Costa Ricas Ransomware Emergency & Colonial Pipelines $1M Penalty
Costa Rica declares ransomware emergency and colonial pipeline cyber attack fetches 1 million penalty – these headlines highlight a growing global threat. This isn’t just about money; it’s about the crippling impact of ransomware on essential services, from government operations to fuel distribution. We’ll delve into the specifics of both attacks, exploring the vulnerabilities exploited, the devastating consequences, and the crucial lessons learned about cybersecurity preparedness.
We’ll also examine the international cooperation needed to combat this escalating threat and discuss strategies for bolstering our collective defenses.
The recent ransomware attack against Costa Rica’s government brought the country to a standstill, disrupting essential services and highlighting the vulnerability of critical infrastructure. Simultaneously, the Colonial Pipeline attack, though seemingly resolved, continues to serve as a stark reminder of the significant financial and operational repercussions of such breaches. This post compares and contrasts these two high-profile incidents, examining the differing responses, the long-term impacts, and the urgent need for improved cybersecurity practices worldwide.
Costa Rica’s Ransomware Emergency
Costa Rica faced a significant cybersecurity crisis in 2023 when a sophisticated ransomware attack crippled its government infrastructure. This wasn’t just a minor disruption; it highlighted the vulnerability of even developed nations to increasingly sophisticated cyberattacks and the potentially devastating consequences for essential public services. The incident served as a stark reminder of the need for robust cybersecurity defenses and international cooperation in combating cybercrime.
Details of the Ransomware Attack
The attack, attributed to the Conti ransomware group (now defunct), began in April 2023. The hackers infiltrated various government agencies, encrypting sensitive data and demanding a substantial ransom in cryptocurrency. The Conti group is known for its aggressive tactics and targeting of critical infrastructure. The attack involved a multi-pronged approach, exploiting vulnerabilities in various systems and deploying malware to spread laterally within the network.
This allowed them to gain control over numerous government computers and servers. The scale of the breach was significant, affecting multiple ministries and disrupting a wide range of services.
Impact on Essential Government Services
The immediate impact on Costa Rica was severe. Numerous government services experienced significant disruptions, including tax collection, healthcare systems, and educational institutions. Citizens faced delays in accessing vital services, impacting everything from paying taxes to receiving medical care. The disruption to the healthcare system was particularly concerning, as it potentially jeopardized patient care and the administration of essential medical resources.
The attack also caused significant economic disruption, impacting businesses and the overall economy. Data breaches exposed sensitive citizen information, raising concerns about identity theft and other privacy violations.
Timeline of Events
April 2023
Initial ransomware attack detected within Costa Rican government systems.
April – May 2023
Attack spreads across multiple government agencies, disrupting services. The government begins to assess the damage and initiates a response.
May 2023
Costa Rica declares a state of national emergency due to the severity of the cyberattack and its impact on essential services. International assistance is sought.
May – June 2023
The government works to restore systems, recover data, and enhance cybersecurity defenses. Investigations into the attack are underway.
Ongoing
Recovery efforts continue, with a focus on long-term cybersecurity improvements and prevention measures. The government is also exploring legal options to pursue the perpetrators.
