
BigFix Supports NIST Cybersecurity Framework for Ransom Risk Management
BigFix supports NIST Cybersecurity Framework for ransom risk management – that’s a mouthful, right? But it’s a game-changer in how we think about protecting ourselves from ransomware attacks. This post dives into how BigFix’s powerful features directly align with the NIST framework’s five core functions: Identify, Protect, Detect, Respond, and Recover. We’ll explore how BigFix helps prevent attacks, detect threats early, and swiftly recover from incidents.
Get ready to level up your ransomware defense strategy!
We’ll unpack BigFix’s capabilities in detail, showing you exactly how it helps you manage vulnerabilities, patch systems, monitor endpoints for suspicious activity, and even isolate infected machines to prevent a full-blown outbreak. I’ll share practical examples and real-world scenarios to illustrate how BigFix can make a real difference in your organization’s security posture. Think of it as your ultimate guide to leveraging BigFix for robust ransomware protection.
BigFix Functionality and NIST Cybersecurity Framework Alignment
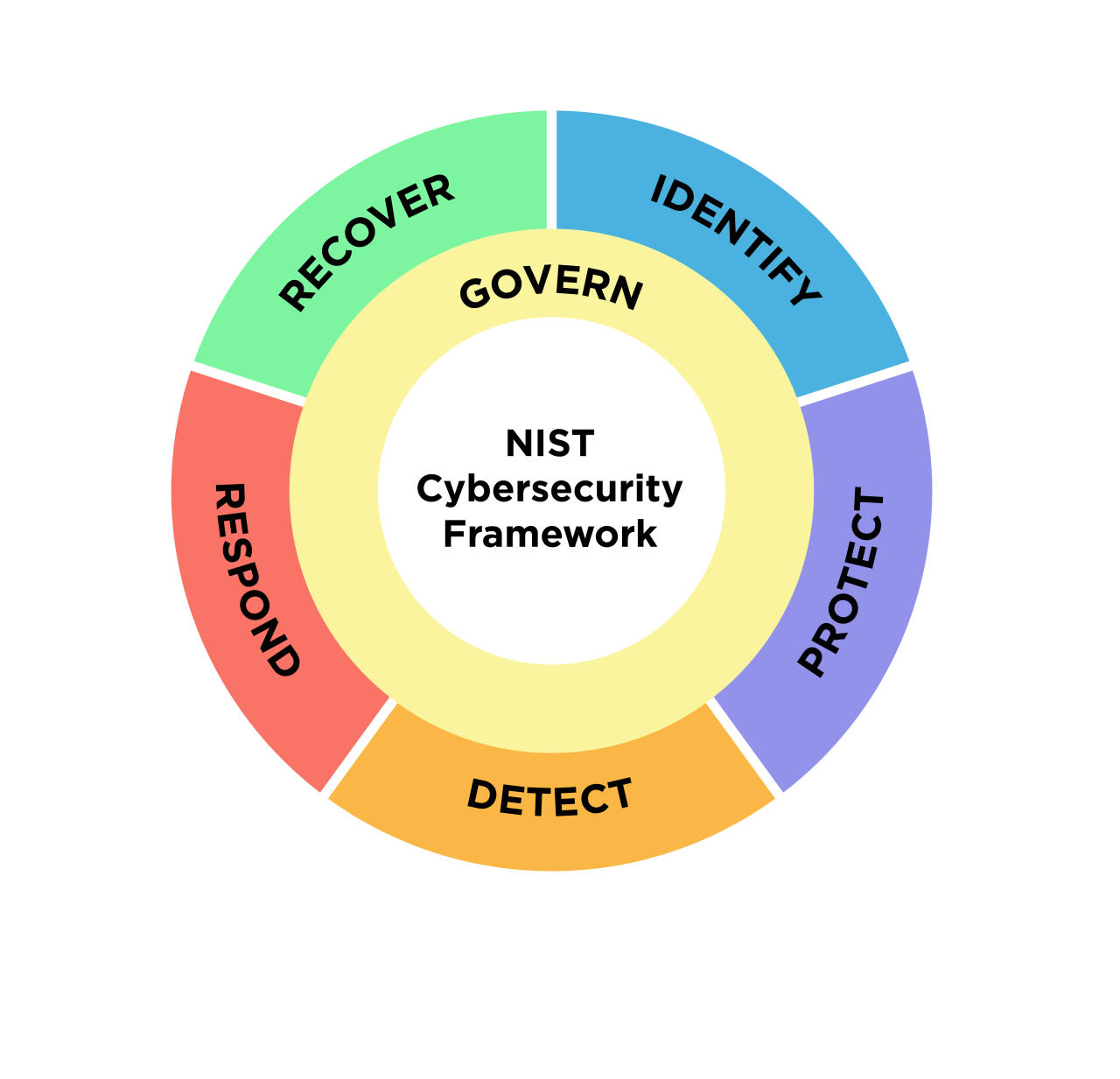
BigFix, now part of HCL Software, offers a robust endpoint management platform ideally suited for bolstering an organization’s cybersecurity posture, particularly in the face of ransomware threats. Its capabilities directly support the five core functions of the NIST Cybersecurity Framework (CSF): Identify, Protect, Detect, Respond, and Recover. This alignment makes BigFix a powerful tool for organizations seeking to implement a comprehensive and effective ransomware risk management strategy.
BigFix and the Identify Function of the NIST CSF
The Identify function focuses on understanding an organization’s assets, risks, and vulnerabilities. BigFix excels in this area by providing a comprehensive inventory of all managed endpoints, including hardware and software details, operating system versions, and installed applications. This granular visibility allows security teams to quickly identify potential vulnerabilities that could be exploited by ransomware. For example, BigFix can identify systems lacking critical security patches, outdated antivirus software, or vulnerable applications, providing a clear picture of the organization’s attack surface.
This detailed inventory is crucial for prioritizing remediation efforts and focusing resources effectively.
BigFix and the Protect Function of the NIST CSF
