Automating the API Security Lifecycle An Interview with Subbu Iyer
Automating the api security lifecycle an interview with subbu iyer of cequence security – Automating the API Security Lifecycle: An Interview with Subbu Iyer of Cequence Security – API security is a HUGE deal right now. Everyone’s building APIs, but are they secure? This interview dives deep into automating the entire security lifecycle, from testing to incident response, and gets the inside scoop from Subbu Iyer, a leading expert in the field.
We’ll explore the challenges, the solutions, and the future of API security automation.
We’ll cover everything from the basics of API security and its lifecycle to advanced techniques like integrating automated testing into CI/CD pipelines. Subbu shares practical implementation strategies, insights into Cequence Security’s approach, and even predicts future trends. Get ready for a deep dive into securing your APIs – because let’s face it, nobody wants a data breach!
Introduction to API Security and its Lifecycle
APIs (Application Programming Interfaces) are the backbone of modern software, facilitating communication between different applications and systems. However, the increasing reliance on APIs also exposes organizations to significant security risks. Understanding the API security lifecycle and the challenges involved is crucial for building robust and secure applications.The API security lifecycle encompasses a series of stages, from design and development to deployment and monitoring.
Effective API security requires a holistic approach that addresses vulnerabilities throughout this entire lifecycle.
Stages of the API Security Lifecycle
The API security lifecycle typically includes these key stages:
- Design and Planning: This initial phase involves defining security requirements, identifying potential threats, and selecting appropriate security controls. This might include choosing strong authentication methods, defining authorization policies, and implementing input validation techniques.
- Development and Implementation: This stage focuses on building the API according to the security specifications defined in the design phase. Secure coding practices, such as using parameterized queries to prevent SQL injection, are essential.
- Testing and Validation: Thorough testing is critical to identify and address vulnerabilities before deployment. This includes static and dynamic application security testing (SAST and DAST), penetration testing, and security audits.
- Deployment and Monitoring: Once the API is deployed, continuous monitoring is crucial to detect and respond to potential threats. This includes real-time threat detection, security information and event management (SIEM), and intrusion detection systems.
- Incident Response: Despite best efforts, security incidents can still occur. A well-defined incident response plan is crucial for minimizing the impact of such events. This includes procedures for identifying, containing, eradicating, recovering from, and learning from security incidents.
Challenges in Securing APIs
Organizations face numerous challenges in securing their APIs, including:
- The growing number of APIs: Many organizations have hundreds or even thousands of APIs, making it difficult to manage and secure them all effectively. This sprawl can lead to vulnerabilities being missed or overlooked.
- The complexity of API architectures: Modern API architectures are often complex and distributed, making it difficult to identify and address security vulnerabilities. Microservices architectures, for example, introduce a higher level of complexity.
- Lack of visibility and control: Organizations often lack sufficient visibility into their API traffic and usage, making it difficult to detect and respond to security threats. This is exacerbated by the use of third-party APIs.
- Rapid pace of development: The fast-paced nature of software development can lead to security being overlooked or compromised in the rush to release new features and updates.
- Skills gap: A shortage of skilled security professionals makes it difficult for organizations to effectively secure their APIs.
Impact of Inadequate API Security
Inadequate API security can have severe consequences for businesses, including:
- Data breaches: Compromised APIs can expose sensitive customer data, leading to significant financial losses and reputational damage. The Equifax data breach, for instance, resulted from a vulnerability in an API.
- Financial losses: Data breaches and other security incidents can lead to significant financial losses due to regulatory fines, legal fees, and remediation costs.
- Reputational damage: Security incidents can severely damage a company’s reputation, leading to loss of customer trust and business.
- Compliance violations: Failure to comply with relevant data protection regulations can result in hefty fines and legal penalties.
- Disruption of services: API attacks can disrupt critical business operations, leading to significant financial losses and operational downtime. A denial-of-service attack on an API could render an entire application unusable.
