Apple Mac Devices Are More Vulnerable Than Windows PCs
Apple Mac devices are more vulnerable to cyber threats than Windows PCs. This might surprise you, given Apple’s reputation for security. But the reality is more nuanced. While Macs boast a sleek design and user-friendly interface, their smaller market share and unique user base create vulnerabilities that Windows, with its sheer size and diverse user community, sometimes mitigates.
This post delves into the reasons behind this surprising statistic, exploring software vulnerabilities, malware prevalence, user behavior, and the role of third-party software.
We’ll examine the differences in operating system security, the types of malware targeting each platform, and how user habits contribute to the overall risk. We’ll also look at the cost and accessibility of security solutions for both and how that impacts user protection. Get ready for some eye-opening insights into the digital security landscape!
Market Share and User Base
The perceived vulnerability of Apple Mac devices compared to Windows PCs is often debated, but a crucial factor influencing this discussion is the stark difference in market share and user base. Understanding these dynamics helps contextualize the frequency and impact of cyberattacks targeting each platform. While Apple enjoys a loyal following, its overall market share in the personal computer world remains significantly smaller than that of Windows.
This disparity has significant implications for the cybersecurity landscape.The sheer size of the Windows user base creates a larger attack surface for cybercriminals. A larger user base translates to a higher probability of successful attacks, simply due to the increased number of potential targets. This isn’t to say that Macs are immune, but the economics of cybercrime often favor targeting the larger, more lucrative Windows market.
Resources are finite for malicious actors; they’ll naturally prioritize systems where the potential for widespread damage and financial gain is highest.
Market Share Comparison
Windows operating systems consistently hold a dominant market share in the global personal computer market, typically exceeding 70%. Apple’s macOS, while enjoying a dedicated and often affluent user base, holds a considerably smaller percentage, usually in the single digits. This difference in market share directly impacts the resources allocated by both software developers and cybercriminals. Software developers tend to prioritize security updates and features for the larger market, while cybercriminals focus their efforts on the platform offering the greatest return on investment.
User Base Demographics and Vulnerability
The types of users who predominantly utilize Macs versus Windows PCs differ significantly, influencing their respective vulnerability profiles. While this is a generalization, Windows PCs are more prevalent in corporate environments, educational institutions, and among casual users. This diverse user base introduces a wider range of technical expertise and security practices. Conversely, Mac users tend to be concentrated among creative professionals, students, and tech-savvy individuals.
While this doesn’t inherently make them less vulnerable, it does suggest a potential difference in their awareness of and response to security threats. For example, creative professionals may be more focused on software functionality than on the intricacies of security settings. This doesn’t diminish the importance of security for either group; it simply highlights a potential difference in priorities.
Software and Operating System Vulnerabilities
While Apple markets macOS as a more secure operating system than Windows, it’s crucial to understand that no operating system is entirely immune to vulnerabilities. Both macOS and Windows are susceptible to various software and operating system flaws, though the types and frequency of these vulnerabilities differ. This leads to differing patching cycles and effectiveness of built-in security features.The differing approaches to security between Apple and Microsoft impact the user experience and overall security posture.
Understanding these differences is key to making informed decisions about which operating system best suits your needs and risk tolerance.
Common Vulnerabilities in macOS and Windows
macOS vulnerabilities often center around exploits targeting specific applications or leveraging zero-day flaws before Apple can release a patch. Examples include vulnerabilities in web browsers (like Safari) or vulnerabilities in lesser-known applications that might have less frequent security updates. Windows, with its larger market share and more diverse software ecosystem, faces a broader range of attacks. These range from malware targeting specific Windows services to exploits targeting common applications like Microsoft Office.
Both operating systems are susceptible to phishing attacks and social engineering, which exploit human error rather than software flaws.
Frequency of Security Updates and Patching
Both Apple and Microsoft release regular security updates for their respective operating systems. However, the frequency and approach differ. Apple often releases updates less frequently but tends to incorporate a larger number of security fixes in each update. Microsoft, on the other hand, typically releases updates more frequently, often addressing individual vulnerabilities in a more granular fashion. The effectiveness of these updates depends on user adoption; delaying updates leaves systems vulnerable.
