Zero Trust Security Endpoint Readiness
Zero trust security how to get your endpoints ready – Zero Trust Security: How to Get Your Endpoints Ready – that’s the burning question for any organization serious about cybersecurity in today’s threat landscape. Forget the old perimeter-based security model; we’re diving deep into a world where “never trust, always verify” is the golden rule. This means securing every single endpoint, from laptops and desktops to mobile devices and IoT gadgets, with a robust, multi-layered defense.
We’ll explore the core principles of zero trust, assess your current security posture, implement effective controls, and establish a continuous monitoring strategy. Get ready to transform your endpoint security game!
This isn’t just about installing software; it’s about a fundamental shift in mindset. We’ll cover everything from multi-factor authentication (MFA) and endpoint detection and response (EDR) to data loss prevention (DLP) and micro-segmentation. We’ll also tackle the crucial aspects of user training and managing the complexities of different endpoint types, including the ever-growing challenge of BYOD (Bring Your Own Device).
Think of this as your comprehensive guide to building a truly secure and resilient endpoint environment.
Understanding Zero Trust Principles for Endpoints
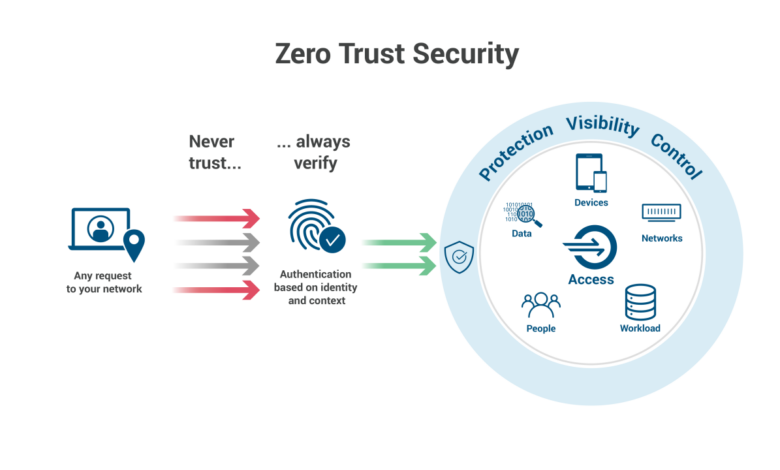
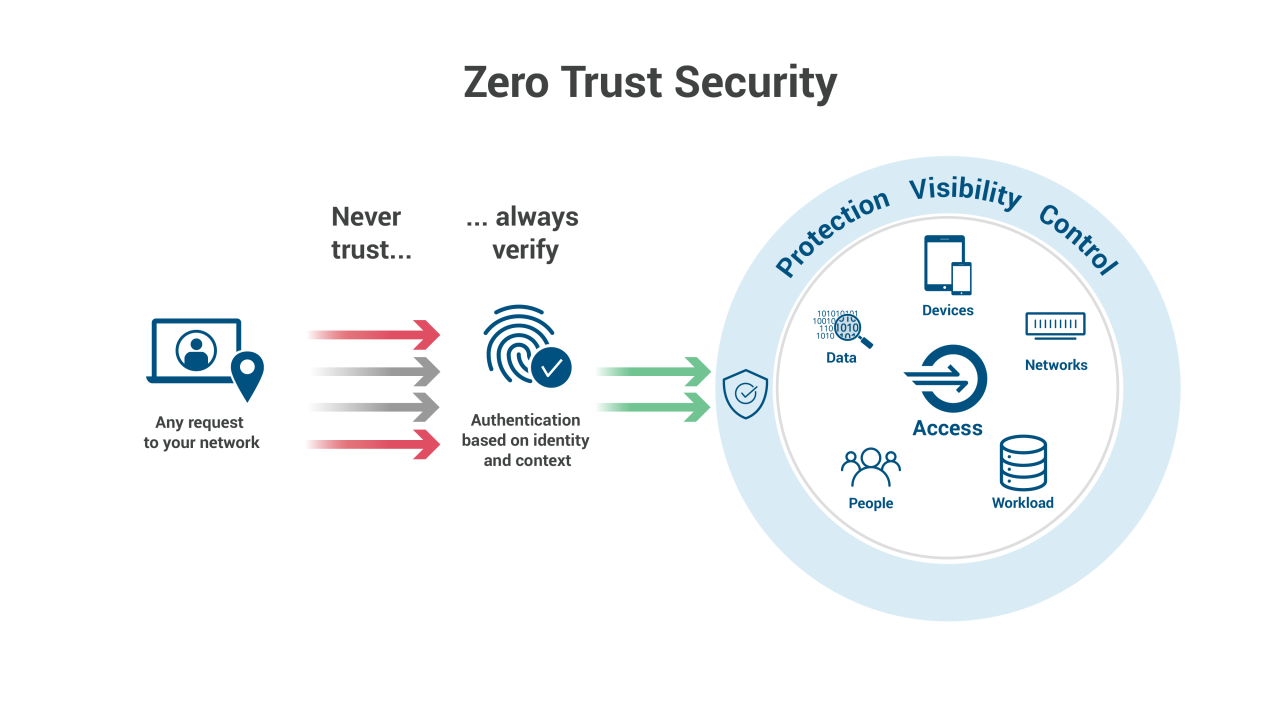
Zero trust security represents a fundamental shift in how we approach network security. Instead of relying on a perimeter-based model that assumes anything inside the network is trustworthy, zero trust operates on the principle of “never trust, always verify.” This applies to every device, user, and application, regardless of location. This means that even devices considered “internal” must prove their identity and authorization before accessing any resources.
This paradigm shift is especially crucial for endpoints, the devices that are often the most vulnerable points of entry for cyberattacks.Zero trust for endpoints emphasizes continuous verification and least privilege access. This means that access is granted only for the specific resources needed and only for the duration required, constantly reassessing and re-validating the device’s trustworthiness based on various factors.