Automating API Security Testing
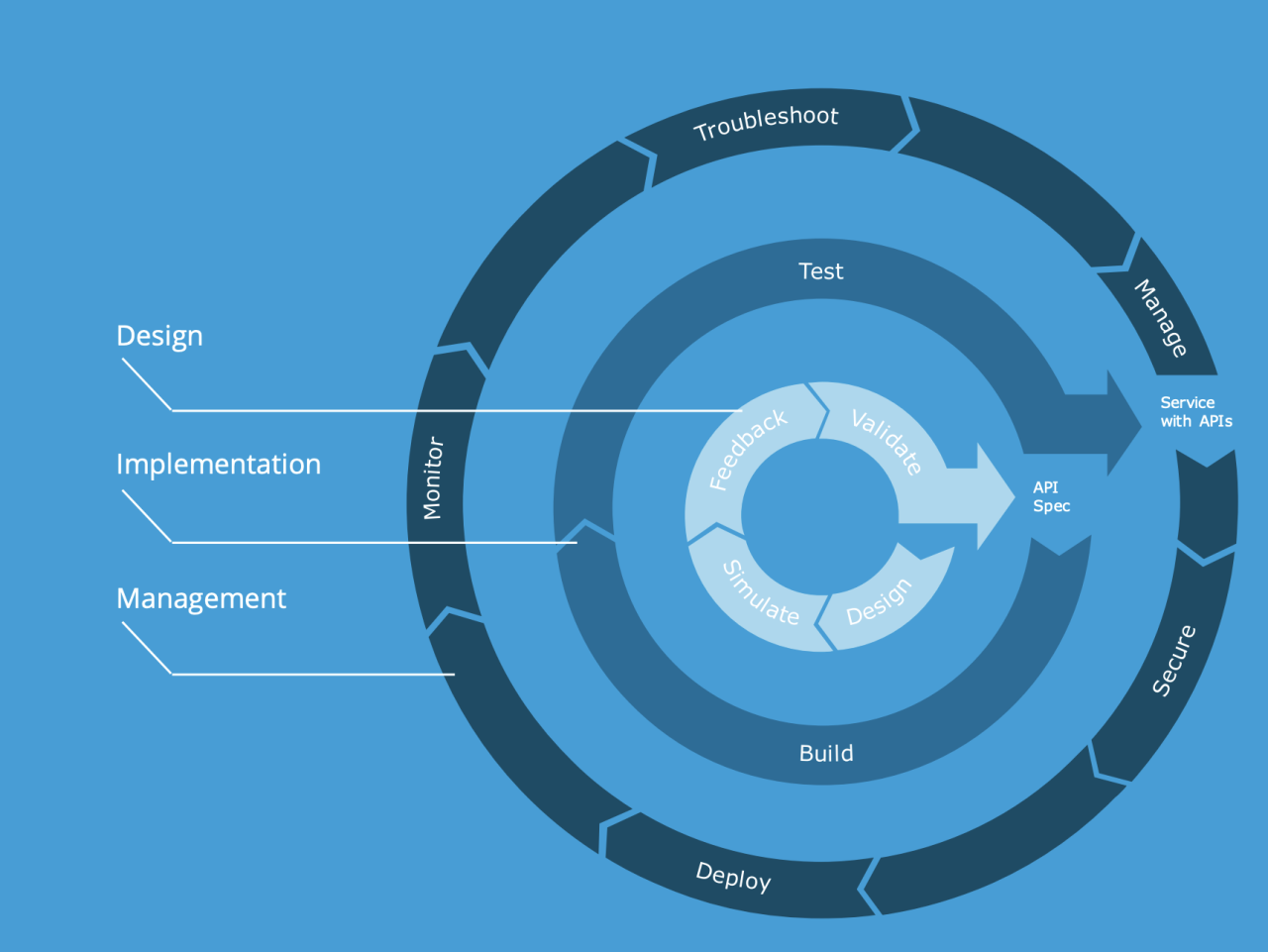
Automating API security testing is crucial in today’s fast-paced development cycles. Manual testing is simply too slow and prone to human error to keep up with the frequency of API deployments. Automation allows for consistent, comprehensive security checks, catching vulnerabilities before they reach production and potentially expose sensitive data or compromise system integrity. This increased efficiency and accuracy significantly reduce the risk associated with API breaches.
Automating API security testing involves integrating automated tools and techniques into your software development lifecycle (SDLC), specifically within the CI/CD pipeline. This allows for continuous security validation alongside functional testing, resulting in faster feedback loops and improved overall security posture.
