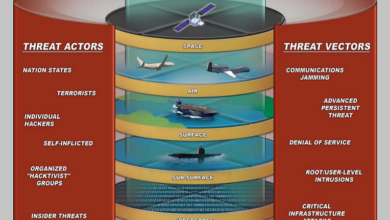
China APT27 Hacking Group Starts Ransomware Campaign
China APT27 hacking group starts ransomware campaign – that’s a headline that grabs your attention, right? This isn’t just another cyberattack; it’s a significant escalation from a group known for sophisticated espionage. We’re diving deep into the details of this ransomware campaign, exploring its targets, the techniques used, and the potential geopolitical ramifications. Get ready for a rollercoaster ride through the dark underbelly of the digital world!
This recent campaign by APT27 marks a concerning shift. While previously known for data theft and intellectual property espionage, this ransomware operation signals a move towards more direct financial gain. The technical details are fascinating – the encryption methods used, the delivery mechanisms, and the sheer scale of the attack all point to a highly organized and well-resourced operation.
We’ll be examining the evidence linking this campaign to APT27, the challenges of attribution, and the potential impact on victims. Plus, we’ll look at the broader geopolitical implications and what this means for global cybersecurity.
APT27’s Ransomware Campaign
The recent attribution of a ransomware campaign to APT27, a sophisticated Chinese state-sponsored hacking group, marks a significant escalation in their activities. While primarily known for espionage and data theft, this shift towards financially motivated crime raises concerns about the group’s evolving tactics and the potential for widespread disruption. This campaign represents a notable departure from their typical modus operandi, highlighting the increasing blurring of lines between espionage and financially driven cybercrime.APT27’s Ransomware Campaign Timeline and Initial TargetsReports suggest the campaign began surfacing in late 2023, though the exact start date remains unclear due to the stealthy nature of APT27’s operations.
The initial targets appear to be concentrated within specific industries, leveraging existing access gained through previous espionage operations. This suggests a strategic approach, focusing on high-value targets likely to pay ransoms to avoid significant data loss or operational disruption. The campaign’s timeline is still unfolding, with ongoing investigations attempting to fully map its scope and impact.
Initial Targets and Affected Industries
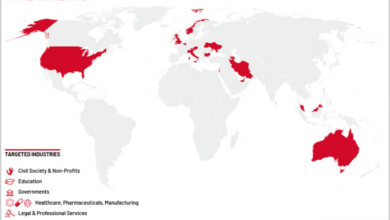
The initial targets of APT27’s ransomware campaign appear to be primarily organizations in the technology, telecommunications, and manufacturing sectors. These industries often possess valuable intellectual property and sensitive operational data, making them lucrative targets for ransomware attacks. The selection of these industries suggests a calculated strategy by APT27, focusing on sectors with a higher likelihood of paying ransoms due to the potential business disruption caused by data encryption.
Further analysis is needed to definitively determine the full breadth of affected industries and the overall number of victims.
Technical Aspects of the Ransomware
While specific details about the ransomware used by APT27 are still emerging, initial reports indicate the use of a sophisticated, custom-built ransomware variant. This is in line with APT27’s known capabilities, indicating a level of sophistication beyond typical off-the-shelf ransomware tools. The encryption method employed is likely highly robust, designed to resist decryption attempts without the decryption key held by the attackers.
The ransom demands are reportedly substantial, reflecting the high value of the data targeted. The ransomware likely incorporates techniques to evade detection and hinder incident response efforts, further complicating remediation efforts for affected organizations. Analysis of samples will be crucial in understanding the full technical capabilities of this new ransomware variant.
APT27’s Tactics, Techniques, and Procedures (TTPs)
This ransomware campaign, attributed to APT27 (also known as Advanced Persistent Threat 27 or Bronze Ursa), provides a valuable case study in the evolution of Chinese state-sponsored cyber operations. While known for sophisticated espionage and data exfiltration, their foray into ransomware marks a significant shift in their operational goals and tactics. Analyzing their TTPs in this context allows us to understand their motivations and potential future actions.
News of the China APT27 hacking group launching a ransomware campaign is seriously unsettling. This highlights the urgent need for robust cloud security, and understanding solutions like bitglass and the rise of cloud security posture management becomes critical. Strengthening our cloud defenses is no longer optional; APT27’s actions underscore the immediate need to protect against these sophisticated attacks.