This proactive approach significantly reduces the blast radius of a successful breach, limiting the damage a compromised endpoint can inflict.
Core Tenets of Zero Trust Security
Zero trust security rests on several key principles. These include strong authentication and authorization, micro-segmentation of the network, continuous monitoring and assessment of devices, and the use of least privilege access. Each of these elements works in concert to minimize the impact of a potential security breach. For endpoints, this translates into robust device posture checks, multi-factor authentication, and granular control over application access.
Never Trust, Always Verify: Endpoint Application
The “never trust, always verify” principle is central to zero trust security. When applied to endpoints, it means that every endpoint, whether a laptop, mobile device, or IoT gadget, must prove its identity and its current security posture before accessing any resources. This verification process might include checking for up-to-date antivirus software, the presence of a valid digital certificate, and the device’s compliance with security policies.
Only after successful verification is access granted, and even then, it’s often limited to the minimum necessary level.
Zero Trust vs. Traditional Perimeter-Based Security
Traditional perimeter-based security relies on a castle-and-moat approach, assuming that anything inside the network is safe. This model is vulnerable because once an attacker breaches the perimeter, they have relatively free reign within the network. Zero trust, in contrast, eliminates the concept of an implicit trust zone. Every access request is treated as if it originates from an untrusted source, regardless of location.
This fundamental difference makes zero trust far more resilient to modern sophisticated attacks that often bypass traditional perimeter defenses.
Conceptual Model of Zero Trust Endpoint Security
Imagine a model where each endpoint is treated as an independent island. Each island has a robust security perimeter (strong authentication, device posture checks, etc.). Communication between islands is strictly controlled and mediated through a central security policy enforcement point. This point verifies the identity and authorization of each request before granting access to specific resources on the target island.
