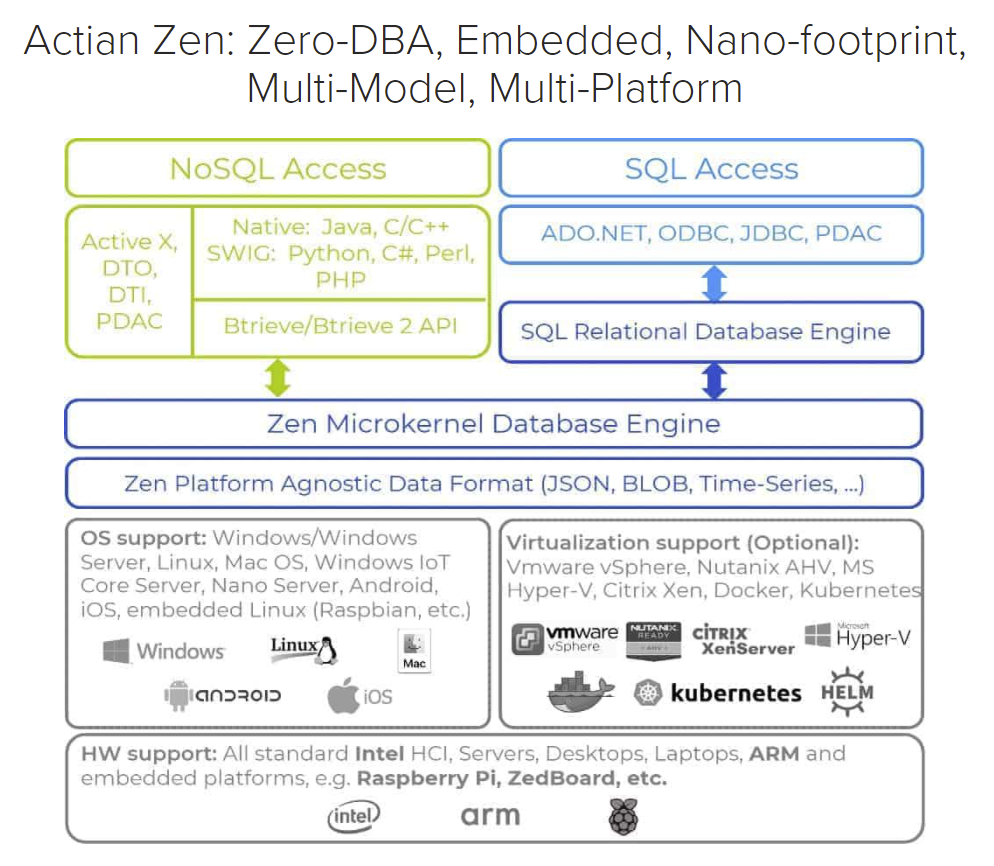
Zen Edge Data Management represents a significant shift in how we approach data. By bringing processing closer to the source, we unlock unprecedented speed, efficiency, and control. While challenges exist – particularly around security and scalability – the potential rewards are immense. As we’ve seen, successful implementation hinges on a well-defined architecture, robust data governance, and a proactive approach to system management.
The future of data management is undeniably at the edge, and understanding its nuances is key to staying ahead.
Frequently Asked Questions
What are the main benefits of Zen Edge Data Management over cloud-based solutions?
Reduced latency, improved bandwidth efficiency, enhanced data security through localized processing, and the ability to operate in disconnected or low-bandwidth environments are key advantages.
How does Zen Edge Data Management address data privacy concerns?
By processing sensitive data closer to its source and potentially within geographically restricted zones, Zen Edge Data Management minimizes the need to transmit large volumes of data across potentially insecure networks, thus enhancing privacy.
What are some common challenges in implementing Zen Edge Data Management?
Challenges include managing the complexity of distributed systems, ensuring data consistency across edge locations, and securing edge devices from potential threats. Scalability and maintaining efficient data governance are also critical considerations.
What types of industries benefit most from Zen Edge Data Management?
Industries with high volumes of real-time data and stringent latency requirements, such as manufacturing, healthcare, transportation, and smart cities, stand to gain significantly from Zen Edge Data Management.