Automated API Security Testing Tools and Techniques
Several tools and techniques facilitate automated API security testing. These range from commercial solutions offering comprehensive features to open-source tools providing specific functionalities. Effective automation often involves a combination of approaches to cover a broad spectrum of vulnerabilities.
Examples of automated API security testing tools include:
- PortSwigger Burp Suite: A comprehensive platform offering various features, including automated scanning for vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication.
- OWASP ZAP: An open-source tool providing similar functionality to Burp Suite, ideal for organizations seeking a cost-effective solution. It offers automated scans and manual testing capabilities.
- Salt Security: A commercial solution specializing in API security, offering features like runtime protection and vulnerability detection.
- Astra Pentest: Another commercial option offering automated API security testing, along with features for vulnerability management and remediation.
Techniques employed include:
- Static Application Security Testing (SAST): Analyzing the API’s source code for vulnerabilities without executing the code. This helps identify potential issues early in the development process.
- Dynamic Application Security Testing (DAST): Testing the running API to identify vulnerabilities by simulating attacks. This provides a more realistic assessment of security risks.
- Interactive Application Security Testing (IAST): Combining aspects of SAST and DAST by instrumenting the application to detect vulnerabilities in real-time during testing.
- Runtime Application Self-Protection (RASP): A technique that integrates security directly into the application to detect and respond to attacks as they occur.
Static and Dynamic API Security Testing: A Comparison
Static and dynamic API security testing approaches differ significantly in their methodology and the types of vulnerabilities they detect.
Static testing analyzes the source code without executing the application. This allows for early detection of potential vulnerabilities, but it might miss runtime errors or vulnerabilities that only manifest during execution. It’s generally faster and less resource-intensive than dynamic testing.
Dynamic testing, on the other hand, involves testing the running application. This approach can detect vulnerabilities that are not apparent in the source code, but it requires a fully functional application and can be more time-consuming and resource-intensive.
| Feature | Static Testing | Dynamic Testing |
|---|---|---|
| Method | Code analysis | Runtime testing |
| Execution | No execution needed | Requires running application |
| Vulnerability Detection | Early detection of potential vulnerabilities | Detection of runtime vulnerabilities |
| Resource Consumption | Lower | Higher |
| Speed | Faster | Slower |
Integrating Automated API Security Testing into CI/CD Pipelines
Integrating automated API security testing into CI/CD pipelines ensures continuous security validation throughout the software development lifecycle. This streamlined approach enables early detection and remediation of vulnerabilities, reducing the risk of security breaches in production environments.
A typical workflow involves the following steps:
- Triggering the tests: Automated tests are triggered upon code commits or deployments.
- Running the tests: Automated tools scan the API for vulnerabilities using both static and dynamic analysis methods.
- Reporting results: Test results, including identified vulnerabilities and their severity levels, are reported to the development team.
- Remediation: Developers address the identified vulnerabilities based on their severity and impact.
- Continuous Monitoring: Post-deployment monitoring ensures that the API remains secure and that new vulnerabilities are detected and addressed promptly.
For example, a team might use Jenkins or GitLab CI/CD to trigger automated API security tests using a tool like ZAP after each code commit. The results are then integrated into the CI/CD pipeline, halting the deployment process if critical vulnerabilities are detected. This allows developers to address issues immediately, preventing them from reaching production.
API Security Automation with Cequence Security
Cequence Security offers a unique approach to API security automation, moving beyond traditional testing methods to provide continuous, real-time protection. Instead of relying solely on scheduled scans, Cequence leverages its AI-powered platform to identify and respond to API security threats as they emerge, significantly reducing the window of vulnerability. This proactive approach is crucial in today’s dynamic API landscape.Cequence Security’s platform automates the API security lifecycle by integrating directly into the development and deployment pipelines.
This allows for continuous monitoring and automated responses, minimizing manual intervention and accelerating the overall security process. The platform’s ability to learn and adapt to evolving attack patterns is a key differentiator, ensuring that protection remains effective against even the most sophisticated threats.
Cequence Security’s Automated API Security Features
Cequence Security’s platform boasts several features specifically designed for API security automation. These features work in concert to provide comprehensive protection throughout the API lifecycle. Key features include automated discovery of APIs, continuous monitoring for anomalous behavior, and automated response mechanisms to mitigate threats. The platform’s ability to integrate with existing security tools and workflows further enhances its automation capabilities.