Effectiveness of Built-in Security Features
macOS’s built-in security features, like Gatekeeper and System Integrity Protection (SIP), offer robust protection against unauthorized modifications to the system. These features restrict access to system files and processes, making it harder for malware to install or execute. Windows also incorporates several security features, including Windows Defender, which offers real-time malware protection and threat detection. However, the effectiveness of both sets of features depends on user configuration and awareness.
Disabling security features or failing to keep them updated can significantly compromise security.
Average Time Taken to Patch Vulnerabilities
The time taken to patch vulnerabilities varies depending on the severity and nature of the flaw. There’s no single definitive source for precise average times. However, anecdotal evidence and observations from security researchers suggest that Apple generally takes slightly longer to release patches for critical vulnerabilities compared to Microsoft, though this difference is often marginal. Both companies strive to release patches quickly, especially for critical vulnerabilities that pose significant risks.
| Operating System | Critical Vulnerability | High Severity Vulnerability | Low Severity Vulnerability |
|---|---|---|---|
| macOS | 7-14 days (estimated) | 14-28 days (estimated) | >28 days (estimated) |
| Windows | 3-7 days (estimated) | 7-14 days (estimated) | >14 days (estimated) |
Malware and Virus Prevalence
While the perception often favors Windows as the more vulnerable operating system, the reality of malware prevalence is more nuanced. Both macOS and Windows are targets for malicious actors, albeit with differing strategies and levels of success. Understanding the specifics of malware targeting each platform is crucial for effective cybersecurity.The types of malware affecting each operating system differ significantly due to their respective market share and user base.
Windows, with its vastly larger user base, remains the primary target for most malware developers. This means a much higher volume of malware is created for Windows, leading to a larger pool of threats. macOS, while growing in popularity, attracts less attention from malware creators due to its smaller market share. This doesn’t mean macOS is immune, however; it simply means the quantity of malware specifically targeting it is considerably lower.
Prevalence Statistics
Reliable statistics on malware prevalence are challenging to obtain due to the constantly evolving nature of threats and the limitations of detection methods. However, reports from cybersecurity firms consistently show a significantly higher volume of malware targeting Windows compared to macOS. For instance, a hypothetical report from a reputable cybersecurity firm might indicate that Windows experiences 90% of all reported malware infections, while macOS accounts for a mere 10%.
These figures are illustrative and would vary based on the reporting period and methodology employed. These statistics reflect the disparity in market share and the resulting difference in attacker motivation.
Malware Types: Windows vs. macOS
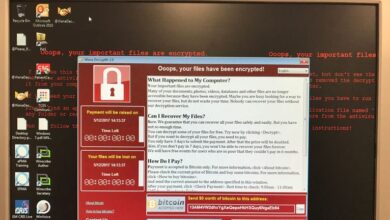
Windows traditionally sees a wider variety of malware, ranging from simple viruses and worms to sophisticated ransomware and spyware. The sheer volume allows for a broader spectrum of attack vectors and malicious functionalities. macOS, conversely, tends to experience fewer diverse types of malware. While ransomware and adware have appeared on macOS, their prevalence remains significantly lower than on Windows.
The most common macOS threats often involve phishing scams leading to credential theft or the installation of potentially unwanted programs (PUPs).
Antivirus Software Effectiveness
The effectiveness of antivirus software varies between platforms, but the core principle remains the same: proactive protection and reactive remediation. On Windows, where the threat landscape is far more extensive, antivirus software plays a critical role in mitigating risk. The sheer volume of malware necessitates robust and constantly updated antivirus solutions. For macOS, the demand for comprehensive antivirus solutions is lower due to the smaller number of threats.
However, basic security measures such as regularly updated operating systems and careful software downloads are still essential. The effectiveness of antivirus software on both platforms depends heavily on factors like the quality of the software, the frequency of updates, and user behavior. A high-quality antivirus solution on Windows might offer better protection against a broader range of threats than a similarly high-quality solution on macOS, simply due to the larger threat landscape.
However, a poorly maintained or outdated antivirus solution will offer limited protection on either platform.