The central point also continuously monitors the security posture of each island, adjusting access based on real-time risk assessments. This approach limits lateral movement, a common tactic used by attackers to compromise multiple systems after gaining initial access. Any compromised endpoint is isolated quickly, minimizing the potential damage.
Assessing Your Current Endpoint Security Posture
Embarking on a Zero Trust journey requires a realistic understanding of your current endpoint security landscape. Before implementing new controls, a thorough assessment is crucial to identify weaknesses and prioritize remediation efforts. This process involves evaluating existing security measures, pinpointing vulnerabilities, and determining your overall readiness for a Zero Trust architecture. Ignoring this step can lead to significant security gaps and undermine the effectiveness of your Zero Trust implementation.Understanding your current state allows for a strategic approach to Zero Trust adoption.
Instead of a wholesale replacement of existing systems, you can focus on strengthening weak points and integrating new technologies where needed, optimizing your resources and minimizing disruption.
Identifying Vulnerabilities in Existing Endpoint Security Infrastructure
A comprehensive vulnerability assessment should cover all aspects of your endpoint security. This includes examining the operating systems, applications, and configurations of your endpoints (laptops, desktops, mobile devices, servers, IoT devices etc.). Outdated software, weak passwords, missing patches, and improperly configured firewalls are common vulnerabilities. Consider the potential impact of each vulnerability – a critical vulnerability in a system managing sensitive data has a far greater risk than a minor vulnerability in a less critical system.
For example, an unpatched vulnerability in a web server could lead to a data breach, while an outdated version of a productivity application might only pose a minor risk. Analyzing the attack surface area, considering both internal and external threats, is paramount.
Best Practices for Conducting a Thorough Endpoint Security Assessment
A robust endpoint security assessment should follow a structured methodology. Begin with a detailed inventory of all endpoints, including their hardware specifications, operating systems, and installed software. This inventory provides a baseline for understanding the attack surface. Next, conduct vulnerability scans using automated tools to identify known vulnerabilities in the software and operating systems. Supplement these automated scans with penetration testing, simulating real-world attacks to identify exploitable weaknesses not detected by automated tools.
Regular assessments, preferably automated and scheduled, are crucial to continuously monitor and adapt to the evolving threat landscape. Finally, carefully analyze the findings, prioritizing vulnerabilities based on their severity and likelihood of exploitation.
The Importance of Vulnerability Scanning and Penetration Testing
Vulnerability scanning employs automated tools to identify known security weaknesses in software and systems. These tools compare the endpoint’s configuration against a database of known vulnerabilities (CVEs – Common Vulnerabilities and Exposures). Penetration testing, on the other hand, involves simulating real-world attacks to uncover vulnerabilities that might be missed by vulnerability scanners. Penetration testers attempt to exploit weaknesses in the system, providing a more comprehensive understanding of the security posture.
Both are essential for a complete assessment; vulnerability scanning provides a broad overview, while penetration testing focuses on the most critical vulnerabilities and identifies potential exploits. For example, a vulnerability scan might identify an outdated version of a web server, while a penetration test might reveal that this outdated server is vulnerable to a specific exploit allowing attackers to gain control.
Endpoint Security Readiness Checklist for Zero Trust Adoption
Before implementing Zero Trust, it’s vital to assess your readiness. This checklist helps organize the assessment process:
- Inventory of Endpoints: A complete list of all endpoints, including their operating systems, applications, and locations.
- Vulnerability Scanning: Regular automated scans to identify known vulnerabilities.
- Penetration Testing: Simulated attacks to identify exploitable weaknesses.
- Patch Management: A process for timely patching of vulnerabilities.
- Endpoint Detection and Response (EDR): Deployment of EDR solutions to detect and respond to threats.
- Data Loss Prevention (DLP): Implementation of DLP measures to prevent sensitive data leakage.
- Multi-Factor Authentication (MFA): Enforcement of MFA for all users and devices.
- Access Control Policies: Well-defined access control policies based on the principle of least privilege.
- Security Awareness Training: Regular security awareness training for users.