This integration streamlines the security process and ensures a cohesive security posture across the organization.
Addressing Challenges in API Security Automation
Automating API security presents several challenges, including the sheer volume of APIs, the complexity of API interactions, and the constant evolution of attack techniques. Cequence Security addresses these challenges through its AI-driven approach. The platform’s ability to learn and adapt to new attack patterns, combined with its automated discovery and monitoring capabilities, allows it to effectively manage the scale and complexity of modern API environments.
Furthermore, the platform’s integration capabilities streamline workflows and minimize the manual effort required for effective API security management. The platform’s real-time threat detection and automated response capabilities significantly reduce the time it takes to identify and remediate vulnerabilities, addressing the speed at which attacks evolve. For example, a sudden surge in requests to a specific API endpoint, indicative of a potential denial-of-service attack, would be automatically flagged and mitigated by Cequence Security’s platform, without requiring manual intervention.
Practical Implementation Strategies
Automating API security testing isn’t a simple switch-flip; it requires a strategic approach and a phased implementation. This section Artikels a practical, step-by-step guide, best practices, and integration strategies for seamlessly incorporating automated API security into your development lifecycle. Success hinges on careful planning, selecting the right tools, and fostering collaboration across teams.
Step-by-Step Guide for Implementing Automated API Security Testing
Implementing automated API security testing involves a structured approach. Begin by identifying critical APIs, prioritizing them based on risk and business impact. Then, select appropriate automated testing tools based on your needs and budget, ensuring they integrate well with your existing CI/CD pipeline. Next, create and execute automated tests, focusing on common vulnerabilities. Finally, continuously monitor and refine your testing strategy based on the results.
Regular updates and improvements are crucial to maintain effectiveness.
API Security Automation Best Practices
A robust API security automation strategy relies on several key best practices. These practices ensure comprehensive coverage, efficient processes, and maintainable solutions.
- Prioritize API testing based on risk assessment: Focus on high-risk APIs first.
- Use a combination of static and dynamic testing: This provides comprehensive coverage of vulnerabilities.
- Integrate security testing early and often: Shift left security practices reduce costs and improve quality.
- Automate security testing as part of CI/CD: Ensure security is a core part of your software development lifecycle.
- Establish clear metrics and reporting: Track key indicators to measure the effectiveness of your security efforts.
- Regularly update your testing tools and processes: Keep up with evolving threats and vulnerabilities.
Integrating Automated Security into Agile and DevOps Methodologies
Integrating automated API security testing into Agile and DevOps environments requires a collaborative approach. In Agile, security should be built into each sprint, with automated tests running as part of the continuous integration process. In DevOps, automated security testing should be integrated into the continuous delivery pipeline, ensuring that security is addressed throughout the entire software delivery lifecycle. This requires close collaboration between security, development, and operations teams.
For example, in an Agile environment, security considerations could be incorporated into user stories, with automated tests designed and implemented alongside the development of new API features. Similarly, in a DevOps pipeline, automated security scans could be triggered automatically upon code deployment to a testing environment. This ensures rapid feedback and continuous improvement of security posture.
Future Trends in API Security Automation
The landscape of API security is rapidly evolving, driven by the increasing reliance on APIs for business operations and the sophistication of modern cyberattacks. Automation is no longer a luxury but a necessity, and the future of API security hinges on advancements in technology and innovative approaches to threat detection and mitigation. This section explores the key trends shaping the future of API security automation.
The convergence of several technologies is poised to significantly enhance the effectiveness and efficiency of API security automation. This includes advancements in AI and Machine Learning, improved orchestration capabilities, and the adoption of more robust security protocols. These developments will lead to more proactive, intelligent, and adaptable security solutions.
The Role of AI and Machine Learning in API Security
AI and machine learning are transforming API security by enabling more sophisticated threat detection and response capabilities. Machine learning algorithms can analyze vast amounts of API traffic data to identify anomalous patterns and potential threats that traditional signature-based systems might miss. For example, ML models can be trained to recognize subtle deviations from normal API usage patterns, such as unusual request frequencies or data volumes, indicating potential attacks like brute-force attempts or data exfiltration.