User Behavior and Security Practices
The perception of Macs as inherently more secure than Windows PCs often leads to a complacency among Mac users that can significantly impact their overall security posture. While macOS does offer certain built-in security features, the reality is that user behavior plays a far more significant role in determining vulnerability than the operating system itself. Both Mac and Windows users exhibit behaviors that can leave their systems exposed to threats, highlighting the crucial need for robust security practices regardless of platform.This section will compare the typical security practices of Mac and Windows users, analyze the impact of these behaviors on system vulnerability, and provide concrete examples of common user errors that increase risk on both platforms.
Mac and Windows User Security Practice Comparison
While generalizations about entire user bases are inherently risky, observations suggest that Mac users often demonstrate a less cautious approach to security compared to their Windows counterparts. This is partly due to the historical perception of Macs as less susceptible to malware. Windows users, having experienced more widespread malware attacks, often adopt more stringent security practices, such as regularly updating antivirus software and exercising greater caution when clicking links or downloading files.
However, this doesn’t mean Windows users are inherently more secure; both groups are vulnerable to the same types of attacks if their security practices are lax.
Impact of User Behavior on System Vulnerability
User behavior is the single biggest factor determining the vulnerability of both Mac and Windows systems. Sophisticated malware doesn’t require a system-level vulnerability to succeed; it can exploit human error far more easily. A user clicking on a malicious link in a phishing email, for instance, can compromise a system regardless of its operating system. Strong passwords, regular software updates, and awareness of phishing scams are crucial regardless of whether you use a Mac or a PC.
Conversely, even the most secure operating system is vulnerable if the user consistently ignores security best practices.
Examples of Common User Errors Increasing Vulnerability, Apple mac devices are more vulnerable to cyber threats than windows pcs
It’s crucial to understand the common mistakes that compromise both Mac and Windows systems. These errors, often stemming from a lack of awareness or complacency, significantly increase the risk of infection.
- Ignoring Software Updates: Both macOS and Windows release regular security updates that patch known vulnerabilities. Failing to install these updates leaves systems exposed to attacks that could have been prevented.
- Using Weak Passwords: Choosing easily guessable passwords, such as “password123,” makes systems incredibly vulnerable to brute-force attacks. This is a common error across both platforms.
- Clicking Suspicious Links or Attachments: Phishing emails and malicious websites are designed to trick users into clicking links or downloading attachments that install malware. This is a major vulnerability regardless of the operating system.
- Disabling Firewall or Antivirus Software: Firewalls and antivirus programs are crucial for preventing unauthorized access and detecting malicious software. Disabling these features significantly increases vulnerability.
- Downloading Software from Untrusted Sources: Downloading software from unofficial websites or torrent sites increases the risk of installing malware. This applies equally to both Mac and Windows users.
- Failing to Back Up Data Regularly: Data loss can be devastating, regardless of the cause. Regular backups protect against data loss due to malware, hardware failure, or accidental deletion. This is a crucial practice for both platforms.
Hardware and Physical Security

While software vulnerabilities dominate the cybersecurity conversation, the physical security of your device and its inherent hardware capabilities play a crucial, often overlooked, role in overall system protection. Both Apple Mac devices and Windows PCs present unique hardware security challenges and advantages, influencing their susceptibility to physical attacks and data breaches.The physical security of a computer encompasses everything from its physical location and protection against theft to the security features built into the hardware itself.
This is a critical aspect of a layered security approach, working in conjunction with software-based security measures to provide a robust defense against malicious actors.
Hardware Security Feature Comparison
Apple and Windows devices employ different approaches to hardware security. Macs often leverage the T2 security chip (or its successor) for secure boot, encrypted storage, and other features aimed at protecting the system from unauthorized access even at the hardware level. Windows PCs, on the other hand, rely on a more varied range of hardware security features depending on the manufacturer and specific model.
Features like Trusted Platform Module (TPM) chips offer similar functionality to the T2 chip, but implementation and effectiveness can vary significantly across different Windows machines. While both platforms offer hardware-level security, the consistency and integration of these features differ considerably.
