Global Cybercrime A Rising Threat
An analysis of the rising cyber crime levels across the globe reveals a chilling reality: we’re living in a digital Wild West. Cybercrime isn’t just a tech problem anymore; it’s impacting every facet of our lives, from our finances to our national security. This isn’t just about stolen credit cards; it’s about the erosion of trust, the manipulation of information, and the very real emotional toll on victims.
We’re going to dive deep into the numbers, the motivations, and the frighteningly effective methods used by cybercriminals, exploring how this global crisis is evolving and what we can do to fight back.
This exploration will cover the alarming growth of cybercrime over the past five years, examining specific types of attacks like phishing, ransomware, and data breaches. We’ll look at who’s behind these attacks – from lone wolves to sophisticated state-sponsored actors – and the vulnerabilities they exploit. The economic and social consequences will be examined, along with the psychological impact on victims.
Finally, we’ll delve into countermeasures, prevention strategies, and the legal landscape trying to keep up with this ever-evolving threat.
Global Trends in Cybercrime
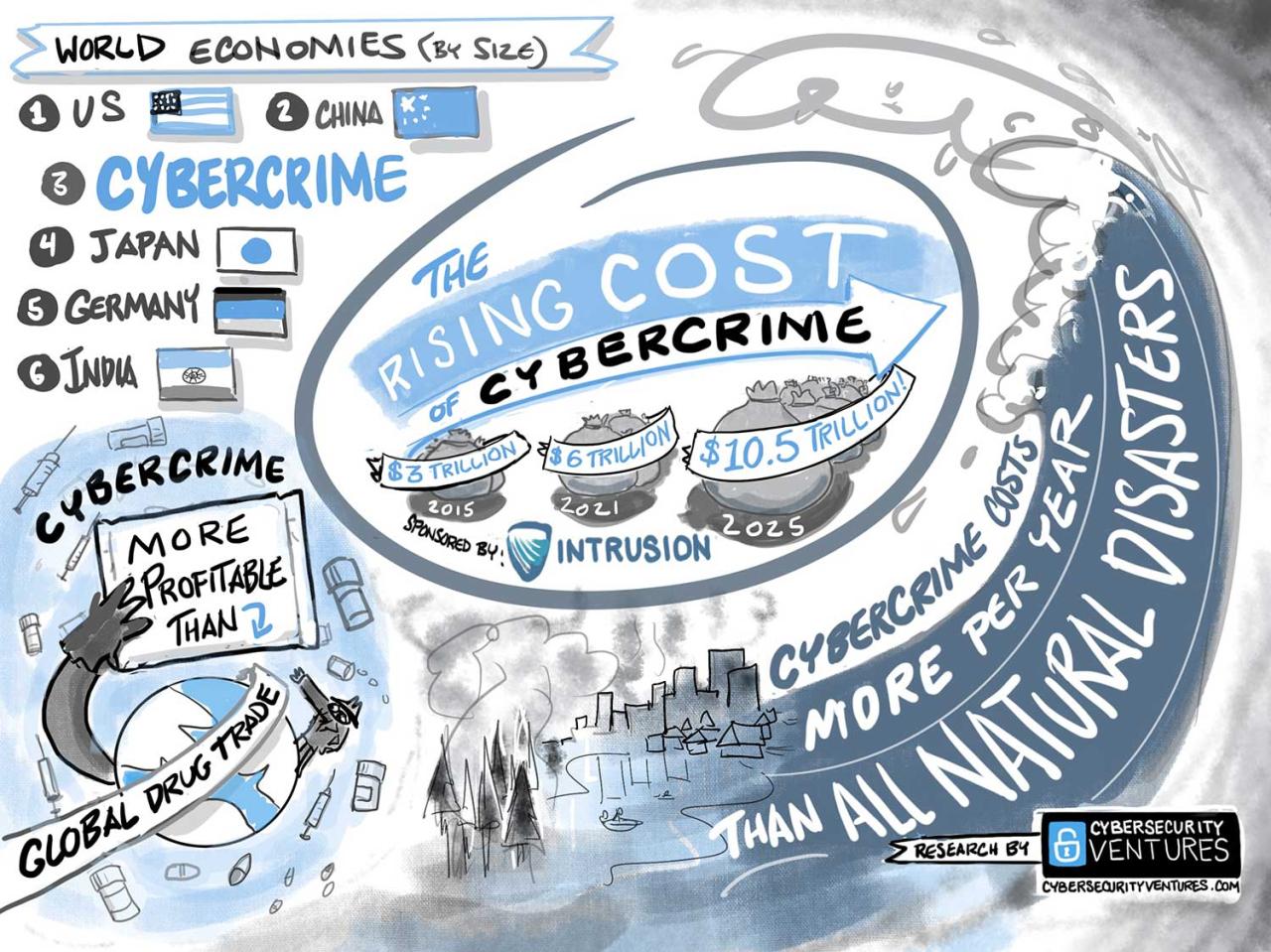
The digital landscape is rapidly evolving, and unfortunately, so is the sophistication and scale of cybercrime. Over the past five years, we’ve witnessed an alarming surge in cyberattacks, impacting individuals, businesses, and governments worldwide. This necessitates a thorough understanding of the global trends to effectively combat this growing threat.