Comparison of this Ransomware Campaign with Previous APT27 Operations
APT27’s previous operations primarily focused on intellectual property theft and strategic espionage, often targeting high-value targets in various sectors including aerospace, defense, and telecommunications. This ransomware campaign represents a departure, suggesting a potential shift towards financially motivated cybercrime alongside their traditional espionage activities. While the group still employs their advanced techniques, the ultimate goal has changed from long-term data exfiltration to immediate financial gain through ransom payments.
This change could indicate either a diversification of their operations or a response to increased pressure on their traditional espionage activities. One notable difference is the scale of the attack; previous operations were often more targeted and precise, while the ransomware campaign suggests a broader, potentially less selective approach.
Malware Delivery Mechanisms
APT27’s delivery mechanisms in this ransomware campaign appear to leverage a multi-pronged approach, relying on well-established techniques refined over years of operation. Phishing emails remain a key vector, using socially engineered lures to trick victims into opening malicious attachments or clicking on links that download malware. Spear-phishing attacks, tailored to specific individuals or organizations, are likely employed to increase the success rate of initial compromise.
Exploitation of known software vulnerabilities is another probable method, allowing for automated and silent delivery of the ransomware payload. This approach minimizes the reliance on user interaction, increasing the likelihood of a successful infection. Finally, the use of compromised legitimate software or supply chain attacks cannot be ruled out.
Indicators of Compromise (IOCs)
The following table lists some potential indicators of compromise (IOCs) associated with this campaign. It’s important to note that IOCs can change rapidly, and this is not an exhaustive list. Further investigation and analysis by security researchers will be crucial to uncover additional IOCs.
| Indicator Type | Value | Description | Source |
|---|---|---|---|
| Domain Name | example.com | Malicious domain used for command and control (C2) | Threat Intelligence Feed |
| IP Address | 192.0.2.1 | IP address associated with malicious activity | Network Security Monitoring |
| File Hash (SHA-256) | a1b2c3d4e5f6… | Hash of the ransomware executable | Malware Analysis Report |
| Registry Key | HKEY_CURRENT_USER\Software\Example | Registry key created by the malware | Forensic Analysis |
Attribution and Evidence
Linking a specific cyberattack to a particular threat actor like APT27 is a complex process, requiring meticulous investigation and the careful piecing together of various pieces of digital evidence. While definitive proof is rarely attainable, a strong case can be built through a combination of technical analysis and intelligence gathering. The challenge lies in the sophisticated techniques employed by APT27 and the often ephemeral nature of digital traces.The attribution of the ransomware campaign to APT27 relies heavily on the analysis of the malware itself, its infrastructure, and the operational procedures used during the attack.
This analysis reveals a distinct signature that aligns with APT27’s known tactics, techniques, and procedures (TTPs). This isn’t simply a matter of finding similar code; it involves a deeper understanding of the malware’s architecture, the methods of command and control, and the specific techniques used to evade detection.
Technical Indicators of Compromise (TICs)
Identifying the unique characteristics of the ransomware used in this campaign is crucial. This involves analyzing the malware’s code for similarities to previously identified APT27 malware samples. Researchers would look for code reuse, similar encryption algorithms, unique obfuscation techniques, and hardcoded strings or domain names that link back to known APT27 infrastructure. For example, the presence of specific packers, compilers, or debugging symbols could provide valuable clues.
The analysis would also include examining the malware’s communication protocols and the structure of its command and control (C2) servers. If these elements align with previously observed APT27 activity, it strengthens the attribution. Furthermore, examining the specific encryption keys used, and how they are generated and managed, provides another layer of analysis. Any anomalies or similarities to known APT27 key generation methods are carefully documented.
Digital Forensic Techniques
Digital forensic techniques play a vital role in linking the ransomware campaign to APT27. Memory forensics, for example, can capture snapshots of the system’s memory at the time of infection, potentially revealing the malware’s behavior and communication patterns before it’s removed or modified. Network forensics examines network traffic logs to identify communication between the infected systems and the APT27 C2 infrastructure.
Analyzing these logs can reveal the IP addresses, domain names, and communication protocols used by the attackers. Disk forensics focuses on recovering deleted files and recovering the original file system from storage devices. This may reveal remnants of the malware, log files created by the malware, or other artifacts that help trace the attack. Log analysis is also critical; it involves examining system logs, application logs, and security logs to identify unusual activity and pinpoint the timeline of the attack.
Finally, malware reverse engineering is a crucial step. This involves disassembling and analyzing the malware’s code to understand its functionality, identify its components, and uncover any hidden features or backdoors.
