BigFix Extends Inventory to Discover Container Software
BigFix extends inventory capability to discover software in containers – a game-changer for anyone managing complex, containerized applications! This powerful new feature lets you get a complete picture of the software running inside your Docker, Kubernetes, and other container environments. Imagine effortlessly identifying every piece of software, from base images to application-specific layers, all within a single, unified view.
No more hunting through disparate logs or struggling to keep track of your ever-changing software landscape. This post dives into how BigFix achieves this, the benefits it unlocks, and some things to keep in mind.
We’ll explore the different data collection methods BigFix employs, its seamless integration with popular container orchestration platforms, and the security implications of managing this crucial inventory data. We’ll also delve into practical use cases, from security auditing and compliance reporting to capacity planning and license management. Get ready to streamline your container management and gain unprecedented visibility into your software deployments.
BigFix Container Discovery
BigFix has significantly enhanced its inventory capabilities to effectively manage and monitor software deployed within containerized environments. This extension provides crucial visibility into the software composition of containers, enabling more comprehensive asset management and streamlined security patching. This functionality is vital in today’s increasingly containerized infrastructure.BigFix’s container discovery leverages its existing agent technology, extending its reach to inspect and report on the contents of various container runtimes.
This allows for a unified view of both traditional and containerized software assets, simplifying management across heterogeneous environments. The system’s ability to differentiate between base images and application layers offers granular control and detailed reporting.
Supported Container Environments
BigFix’s container discovery supports a range of popular container technologies, including Docker, Kubernetes, and other container orchestration platforms. The specific methods for integration may vary depending on the platform, but the core functionality of identifying and cataloging software remains consistent. This broad support ensures compatibility across diverse deployment models. For instance, BigFix can interact directly with Docker daemons to retrieve container metadata and inspect running processes, while Kubernetes integration often involves leveraging the Kubernetes API to gather information about pods and containers.
Software Identification and Cataloguing within Containers
BigFix’s inventory process identifies software within containers by analyzing various data sources. It examines the container’s filesystem to detect installed packages and applications, leveraging both file-based signatures and process-level information. This allows BigFix to create an accurate inventory of the software components present, regardless of whether they’re part of the base image or layered on top. The system distinguishes between base images and application layers, providing a detailed breakdown of the software stack within each container.
This level of granularity is crucial for identifying vulnerabilities and managing software updates efficiently. For example, if a vulnerability is discovered in a specific library within an application layer, BigFix can precisely target that layer for remediation, avoiding unnecessary updates to the base image.
Inventory Data Collection Methods
BigFix’s extended inventory capabilities for containerized environments leverage several methods to gather comprehensive software information. The choice of method often depends on the container runtime, image format, and the level of detail required. Understanding these methods is crucial for effective software asset management and security posture assessment within dynamic containerized infrastructures.BigFix employs a multi-faceted approach to collect inventory data from containers, utilizing both agent-based and agentless techniques depending on the deployment strategy and the level of access available.
This ensures flexibility and robustness in diverse container environments.
Data Collection from Docker Images
BigFix extracts software inventory information from Docker images primarily by analyzing the image’s layer structure and metadata. This involves inspecting the filesystem within each layer to identify installed packages, executables, libraries, and configuration files. For example, BigFix can parse package managers’ databases (like `dpkg` for Debian-based images or `rpm` for Red Hat-based images) to identify installed software and their versions.
It also utilizes file system scanning techniques to discover other software components not explicitly managed by a package manager. The process typically involves utilizing the Docker API to access image layers, thereby avoiding the need to pull and run the entire image.
Data Collection from OCI Images
The approach to collecting inventory data from Open Container Initiative (OCI) images is largely similar to that used for Docker images. BigFix leverages the OCI image specification to access and analyze the image layers and filesystem. Because OCI is a more general standard, BigFix’s approach to parsing the image’s content and identifying installed software remains consistent across various container runtimes that support the OCI specification, such as containerd, CRI-O, and others.
The core principle remains the analysis of the layered filesystem, regardless of the specific container runtime used.