Global Cybercrime Statistics
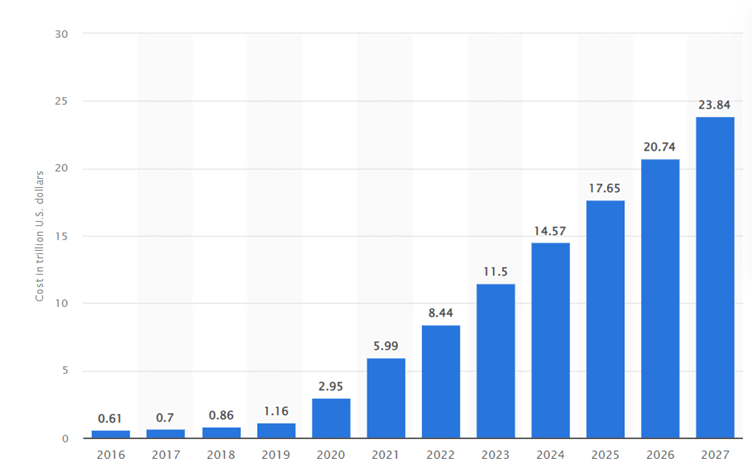
The sheer volume of cybercrime incidents and their associated financial losses are staggering. While precise figures are difficult to obtain due to underreporting and the complexity of attributing losses, available data paints a concerning picture. The following table, compiled from reports by organizations like the Cybersecurity and Infrastructure Security Agency (CISA) and Interpol, provides a glimpse into the scale of the problem.
Note that these figures represent a fraction of the actual incidents, as many go unreported.
| Year | Type of Crime | Number of Incidents (Estimate) | Estimated Financial Losses (USD) |
|---|---|---|---|
| 2019 | Ransomware | 500,000+ | Billions (unspecified) |
| 2020 | Phishing | Millions | Tens of Billions |
| 2021 | Data Breaches | Hundreds of Thousands | Hundreds of Billions |
| 2022 | Supply Chain Attacks | Tens of Thousands | Billions (unspecified) |
| 2023 (YTD) | Various (including Cryptojacking) | Millions | Hundreds of Billions |
Regional Variations in Cybercrime Prevalence
The prevalence of different cybercrime types varies significantly across regions. Several factors contribute to this, including levels of digital literacy, cybersecurity infrastructure, and legal frameworks.
For example:
- North America and Europe: Experience high rates of ransomware attacks targeting businesses, as well as sophisticated phishing campaigns aimed at individuals and organizations. Data breaches are also prevalent, often involving large corporations.
- Asia-Pacific: Witnesses a significant increase in cybercrime, particularly phishing and online fraud, driven by a large and growing online population. The region is also a hotbed for organized cybercrime syndicates.
- Africa: Faces challenges related to limited cybersecurity infrastructure and resources, making it vulnerable to various cyber threats, including financial fraud and identity theft.
- Latin America: Experiences a mix of cybercrime types, including ransomware, phishing, and financial fraud, often linked to transnational criminal organizations.
Impact of Emerging Technologies on Cybercrime
The rise of Internet of Things (IoT) devices and advancements in Artificial Intelligence (AI) are fundamentally reshaping the cybercrime landscape.
The proliferation of IoT devices, while offering convenience, creates a vast attack surface for cybercriminals. Weak security protocols in many IoT devices make them easy targets for botnet creation and distributed denial-of-service (DDoS) attacks. For instance, the Mirai botnet, which used compromised IoT devices to launch massive DDoS attacks, demonstrated the vulnerability of poorly secured connected devices.
AI, while offering potential for cybersecurity defenses, is also being weaponized by attackers. AI-powered tools can automate phishing campaigns, create more convincing social engineering tactics, and even develop sophisticated malware. The use of AI in creating deepfakes, for instance, has raised concerns about its potential misuse in identity theft and disinformation campaigns.