Comparison with Other Significant Ransomware Incidents
The Costa Rican attack is one of many significant ransomware incidents targeting governments and critical infrastructure globally. Below is a comparison to other notable attacks:
| Date | Target | Ransomware Used | Impact |
|---|---|---|---|
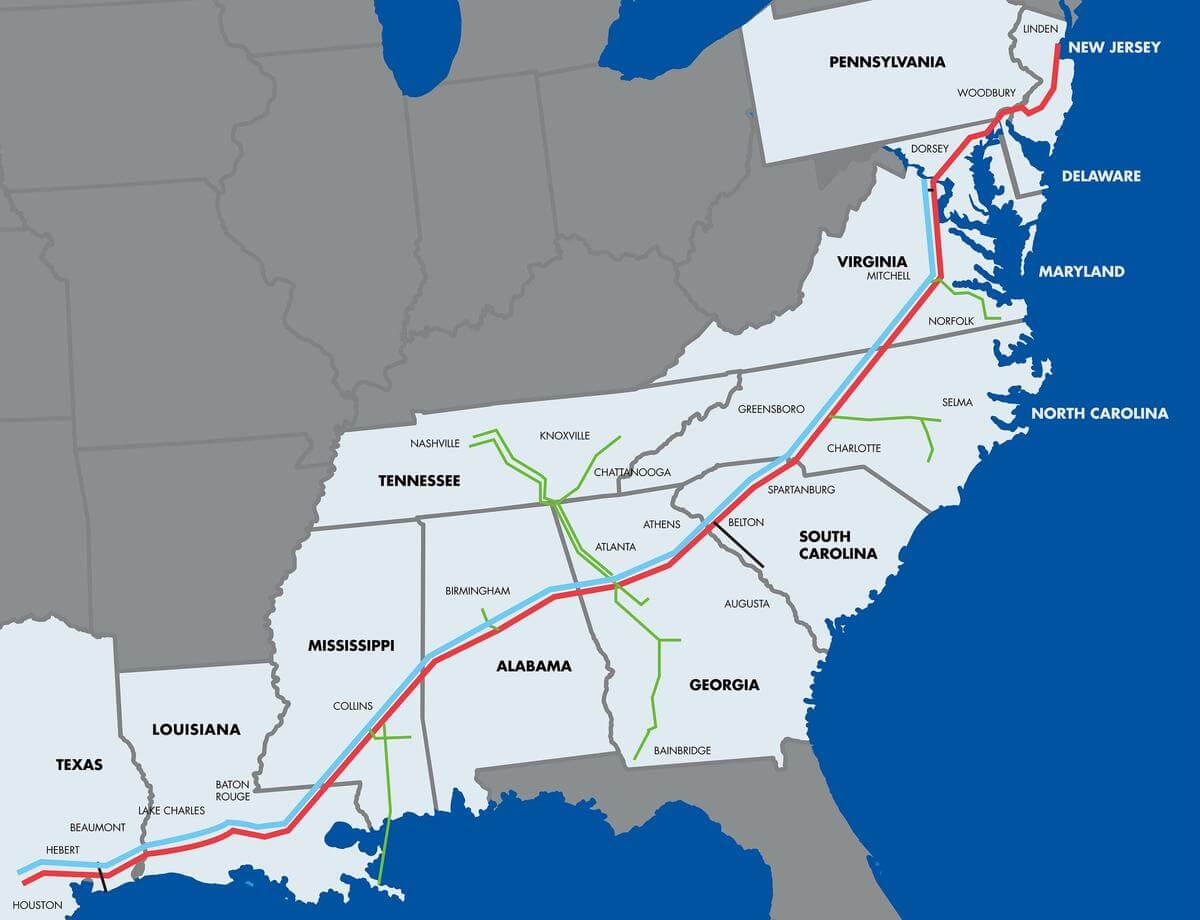
| May 2021 | Colonial Pipeline (USA) | DarkSide | Fuel shortages across the East Coast; $4.4 million ransom paid. |
| 2021 | City of Atlanta (USA) | SamSam | Disruption of city services; significant financial losses. |
| 2020 | Travelex (UK) | Sodinuqi | Global disruption of foreign exchange services; significant financial losses. |
| 2023 | Costa Rican Government | Conti | Disruption of essential government services; significant economic and social impact. |
Colonial Pipeline Attack
The Colonial Pipeline ransomware attack in May 2021 served as a stark reminder of the vulnerability of critical infrastructure to cyberattacks. The incident, which crippled a major fuel pipeline supplying the East Coast of the United States, highlighted the significant economic and societal consequences of successful ransomware deployments against essential services. This event prompted a wave of regulatory scrutiny and spurred companies to reassess their cybersecurity posture.The attack’s impact extended far beyond the immediate disruption of fuel supplies.
It exposed weaknesses in cybersecurity defenses and raised concerns about the preparedness of critical infrastructure providers to withstand sophisticated cyberattacks. The long-term effects continue to ripple through the industry, forcing a reassessment of risk management strategies and prompting significant investments in cybersecurity infrastructure.
Financial Penalties Against Colonial Pipeline
While the exact amount paid to the DarkSide ransomware group remains undisclosed, Colonial Pipeline faced significant financial penalties related to the attack. These penalties included direct costs associated with the incident response, including paying the ransom, restoring systems, and hiring cybersecurity experts. Indirect costs, such as lost revenue due to the shutdown, legal fees, and reputational damage, were substantially higher.
The company also faced regulatory scrutiny and potential fines from various government agencies, although the precise figures are not publicly available in a consolidated form. It’s crucial to note that the payment of the ransom itself remains a point of contention, sparking debate about the ethical and practical implications of paying cybercriminals.