- Incident Response Plan: A comprehensive plan for handling security incidents.
Implementing Zero Trust Endpoint Security Controls: Zero Trust Security How To Get Your Endpoints Ready
Implementing robust endpoint security is paramount in a Zero Trust architecture. It shifts the focus from network perimeter security to securing individual devices and the data they access, regardless of location. This requires a multi-layered approach, encompassing authentication, threat detection, data protection, and access control. The following sections detail key controls and their implementation.
Multi-Factor Authentication (MFA) for Endpoints
MFA adds an extra layer of security beyond traditional passwords. By requiring multiple forms of authentication – something you know (password), something you have (phone, security key), and/or something you are (biometrics) – MFA significantly reduces the risk of unauthorized access, even if credentials are compromised. Implementation involves integrating MFA capabilities into your endpoint management system and enforcing its use for all users accessing company resources.
This might involve using a cloud-based MFA provider or integrating with your existing identity provider. Consider offering a variety of MFA methods to cater to user preferences and device capabilities. Proper training for users on the importance of MFA and how to use it effectively is crucial.
Endpoint Detection and Response (EDR) Solution Deployment
EDR solutions provide real-time visibility into endpoint activity, detecting and responding to malicious behavior. Deployment involves installing the EDR agent on all endpoints, configuring central management, and establishing alerting rules based on your organization’s risk profile. Successful deployment necessitates careful planning, including agent compatibility testing across your diverse endpoint ecosystem. Regular updates are critical to ensure protection against emerging threats.
Integration with other security tools, such as SIEM (Security Information and Event Management) systems, is highly recommended to improve threat analysis and incident response. A phased rollout, starting with pilot groups, can help identify and address potential issues before full deployment.
Leveraging Data Loss Prevention (DLP) Tools for Endpoint Security
DLP tools help prevent sensitive data from leaving the organization’s control. Implementation involves installing and configuring DLP agents on endpoints, defining data loss prevention policies based on data type and sensitivity, and integrating with other security systems for centralized monitoring and reporting. Careful consideration must be given to balancing data protection with user productivity. Overly restrictive policies can hinder legitimate business activities.
Regular policy reviews and adjustments are necessary to ensure effectiveness and adapt to evolving threats and business needs. Consider using both agent-based and agentless DLP solutions to provide comprehensive protection across various endpoints and applications.
Configuring Device Posture Assessment
Device posture assessment involves evaluating the security configuration of endpoints before granting access to resources. This is a step-by-step process:
- Define Security Baselines: Establish clear security standards for endpoints, including operating system patching, antivirus software, firewall configurations, and acceptable software.
- Implement Assessment Tools: Integrate device posture assessment capabilities into your endpoint management system or use dedicated tools. These tools will scan endpoints for compliance with defined baselines.
- Configure Access Control Rules: Create policies that restrict access based on endpoint posture. Endpoints failing to meet security baselines should be denied access to sensitive resources.
- Remediation Strategies: Establish processes for addressing non-compliant endpoints. This may involve providing users with instructions on how to remediate issues or deploying automated remediation tools.
- Continuous Monitoring: Regularly monitor endpoint posture to ensure ongoing compliance and identify potential vulnerabilities.
Effective Access Control Policies for Endpoints
Implementing granular access control policies is crucial. The following table illustrates examples:
| Control Type | Implementation Details | Benefits | Potential Challenges |
|---|---|---|---|
| Least Privilege Access | Grant users only the minimum necessary permissions to perform their jobs. | Reduces the impact of compromised accounts, limits lateral movement. | Requires careful planning and ongoing review of user permissions. |
| Role-Based Access Control (RBAC) | Assign permissions based on user roles within the organization. | Simplifies permission management, improves consistency. | Requires a well-defined role structure and regular updates. |
| Context-Aware Access Control | Control access based on factors like device location, time of day, and user behavior. | Enhances security by adapting to changing conditions. | Can be complex to implement and manage. Requires sophisticated tools. |
| Network Segmentation | Isolate sensitive resources on separate networks, limiting access based on network location. | Limits the impact of breaches by containing threats within specific segments. | Requires careful planning and may increase network complexity. |
Securing Endpoint Communication and Data
Implementing Zero Trust requires a robust strategy for securing endpoint communication and data, both in transit and at rest. This goes beyond traditional perimeter security and focuses on protecting individual endpoints and the data they handle, regardless of their location or network connection. A layered approach, combining multiple security controls, is crucial for achieving a truly secure environment.