Motivations and Actors Behind Cybercrime
The dramatic rise in global cybercrime isn’t simply a matter of increasing technological capabilities; it’s driven by a complex interplay of motivations and the diverse actors involved. Understanding these factors is crucial to developing effective countermeasures. This section will delve into the primary drivers behind cybercriminal activity and explore the characteristics and capabilities of the various groups perpetrating these crimes.
The motivations behind cybercrime are as varied as the individuals and groups involved. While financial gain is undoubtedly the most prevalent driver, other significant factors include political activism, espionage, and even personal vendettas. The methods employed and the scale of operations, however, vary considerably depending on the actors involved.
Types of Cybercriminals and Their Motivations
Cybercriminals are not a monolithic group. They range from lone individuals operating from their bedrooms to highly sophisticated, well-funded organized crime syndicates and state-sponsored actors. Each group possesses distinct characteristics, operational methods, and resources.
- Lone Wolves: These are individuals acting independently, often driven by personal gain (e.g., financial profit from credit card fraud or ransomware attacks) or ideological motivations (e.g., defacing websites as an act of protest). Their methods are typically less sophisticated than organized groups, often relying on readily available tools and techniques found on dark web forums. They may lack the resources for large-scale attacks but can still cause significant damage to individual victims.
- Organized Crime Groups: These groups are highly structured, often operating transnationally with specialized roles and divisions of labor. Their primary motivation is financial profit, achieved through large-scale operations such as data breaches, identity theft, and the distribution of malware. They possess advanced technical skills, significant financial resources, and often utilize sophisticated techniques to evade detection and prosecution. The notorious Conti ransomware group, for example, is a prime illustration of a highly organized and financially successful cybercrime syndicate.
- State-sponsored Actors: These actors are government-backed groups, often with advanced technical capabilities and significant resources. Their motivations are typically geopolitical, involving espionage, sabotage, or information warfare. They may engage in sophisticated attacks targeting critical infrastructure, government agencies, or private companies to steal intellectual property, disrupt operations, or spread disinformation. The alleged involvement of certain nation-states in large-scale cyberattacks against other countries serves as a stark reminder of the destructive potential of state-sponsored cybercrime.
Resource and Capability Comparison
A clear disparity exists in the resources and capabilities of these different groups. Lone wolves often operate with limited resources, relying on free or readily available tools. Organized crime groups, on the other hand, often command significant financial resources, allowing them to invest in sophisticated malware development, advanced infrastructure, and skilled personnel. State-sponsored actors typically possess the most advanced capabilities, including access to cutting-edge technologies and highly trained personnel.
| Actor Type | Resources | Capabilities | Motivations |
|---|---|---|---|
| Lone Wolf | Limited financial resources, readily available tools | Basic hacking skills, limited operational reach | Financial gain, personal vendetta, ideological motivations |
| Organized Crime Group | Significant financial resources, dedicated infrastructure | Advanced hacking skills, large-scale operations, sophisticated evasion techniques | Financial gain, large-scale data theft |
| State-sponsored Actor | Extensive resources, advanced technologies, highly trained personnel | Sophisticated attacks targeting critical infrastructure, espionage, disinformation campaigns | Geopolitical objectives, espionage, information warfare |
Vulnerabilities and Targets
The ever-increasing sophistication of cyberattacks necessitates a thorough understanding of the vulnerabilities exploited and the targets most frequently affected. This knowledge is crucial for developing effective preventative measures and mitigation strategies. By examining common weaknesses and the profiles of victims, we can better understand the landscape of cybercrime and work towards a more secure digital world.
Cybercriminals exploit a wide range of vulnerabilities, leveraging weaknesses in software, human behavior, and organizational security practices. These vulnerabilities often intersect, creating complex attack vectors that are difficult to defend against. Understanding these vulnerabilities is the first step in building robust defenses.
Common Vulnerabilities Exploited by Cybercriminals
The following list categorizes the most prevalent vulnerabilities exploited by cybercriminals. These vulnerabilities represent weaknesses that attackers actively target due to their prevalence and potential for exploitation.
- Software Flaws: Outdated software, unpatched vulnerabilities, and insecure coding practices create entry points for malicious actors. Examples include known exploits in operating systems, applications, and web browsers. These flaws often allow attackers to gain unauthorized access, execute malicious code, or steal sensitive data.