Long-Term Consequences for Colonial Pipeline
The Colonial Pipeline attack had profound and lasting consequences for the company. Beyond the immediate financial losses, the attack severely damaged the company’s reputation, raising questions about its cybersecurity capabilities and its ability to protect critical infrastructure. The incident prompted increased regulatory oversight, leading to stricter compliance requirements and potentially higher insurance premiums. The long-term operational consequences included increased investment in cybersecurity infrastructure, staff training, and incident response planning.
The attack also led to a reevaluation of the company’s risk management strategies and a greater focus on proactive security measures to prevent future incidents.
Colonial Pipeline’s Response Strategies
Colonial Pipeline’s response to the attack involved a multi-pronged approach. This included immediate efforts to contain the ransomware, followed by a phased restoration of its systems. The company engaged cybersecurity experts to assist in the investigation and remediation efforts. They also collaborated with law enforcement agencies and government officials to share information and coordinate the response. Communication with stakeholders, including customers and the public, was a crucial aspect of their response, although the initial lack of transparency drew criticism.
The incident highlighted the importance of robust incident response plans, including clear communication protocols and well-defined roles and responsibilities.
Cybersecurity Measures: Colonial Pipeline vs. Costa Rican Government
Comparing the cybersecurity measures in place at Colonial Pipeline and the Costa Rican government reveals significant differences. While specific details regarding Costa Rica’s government cybersecurity infrastructure remain partially undisclosed for security reasons, the Colonial Pipeline attack exposed vulnerabilities that likely contrast with the government’s approach. The Colonial Pipeline’s initial reliance on older technology and insufficient security protocols contributed to the success of the ransomware attack.
It is likely that a national government, while facing different challenges in terms of scale and complexity, would (or should) have more robust, layered security defenses, including advanced threat detection, regular security audits, and stronger access control measures. The difference lies in the scale and resources dedicated to cybersecurity, as well as the potential for centralized coordination and oversight within a governmental structure compared to a private entity.
However, both entities ultimately face the challenge of adapting to the ever-evolving landscape of cyber threats.
The Role of Cybersecurity in Critical Infrastructure: Costa Rica Declares Ransomware Emergency And Colonial Pipeline Cyber Attack Fetches 1 Million Penalty
The recent ransomware attacks against Costa Rica’s government and the Colonial Pipeline highlight the critical need for robust cybersecurity measures protecting essential services. These incidents underscore the devastating consequences – from crippling government operations to widespread fuel shortages – when critical infrastructure falls victim to cyberattacks. A proactive and comprehensive approach to cybersecurity is no longer a luxury but a necessity for national security and economic stability.
A Hypothetical National Cybersecurity Plan to Mitigate Ransomware Attacks
A national cybersecurity plan must be multi-layered and encompass various strategies. It should begin with a comprehensive risk assessment identifying critical infrastructure components and their vulnerabilities. This assessment should inform the development of a robust incident response plan, including clear communication protocols and established escalation procedures. The plan should mandate regular security audits and penetration testing to identify weaknesses before attackers can exploit them.
Furthermore, employee training on cybersecurity best practices, including phishing awareness and safe password management, is crucial. The government should invest heavily in advanced threat detection and response capabilities, including intrusion detection systems and security information and event management (SIEM) tools. Finally, strong collaboration between government agencies, private sector entities, and international partners is vital for information sharing and coordinated responses to threats.
This collaborative approach enables faster threat detection and facilitates the sharing of best practices and remediation strategies.
Key Vulnerabilities Exploited in the Costa Rica and Colonial Pipeline Incidents
The attacks on Costa Rica and the Colonial Pipeline exposed several critical vulnerabilities. In Costa Rica’s case, the attackers exploited weaknesses in the government’s network security, likely gaining initial access through phishing emails or exploiting unpatched software vulnerabilities. The ransomware then spread laterally across the network, encrypting critical data and disrupting essential services. The Colonial Pipeline attack, on the other hand, involved exploiting a known vulnerability in a virtual private network (VPN) system.
This allowed attackers to gain unauthorized access to the pipeline’s operational technology (OT) network, ultimately leading to the shutdown of the pipeline. Both incidents highlight the dangers of outdated software, insufficient employee training, and inadequate network segmentation. The lack of multi-factor authentication also contributed to the success of these attacks.