Handling Dynamic Changes in Container Environments
BigFix employs several mechanisms to address the dynamic nature of container environments. Regular polling of container runtimes using their respective APIs allows for near real-time updates on container status, including restarts and deployments. Event-driven mechanisms, triggered by container lifecycle events (such as container creation, start, stop, and deletion), are also utilized to ensure timely updates to the inventory.
This proactive approach minimizes the lag between changes in the container environment and the corresponding updates in the BigFix inventory. Furthermore, BigFix’s ability to execute custom scripts within containers allows for tailored data collection and processing, addressing specific requirements or unusual container configurations.
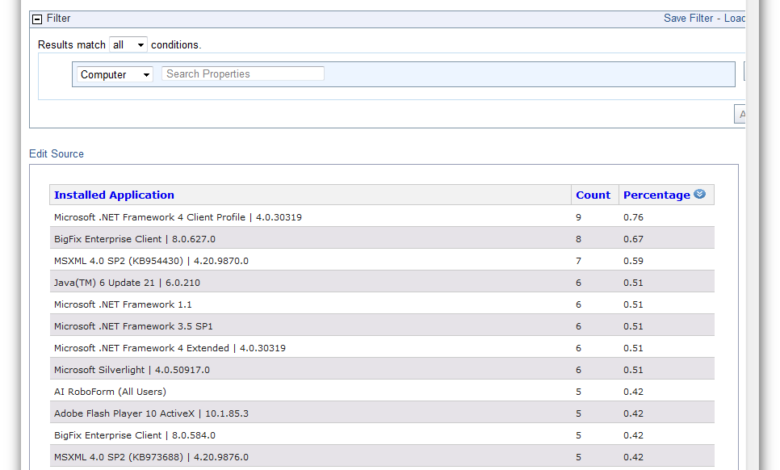
Inventory Data Points Collected
The following table illustrates the typical data points collected by BigFix for containerized software.
| Data Point | Description | Example | Data Type |
|---|---|---|---|
| Image Name | The name of the container image. | nginx | String |
| Image Tag | The tag associated with the image. | latest | String |
| Image Version | The version of the container image. | 1.23.4 | String |
| Dependencies | List of software dependencies. | libssl, libc | Array of Strings |
| Running Processes | List of processes running within the container. | nginx: 8080 | Array of Strings |
| Operating System | The operating system running inside the container. | Ubuntu 20.04 | String |
| Container ID | Unique identifier for the container instance. | a1b2c3d4e5f6 | String |
| Container Runtime | The container runtime used (e.g., Docker, containerd). | Docker | String |
Integration with Existing Infrastructure: Bigfix Extends Inventory Capability To Discover Software In Containers
BigFix’s strength lies in its ability to seamlessly integrate with your existing infrastructure, extending its powerful inventory and remediation capabilities into the dynamic world of containers. This integration allows for comprehensive visibility and management of software within containerized environments, regardless of the orchestration platform used. Proper configuration is key to unlocking this power.BigFix integrates with popular container orchestration platforms like Kubernetes and Docker Swarm through various methods, leveraging existing APIs and agent deployment strategies.
This integration allows for automated discovery and inventory of software running inside containers, providing a centralized view of your entire software landscape, including both traditional and containerized applications. This centralized view significantly simplifies software management and patching, reducing vulnerabilities and improving operational efficiency.
BigFix Integration with Kubernetes
BigFix can integrate with Kubernetes using a variety of methods, including the use of Kubernetes custom resources (CRDs) to manage BigFix agents as deployments or daemonsets. This allows for the automated deployment and management of BigFix agents across your Kubernetes cluster. A common approach involves creating a Kubernetes deployment that includes the BigFix agent as a container within the pod.
The agent then communicates with the BigFix server, reporting inventory data and responding to remediation actions. This approach ensures that all containers within a given deployment or namespace are automatically monitored and managed by BigFix. Configuration involves defining the necessary environment variables within the agent container, specifying the BigFix server address and relevant authentication credentials. Properly configured service accounts and network policies within Kubernetes are crucial for secure agent communication.