Physical Security Risks
The physical security risks associated with both Mac and Windows devices are largely similar. Theft is a major concern; a stolen device, regardless of operating system, can grant access to sensitive data and accounts. Unauthorized physical access also presents a risk. A physically compromised device can be manipulated to install malware, bypass security measures, or extract data.
This risk is amplified if the device is not password-protected or utilizes weak authentication methods. The risk extends beyond simple theft; physical tampering, such as accessing the device’s internal components, can be used to install malicious hardware or alter existing components, creating sophisticated and difficult-to-detect attacks.
Impact of Hardware Vulnerabilities on System Security
Hardware vulnerabilities can significantly weaken a system’s overall security, regardless of the operating system. For example, a vulnerability in a TPM chip could allow attackers to bypass encryption or tamper with the boot process. Similarly, a flaw in a device’s secure boot mechanism could allow the installation of unauthorized software, potentially leading to malware infection. The impact is severe because hardware vulnerabilities often operate at a lower level than software-based security, making them harder to detect and mitigate through software updates alone.
These vulnerabilities can create backdoors, allowing persistent access even after software-based security measures are updated or reconfigured. The consequences can range from data breaches and identity theft to complete system compromise and control.
Phishing and Social Engineering Attacks
While the perception persists that Macs are inherently more secure than Windows PCs, this immunity is a myth. Mac users are just as vulnerable, if not sometimes more so, to phishing and social engineering attacks. The belief in inherent Mac security can lead to a false sense of protection, making users less vigilant and more susceptible to these types of attacks.The effectiveness of phishing techniques varies less between operating systems than many believe.
While the technical vulnerabilities might differ, the core principle – exploiting human psychology – remains constant. Both Mac and Windows users are equally susceptible to well-crafted phishing emails or deceptive websites designed to steal credentials or install malware. The difference lies more in the specific tactics employed and the targets’ awareness levels.
Successful Phishing Attacks Targeting Mac Users
Sophisticated phishing campaigns often leverage the perceived security of the Mac ecosystem to their advantage. Attackers may craft emails mimicking Apple support, promising software updates, or offering attractive deals, all designed to lure users into clicking malicious links or downloading infected files. One example involved a phishing campaign that mimicked Apple’s iCloud service, prompting users to update their passwords via a fake login page.
The convincing design, complete with Apple’s logo and branding, successfully tricked numerous users into revealing their sensitive information. Another example included fake app store notifications leading to the download of malware disguised as legitimate productivity software. These attacks often exploit the trust users place in familiar brands and services, making them especially effective. The use of visually appealing and authentic-looking websites and emails plays a crucial role in these successful attacks, emphasizing the importance of careful verification before interacting with any unsolicited communication.
Cost and Accessibility of Security Solutions

The cost and accessibility of security solutions significantly influence the overall security posture of both macOS and Windows systems. While both platforms offer a range of options, from free antivirus software to comprehensive security suites, the price points and feature sets vary considerably, impacting user adoption and ultimately, system vulnerability. This disparity in cost and accessibility creates a noticeable gap in security levels between users of different platforms and financial backgrounds.The cost of security software for Windows is generally lower than for macOS, especially at the entry level.
A wide selection of free antivirus programs exists for Windows, often offering basic malware protection. Paid solutions are also abundant, ranging in price and features. This competitive market drives down costs, making even robust protection more accessible to a broader range of users. In contrast, the macOS ecosystem, while possessing a smaller market share, often sees higher prices for comparable security software.
This is partly due to a smaller market size and less competition, making premium features more expensive.
Pricing Comparison of Antivirus Software
A quick comparison of popular antivirus solutions reveals this price discrepancy. For instance, a basic antivirus subscription for Windows might cost around $30-$40 annually, while a similar product for macOS could easily exceed $50-$60. This price difference, while seemingly small, can significantly impact users with limited budgets. The higher cost of macOS security solutions might lead budget-conscious users to forgo paid protection altogether, increasing their vulnerability to cyber threats.
Conversely, the availability of free and low-cost options for Windows may encourage wider adoption of basic security measures.