Best Practices for Improving Ransomware Resilience
Organizations must adopt a proactive approach to enhance their ransomware resilience. This begins with implementing strong network segmentation to limit the impact of a successful breach. Regular software patching and updates are crucial to eliminate known vulnerabilities. Multi-factor authentication (MFA) should be mandated for all user accounts to prevent unauthorized access. Robust data backups, regularly tested and stored offline, are essential for data recovery in the event of a ransomware attack.
The news about Costa Rica’s ransomware emergency and the Colonial Pipeline’s $1 million penalty really highlights the urgent need for robust cybersecurity. Building secure, resilient systems is crucial, and that’s where learning more about domino app dev, the low-code and pro-code future , comes in. Understanding modern development approaches can help organizations better protect themselves against these kinds of attacks, ultimately reducing the risk of similar devastating incidents.
Employee cybersecurity awareness training should be a continuous process, covering topics like phishing, social engineering, and safe browsing practices. Finally, incident response planning and regular tabletop exercises are crucial to ensure a coordinated and effective response to a ransomware attack. These exercises help organizations test their plans and identify areas for improvement. Investing in threat intelligence services can also help proactively identify and mitigate potential threats.
The Role of Proactive Threat Intelligence in Preventing Future Attacks
Proactive threat intelligence plays a vital role in preventing future ransomware attacks. By monitoring threat actor activity, vulnerabilities, and emerging attack techniques, organizations can proactively identify and mitigate potential risks. Threat intelligence feeds can provide early warning signs of impending attacks, allowing organizations to take preventative measures, such as patching vulnerable systems or implementing additional security controls. This proactive approach significantly reduces the likelihood of a successful attack.
For example, if threat intelligence reveals a new ransomware variant targeting a specific vulnerability, organizations can patch their systems before they become victims. Furthermore, threat intelligence can inform the development of more effective security policies and procedures. The ability to anticipate and respond to threats before they materialize is paramount to mitigating risk.
Economic and Societal Impacts

The ransomware attacks on Costa Rica and the Colonial Pipeline, while geographically distinct, both highlight the devastating economic and societal consequences of successful cyberattacks targeting critical infrastructure. The ripple effects extend far beyond the immediate victims, impacting citizens, businesses, and national economies in profound ways. Understanding these impacts is crucial for developing effective preventative measures and response strategies.The Costa Rican ransomware attack, orchestrated by Conti, crippled government services for weeks, severely impacting essential functions like tax collection, healthcare, and education.
This disruption caused significant economic hardship for citizens and businesses alike. Businesses experienced delays in payments, difficulty accessing government services, and a general sense of uncertainty, leading to decreased productivity and investment. The government, meanwhile, faced significant losses in revenue and incurred substantial costs in recovering from the attack, diverting funds from other essential public services. The attack also damaged Costa Rica’s international reputation, potentially affecting foreign investment and tourism.
Economic Impacts of the Costa Rica Attack
The economic damage from the Costa Rica attack is difficult to quantify precisely, but estimates suggest billions of colones in losses. This includes direct costs like ransom payments (though the Costa Rican government refused to pay), the cost of remediation, and lost productivity. Indirect costs are even harder to measure, encompassing lost business opportunities, decreased investor confidence, and the long-term impact on economic growth.
The disruption to vital government services like tax collection resulted in a significant shortfall in government revenue, impacting public spending and potentially leading to increased public debt. Furthermore, the attack undermined the country’s digital infrastructure, a critical element for attracting foreign investment and fostering economic development. The impact on small and medium-sized enterprises (SMEs), which form the backbone of the Costa Rican economy, was particularly severe, as many lacked the resources to recover quickly from the attack.
Societal Disruption in Costa Rica
The disruption of government services caused significant societal disruption. The healthcare system faced delays in accessing medical records and scheduling appointments, impacting patient care. Educational institutions struggled with online learning platforms, leading to disruptions in the education of thousands of students. Access to vital government services like passport applications and driver’s license renewals was severely limited, causing significant inconvenience and hardship for citizens.
The overall sense of insecurity and uncertainty fueled public anxiety and eroded trust in the government’s ability to protect critical infrastructure. The long-term societal impact of this disruption could include increased inequality, hampered economic mobility, and a decline in public trust.