The core principle is to assume breach and minimize the impact of a compromised endpoint. This involves encrypting sensitive data, controlling access, and limiting the potential for lateral movement within your network. By implementing these strategies, organizations can significantly reduce their attack surface and improve their overall security posture.
Endpoint-to-Endpoint Communication Security Best Practices
Securing communication between endpoints involves multiple layers of protection. It’s not enough to rely solely on network security; endpoint-level security is paramount. A multi-faceted approach is essential.
- Utilize VPNs: Virtual Private Networks (VPNs) encrypt all traffic between the endpoint and the network, protecting data in transit from eavesdropping and man-in-the-middle attacks. This is especially crucial for remote workers accessing company resources.
- Implement TLS/SSL: Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL) encrypt communication between applications and servers. Ensuring all web traffic and other relevant communications use HTTPS is a fundamental best practice.
- Employ strong authentication: Multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access. This should be mandatory for all endpoint access.
- Regular security updates: Keeping operating systems, applications, and security software up-to-date is crucial to patching vulnerabilities that attackers could exploit.
Data Encryption at Rest and in Transit
Encryption is the cornerstone of data protection. It transforms readable data (plaintext) into an unreadable format (ciphertext), protecting it from unauthorized access. This protection applies to both data at rest (stored on the endpoint’s hard drive or other storage media) and data in transit (being transmitted over a network).
- Disk Encryption: Full disk encryption (FDE) protects all data stored on an endpoint’s hard drive, even if the device is lost or stolen. Examples include BitLocker (Windows) and FileVault (macOS).
- Data Encryption in Transit: As mentioned previously, TLS/SSL and VPNs provide robust encryption for data in transit. This prevents attackers from intercepting sensitive information as it travels across the network.
- Data Loss Prevention (DLP): DLP tools monitor and control the movement of sensitive data, preventing unauthorized copying or transfer of confidential information. They can encrypt data before it leaves the endpoint.
Micro-segmentation for Endpoint Isolation
Micro-segmentation divides a network into smaller, isolated segments. This limits the impact of a compromised endpoint, preventing attackers from moving laterally to other parts of the network. If one segment is breached, the rest remain protected.
For example, a compromised workstation in the marketing segment will be prevented from accessing sensitive data in the finance segment. This containment strategy drastically reduces the potential damage from a successful attack.
Secure Endpoint Certificate and Key Management
Endpoint certificates and keys are crucial for authentication and encryption. Their security is paramount. A robust strategy for managing these elements is essential.
- Centralized Key Management: A centralized system simplifies the management of certificates and keys, allowing for easier revocation and updates. This improves overall security and reduces the risk of misconfigurations.
- Hardware Security Modules (HSMs): HSMs provide a secure hardware environment for storing and managing cryptographic keys, offering a higher level of protection against attacks.
- Regular Certificate Rotation: Regularly rotating certificates minimizes the impact of a compromised certificate. A shorter lifespan reduces the window of vulnerability.
- Automated Certificate Management: Automating certificate lifecycle management reduces the risk of human error and ensures timely renewals and revocations.
Continuous Monitoring and Improvement
Implementing a Zero Trust framework isn’t a one-time fix; it’s an ongoing process. Continuous monitoring and improvement are crucial to maintaining the effectiveness of your endpoint security posture and adapting to the ever-evolving threat landscape. This involves actively tracking the health of your endpoints, analyzing security data, and proactively updating your defenses.Continuous monitoring provides real-time visibility into the security state of your endpoints, allowing for prompt identification and remediation of vulnerabilities before they can be exploited.