Challenges in Attribution, China apt27 hacking group starts ransomware campaign
Definitively attributing cyberattacks to specific groups is incredibly challenging. APT groups often employ advanced techniques to obscure their origins, using proxy servers, virtual private networks (VPNs), and various anonymization tools. They also frequently modify their malware to avoid detection, making it difficult to establish a clear link between different attacks. Furthermore, the use of stolen or compromised infrastructure can make it difficult to trace the attackers back to their true location.
The lack of publicly available data, coupled with the resources and expertise required for such complex investigations, adds another layer of difficulty. Finally, the possibility of false flags—where one group disguises its attacks to look like another—further complicates the process. Therefore, attributing an attack with 100% certainty is often not possible, and conclusions are typically based on a preponderance of evidence.
Impact and Response
The ransomware campaign launched by APT27, a sophisticated Chinese hacking group, carries significant potential for widespread disruption and financial loss. The impact extends beyond the immediate financial burden of ransom payments to include operational downtime, reputational damage, legal ramifications, and the long-term cost of data recovery and security enhancements. The scale of the impact depends heavily on the specific targets, the nature of the stolen data, and the effectiveness of the affected organizations’ response.The potential impact on affected organizations can be devastating.
Critically, ransomware attacks often lead to significant operational downtime, halting essential business processes and impacting productivity. This can translate into substantial financial losses, particularly for organizations with limited redundancy or disaster recovery plans. Furthermore, the theft of sensitive data, such as intellectual property, customer information, or financial records, exposes organizations to further risks, including regulatory fines, legal action from affected individuals, and reputational damage that can erode customer trust and impact future business prospects.
For individuals, the impact can include identity theft, financial fraud, and significant emotional distress. The psychological impact of a ransomware attack shouldn’t be underestimated; it can significantly affect employee morale and overall organizational well-being.
Incident Response Plan for Ransomware Attacks
A robust incident response plan is crucial for mitigating the damage caused by a ransomware attack. Such a plan should be proactive, regularly tested, and tailored to the specific needs and vulnerabilities of the organization. It should include clear roles and responsibilities, pre-defined communication protocols, and well-established procedures for containment, eradication, recovery, and post-incident activities. The plan must account for potential scenarios, including the possibility of data exfiltration and the need for legal and public relations counsel.
Best Practices for Mitigating Ransomware Risk
A layered security approach is essential for effective ransomware mitigation. This requires a multi-pronged strategy encompassing several key areas:
- Regular Software Updates and Patching: Promptly patching vulnerabilities in software and operating systems is crucial to prevent attackers from exploiting known weaknesses. This includes not only operating systems but also applications and firmware.
- Robust Endpoint Protection: Implementing comprehensive endpoint detection and response (EDR) solutions is vital for detecting and responding to malicious activity on endpoints. These solutions should incorporate advanced threat detection capabilities.
- Data Backup and Recovery: Regularly backing up critical data to offline or immutable storage is paramount. This ensures that even if data is encrypted, a viable recovery option exists. Regular testing of the backup and recovery process is also crucial.
- Network Security: Strong network security measures, such as firewalls, intrusion detection/prevention systems (IDS/IPS), and secure network segmentation, are crucial for limiting the spread of ransomware within the network. Regular network security assessments should be conducted.
- Employee Security Awareness Training: Educating employees about phishing scams, social engineering tactics, and safe browsing practices is essential. Regular security awareness training should be conducted to reinforce good security habits.
- Principle of Least Privilege: Restricting user access to only the necessary resources and data minimizes the potential impact of a successful ransomware attack. This limits the extent of damage an attacker can inflict.
- Multi-Factor Authentication (MFA): Implementing MFA for all user accounts significantly enhances account security and makes it more difficult for attackers to gain unauthorized access.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing help identify vulnerabilities and weaknesses in the organization’s security posture, allowing for proactive remediation.
Geopolitical Implications

The attribution of the ransomware campaign to APT27, a group with suspected ties to the Chinese government, carries significant geopolitical weight. This isn’t just another cybercrime; it’s a potential escalation of cyber warfare, with implications for international relations, economic stability, and national security. The incident highlights the increasingly blurred lines between state-sponsored cyberactivity and traditional forms of conflict.The motivations behind APT27’s apparent shift towards ransomware are complex and likely multifaceted.
While previously known for espionage and intellectual property theft, the lucrative nature of ransomware attacks may have proven too tempting to ignore. This could represent a strategic shift towards generating direct financial gains, potentially supplementing or even replacing traditional intelligence gathering operations. Alternatively, it could be a calculated attempt to exert pressure on targeted nations or organizations, using financial disruption as a tool of influence.