The Protect function centers on developing and implementing safeguards to limit or contain the impact of a cybersecurity incident. BigFix facilitates this by enabling the deployment and management of security controls across the entire endpoint ecosystem. This includes deploying security patches, configuring security settings, and enforcing access control policies. For instance, BigFix can automatically deploy the latest security updates to all vulnerable systems, reducing the window of opportunity for ransomware attacks.
It can also enforce strong password policies and control access to sensitive data, limiting the potential damage from a successful attack.
BigFix and the Detect Function of the NIST CSF, Bigfix supports nist cybersecurity framework for ransom risk management
The Detect function focuses on identifying the occurrence of a cybersecurity event. BigFix’s real-time monitoring capabilities allow for the early detection of suspicious activity. This includes detecting unusual process activity, unauthorized software installations, and attempts to encrypt files. For example, BigFix can monitor for unusual network traffic patterns indicative of a ransomware infection or detect the execution of known malicious scripts.
Early detection significantly increases the chances of a successful response and minimizes the impact of a ransomware attack.
BigFix and the Respond Function of the NIST CSF
The Respond function emphasizes taking action to contain and mitigate the effects of a cybersecurity event. BigFix’s capabilities are crucial in this phase. It enables rapid containment of infected systems through actions such as isolating compromised machines from the network, terminating malicious processes, and deploying remediation scripts. For instance, upon detecting a ransomware infection, BigFix can automatically isolate the affected system, preventing further spread of the malware.
This swift response is vital in minimizing the damage caused by a ransomware attack.
BigFix and the Recover Function of the NIST CSF
The Recover function deals with restoring systems and data to normal operations following a cybersecurity event. BigFix aids in this process by facilitating the restoration of systems from backups, reinstalling software, and restoring configurations. For example, after a ransomware attack, BigFix can be used to deploy scripts to restore systems from known good backups and reconfigure security settings.
This allows for a quicker recovery and minimizes downtime.