BigFix Integration with Docker Swarm
For Docker Swarm environments, BigFix integration typically involves deploying the BigFix agent as a service alongside the applications. This can be achieved through Docker Compose or directly via the Docker Swarm CLI. Similar to the Kubernetes approach, the agent container needs to be configured with the appropriate environment variables to connect to the BigFix server. The agent’s communication with the BigFix server should be secured using TLS encryption.
Monitoring the agent’s logs is vital for identifying and resolving any connectivity or operational issues. This allows for efficient management and monitoring of the BigFix agents within the Docker Swarm cluster. Consider using Docker secrets to securely manage sensitive information like BigFix server credentials.
Deploying and Managing BigFix Agents in Containerized Environments
Deploying BigFix agents within containerized environments requires careful consideration of several factors. The agent must be configured to connect to the BigFix server, receive commands, and report back inventory data. This often involves using environment variables within the container to specify the server’s address, port, and authentication credentials. Effective agent management involves monitoring agent health, ensuring successful communication with the server, and promptly addressing any issues that arise.
Automated deployment using orchestration tools like Kubernetes or Docker Swarm is highly recommended to streamline the process and maintain consistency across the environment. Regular updates to the agent are crucial for maintaining security and access to the latest features.
Securing BigFix Agent Communication within Containerized Environments
Securing BigFix agent communication is paramount to maintaining the integrity and confidentiality of your infrastructure. Using TLS encryption for all communication between the agent and the server is essential. This encryption protects sensitive data transmitted during inventory reporting and remediation actions. Furthermore, network policies within the container orchestration platform should be implemented to restrict access to the BigFix server and limit the agent’s network exposure.
Regular security audits and vulnerability scans are necessary to identify and mitigate potential security risks. Properly configured firewalls and intrusion detection systems should also be in place to provide additional layers of security. Regularly updating the BigFix agent and server software is crucial for patching security vulnerabilities and ensuring the continued security of your infrastructure.
Benefits and Use Cases
BigFix’s extended inventory capabilities for containerized software offer significant advantages in managing the complexities of modern application deployments. By providing a comprehensive view of software within containers, BigFix empowers organizations to streamline software lifecycle management, enhance security posture, and optimize resource utilization. This visibility is crucial in today’s dynamic containerized environments where applications are frequently updated and deployed across multiple platforms.Extending BigFix’s inventory to include containerized software directly translates to improved efficiency and reduced operational risks.
The ability to accurately track software versions, dependencies, and vulnerabilities within containers allows for proactive management of the entire software lifecycle. This detailed inventory empowers informed decision-making across various operational domains, including security, compliance, and capacity planning.
Software Lifecycle Management Improvements
BigFix’s container software inventory significantly enhances software lifecycle management by providing real-time visibility into the software deployed in containers across your infrastructure. This allows for automated patching, streamlined updates, and improved version control. For example, imagine a scenario where a critical security vulnerability is discovered in a specific library used across multiple containerized applications. BigFix can identify all affected containers and automatically deploy the necessary patches, minimizing the window of vulnerability.
This proactive approach reduces the risk of security breaches and ensures compliance with industry standards. Similarly, managing software updates becomes much more efficient. Instead of manual checks and deployments, BigFix can automate the process, ensuring that all containers are running the latest, secure versions of their software.
Security Auditing and Compliance Reporting
Understanding the software composition of your containerized applications is paramount for maintaining a robust security posture. BigFix’s container inventory provides the necessary data for comprehensive security audits and compliance reporting. This capability enables organizations to identify vulnerabilities, track unauthorized software installations, and demonstrate compliance with industry regulations such as PCI DSS or HIPAA. For example, a regular scan using BigFix can reveal outdated libraries or unauthorized access points, providing valuable insights to proactively address potential security risks.
This data can then be used to generate detailed reports demonstrating compliance with relevant regulations, simplifying the audit process.
- Identify and remediate vulnerabilities in containerized applications.
- Track unauthorized software installations within containers.
- Generate compliance reports for various industry regulations.
- Automate security patching and updates.
Capacity Planning and Resource Optimization
BigFix’s container software inventory facilitates better capacity planning and resource optimization. By providing a detailed view of the software running within containers, organizations can accurately assess resource consumption and identify potential bottlenecks. This granular visibility allows for more effective resource allocation, reducing wasted resources and improving overall system performance. For example, by analyzing the resource utilization of different containerized applications, IT teams can identify applications that require more resources and optimize resource allocation accordingly.