- Weak Passwords and Authentication Mechanisms: Simple, easily guessable passwords, or the reuse of passwords across multiple accounts, significantly increase the risk of unauthorized access. Weak authentication mechanisms, such as easily cracked password protection or lack of multi-factor authentication, exacerbate this vulnerability.
- Human Error: Phishing attacks, social engineering, and other forms of manipulation exploit human weaknesses. Employees may inadvertently click malicious links, download infected files, or reveal sensitive information through social engineering tactics. Lack of security awareness training contributes significantly to this vulnerability.
- Network Vulnerabilities: Weak network security configurations, inadequate firewalls, and insufficient intrusion detection/prevention systems leave networks vulnerable to attacks. This includes weaknesses in routers, switches, and other network devices.
- Misconfigured Cloud Services: Improperly configured cloud storage, databases, or other cloud services can expose sensitive data or provide attackers with access to critical systems. This includes inadequate access controls, insufficient encryption, and lack of monitoring.
Frequently Targeted Organizations and Individuals
Cybercriminals target a diverse range of organizations and individuals, selecting victims based on the potential value of their data or systems. The motivations behind these attacks vary, but the common thread is the pursuit of financial gain, intellectual property theft, or disruption of operations.
My recent analysis of rising cyber crime levels globally highlighted a critical need for robust, adaptable security solutions. This is where the innovative approach of domino app dev, the low-code and pro-code future , becomes incredibly relevant; faster development cycles could mean quicker deployment of security patches and improved threat response systems, ultimately helping to combat the escalating cyber threats we face.
- Financial Institutions: Banks, credit unions, and other financial institutions are prime targets due to the vast amounts of financial data they hold. Examples include attacks aimed at stealing customer data, manipulating financial transactions, or disrupting banking operations. The 2014 Target data breach, which compromised millions of credit card numbers, is a prime example.
- Healthcare Providers: Hospitals, clinics, and other healthcare providers store sensitive patient data, making them attractive targets for cyberattacks. Examples include ransomware attacks that encrypt patient records, demanding ransom payments for their release, or data breaches exposing protected health information (PHI).
- Government Agencies: Government agencies hold sensitive information related to national security, public safety, and other critical areas. Attacks against government agencies can range from data breaches to espionage and sabotage. The 2016 US election interference, involving hacking and disinformation campaigns, is a high-profile example.
- Individuals: Individuals are targeted for various reasons, including identity theft, financial fraud, and extortion. Phishing scams, malware infections, and ransomware attacks are common methods used to target individuals.
Examples of High-Profile Cyberattacks, An analysis of the rising cyber crime levels across the globe
Several high-profile cyberattacks illustrate the techniques used and the devastating impact these attacks can have. These examples highlight the need for robust security measures and proactive threat intelligence.
- NotPetya (2017): This ransomware attack, disguised as a software update, spread rapidly through networks, causing billions of dollars in damage globally. It used a combination of exploits and social engineering to infect systems, demonstrating the power of supply chain attacks.
- SolarWinds Attack (2020): This sophisticated attack involved compromising the SolarWinds Orion software update, allowing attackers to gain access to the networks of numerous organizations, including government agencies and Fortune 500 companies. This demonstrated the effectiveness of supply chain attacks and the potential for widespread compromise.
- Colonial Pipeline Ransomware Attack (2021): This attack targeted the Colonial Pipeline, a major fuel pipeline in the US, causing widespread fuel shortages. The attackers used ransomware to encrypt the company’s systems, demanding a large ransom for their release. This highlighted the vulnerability of critical infrastructure to cyberattacks.
Economic and Social Impacts
The escalating global cybercrime landscape doesn’t just involve technological breaches; it carries profound economic and social consequences, impacting individuals, businesses, and nations alike. The financial losses are staggering, and the social disruption is far-reaching, affecting trust, security, and mental well-being. Understanding these impacts is crucial for developing effective prevention and mitigation strategies.