BigFix Features Mapped to NIST CSF Subcategories for Ransomware Mitigation
| NIST Subcategory | BigFix Feature | Explanation | Example Scenario |
|---|---|---|---|
| ID.AM-1 Asset Management | Inventory and Reporting | Provides a comprehensive inventory of all endpoints and their configurations. | Identifying systems running outdated operating systems vulnerable to ransomware exploits. |
| PR.AC-1 Access Control | Policy Enforcement | Enforces security policies, such as password complexity and access control lists. | Preventing unauthorized access to critical systems and data. |
| PR.IP-1 Protective Technology | Patch Management | Automates the deployment of security patches to mitigate vulnerabilities. | Deploying patches for known vulnerabilities exploited by ransomware. |
| DE.CM-6 Security Information and Event Management (SIEM) Integration | Event Monitoring and Correlation | Integrates with SIEM systems to provide real-time monitoring and threat detection. | Detecting unusual file access patterns indicating a ransomware attack. |
| RS.RP-1 Response Planning | Automated Remediation Actions | Enables automated responses to security incidents, such as isolating infected systems. | Automatically isolating an infected system upon detection of ransomware activity. |
| RC.CM-8 Recovery Planning | System Restoration | Facilitates the restoration of systems from backups. | Restoring systems from backups after a successful ransomware attack. |
Ransomware Risk Management with BigFix

BigFix, now part of IBM, offers a robust platform for managing and mitigating the risks associated with ransomware attacks. Its capabilities span proactive prevention through vulnerability and patch management, real-time detection via endpoint monitoring and threat intelligence integration, and effective response mechanisms for containment and recovery. This makes it a valuable tool for organizations striving to meet the requirements of frameworks like NIST Cybersecurity Framework for ransomware risk management.
Proactive Ransomware Prevention with BigFix
BigFix’s strength lies in its ability to proactively prevent ransomware infections. This is achieved primarily through comprehensive vulnerability and patch management. By identifying and remediating vulnerabilities before attackers can exploit them, BigFix significantly reduces the attack surface. Its automated patch deployment capabilities ensure that critical security updates are applied consistently across all managed endpoints, minimizing the risk of ransomware infiltration via known exploits.
Regular security scans and vulnerability assessments, facilitated by BigFix, further enhance this proactive approach, providing a clear picture of the organization’s security posture and identifying potential weaknesses. This proactive approach aligns directly with the NIST Cybersecurity Framework’s emphasis on prevention.
Ransomware Detection with BigFix
BigFix’s endpoint monitoring capabilities play a crucial role in detecting ransomware attacks. Real-time monitoring of system activity allows for the identification of suspicious behaviors indicative of ransomware infection. This includes unusual file access patterns, rapid file encryption, and network communication anomalies. Furthermore, integration with threat intelligence feeds allows BigFix to correlate observed behavior with known ransomware signatures and tactics, techniques, and procedures (TTPs), providing early warning signals of potential attacks.
For example, if a known ransomware strain’s encryption behavior is detected, BigFix can immediately trigger alerts, enabling rapid response.
Containing Ransomware Outbreaks with BigFix
Upon detection of a ransomware attack, BigFix’s response capabilities are vital in containing the outbreak and limiting its impact. Immediate isolation of infected systems prevents the ransomware from spreading laterally across the network, protecting other critical assets. BigFix can remotely disable network connectivity, halt suspicious processes, and even initiate a system shutdown on compromised endpoints, effectively quarantining the threat.
This swift response capability is critical in minimizing the damage caused by ransomware, aligning with the NIST Cybersecurity Framework’s focus on detection and response.
Recovering from a Ransomware Attack with BigFix
BigFix aids in the recovery process by providing tools for restoring impacted systems and remediating vulnerabilities. This includes the ability to deploy recovery images to restore systems to a clean state before the infection. BigFix can also facilitate the restoration of data from backups, ensuring business continuity. Furthermore, post-incident vulnerability analysis and remediation can be orchestrated through BigFix, addressing the root causes of the attack and preventing future incidents.
A step-by-step procedure might involve: 1) Isolating infected systems; 2) Creating a forensic image of infected systems; 3) Restoring systems from backups; 4) Applying patches and updates; 5) Implementing enhanced security measures; and 6) Conducting a thorough post-incident review. This structured approach, facilitated by BigFix, is crucial for effective recovery and future resilience.