This can lead to significant cost savings and improved efficiency.
Software License Management
Accurate software inventory is crucial for effective software license management. BigFix’s container inventory helps organizations track software licenses associated with applications running within containers. This helps ensure compliance with software license agreements, preventing potential legal and financial penalties. For example, BigFix can identify instances where software is used without a valid license, enabling prompt action to rectify the situation and avoid licensing violations.
This proactive approach ensures compliance and helps organizations avoid costly fines.
- Track software licenses associated with containerized applications.
- Identify unlicensed software usage within containers.
- Ensure compliance with software license agreements.
- Reduce the risk of licensing violations and associated penalties.
Limitations and Considerations
While BigFix offers powerful container discovery capabilities, it’s crucial to understand its limitations and plan accordingly for successful implementation in large-scale containerized environments. Ignoring these aspects can lead to performance bottlenecks, inaccurate inventory data, and ultimately, hinder your ability to effectively manage your container infrastructure.BigFix’s container discovery relies on accessing container metadata and runtime information. This access depends on the container runtime (Docker, Kubernetes, etc.) and the level of permissions granted to the BigFix agent.
Restrictions on these access points, such as network segmentation or restrictive security policies, can directly impact the accuracy and completeness of the inventory data. Furthermore, the agent’s resource consumption within each container needs careful consideration, especially in resource-constrained environments.
Limitations of BigFix Container Discovery Capabilities
Several factors can limit BigFix’s ability to fully discover and inventory software within containers. These limitations stem from the dynamic nature of containers, the variety of container runtimes, and potential security restrictions. For example, ephemeral containers, those with short lifecycles, might not be consistently inventoried. Similarly, containers utilizing sophisticated security measures or employing unique networking configurations might pose challenges for BigFix’s discovery mechanisms.
The ability to accurately inventory software within containers that employ advanced security features like encrypted file systems or utilize custom container images may be hampered, requiring specific configurations or workarounds.
Scaling BigFix for Large Container Deployments
Scaling BigFix to manage a large number of containers requires careful planning and infrastructure optimization. Simply increasing the number of BigFix relays might not suffice; efficient data aggregation and processing become critical. Implementing a hierarchical relay structure, optimizing database performance, and potentially utilizing distributed databases can help manage the increased data volume and improve overall performance. Consideration should also be given to leveraging BigFix’s built-in reporting and analysis features to efficiently manage and analyze the vast amount of inventory data generated from a large containerized environment.
For example, a company managing thousands of containers across multiple data centers might need to implement a distributed architecture with regional relays feeding into a central server for consolidated reporting and analysis.
Performance and Resource Consumption Challenges
Running the BigFix agent within containers consumes resources, including CPU, memory, and network bandwidth. In resource-constrained environments, this consumption can impact the performance of the applications running within the containers. Overly frequent inventory scans can exacerbate this issue. Therefore, optimizing the BigFix agent configuration, including adjusting the scan frequency and selecting relevant inventory data points, is vital to minimize resource consumption and maintain application performance.
For example, prioritizing the collection of only essential software inventory data rather than comprehensive system information can significantly reduce resource usage.
Troubleshooting Common Issues
Addressing issues related to BigFix container discovery often requires a systematic approach. The following steps can help in troubleshooting common problems:
- Verify BigFix agent installation and configuration within the containers. Ensure the agent has the necessary permissions to access container metadata and runtime information.
- Check the BigFix server logs for errors or warnings related to container discovery. These logs often provide valuable clues about the root cause of the problem.
- Inspect the network connectivity between the BigFix agent and the server. Network issues can prevent data from being sent to the server.
- Review the BigFix agent’s resource utilization within the containers. High CPU or memory usage might indicate configuration issues or conflicts with other applications.
- Test the BigFix agent’s ability to discover and inventory software in a simple, isolated container environment before deploying to production.
- Ensure that the BigFix server has sufficient resources (CPU, memory, disk space) to handle the increased workload from a large number of containers.