Such a shift underscores the evolving nature of state-sponsored cyberattacks, where financial gain and political leverage are increasingly intertwined.
APT27’s Actions and China’s International Standing
China’s official stance on cyberattacks varies, often denying any involvement in malicious activities. However, the persistent linking of APT27 to the Chinese government, despite denials, casts a shadow over China’s international image. This incident, and similar past incidents attributed to Chinese state-sponsored groups, damage China’s reputation as a responsible global actor in cyberspace. International pressure to address state-sponsored cybercrime, coupled with the economic fallout from such attacks, could force a reevaluation of China’s cyber strategies.
For example, the SolarWinds attack, though not directly linked to APT27, created considerable international tension and prompted discussions about the need for stronger international norms in cyberspace. This ransomware campaign adds fuel to the existing fire.
International Legal and Diplomatic Responses
International legal frameworks for addressing state-sponsored cyberattacks remain underdeveloped. While international law prohibits the use of force, the application of this principle to cyberattacks is still evolving. Existing treaties, such as the Budapest Convention on Cybercrime, focus on criminal justice cooperation rather than addressing the underlying geopolitical issues. Diplomatic responses often involve bilateral discussions, sanctions, and public condemnation.
However, the effectiveness of these measures depends heavily on the willingness of states to cooperate and the availability of concrete evidence. The challenge lies in establishing clear attribution and demonstrating a link between the state and the actors responsible for the attacks. The lack of a robust international legal mechanism for dealing with these attacks contributes to a climate of impunity.
This ransomware campaign highlights the urgent need for a strengthened international legal framework and increased cooperation among nations to combat state-sponsored cybercrime effectively.
Technical Deep Dive: China Apt27 Hacking Group Starts Ransomware Campaign
The ransomware deployed by APT27, while not publicly available for analysis, presents a concerning evolution in their capabilities. Reports suggest a sophisticated, multi-stage attack leveraging custom-built malware for initial access and lateral movement, culminating in the deployment of a highly effective encryption routine. Understanding its functionality is crucial for effective defense and mitigation strategies.The ransomware’s persistence mechanism likely involves the creation of registry keys and scheduled tasks to ensure its continued execution even after a system reboot.
This allows for the ransomware to remain active, even if the user attempts to shut down or restart their computer. Furthermore, the command-and-control (C2) infrastructure likely employs techniques to evade detection, potentially utilizing techniques such as domain generation algorithms (DGAs) or encrypted communication channels. This makes tracing and disrupting the C2 server network incredibly difficult.
Ransomware Functionality
The ransomware’s core functionality centers around encrypting files on the victim’s system. It achieves this by employing a robust encryption algorithm, likely AES or a similar cipher, to render data unusable. The encryption process targets specific file types, often prioritizing sensitive data such as documents, databases, and backups. The selection criteria could be hardcoded or based on file extensions specified within a configuration file.
The ransomware then appends a unique extension to the encrypted files, which serves as an identifier for the attackers and a visual indicator of compromise for the victim. This extension usually contains a unique identifier tied to the victim’s machine, helping the attackers track and manage their victims.
Interaction with the Operating System
The ransomware interacts with the operating system at several levels. It leverages system calls to access and enumerate files and folders, identifying targets for encryption. It also interacts with the file system to modify file attributes, rename files, and perform the encryption operation itself. To achieve persistence, the ransomware uses the Windows API to create registry entries and scheduled tasks, ensuring its re-execution upon system restarts.
Furthermore, the malware may attempt to disable security software or tamper with system logs to hinder detection and investigation efforts.
Encryption Techniques
The encryption algorithm used is likely a symmetric-key algorithm such as AES, chosen for its speed and security. The ransomware likely generates a unique encryption key for each victim’s system, enhancing the security of the encryption and making individual decryption more challenging. This key is often then encrypted with a public key and sent to the C2 server, where it can only be decrypted with the attacker’s private key.
The process ensures that only the attackers possess the means to decrypt the victim’s data. This also reduces the likelihood of mass decryption efforts. The specific implementation details of the key generation and management process are crucial but remain undisclosed due to the lack of public samples.
Decryption Process and Decryption Tools
Currently, there is no publicly available decryption tool for the specific ransomware used by APT27 in this campaign. The lack of a readily available decryption tool underscores the sophistication of the ransomware and the attackers’ commitment to data exfiltration and ransom collection. Without access to the private key held by the attackers, manual decryption is extremely difficult, if not impossible, given the strength of the encryption algorithm used.