Furthermore, AI-powered systems can automate the process of vulnerability identification and remediation, significantly reducing the time and resources required to secure APIs. This proactive approach allows for faster response times to emerging threats and minimizes the window of vulnerability. Companies like Cequence Security are already leveraging AI/ML to provide real-time threat detection and automated responses.
Emerging Technologies Impacting API Security Automation
Beyond AI/ML, several other technologies are contributing to the evolution of API security automation. Serverless computing, for instance, presents both opportunities and challenges. While it offers scalability and cost-effectiveness, it also introduces complexities in securing serverless functions and APIs. Automated security solutions must adapt to these architectures, offering comprehensive protection for serverless deployments. Similarly, the rise of microservices necessitates automated security measures tailored to the distributed nature of these applications.
This involves integrating security into the DevOps pipeline and automating the deployment of security controls across multiple microservices. Blockchain technology, though still in its early stages of adoption in API security, holds potential for enhancing API authentication and authorization, offering tamper-proof and transparent security mechanisms.
The Future Landscape of API Security and Automation
The future of API security will be characterized by increased automation, proactive threat detection, and a shift towards a more holistic security approach. We can expect to see a greater integration of API security into the broader DevSecOps lifecycle, with automated security testing and monitoring becoming integral parts of the software development process. Furthermore, the use of AI and ML will continue to grow, enabling more intelligent and adaptive security solutions.
The concept of “API security posture management” (API SPM) will gain traction, providing organizations with a comprehensive view of their API security landscape and enabling them to prioritize and address vulnerabilities effectively. This proactive approach, combined with automated remediation, will be crucial in mitigating the growing threat of API attacks. For example, imagine a scenario where an anomaly detection system, powered by AI, automatically identifies a suspicious access pattern to a payment API.
The system then automatically quarantines the offending IP address and triggers an alert to the security team, all without human intervention. This exemplifies the future of automated API security, where proactive defense and rapid response are the norm.
Subbu Iyer’s Insights and Expertise
Subbu Iyer, with his extensive experience at Cequence Security, offers a unique perspective on the ever-evolving landscape of API security. His insights are invaluable, particularly concerning the automation of security testing and the strategic implementation of robust API protection measures. This section delves into his views on the current state of API security, his practical experience, and his predictions for the future.Subbu Iyer’s perspective on the current state of API security highlights a critical gap between the rapid adoption of APIs and the maturity of security practices surrounding them.
He emphasizes that many organizations are still struggling to keep pace with the increasing complexity and volume of their API deployments, leaving them vulnerable to a wide range of attacks. He observes a significant shift towards automation as a necessary response to this challenge, recognizing that manual processes are simply not scalable or efficient enough to address the growing threat landscape.
Subbu Iyer’s Experience Implementing API Security Automation Strategies
His experience in implementing API security automation strategies centers on the practical challenges of integrating security testing into the DevOps pipeline. He stresses the importance of shifting left, integrating security testing early and often in the development lifecycle, rather than treating it as an afterthought. This approach, he argues, significantly reduces the cost and effort associated with remediation, while simultaneously improving the overall security posture.
A key element of his approach involves utilizing automated tools and processes to scan APIs for vulnerabilities, conduct penetration testing, and continuously monitor for suspicious activity. He cites numerous examples where this proactive approach has prevented significant security breaches, demonstrating the effectiveness of automation in mitigating risk.
Subbu Iyer’s Predictions for the Future of API Security and its Automation
Subbu Iyer predicts a continued increase in the adoption of AI and machine learning in API security automation. He foresees tools that can not only detect known vulnerabilities but also proactively identify and mitigate emerging threats, based on patterns and anomalies in API traffic. He believes that this will lead to a more proactive and adaptive security posture, enabling organizations to stay ahead of the curve in the face of increasingly sophisticated attacks.
He also anticipates a greater emphasis on API security observability, with tools providing real-time insights into API behavior and performance, allowing for quicker identification and resolution of security incidents. This increased visibility, he argues, will be critical in managing the risks associated with the growing number and complexity of APIs within modern applications. For example, he suggests the future will see a rise in AI-powered solutions that can automatically generate and update API security policies, based on real-time threat intelligence and evolving best practices, minimizing the manual effort required for ongoing maintenance and reducing the risk of human error.