BigFix’s Role in NIST CSF Implementation for Ransomware
BigFix, now part of HCLSoftware, plays a crucial role in bolstering an organization’s cybersecurity posture against ransomware attacks by providing a robust platform for implementing the NIST Cybersecurity Framework (CSF). Its capabilities extend across various CSF functions, enabling proactive threat detection, rapid response, and continuous monitoring to minimize the impact of ransomware incidents. This detailed analysis explores how BigFix contributes to a comprehensive ransomware risk management program aligned with the NIST CSF.
Key BigFix Components and Their Contributions to Ransomware Risk Management
BigFix’s strength lies in its integrated approach. Several key components work together to create a comprehensive ransomware defense. The core is its agent, which resides on managed endpoints and allows for remote control and patching. This agent facilitates the timely deployment of security updates and vulnerability fixes, a critical aspect of the NIST CSF’s Identify and Protect functions.
BigFix Inventory provides a clear view of the organization’s IT landscape, allowing for the identification of high-risk systems and vulnerabilities that could be exploited by ransomware. BigFix Compliance enables the enforcement of security policies and baselines, further strengthening the organization’s security posture. Finally, BigFix Actions allow for rapid remediation of compromised systems, minimizing the damage caused by a ransomware attack, which aligns with the NIST CSF’s Respond and Recover functions.
Best Practices for Leveraging BigFix to Improve Cybersecurity Posture Against Ransomware
Effective ransomware mitigation requires a proactive strategy. The following best practices, aligned with NIST CSF guidelines, showcase BigFix’s potential:
- Regular Vulnerability Scanning and Patching: Utilize BigFix Inventory to identify vulnerable systems and BigFix Patch to deploy security updates promptly. This addresses the NIST CSF’s Identify and Protect functions.
- Endpoint Detection and Response (EDR) Integration: Integrate BigFix with EDR solutions to enhance threat detection and incident response capabilities. This supports the Detect and Respond functions of the NIST CSF.
- Security Hardening and Configuration Management: Leverage BigFix Compliance to enforce security baselines and configurations, reducing the attack surface. This aligns with the Protect function of the NIST CSF.
- Data Backup and Recovery Strategies: While BigFix doesn’t directly handle backups, its inventory and reporting features can help track the backup status of critical systems, ensuring compliance with the NIST CSF’s Recover function.
- Regular Security Audits and Reporting: Utilize BigFix’s reporting capabilities to generate regular reports on system vulnerabilities, patch compliance, and security configurations. This supports the NIST CSF’s Govern function.
Comparison of BigFix’s Approach to Ransomware Mitigation with Alternative Security Solutions
BigFix’s strength lies in its comprehensive approach to endpoint management and security. Unlike standalone antivirus solutions that primarily focus on malware detection, BigFix provides a holistic platform for vulnerability management, patch deployment, and security configuration management. While cloud-based security solutions offer centralized management and threat intelligence, BigFix offers robust on-premises capabilities and strong control over endpoint security, which can be critical in highly regulated industries.
However, BigFix might require more specialized expertise for optimal configuration and management compared to simpler, more user-friendly solutions. The choice depends on the organization’s specific needs, technical expertise, and risk tolerance.
BigFix’s Reporting and Auditing Features Supporting NIST CSF Compliance for Ransomware Risk Management
BigFix’s reporting and auditing features are vital for demonstrating compliance with NIST CSF requirements. The platform provides detailed logs of all actions performed, including patch deployments, security policy changes, and remediation activities. This audit trail is crucial for demonstrating compliance with regulatory requirements and for conducting post-incident investigations. BigFix’s reporting capabilities allow organizations to generate customized reports on various aspects of their security posture, including vulnerability assessments, patch compliance levels, and security configuration adherence.
This allows for proactive risk management and facilitates compliance reporting to regulatory bodies. For example, reports detailing the timely application of critical security patches can directly demonstrate adherence to the NIST CSF’s Protect function.
Case Studies and Best Practices
BigFix’s strength lies not just in its features, but in its real-world application. Numerous organizations have leveraged its capabilities to bolster their ransomware defenses, significantly reducing their risk profile. This section will explore several case studies highlighting BigFix’s effectiveness and offer best practices for integrating it into a robust cybersecurity strategy aligned with the NIST Cybersecurity Framework.