Economic Consequences of Cybercrime
Cybercrime inflicts significant economic damage through various channels. Remediation costs, lost productivity, and reputational harm all contribute to substantial financial losses for victims. These costs often extend beyond direct financial losses, impacting long-term business viability and investor confidence. The sheer scale of these impacts necessitates a comprehensive understanding to develop effective countermeasures.
| Impact Category | Description | Example | Estimated Cost |
|---|---|---|---|
| Remediation Costs | Expenses incurred in recovering from a cyberattack, including system restoration, data recovery, legal fees, and incident response services. | A company experiencing a ransomware attack might spend hundreds of thousands of dollars on decryption, data recovery, and legal counsel. | Varies greatly depending on the scale and type of attack; can range from thousands to millions of dollars. |
| Lost Productivity | Reduced output due to system downtime, employee time spent on recovery efforts, and disruption of business operations. | A major data breach forcing a company to shut down operations for several days to investigate and secure systems could lead to significant lost revenue and productivity. | Difficult to quantify precisely; depends on the duration and severity of the disruption. Can represent a significant portion of annual revenue for affected businesses. |
| Reputational Damage | Loss of customer trust, damaged brand image, and decreased market value following a cyberattack. | A large-scale data breach exposing customer personal information can severely damage a company’s reputation, leading to customer churn and decreased stock prices. The 2017 Equifax breach, for example, resulted in significant reputational damage and billions of dollars in losses. | Difficult to quantify directly; can result in long-term loss of revenue and market share. |
Social Implications of Cybercrime
Beyond the economic repercussions, cybercrime profoundly impacts society. The erosion of trust in online systems and institutions is a significant concern. The spread of misinformation and disinformation through cyberattacks, such as hacking social media accounts or manipulating search engine results, can destabilize social cohesion and fuel political polarization. Identity theft and fraud, enabled by cybercrime, cause significant personal distress and financial hardship for individuals.
Psychological Effects on Victims
The psychological toll of cybercrime on victims is often overlooked but is a crucial aspect of its overall impact. Victims frequently experience stress, anxiety, and depression as a result of data breaches, identity theft, or online harassment. The feeling of vulnerability and violation can be significant, leading to long-term emotional and mental health challenges. The impact is particularly acute for victims of online harassment and cyberbullying, who may experience isolation, fear, and diminished self-esteem.
Countermeasures and Prevention Strategies
The escalating tide of cybercrime necessitates a robust and multifaceted approach to prevention and mitigation. Simply reacting to attacks is no longer sufficient; proactive measures are crucial for individuals and organizations alike. This section explores the key countermeasures and strategies employed to combat this ever-evolving threat landscape.
Effective cybersecurity relies on a layered approach, combining technological solutions with robust security practices and well-trained personnel. No single solution is a silver bullet; a comprehensive strategy is essential.
Existing Cybersecurity Measures and Technologies
A range of technologies and measures are employed to detect and prevent cyberattacks. These tools, when implemented correctly and integrated effectively, form a powerful defense system.
- Firewalls: These act as gatekeepers, controlling network traffic by inspecting incoming and outgoing data packets and blocking those that violate predefined security rules. They can be hardware or software-based and form a first line of defense against unauthorized access.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic and system activity for malicious behavior, such as unauthorized access attempts or malware infections. Intrusion detection systems (IDS) alert administrators to suspicious activity, while intrusion prevention systems (IPS) can automatically block or mitigate threats.
- Encryption: This process converts data into an unreadable format, protecting it from unauthorized access even if intercepted. Encryption is crucial for protecting sensitive data both in transit (e.g., using HTTPS for website communication) and at rest (e.g., encrypting hard drives).
- Antivirus and Antimalware Software: These programs scan systems for and remove malicious software, providing an essential layer of protection against various threats. Regular updates are crucial to ensure effectiveness against the latest malware variants.
- Virtual Private Networks (VPNs): VPNs create secure connections over public networks, encrypting data and masking the user’s IP address. This is particularly useful when using public Wi-Fi networks or accessing sensitive data remotely.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events and facilitating threat detection and response.
Cybersecurity Awareness Training and Education
Technological solutions alone are insufficient. Human error remains a major vulnerability in cybersecurity. Comprehensive cybersecurity awareness training is essential to equip individuals and organizations with the knowledge and skills to identify and avoid threats.
Effective training programs should cover topics such as phishing scams, social engineering tactics, password security, malware awareness, and safe browsing practices. Regular training and reinforcement are vital, especially as new threats emerge.
Best Practices for Cyberattack Protection
Implementing best practices is crucial for both individuals and organizations to minimize their vulnerability to cyberattacks. A proactive approach is far more effective than reactive damage control.
- Strong Passwords: Use long, complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Avoid reusing passwords across different accounts.
- Multi-Factor Authentication (MFA): Enable MFA whenever possible, adding an extra layer of security by requiring multiple forms of authentication (e.g., password and a code from a mobile app).
- Regular Software Updates: Keep operating systems, applications, and antivirus software up-to-date to patch security vulnerabilities.