Comparison of Economic Impacts: Costa Rica vs. Colonial Pipeline
While both attacks caused significant economic damage, the nature of the impact differed. The Colonial Pipeline attack, which temporarily shut down a major fuel pipeline, caused immediate and widespread fuel shortages across the eastern United States. This led to panic buying, price spikes, and disruptions to various industries reliant on fuel transportation. The economic impact was felt acutely and rapidly, with estimates placing the cost in the hundreds of millions of dollars.
The Costa Rica attack, on the other hand, had a more prolonged and diffuse impact, affecting various sectors over a longer period. While the immediate impact might not have been as visually striking as the fuel shortages, the long-term economic consequences could be equally, if not more, damaging. The Colonial Pipeline attack’s impact was more concentrated geographically and temporally, while Costa Rica’s was more widespread and sustained.
Potential Long-Term Consequences
The long-term consequences for both countries are significant and multifaceted.
- Costa Rica: Increased investment in cybersecurity infrastructure, potential for long-term economic stagnation if recovery efforts are insufficient, erosion of public trust in government, and a potential chilling effect on foreign investment.
- United States (Colonial Pipeline): Increased scrutiny of cybersecurity practices in critical infrastructure, potential for increased regulation and investment in cybersecurity, and a heightened awareness of the vulnerability of essential services to cyberattacks.
International Cooperation and Response
The escalating threat of ransomware attacks targeting critical infrastructure necessitates a robust and coordinated international response. The interconnected nature of global systems means that a successful attack in one nation can quickly ripple outwards, impacting multiple countries and economies. Therefore, international collaboration isn’t just beneficial; it’s essential for effective mitigation and prevention.International cooperation in combating ransomware requires a multi-faceted approach, encompassing information sharing, joint investigations, and the development of common cybersecurity standards and best practices.
Effective responses rely on the swift exchange of intelligence regarding emerging threats, vulnerabilities, and attacker tactics, techniques, and procedures (TTPs). This collaborative approach fosters a stronger collective defense against these sophisticated cybercriminals.
Successful International Responses to Cyberattacks, Costa rica declares ransomware emergency and colonial pipeline cyber attack fetches 1 million penalty
Several instances demonstrate the effectiveness of international cooperation in addressing major cyberattacks. The NotPetya ransomware outbreak of 2017, while devastating, highlighted the importance of coordinated action. While attribution remains challenging, the international community rallied to share threat intelligence and develop mitigation strategies. This collective response, though not preventing the initial attack, helped limit its spread and accelerated the development of improved security protocols.
Similarly, investigations into attacks targeting financial institutions often involve international collaboration, with law enforcement agencies across multiple countries working together to trace the funds and apprehend the perpetrators. The sharing of forensic data and expertise significantly enhances the chances of successful prosecution.
The Role of International Organizations in Addressing Cybersecurity Threats
International organizations play a crucial role in facilitating international cooperation on cybersecurity. Organizations like Interpol, Europol, and the Cybersecurity and Infrastructure Security Agency (CISA) in the United States, actively work to coordinate investigations, share threat intelligence, and provide technical assistance to member states. They serve as platforms for information exchange, fostering collaboration between law enforcement agencies, cybersecurity experts, and private sector organizations.
Furthermore, international bodies like the United Nations and the Organization for Economic Co-operation and Development (OECD) are increasingly involved in developing international norms and standards for cybersecurity, promoting responsible state behavior in cyberspace, and encouraging international cooperation in this critical area.
A Framework for Improved Information Sharing
An improved framework for information sharing necessitates several key components. First, establishing secure and reliable channels for the rapid exchange of threat intelligence is paramount. This could involve the development of dedicated platforms and protocols, ensuring confidentiality and the protection of sensitive information. Second, harmonizing legal frameworks and data protection regulations across nations is crucial to facilitate cross-border investigations and evidence sharing.
Third, fostering trust and confidence between nations is vital; this requires establishing clear protocols for information sharing, ensuring transparency and accountability in the process. Fourth, investing in capacity building programs to enhance the cybersecurity capabilities of less developed nations is crucial. A strong global response requires that all nations, regardless of their technological capabilities, have access to the resources and expertise needed to defend against cyber threats.
This framework should prioritize the rapid dissemination of information on emerging threats, vulnerabilities, and attacker TTPs, allowing nations to proactively defend their critical infrastructure.