Subbu Iyer’s interview on automating the API security lifecycle with Cequence Security really got me thinking about the broader implications for application development. It made me realize how crucial robust security is, especially considering the rapid advancements in app development, like what’s discussed in this insightful article on domino app dev, the low-code and pro-code future. Ultimately, secure and efficient API management, as highlighted by Iyer, is key regardless of the development methodology you choose.
Case Studies
Automating API security is no longer a futuristic concept; it’s a necessity for organizations of all sizes. Many companies have successfully implemented API security automation, reaping significant benefits in terms of efficiency, cost savings, and improved security posture. Examining these success stories provides valuable insights into best practices and potential challenges.
The following case studies illustrate the diverse approaches organizations take to automate their API security lifecycle and the tangible results they achieve. The common thread is a proactive shift towards automated solutions to address the ever-growing threat landscape surrounding APIs.
Successful API Security Automation Implementations
| Organization | Approach | Results | Lessons Learned |
|---|---|---|---|
| Hypothetical Fintech Company (Example 1) | Implemented a comprehensive API security platform incorporating automated vulnerability scanning, runtime protection, and security policy enforcement. This included integrating the platform with their CI/CD pipeline for continuous security testing. | Reduced API vulnerability detection time by 80%, decreased remediation time by 50%, and prevented three major security breaches. Significant cost savings were realized through automated patching and reduced manual intervention. | Thorough integration with existing infrastructure and workflows is crucial. Training and buy-in from development teams are essential for successful adoption. |
| Hypothetical E-commerce Platform (Example 2) | Focused on automating runtime API protection using a combination of Web Application Firewalls (WAFs) and bot detection systems. This approach prioritized the prevention of attacks targeting their public-facing APIs. | Significant reduction in API-related attacks (95% decrease in successful attacks), improved customer experience through reduced latency, and enhanced brand reputation due to improved security posture. | Prioritizing critical APIs for automation is key. Regular monitoring and adjustments to the security controls are necessary to maintain effectiveness. A phased approach to implementation can reduce disruption. |
| Hypothetical Healthcare Provider (Example 3) | Emphasized automated static and dynamic API security testing integrated into their DevOps pipeline. This allowed for early detection of vulnerabilities during the development phase, minimizing the impact on production systems. | Improved code quality, reduced the number of vulnerabilities found in production by 70%, and accelerated the release cycle of new API features. Compliance requirements were met more efficiently. | Automated testing needs to be tailored to the specific characteristics of the APIs being secured. Continuous monitoring and improvement of the automated testing processes are crucial. |
Addressing Common API Security Vulnerabilities Through Automation
API security vulnerabilities represent a significant threat to modern applications. Many of these vulnerabilities stem from weaknesses in API design, implementation, and management. Fortunately, automation plays a crucial role in mitigating these risks, significantly improving the security posture of organizations. By leveraging automated tools and processes, developers and security teams can proactively identify and address vulnerabilities before they can be exploited by malicious actors.Automation significantly enhances the speed and efficiency of API security testing, enabling more frequent scans and quicker remediation of identified issues.
This proactive approach reduces the window of vulnerability and minimizes the potential impact of successful attacks. Moreover, automation helps address the human element—reducing the chances of human error in the testing process and providing consistent, repeatable security assessments.
Common API Vulnerabilities and Automated Mitigation Strategies
Automated security testing is essential for effectively addressing the wide range of API vulnerabilities. A robust automated security program should encompass a variety of techniques and tools to ensure comprehensive coverage.
- Injection Flaws (SQL Injection, Command Injection, Cross-Site Scripting (XSS)): These vulnerabilities allow attackers to inject malicious code into API requests, potentially compromising data integrity, confidentiality, and availability. Automated tools like dynamic application security testing (DAST) tools can identify these flaws by analyzing API responses and identifying suspicious patterns. Static application security testing (SAST) tools can detect injection vulnerabilities in the source code itself, before deployment.
Furthermore, robust input validation and parameterized queries (for SQL injection) are crucial preventative measures easily enforced via automated code review and testing tools.
- Broken Authentication and Session Management: Weak or improperly implemented authentication mechanisms can allow attackers to gain unauthorized access to API resources. Automated security testing tools can simulate attacks to identify vulnerabilities in authentication flows, session management, and authorization controls. Automated penetration testing tools can actively probe for weaknesses in these mechanisms. Implementing strong password policies, multi-factor authentication, and secure session management techniques, enforced through automated code analysis, are vital mitigation strategies.