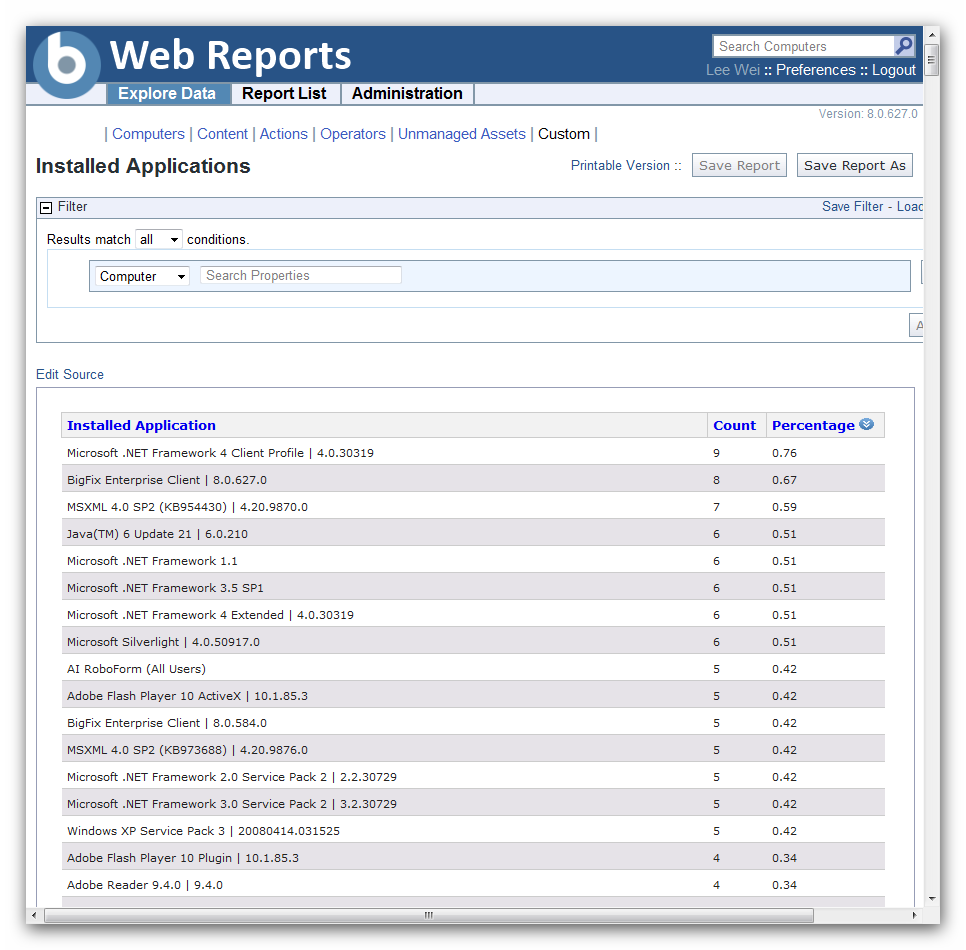
Illustrative Example: Software Inventory Report
This section presents a sample software inventory report generated by BigFix for containers, demonstrating the detailed information that can be gathered. The report showcases the power of BigFix in providing a comprehensive view of software installed within your containerized environment, crucial for security auditing, compliance checks, and efficient resource management. The example focuses on key data points readily available through BigFix’s container discovery capabilities.
The following table illustrates a typical BigFix report, showing software inventory data from various containers. The data includes container-specific identifiers, along with details on the installed software packages and their respective versions. This level of granularity is essential for tracking software updates, identifying vulnerabilities, and maintaining consistent configurations across your containerized infrastructure.
Sample BigFix Container Software Inventory Report
| Container Name | Image ID | Installed Package | Version |
|---|---|---|---|
| webserver-prod-01 | sha256:a1b2c3d4e5f6… | nginx | 1.21.6 |
| database-dev-02 | sha256:f6e5d4c3b2a1… | PostgreSQL | 14.5 |
| database-dev-02 | sha256:f6e5d4c3b2a1… | psql | 14.5 |
| webserver-prod-02 | sha256:a1b2c3d4e5f6… | nginx | 1.21.6 |
| appserver-staging-01 | sha256:7890abcdef… | java | 17.0.7 |
| appserver-staging-01 | sha256:7890abcdef… | tomcat | 9.0.78 |
This report provides a clear and concise overview of the software landscape within the monitored containers. The consistent formatting ensures easy readability and facilitates quick identification of discrepancies or potential vulnerabilities across different container instances. The use of Image IDs allows for precise tracking of software versions tied to specific container images.