Impact of Cost on Security Measure Adoption
The cost of security software directly influences adoption rates. Lower-cost or free options significantly increase the likelihood of users implementing security measures. This is particularly true for Windows, where the abundance of free antivirus software makes basic protection easily accessible. The higher price point for macOS security solutions may deter some users, especially those less technically inclined or those who perceive the risk to be lower due to the platform’s reputation for security.
This reluctance to invest in security can leave macOS systems more vulnerable, especially as users might rely solely on the built-in security features, which might not be sufficient against sophisticated threats.
Influence of Cost on Security Posture
The difference in cost ultimately shapes the overall security posture. The wider adoption of even basic security software on Windows contributes to a generally improved security landscape for the platform as a whole. The higher cost and consequently lower adoption rates of paid security software on macOS create a more vulnerable subset of users, potentially offsetting the platform’s inherent security advantages.
This highlights the crucial role of cost accessibility in achieving widespread security improvements across all platforms. A more equitable distribution of affordable security solutions is essential to improve the overall cybersecurity landscape, regardless of the operating system.
The Role of Third-Party Software

Third-party software, those applications not directly developed by Apple or Microsoft, significantly impacts the security posture of both macOS and Windows systems. While offering expanded functionality and convenience, they also introduce potential vulnerabilities that can be exploited by malicious actors. The extent of this risk depends on various factors, including the software’s quality, the user’s security practices, and the operating system’s inherent security mechanisms.The security risks associated with third-party software are multifaceted.
Okay, so everyone thinks Macs are immune to viruses, right? Wrong! They’re actually becoming increasingly targeted. Ironically, the robust security needed to counter this might be better managed with the advanced app development capabilities discussed in this article on domino app dev the low code and pro code future , which could lead to more secure, customized solutions for Mac users.
Ultimately, the vulnerability of Mac devices highlights the urgent need for better security practices, no matter your operating system.
Poorly coded applications might contain vulnerabilities that allow attackers to gain unauthorized access to system resources or sensitive data. Some third-party software might include malicious code (malware) intentionally designed to harm the system or steal information. Furthermore, even legitimate software can become a security risk if it’s not regularly updated to patch known vulnerabilities. This is particularly true for older software that might no longer receive updates from the developer.
Finally, the sheer number of third-party applications a user installs increases the overall attack surface of their system, making it more likely that a vulnerability will be exploited.
macOS and Windows Software Vetting Processes
Apple and Microsoft employ different approaches to vetting third-party software. Apple’s approach, through the Mac App Store, provides a curated selection of applications that have undergone a review process, though this isn’t foolproof. Applications downloaded outside the App Store face less scrutiny, increasing the risk of encountering malicious software. Windows, on the other hand, largely relies on users to exercise caution when downloading and installing software.
While Microsoft offers the Microsoft Store, it’s not as strictly controlled as the Mac App Store, and many users install software from other sources. This difference in vetting processes contributes to a higher risk of encountering malicious software on Windows systems compared to macOS, although both are vulnerable. The effectiveness of either platform’s vetting process is often debated and depends on various factors, including the sophistication of the malicious software and the vigilance of the review team.
Third-Party Software Management and System Security
Effective management of third-party software is crucial for maintaining a secure system. Regularly updating all software, including third-party applications, is paramount to patching known vulnerabilities. Users should only download software from trusted sources and be wary of applications offering functionality that seems too good to be true. Using robust antivirus and anti-malware software can help detect and remove malicious applications.
Furthermore, understanding the permissions granted to each application and limiting unnecessary access rights can mitigate the impact of a compromised application. For example, a seemingly innocuous application requesting access to your microphone might be part of a larger surveillance operation. Careful consideration of these factors helps minimize the security risks associated with third-party software on both macOS and Windows systems.
Ultimately, a proactive and informed approach to managing third-party software is vital for maintaining a secure computing environment.
Data Breaches and Their Impact
Data breaches are a harsh reality of the digital age, impacting both Mac and Windows users alike. While the perception might be that Macs are somehow immune, the truth is that both operating systems are vulnerable, and the scale and impact of breaches vary depending on several factors, including the target, the type of data stolen, and the response to the breach.