- Broken Access Control: Inadequate access control mechanisms allow unauthorized users or applications to access sensitive data or functionality. Automated tools can test access control by attempting to access resources with various user roles and permissions. Automated API security testing platforms can validate that only authorized users can access specific API endpoints and data. Regular automated scans for misconfigurations are crucial.
- Sensitive Data Exposure: Exposing sensitive data, such as personally identifiable information (PII) or credentials, through APIs poses a significant risk. Automated tools can scan API responses for sensitive data and alert developers to potential leaks. Static and dynamic analysis tools can identify hardcoded credentials or insecure storage mechanisms in the API code and infrastructure. Automated data masking and encryption techniques can help protect sensitive data at rest and in transit.
- XML External Entities (XXE): XXE vulnerabilities allow attackers to access local files or internal networks through maliciously crafted XML requests. Automated tools can detect XXE vulnerabilities by sending specially crafted XML requests and monitoring the API’s response. Automated code analysis can detect vulnerable XML processing libraries and ensure proper configuration to mitigate this threat.
The Role of Security Orchestration, Automation, and Response (SOAR)
SOAR platforms are crucial for effectively managing the complexities of modern cybersecurity threats, especially in the context of API security. By automating incident response and integrating with automated API security testing, SOAR significantly improves an organization’s ability to detect, respond to, and recover from API security breaches. This integrated approach reduces response times, minimizes damage, and enhances overall security posture.SOAR platforms can automate various aspects of API security incident response.
This automation streamlines workflows, reduces human error, and allows security teams to focus on more strategic tasks.
Automating API Security Incident Response with SOAR, Automating the api security lifecycle an interview with subbu iyer of cequence security
SOAR platforms automate incident response by centralizing security tools and processes. This includes automating tasks like threat detection, vulnerability analysis, containment, eradication, and post-incident recovery. For example, upon detection of a suspicious API activity flagged by an automated API security testing tool, the SOAR platform can automatically trigger a series of actions. These actions might include isolating the affected API, blocking malicious IP addresses, analyzing logs for further insights, and notifying relevant security personnel.
The automation reduces the time it takes to respond to an incident, which is critical in minimizing potential damage. The centralized view provided by SOAR also allows for better coordination and collaboration among different security teams.
Benefits of Integrating SOAR with Automated API Security Testing
Integrating SOAR with automated API security testing creates a powerful synergy. Automated testing continuously scans APIs for vulnerabilities, providing valuable data that feeds directly into the SOAR platform. This continuous monitoring allows for proactive identification of potential threats before they can be exploited. When a vulnerability is discovered, the SOAR platform can automatically initiate remediation actions, such as patching the vulnerability or implementing compensating controls.
This proactive approach minimizes the window of vulnerability and reduces the risk of successful attacks. Furthermore, the integrated system provides a comprehensive audit trail of all security activities, facilitating compliance and regulatory reporting.
Hypothetical SOAR Workflow for an API Security Breach
Imagine a scenario where an automated API security testing tool detects a SQL injection vulnerability in a critical payment processing API. Here’s a hypothetical SOAR workflow to handle the breach:
1. Detection
The automated API security testing tool identifies the SQL injection vulnerability and sends an alert to the SOAR platform.
2. Investigation
The SOAR platform automatically initiates an investigation, collecting relevant logs and data from various security tools.
3. Containment
Based on pre-defined playbooks, the SOAR platform automatically isolates the affected API, preventing further exploitation. This might involve temporarily disabling the API or restricting access to specific IP addresses.
4. Remediation
The SOAR platform triggers a workflow to patch the vulnerability, potentially deploying a pre-approved patch or implementing a workaround. It may also notify the development team to address the root cause.
5. Recovery
Once the vulnerability is patched and the API is restored, the SOAR platform automatically monitors the API for any further suspicious activity.
6. Reporting
The SOAR platform generates a detailed report summarizing the incident, including the timeline, affected systems, and remediation steps taken. This report can be used for post-incident analysis and improvement of security processes.This workflow demonstrates how SOAR can significantly streamline the response to API security breaches, reducing the impact and improving overall security posture. The speed and efficiency gained through automation are critical in today’s fast-paced threat landscape.