This proactive approach significantly reduces the risk of breaches and minimizes potential damage. By regularly assessing and updating your security controls, you ensure your defenses remain effective against the latest threats.
Endpoint Security Posture Monitoring Implementation
Effective endpoint security posture monitoring requires a multi-faceted approach. This includes deploying endpoint detection and response (EDR) solutions, regularly scanning for vulnerabilities using automated tools, and leveraging security information and event management (SIEM) systems to collect and analyze security logs from various sources. Automated alerts for critical events, such as failed login attempts or suspicious file activity, are essential for timely response.
Regularly reviewing these alerts and investigating any suspicious activity is crucial for identifying and mitigating potential threats. Furthermore, employing vulnerability scanners to identify and prioritize patching of known weaknesses in your endpoint operating systems and applications is key to maintaining a strong security posture. Finally, the use of security configuration management tools ensures that your endpoints consistently adhere to defined security policies.
Security Log and Alert Analysis
Analyzing security logs and alerts from endpoints is vital for identifying security incidents and understanding attack patterns. This process involves collecting logs from various sources, such as operating systems, applications, and security tools. These logs should be centralized and analyzed using a SIEM system or other log management tools. The analysis should focus on identifying unusual patterns, such as a sudden surge in failed login attempts or unusual file access activity.
Correlation of events across different endpoints and systems can reveal more complex attack patterns. For example, a series of seemingly innocuous events might collectively indicate a sophisticated attack. Effective analysis requires skilled security personnel capable of interpreting log data and identifying significant security events. Prioritization of alerts based on severity and potential impact is crucial to ensure efficient incident response.
Key Performance Indicators (KPIs) for Endpoint Security
Tracking key performance indicators (KPIs) provides valuable insights into the effectiveness of your endpoint security program. Examples of important KPIs include the number of vulnerabilities identified and remediated, the mean time to detect (MTTD) and mean time to respond (MTTR) for security incidents, the percentage of endpoints compliant with security policies, and the number of successful and failed login attempts.
Monitoring these metrics allows you to identify areas for improvement and measure the overall effectiveness of your security measures. A high MTTD or MTTR indicates a need for improvements in your incident response process. A low percentage of compliant endpoints highlights areas where security policies need to be enforced more effectively. Tracking these KPIs over time allows for trend analysis, providing valuable information for continuous improvement.
For instance, a consistent increase in the number of successful phishing attempts might indicate a need for enhanced security awareness training.
Regular Security Assessments and Updates
A planned approach to regular security assessments and updates is essential for maintaining a strong endpoint security posture. This involves scheduling regular vulnerability scans, penetration testing, and security audits to identify and address weaknesses in your systems. These assessments should cover all aspects of your endpoint security, including operating systems, applications, and network configurations. Based on the findings of these assessments, necessary updates and patches should be deployed promptly.
This process should include a clear escalation path for critical vulnerabilities, ensuring timely remediation. Regular review and updates of security policies are also crucial to ensure they remain relevant and effective in the face of evolving threats. For example, a company that has recently implemented cloud-based services should update their policies to address the specific security challenges posed by this new environment.
Using SIEM Systems for Endpoint Data Analysis
Security Information and Event Management (SIEM) systems play a critical role in analyzing endpoint data. SIEM systems collect and correlate security logs from various sources, providing a centralized view of security events across your organization. This allows for the detection of anomalies and patterns that might indicate malicious activity. SIEM systems can be configured to generate alerts based on predefined rules, allowing for timely response to security incidents.
For instance, a SIEM system might alert security personnel to a large number of failed login attempts from a single IP address, indicating a potential brute-force attack. Effective use of SIEM systems requires proper configuration, including the definition of relevant rules and thresholds. The ability to effectively analyze the large volumes of data generated by SIEM systems often requires specialized skills and tools.