The Human Element in Cybersecurity
The recent ransomware attacks targeting Costa Rica and the Colonial Pipeline highlight a crucial, often overlooked aspect of cybersecurity: the human element. While sophisticated technical defenses are essential, the weakest link in any security system remains the individual user. Human error, coupled with increasingly sophisticated social engineering tactics, continues to be the primary entry point for many successful ransomware attacks.
Understanding these vulnerabilities is paramount to building a truly resilient cybersecurity posture.Employee training and awareness are not simply “best practices”—they are fundamental necessities. A well-trained workforce is far less likely to fall victim to phishing scams, malicious attachments, or other social engineering ploys. Investing in comprehensive cybersecurity awareness training is an investment in the organization’s overall security, significantly reducing the risk of a ransomware infection.
Common Human Errors Contributing to Ransomware Attacks
Numerous human errors consistently contribute to successful ransomware attacks. These errors often stem from a lack of awareness or training. For instance, clicking on malicious links in phishing emails remains a leading cause of infection. Opening seemingly harmless attachments containing malware is another common mistake. Failure to update software promptly leaves systems vulnerable to known exploits, creating easy access points for ransomware.
Finally, weak or easily guessed passwords provide a simple path for attackers to gain unauthorized access. These seemingly minor oversights can have devastating consequences.
With Costa Rica facing a ransomware emergency and the Colonial Pipeline attack resulting in a $1 million penalty, the need for robust cybersecurity is screamingly obvious. Understanding how to effectively manage cloud security is crucial, and that’s where solutions like those discussed in this article on bitglass and the rise of cloud security posture management become invaluable.
These kinds of incidents highlight the urgent need for proactive measures to prevent future attacks and protect vital infrastructure.
The Role of Social Engineering in Ransomware Attacks
Social engineering is the art of manipulating individuals into divulging confidential information or performing actions that compromise security. Ransomware attackers frequently employ social engineering tactics, leveraging human psychology to gain access to systems. Phishing emails, posing as legitimate communications from trusted sources, are a common method. These emails often contain urgent requests, creating a sense of pressure and urgency that can cloud judgment.
Other techniques include pretexting (creating a false scenario to gain trust), baiting (offering enticing rewards), and quid pro quo (offering something in exchange for information). The success of these attacks hinges on exploiting human tendencies towards trust and compliance.
Visual Representation of a Typical Ransomware Attack Lifecycle
Imagine a visual representation as a series of connected boxes. The first box, labeled “Initial Access,” depicts the attacker gaining entry, perhaps via a phishing email. The second box, “Lateral Movement,” shows the attacker moving through the network, often exploiting weak passwords or unpatched systems. The third box, “Data Exfiltration,” illustrates the attacker stealing sensitive data as a backup in case the encryption fails.
The fourth box, “Ransomware Deployment,” shows the malware being deployed, encrypting critical files. The final box, “Ransom Demand,” shows the attacker demanding payment in exchange for decryption keys. This simplified model demonstrates how human error, such as clicking a malicious link in the “Initial Access” stage, can trigger the entire chain of events, leading to a successful ransomware attack.
Ending Remarks
The ransomware attacks on Costa Rica and the Colonial Pipeline underscore a critical need for proactive cybersecurity measures. The multi-million dollar penalty levied against Colonial Pipeline serves as a potent warning to organizations of all sizes. Investing in robust security protocols, employee training, and international collaboration is no longer optional – it’s essential for protecting critical infrastructure and mitigating the devastating consequences of these increasingly sophisticated attacks.
The future of cybersecurity hinges on our collective ability to learn from past mistakes and proactively strengthen our defenses against this evolving threat.
FAQ Explained
What type of ransomware was used in the Costa Rica attack?
While the specific ransomware variant used in the Costa Rica attack wasn’t publicly disclosed immediately, reports suggest it was a sophisticated and customized variant, possibly a variant of Conti or a similar strain.
What were the long-term effects on Colonial Pipeline’s reputation?
The Colonial Pipeline attack severely damaged their reputation, leading to decreased public trust and increased scrutiny of their cybersecurity practices. It highlighted the vulnerability of critical infrastructure and the potential for significant disruption.
How can individuals protect themselves from ransomware?
Individuals can protect themselves by regularly backing up data, being wary of suspicious emails and attachments, keeping software updated, and using strong, unique passwords.
What role did human error play in these attacks?
Human error, such as clicking malicious links or falling prey to phishing scams, often plays a significant role in successful ransomware attacks. Strong security awareness training is crucial.