Measuring the Effectiveness of Automated API Security
Effectively measuring the success of your automated API security program is crucial for demonstrating ROI and ensuring continuous improvement. It’s not enough to simply implement tools; you need quantifiable data to show their impact on your overall security posture. This involves tracking key metrics and visualizing the correlation between automation and reduced security incidents.Key metrics provide a clear picture of the effectiveness of your API security automation strategy.
These metrics should be tracked consistently to identify trends and areas for improvement. Regular reporting on these metrics enables informed decision-making and demonstrates the value of the program to stakeholders.
Key Metrics for Measuring Effectiveness
The effectiveness of automated API security can be measured through several key performance indicators (KPIs). These metrics offer a comprehensive view of the program’s impact, from the efficiency of testing to the reduction of security risks.
- Number of APIs Scanned: Tracks the total number of APIs assessed by automated tools. This provides a baseline measure of coverage.
- Vulnerability Detection Rate: This metric indicates the percentage of vulnerabilities successfully identified by automated tools. A higher rate suggests better tool effectiveness and configuration.
- Time to Remediation: Measures the time elapsed between vulnerability detection and its resolution. Shorter remediation times indicate efficient workflows and prioritization.
- False Positive Rate: Represents the percentage of alerts generated by automated tools that are not actual vulnerabilities. A high false positive rate can lead to alert fatigue and decreased efficiency.
- Security Incidents Reduced: This directly measures the reduction in security breaches related to APIs attributable to the automated security program.
- Cost Savings: This quantifies the financial benefits of automation, including reduced manual effort and faster remediation.
Tracking and Reporting on Metrics
Establishing a robust tracking and reporting system is essential for monitoring the performance of your automated API security program. This system should facilitate data collection, analysis, and visualization to provide actionable insights.Regular reports should be generated, summarizing key metrics and identifying trends. These reports should be tailored to the audience, focusing on relevant KPIs and providing clear, concise interpretations.
Dashboards can effectively visualize these metrics, providing a quick overview of the program’s performance. For example, a dashboard could display the number of APIs scanned, vulnerabilities detected, and remediation times over a specified period, highlighting trends and areas needing attention.
Visual Representation of Automated Testing and Reduced Security Incidents
A simple bar chart can effectively illustrate the relationship between automated API security testing and a reduction in security incidents.The X-axis would represent time periods (e.g., months or quarters). The Y-axis would represent the number of security incidents. Two bars would be displayed for each time period: one representing the number of security incidents before the implementation of automated API security testing, and the other representing the number of security incidents after implementation.
A clear downward trend in the “after implementation” bars would visually demonstrate the effectiveness of the automation program. For instance, if in Q1 2023 there were 15 incidents before automation and 5 after, this would be clearly shown. A similar comparison for Q2, Q3, and Q4 would further reinforce the positive impact. This visualization would clearly show a significant reduction in security incidents following the introduction of automated API security testing.
End of Discussion
This interview with Subbu Iyer was a real eye-opener. It’s clear that automating API security isn’t just a good idea – it’s a necessity. From the practical steps of integrating automated testing to the potential of AI and machine learning, the conversation highlighted the transformative power of automation in securing our increasingly API-dependent world. The key takeaway? Proactive, automated security isn’t just about patching holes; it’s about building security into the very fabric of your API development.
Don’t wait for a breach – start automating your API security today!
Clarifying Questions: Automating The Api Security Lifecycle An Interview With Subbu Iyer Of Cequence Security
What are the biggest misconceptions about API security automation?
Many believe automation is a silver bullet, solving all security problems. It’s a powerful tool, but it requires careful planning, integration, and ongoing monitoring to be truly effective. It’s not a “set it and forget it” solution.
How much does API security automation cost?
The cost varies greatly depending on the tools, the size of your API landscape, and the level of automation you implement. There are free open-source tools and more comprehensive, enterprise-grade solutions available.
What if my APIs are already in production? Can I still automate security?
Absolutely! You can start by implementing automated testing for new APIs and gradually incorporate automation for existing ones. Prioritization is key, focusing on the most critical APIs first.
What skills are needed to implement API security automation?
A multidisciplinary team is ideal, including developers, security engineers, and DevOps professionals. Skills in scripting, API testing, and security best practices are essential.