Security Implications
Collecting and managing software inventory data from containers introduces unique security challenges. The dynamic nature of containers, coupled with their often ephemeral lifecycles, requires a robust approach to securing both the data itself and the communication channels used to collect it. Failure to adequately address these concerns can lead to significant security vulnerabilities and compliance violations.Securing BigFix agent communication and data transmission is paramount.
Compromised communication channels can expose sensitive inventory data, potentially revealing critical vulnerabilities within your containerized applications. This section details best practices and BigFix capabilities to mitigate these risks.
BigFix Agent Communication Security, Bigfix extends inventory capability to discover software in containers
BigFix utilizes several mechanisms to secure agent communication. These include TLS/SSL encryption for all communication between the BigFix agent and the BigFix server, ensuring data confidentiality and integrity. Additionally, authentication mechanisms, such as certificates or user credentials, verify the identity of both the agent and the server, preventing unauthorized access and data manipulation. Regular updates to the BigFix agent and server are crucial to maintain the effectiveness of these security measures and to patch any known vulnerabilities.
Implementing strong access control policies on the BigFix server further limits access to sensitive inventory data, preventing unauthorized users from viewing or modifying information.
Identifying and Mitigating Vulnerabilities
BigFix can proactively identify security vulnerabilities in containerized applications by correlating software inventory data with known vulnerability databases. By integrating with vulnerability scanners and threat intelligence feeds, BigFix can automatically detect and alert administrators about vulnerabilities present in the software running within containers. This allows for timely remediation, minimizing the window of opportunity for attackers to exploit these vulnerabilities.
For instance, if a container is found to be running a vulnerable version of a web server, BigFix can trigger an alert, allowing administrators to update the container image or implement appropriate mitigation strategies. This proactive approach significantly reduces the risk of successful attacks.
Maintaining Security Compliance
BigFix assists in maintaining compliance with various security policies and regulations. By providing a comprehensive inventory of software within containers, BigFix enables organizations to demonstrate compliance with requirements such as PCI DSS, HIPAA, or GDPR. BigFix allows for the creation of custom compliance reports that track the presence of specific software versions, configurations, and security patches, ensuring that all systems meet the defined security standards.
Automated remediation actions, triggered by compliance violations, can further streamline the process of maintaining compliance and minimizing the risk of penalties. For example, BigFix can automatically initiate a patch deployment to containers running outdated software, ensuring ongoing compliance with security mandates.
Wrap-Up
BigFix’s extended inventory capabilities for containerized environments represent a significant leap forward in software management. By providing a comprehensive and integrated view of software within containers, BigFix empowers organizations to enhance security, streamline operations, and optimize resource utilization. While there are considerations around scaling and potential limitations, the benefits of improved visibility, simplified management, and enhanced security far outweigh the challenges.
If you’re wrestling with the complexities of containerized software, BigFix offers a powerful solution to regain control and optimize your software lifecycle.
FAQ Compilation
What types of container registries does BigFix support?
BigFix supports a wide range of container registries, including Docker Hub, private registries, and cloud-based registries. Specific support depends on the version of BigFix and any necessary plugins.
How does BigFix handle container image updates?
BigFix automatically detects changes in container images, including updates and new deployments. It continuously monitors the container environment and updates its inventory accordingly.
Can BigFix identify vulnerabilities in container images?
While BigFix doesn’t directly scan for vulnerabilities, it can integrate with vulnerability scanning tools. By providing an accurate inventory, BigFix helps streamline the vulnerability management process.
What are the performance implications of using BigFix for container inventory?
The performance impact depends on the size and complexity of your container environment. Proper configuration and optimization are crucial for maintaining performance in large-scale deployments.