Successful implementation hinges on a strategic approach. It’s not simply about deploying BigFix; it’s about integrating it seamlessly into existing security infrastructure and processes. This requires careful planning, collaboration between IT and security teams, and a commitment to ongoing monitoring and improvement.
BigFix in Action: Real-World Examples
Several organizations have publicly shared (though often anonymously to protect sensitive information) their success stories using BigFix for ransomware mitigation. One example involves a large financial institution that used BigFix to rapidly deploy patching updates across its extensive network, preventing a known ransomware vulnerability from being exploited. Another case study details how a healthcare provider utilized BigFix’s endpoint detection and response capabilities to quickly identify and isolate infected machines during a ransomware attack, minimizing data loss and operational disruption.
These examples demonstrate BigFix’s capacity to proactively prevent attacks and reactively contain breaches. In these instances, the speed and precision of BigFix’s actions were crucial in mitigating the impact of ransomware.
Best Practices for Integrating BigFix into a Broader Cybersecurity Strategy
Integrating BigFix effectively requires a holistic approach that aligns with the NIST Cybersecurity Framework. This includes focusing on all five functions: Identify, Protect, Detect, Respond, and Recover. BigFix excels in supporting several of these functions. For example, BigFix’s patch management capabilities directly support the “Protect” function by ensuring systems are up-to-date and vulnerabilities are minimized. Its endpoint detection and response features contribute to the “Detect” and “Respond” functions, allowing for rapid identification and isolation of compromised systems.
Finally, BigFix’s ability to roll back changes and restore systems from backups aids in the “Recover” function. A comprehensive strategy should leverage BigFix’s capabilities within the context of a broader security framework, including regular vulnerability assessments, security awareness training, and incident response planning.
Actionable Steps for Enhancing Ransomware Resilience
To maximize the ransomware resilience offered by BigFix, organizations should take several key steps:
Implementing these steps requires a collaborative effort between IT, security, and business teams. A clear understanding of roles and responsibilities is crucial for effective execution.
- Regularly update and patch all systems using BigFix’s automated patching capabilities.
- Implement robust endpoint detection and response (EDR) capabilities within BigFix to monitor for malicious activity.
- Utilize BigFix’s inventory and reporting features to gain a comprehensive understanding of your IT environment and identify potential vulnerabilities.
- Establish clear incident response procedures and utilize BigFix to isolate infected systems and contain the spread of ransomware.
- Regularly test your backup and recovery procedures using BigFix to ensure data can be restored quickly and efficiently.
- Integrate BigFix with other security tools to create a comprehensive security ecosystem.
- Develop and maintain a comprehensive security awareness training program for all employees.
The Importance of Ongoing Monitoring and Improvement
Continuous monitoring and improvement are essential for maintaining effective ransomware protection. Regularly review BigFix’s logs and reports to identify trends and potential issues. Conduct regular security assessments to identify vulnerabilities and ensure your security posture remains strong. This ongoing process is vital for maintaining NIST CSF compliance and reducing the risk of ransomware attacks. Regular updates to BigFix itself, along with proactive adjustments to its configuration based on evolving threat landscapes, are key components of a sustainable ransomware defense strategy.
Technical Deep Dive: Bigfix Supports Nist Cybersecurity Framework For Ransom Risk Management
BigFix offers a robust suite of tools for ransomware mitigation, going beyond simple detection to proactive prevention and rapid response. Its strength lies in its ability to manage and secure endpoints across an entire organization, enforcing consistent security policies and providing granular visibility into system activity. This allows for a layered defense strategy, minimizing the impact of a successful attack.BigFix’s mechanisms for detecting and responding to ransomware attacks are multifaceted.
Ransomware Detection Mechanisms
BigFix employs several methods to detect ransomware. Real-time monitoring of endpoint activity, coupled with its ability to analyze file system changes, is crucial. Suspicious file creations, rapid file encryption patterns, and unusual process activity – all indicative of ransomware – trigger alerts. Furthermore, BigFix can leverage signature-based detection, utilizing updated threat intelligence feeds to identify known ransomware variants.