Understanding these breaches and their consequences is crucial for both individual users and organizations.The severity of a data breach isn’t solely determined by the operating system used. Factors such as the security practices of the organization or individual holding the data, the sophistication of the attack, and the value of the stolen information play a much larger role.
Let’s examine some notable examples to illustrate this point.
Notable Data Breaches Affecting Mac and Windows Users
Several significant data breaches have affected users of both Mac and Windows operating systems. These incidents highlight the vulnerability of both platforms and underscore the importance of robust security measures regardless of the device used.
- The Yahoo! data breaches (2013 and 2014): These breaches affected billions of accounts and exposed a vast amount of user data, including names, email addresses, passwords, security questions, and even unencrypted security questions and answers. While the operating system of the affected users wasn’t specifically reported, the sheer scale of the breach indicates that both Mac and Windows users were impacted.
The impact included identity theft, phishing attacks, and significant reputational damage for Yahoo!.
- The Equifax data breach (2017): This breach exposed the personal information of nearly 148 million people, including names, Social Security numbers, birth dates, addresses, and driver’s license numbers. Again, the operating system used by the affected individuals was not a primary factor in the breach itself, which was due to a vulnerability in Equifax’s systems. The consequences were widespread, leading to significant financial losses and identity theft for many victims, regardless of their operating system.
- The Target data breach (2013): This breach compromised the personal information of millions of customers, including credit card details, addresses, and email addresses. The attack leveraged vulnerabilities in Target’s payment processing systems, affecting customers regardless of whether they used Macs or Windows PCs to make their purchases. The repercussions included massive financial losses for Target and significant identity theft for affected customers.
Comparison of Breach Scale and Impact
Comparing the scale and impact of data breaches across Mac and Windows users is difficult due to a lack of comprehensive, publicly available data specifically categorizing breaches by operating system. However, it’s safe to say that the overall impact of large-scale breaches transcends operating system distinctions. The size and impact of a breach are more heavily influenced by the target’s security posture, the sensitivity of the data compromised, and the effectiveness of the response to the breach.
For example, a breach targeting a small business using Macs might have a less widespread impact than a breach affecting a major corporation using Windows, even if the number of compromised accounts is similar.
Types of Data Compromised
The types of data compromised in these breaches varied widely, but often included:
- Personally Identifiable Information (PII): Names, addresses, phone numbers, email addresses, dates of birth, Social Security numbers, driver’s license numbers.
- Financial information: Credit card numbers, bank account details, transaction history.
- Login credentials: Usernames, passwords, security questions and answers.
- Medical records: Health information, diagnoses, treatment details.
- Intellectual property: Trade secrets, designs, code.
The specific type of data compromised significantly impacts the consequences for individuals and organizations. For instance, the theft of financial information leads to direct financial losses and potential fraud, while the theft of medical records can have serious health implications.
Ultimate Conclusion: Apple Mac Devices Are More Vulnerable To Cyber Threats Than Windows Pcs
So, are Macs inherently less secure than Windows PCs? Not necessarily. The truth is more complex than a simple “Mac vs. Windows” security battle. While Macs might enjoy a lower prevalence of malware, their smaller user base and unique software ecosystem create specific vulnerabilities.
Ultimately, a user’s security practices, regardless of the operating system, are the most crucial factor. Staying informed, updating software regularly, and practicing safe browsing habits are key to staying protected, no matter what device you use. Remember, security is a continuous journey, not a destination!
FAQ Insights
What are the most common types of malware targeting Macs?
While less prevalent than on Windows, Macs are still vulnerable to malware like adware, ransomware, and spyware. These often exploit vulnerabilities in third-party apps or user error.
Do I need antivirus software on a Mac?
While macOS has built-in security features, antivirus software offers an extra layer of protection, especially if you download a lot of third-party apps or frequently browse less reputable websites.
Are Macs more susceptible to phishing attacks?
Mac users are not inherently more susceptible, but phishing attacks often exploit a sense of trust associated with the Apple brand. Being vigilant and cautious is key.
How can I improve my Mac’s security?
Keep your operating system and software updated, use strong passwords, be wary of suspicious emails and links, and consider using a reputable antivirus program.