Sophisticated SIEM systems can employ machine learning algorithms to identify anomalies and predict potential threats. This proactive approach allows for faster detection and response to security incidents.
User Education and Training
A robust zero trust security framework is only as strong as its weakest link – the end-user. Even the most sophisticated endpoint security controls are rendered useless if employees fall victim to phishing scams or inadvertently compromise their systems through careless actions. Therefore, a comprehensive user education and training program is paramount to the success of any zero trust implementation.
This program must go beyond simple awareness campaigns and delve into practical, actionable steps that empower users to become active participants in securing their endpoints.Effective user awareness is crucial for preventing endpoint security breaches because it directly addresses the human element, a major vulnerability in any security system. Users are often the first line of defense against attacks, and their actions—or inaction—can significantly impact the overall security posture of an organization.
By educating users about potential threats and empowering them with the knowledge to recognize and respond appropriately, organizations can significantly reduce their attack surface. This proactive approach is far more effective than relying solely on technical controls.
Phishing Simulations and Security Awareness Training Modules
A multifaceted approach to user training is essential. This includes regular phishing simulations to test user susceptibility to social engineering attacks. These simulations should realistically mimic actual phishing attempts, using convincing emails and websites to gauge employee response. Post-simulation analysis should provide feedback on individual performance and highlight areas for improvement. Furthermore, interactive security awareness training modules should be implemented, covering topics such as password hygiene, recognizing malicious links and attachments, identifying suspicious emails, and understanding the importance of multi-factor authentication (MFA).
These modules can incorporate scenarios, quizzes, and gamification to enhance engagement and knowledge retention. For example, a module might present a series of emails, some legitimate and some malicious, requiring users to identify the phishing attempts. Another module might focus on password creation best practices, demonstrating the difference between weak and strong passwords and emphasizing the importance of password managers.
Communicating Security Policies and Procedures
Clearly communicating security policies and procedures to end-users is vital for ensuring compliance and fostering a security-conscious culture. This communication should be clear, concise, and easily accessible. Instead of lengthy, jargon-filled documents, organizations should opt for digestible formats such as short videos, infographics, or interactive tutorials. Regular updates and reminders are crucial, especially when new threats emerge or policies are revised.
For instance, a short video could explain the importance of MFA and demonstrate how to set it up on different devices. Infographics could highlight key security tips, such as how to identify suspicious websites or attachments. Furthermore, regular security newsletters or email updates can reinforce key messages and keep users informed about current threats. Open communication channels, such as internal forums or Q&A sessions, should be established to address user concerns and provide prompt support.
This fosters a culture of trust and collaboration, ensuring that users feel comfortable reporting suspicious activities.
Addressing Specific Endpoint Types
Zero Trust security isn’t a one-size-fits-all solution. The diverse range of endpoints in today’s organizations – from traditional laptops to increasingly prevalent IoT devices – presents unique security challenges. Successfully implementing Zero Trust requires a nuanced approach tailored to the specific vulnerabilities and access needs of each endpoint type. Failing to do so leaves significant gaps in your overall security posture.The security challenges presented by various endpoint types differ significantly, demanding distinct security controls and strategies.
Understanding these differences is critical to effectively securing your organization’s entire attack surface. A robust Zero Trust framework acknowledges these differences and adapts accordingly.
Endpoint Type Comparisons
The security challenges posed by different endpoint types vary considerably. Laptops, while relatively secure compared to other endpoint types when properly managed, are still susceptible to malware, phishing attacks, and physical theft. Desktops, often located in more controlled environments, present a slightly reduced risk but still require strong access controls and regular patching. Mobile devices, due to their portability and often less robust security features, are particularly vulnerable to loss, theft, and malware infections.