- Secure Wi-Fi Networks: Use strong passwords for home and office Wi-Fi networks and avoid using public Wi-Fi for sensitive tasks.
- Phishing Awareness: Be cautious of suspicious emails, links, and attachments. Verify the sender’s identity before clicking on links or opening attachments.
- Data Backup and Recovery: Regularly back up important data to a separate location, enabling recovery in case of a ransomware attack or other data loss.
- Incident Response Plan: Organizations should have a documented incident response plan outlining procedures to follow in the event of a cyberattack.
Legal and Regulatory Frameworks: An Analysis Of The Rising Cyber Crime Levels Across The Globe
The global fight against cybercrime hinges on a complex web of international and national legal frameworks. These laws aim to define cyber offenses, establish jurisdictional boundaries, and Artikel enforcement procedures. However, the rapidly evolving nature of cyber threats constantly tests the adaptability and effectiveness of these frameworks.The effectiveness of current laws and regulations in combating cybercrime varies significantly across jurisdictions.
While some nations boast robust legal frameworks and dedicated cybercrime units, others lack the resources or political will to effectively address the problem. This disparity creates loopholes that cybercriminals can exploit, often operating from regions with weaker enforcement capabilities. Furthermore, the transnational nature of cybercrime makes it difficult to prosecute offenders who operate across multiple countries. Existing laws often struggle to keep pace with the innovation in cybercriminal tactics, leading to a persistent cat-and-mouse game between law enforcement and malicious actors.
International Legal Instruments
International cooperation is crucial in combating cybercrime due to its transnational nature. Several international treaties and conventions aim to facilitate this cooperation. The Budapest Convention on Cybercrime, for example, provides a framework for international cooperation in investigating and prosecuting cybercrimes, including offenses such as computer-related fraud, data theft, and child pornography. However, the effectiveness of these instruments depends on the willingness of signatory states to actively implement and enforce their provisions.
Furthermore, the lack of universal ratification and varying levels of enforcement across countries remain significant challenges. For instance, while the Budapest Convention has many signatories, the implementation and enforcement differ significantly across countries due to varying legal systems and resources.
National Cybercrime Laws
National laws vary widely in their scope and effectiveness. Some countries have comprehensive cybercrime laws that address a broad range of offenses, while others have more limited legislation. These national laws often mirror aspects of the Budapest Convention, incorporating provisions for offenses such as hacking, data breaches, and cyber fraud. However, differences in legal definitions, evidentiary standards, and enforcement mechanisms can create inconsistencies and challenges in cross-border investigations and prosecutions.
For instance, a data breach that occurs in one country might be prosecuted under different laws and with varying penalties in another. This complexity adds a significant hurdle to effective international cooperation.
Challenges in Cross-Border Enforcement
Enforcing cybercrime laws across borders presents significant challenges. Identifying and locating offenders who operate anonymously online is often difficult. Gathering evidence that is admissible in multiple jurisdictions can be complex and time-consuming. Furthermore, securing the cooperation of foreign law enforcement agencies is often necessary but not always easily achieved due to differences in legal systems, investigative practices, and political considerations.
For example, obtaining data from servers located in a foreign country may require complex legal processes and diplomatic negotiations, significantly hindering investigations. The lack of standardized procedures and mutual legal assistance treaties further exacerbates these challenges, often resulting in delays and obstacles in the pursuit of justice.
Concluding Remarks
The escalating global cybercrime crisis demands immediate and concerted action. While the challenges are immense – from the sheer scale of the problem to the constantly shifting tactics of cybercriminals – there’s reason for cautious optimism. Increased awareness, proactive security measures, and stronger international cooperation are crucial in mitigating the threat. The fight against cybercrime isn’t just about technology; it’s about collective responsibility, education, and a commitment to building a safer digital future.
The future of online security depends on our willingness to learn, adapt, and fight back.
FAQ Summary
What is the most common type of cybercrime?
Phishing remains one of the most prevalent forms of cybercrime, often serving as an entry point for more sophisticated attacks.
How can I protect myself from cybercrime?
Use strong, unique passwords, enable two-factor authentication, be wary of suspicious emails and links, keep your software updated, and regularly back up your data.
What role does the government play in combating cybercrime?
Governments play a vital role in establishing legal frameworks, supporting cybersecurity research, and collaborating internationally to prosecute cybercriminals and share intelligence.
What is the future of cybercrime?
As technology continues to evolve, so will cybercrime. Expect to see more sophisticated attacks leveraging artificial intelligence and the Internet of Things (IoT).