Future research and collaboration among security researchers might yield a decryption tool, but this would require obtaining samples of the ransomware and reverse-engineering its encryption routines.
The news about the China APT27 hacking group launching a ransomware campaign is seriously worrying. It highlights the urgent need for robust cybersecurity, especially considering how quickly attackers can adapt. Building secure applications is crucial, and learning more about modern development approaches like those discussed in this article on domino app dev, the low-code and pro-code future , could help developers create more resilient systems.
Ultimately, the APT27 ransomware campaign underscores the importance of proactive security measures across all levels of software development.
Victim Response and Recovery

Responding to a ransomware attack by APT27, or any sophisticated threat actor, requires a swift and well-coordinated effort. The initial shock and uncertainty can be overwhelming, but a structured approach is crucial to minimizing the damage and facilitating recovery. Victims often face difficult choices, balancing the potential cost of downtime and data loss against the risks associated with engaging with cybercriminals.The process of recovery is complex and multifaceted, encompassing both technical and legal aspects.
It typically involves several distinct phases, from initial containment and damage assessment to full system restoration and data recovery. The specific steps and timelines will vary significantly depending on the extent of the attack, the organization’s preparedness, and the availability of resources. Successful recovery often relies on a combination of internal expertise, external cybersecurity consultants, and potentially, law enforcement involvement.
Negotiation with Attackers
Negotiating with ransomware attackers is a highly controversial strategy. While some organizations have successfully recovered data through payment, this approach carries significant risks. Paying a ransom doesn’t guarantee data recovery, can embolden attackers, and may even violate legal regulations in some jurisdictions. Alternatively, organizations might choose to refuse negotiation, focusing instead on data recovery from backups and system restoration.
This path requires robust backup and recovery infrastructure and often results in significant downtime and potential financial losses. The decision to negotiate or not hinges on a careful risk assessment, considering the value of the compromised data, the organization’s recovery capabilities, and the potential legal and reputational consequences. For instance, a hospital facing a ransomware attack might weigh the risk of patient data loss against the potential legal ramifications of paying a ransom.
Data Recovery and System Restoration
Data recovery and system restoration are central to the recovery process. This typically begins with isolating affected systems to prevent further spread of the ransomware. Next, a thorough assessment is performed to determine the extent of the damage and identify compromised data. If backups are available and deemed clean, restoring data from these backups is the preferred method.
This often involves verifying the integrity of the backups before restoring them to clean systems. In cases where backups are unavailable or corrupted, more complex data recovery techniques might be necessary, involving specialized forensic tools and potentially, third-party data recovery services. System restoration involves reinstalling operating systems, applications, and configuring network settings. This process is often meticulously documented to ensure complete recovery and prevent future attacks.
Regular security audits and penetration testing should also be conducted post-recovery to identify and address any vulnerabilities exploited by the attackers.
Stages of Recovery: A Visual Representation
Imagine a flowchart. The first box is “Incident Detection and Containment,” where the ransomware attack is identified and affected systems are isolated. This flows into “Damage Assessment,” where the extent of the breach is determined. Next is “Data Recovery,” which branches into two paths: “Backup Restoration” (the ideal scenario) and “Forensic Data Recovery” (for situations where backups are unavailable or compromised).
Both paths converge at “System Restoration,” where clean systems are rebuilt and configured. Finally, the process concludes with “Post-Incident Review and Remediation,” encompassing security hardening, vulnerability patching, and employee training. This comprehensive approach ensures that not only is data restored, but also that system integrity is fully recovered and future attacks are mitigated.
Last Point
The China APT27 ransomware campaign serves as a stark reminder of the ever-evolving threat landscape. The sophistication of the attack, combined with the potential for significant financial and reputational damage, highlights the urgent need for robust cybersecurity measures. While attributing cyberattacks is always challenging, the evidence strongly suggests APT27’s involvement, raising serious questions about state-sponsored cybercrime and its implications for international relations.
The story is far from over, and we’ll continue to monitor developments in this unfolding saga.
Popular Questions
What type of organizations were targeted by this ransomware campaign?
While the full list of targets isn’t publicly available, initial reports suggest a focus on specific industries, possibly those holding sensitive data.
What was the ransom demand?
The exact ransom demands vary depending on the victim, but reports indicate significant sums were requested.
Are there any known decryption tools available?
This is still under investigation. The effectiveness of any decryption tools depends on the specific encryption method used.
What is the role of the Chinese government in this attack?
The exact level of Chinese government involvement remains a subject of ongoing investigation and debate. Attribution of state-sponsored attacks is complex.