Finally, IoT devices, often lacking sophisticated security features and frequently operating on less secure networks, represent a significant threat vector, potentially acting as entry points for broader network compromises. BYOD policies, while offering employee flexibility, introduce additional complexities and potential security risks. Cloud-based endpoints, while benefiting from cloud providers’ security infrastructure, still require careful configuration and management to maintain a secure posture within a Zero Trust framework.
BYOD Security Considerations
Bring Your Own Device (BYOD) policies introduce a significant layer of complexity to endpoint security. Employees using personal devices for work access introduce risks associated with varying levels of device security, differing operating systems, and the potential for unauthorized application installations. A successful Zero Trust approach to BYOD necessitates a robust MDM (Mobile Device Management) solution, enforcing strong password policies, device encryption, and regular security updates.
Conditional access policies, based on device posture and user context, are crucial to ensure only compliant devices can access corporate resources. Clear guidelines on acceptable use and data handling are equally important to mitigate potential risks.
Cloud-Based Endpoint Security, Zero trust security how to get your endpoints ready
Cloud-based endpoints, while often leveraging the security infrastructure of cloud providers, still require specific security considerations within a Zero Trust framework. These considerations include securing access to cloud services using multi-factor authentication (MFA), implementing strong access controls, and regularly reviewing and updating security configurations. Data encryption both in transit and at rest is crucial, as is the use of cloud security posture management (CSPM) tools to monitor and improve the security posture of cloud-based resources.
Regular security audits and penetration testing should be performed to identify and address potential vulnerabilities.
Security Controls Comparison Table
| Endpoint Type | Access Control | Data Protection | Device Management | Vulnerability Management |
|---|---|---|---|---|
| Laptops | Multi-factor authentication, VPN | Full disk encryption, data loss prevention (DLP) | Endpoint detection and response (EDR), Mobile Device Management (MDM) | Regular patching, vulnerability scanning |
| Desktops | Strong passwords, access control lists (ACLs) | File-level encryption, DLP | Antivirus, EDR | Regular patching, vulnerability scanning |
| Mobile Devices | MFA, mobile device management (MDM) | Device encryption, data loss prevention (DLP) | MDM, containerization | Regular OS and app updates, mobile threat defense (MTD) |
| IoT Devices | Network segmentation, access control lists (ACLs) | Data encryption in transit and at rest | Firmware updates, secure configuration | Regular security audits, penetration testing |
| BYOD | Conditional access based on device posture, MFA | Device encryption, data separation | MDM, containerization, mobile threat defense (MTD) | Regular security assessments, user education |
| Cloud-Based Endpoints | MFA, role-based access control (RBAC) | Data encryption at rest and in transit | Cloud security posture management (CSPM) | Regular security audits, penetration testing |
Ending Remarks
Securing your endpoints under a zero trust model is a journey, not a destination. It requires a blend of technology, policy, and ongoing vigilance. By implementing the strategies discussed – from rigorous assessments and robust controls to continuous monitoring and user education – you’ll significantly reduce your attack surface and bolster your organization’s overall security posture. Remember, it’s not about achieving perfect security, but about making it exponentially harder for attackers to succeed.
So, take the first step today and start building your zero trust endpoint strategy. Your future self (and your data) will thank you!
Essential FAQs
What is the difference between Zero Trust and traditional security?
Traditional security relies on a perimeter-based approach, trusting everything inside the network. Zero Trust assumes no implicit trust and verifies every user and device before granting access, regardless of location.
How much will implementing Zero Trust cost my organization?
The cost varies greatly depending on your existing infrastructure, the size of your organization, and the specific solutions you choose. A phased approach can help manage costs.
What if my employees resist using MFA?
Strong communication and training are key. Emphasize the benefits of MFA in protecting their accounts and company data. Consider offering incentives or making it a mandatory part of company policy.
How do I choose the right EDR solution?
Consider factors like your budget, the types of endpoints you need to protect, and the level of threat detection and response capabilities required. Research different vendors and compare features.