Behavioral analysis goes a step further, detecting anomalies in system behavior even without relying on specific signatures. This allows for the identification of zero-day threats or novel ransomware variants. Finally, integration with other security tools, such as SIEM systems, allows for correlation of alerts across different security layers, providing a more comprehensive view of potential threats.
Endpoint Security Features for Prevention and Data Exfiltration
Preventing malware execution is paramount. BigFix achieves this through several key features. Application control allows administrators to define allowed and blocked applications, preventing unauthorized software from running. This includes blocking known malicious applications and restricting the execution of scripts from untrusted sources. File integrity monitoring ensures that critical system files remain unaltered, alerting administrators to any unauthorized changes.
This is particularly important for detecting ransomware, which often modifies system files to achieve persistence. Data loss prevention (DLP) capabilities prevent sensitive data from leaving the network, limiting the impact of a successful ransomware attack. This involves monitoring data transfers, identifying sensitive data, and blocking unauthorized exfiltration attempts.
Configuring BigFix for Security Policy Enforcement and NIST CSF Compliance
Configuring BigFix to align with NIST CSF guidelines involves several steps. First, establish baseline security configurations for endpoints. This includes ensuring operating systems are up-to-date, security patches are applied, and antivirus software is active. BigFix can automate these tasks through its remediation capabilities. Next, define and enforce security policies using BigFix’s policy management features.
This includes setting access controls, restricting application execution, and enforcing data encryption standards. Regular vulnerability assessments are critical. BigFix integrates with vulnerability scanners to identify and remediate vulnerabilities before they can be exploited. Finally, continuous monitoring and compliance reporting are essential. BigFix provides dashboards and reports to track compliance with security policies and NIST CSF guidelines.
This ensures that the organization maintains a strong security posture.
Hypothetical Network Infrastructure Diagram Illustrating BigFix Integration
Imagine a network with several key components working together.
At the heart of the system is the BigFix server, acting as the central management console. This server receives data from various endpoints and security tools. Endpoints (desktops, laptops, servers) are all managed by BigFix, receiving and executing policies, providing real-time monitoring data. A SIEM (Security Information and Event Management) system receives security logs from BigFix and other sources, correlating events for threat detection and incident response.
A firewall protects the network perimeter, while intrusion detection/prevention systems (IDS/IPS) monitor network traffic for malicious activity. A dedicated endpoint detection and response (EDR) solution enhances threat detection capabilities, providing advanced analysis of endpoint activity. BigFix integrates with all these tools, enriching the data provided to the SIEM and facilitating a coordinated response to security incidents. For example, if the EDR detects suspicious activity, it can trigger an automated response via BigFix, isolating the affected endpoint and initiating remediation actions.
The BigFix server also communicates with a threat intelligence platform, providing up-to-date information on the latest threats, which informs policy updates and detection capabilities.
Final Thoughts

So, there you have it – a deep dive into how BigFix and the NIST Cybersecurity Framework work hand-in-hand to fight ransomware. By understanding how BigFix addresses each stage of the NIST framework, you can build a more resilient and secure environment. Remember, proactive prevention and a robust response plan are key to minimizing the impact of a ransomware attack.
Implementing BigFix is a significant step towards achieving that goal. Don’t wait until it’s too late – start strengthening your defenses today!
Questions Often Asked
What specific types of ransomware does BigFix protect against?
BigFix doesn’t target specific ransomware names, but its capabilities (patching, endpoint monitoring, etc.) protect against a wide range of ransomware variants.
How does BigFix integrate with other security tools?
BigFix can integrate with various security information and event management (SIEM) systems and threat intelligence platforms, enhancing its threat detection and response capabilities.
Is BigFix suitable for all organizations, regardless of size?
Yes, BigFix offers scalable solutions adaptable to organizations of all sizes, from small businesses to large enterprises.
What’s the cost of implementing BigFix?
The cost of BigFix varies depending on the specific features and the number of managed endpoints. Contact IBM for pricing details.





