Deception Breaches Seeding the Hunt Offensively
Deception breaches and going on the offense to seed the hunt – it sounds like a spy thriller, doesn’t it? And in a way, it is. In the world of cybersecurity, deception is becoming an increasingly important weapon in our arsenal. This isn’t about passively waiting for attackers; it’s about actively luring them in, observing their techniques, and learning how they operate.
We’ll explore the various types of deception breaches, the motivations behind them, and how to use deception proactively to gain a significant advantage in the ongoing battle against cyber threats. Get ready to dive into the shadowy world of cybersecurity deception!
This post will dissect the complex landscape of deception breaches, from understanding their diverse forms and attacker motivations to mastering proactive detection strategies. We’ll cover building resilient systems, analyzing indicators, and responding effectively to breaches. Crucially, we’ll delve into the ethical and practical aspects of employing offensive deception techniques – turning the tables on attackers and using their own tactics against them.
It’s a comprehensive guide to navigating the ever-evolving world of cyber deception.
Defining Deception Breaches
Deception breaches represent a sophisticated evolution in cyberattacks, moving beyond traditional exploit methods to actively lure victims into compromising themselves. Understanding these breaches is crucial for building robust security strategies. They rely on social engineering and cleverly crafted traps to gain unauthorized access, often bypassing traditional security measures.Deception breaches leverage the human element as a primary attack vector.
Unlike traditional attacks that focus on exploiting software vulnerabilities, deception breaches target human behavior, exploiting trust and curiosity to gain access to sensitive information or systems. This makes them particularly difficult to detect and prevent using traditional security tools alone.
Types of Deception Breaches
Several types of deception breaches exist, each employing unique tactics to achieve malicious goals. These tactics often overlap and are frequently combined for maximum impact.
| Type | Method | Example | Impact |
|---|---|---|---|
| Baiting | Offering something enticing (e.g., free gift cards, software downloads) containing malware. | A phishing email promising a free gift card in exchange for filling out a survey that installs malware. | Malware infection, data theft, identity theft. |
| Phishing | Masquerading as a trustworthy entity (e.g., bank, government agency) to trick users into revealing sensitive information. | An email appearing to be from a bank, requesting login credentials to verify an account. | Credential theft, account takeover, financial loss. |
| Quid Pro Quo | Offering a service or assistance in exchange for sensitive information or access. | A fake tech support representative offering to fix a computer problem, requesting remote access to install malware. | Malware infection, data theft, system compromise. |
| Pretexting | Creating a believable scenario to gain trust and manipulate victims into providing information or access. | An attacker posing as a police officer to obtain personal information under the guise of an investigation. | Identity theft, financial loss, reputational damage. |
| Watering Hole Attacks | Compromising a website frequently visited by the target organization to deliver malware. | An attacker compromises a news website frequented by employees of a target company, injecting malware into the site. | Malware infection, data theft, network compromise. |
Motivations Behind Deception Breaches
The motivations behind deception breaches are diverse, ranging from financial gain to espionage and sabotage. Attackers often seek to exploit vulnerabilities in human psychology, rather than technical flaws in systems.Financial gain is a primary driver, with attackers seeking to steal money, credit card information, or other valuable assets. Espionage motivates state-sponsored actors and corporate competitors to steal intellectual property, trade secrets, or sensitive business information.
Sabotage aims to disrupt operations, damage reputation, or cause other forms of harm.
Real-World Case Studies
The Target data breach of 2013, where attackers compromised the payment systems through a third-party vendor, highlights the vulnerability of supply chains to deception breaches. The attackers used spear phishing to gain initial access, demonstrating the effectiveness of targeted attacks. Another example is the Yahoo data breaches, where attackers used sophisticated phishing techniques to steal user credentials, demonstrating the scale of damage possible from such breaches.
These cases underscore the need for comprehensive security measures that account for human vulnerabilities.
Proactive Deception Detection
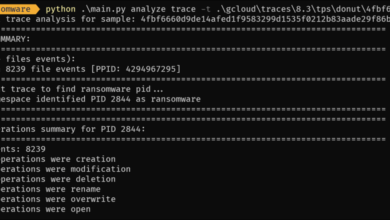
Proactive deception detection, also known as “seeding the hunt,” shifts the cybersecurity paradigm from reactive incident response to a more aggressive, preventative posture. Instead of waiting for attackers to compromise systems, we strategically deploy decoys and traps to lure them in, revealing their tactics and techniques while minimizing the risk of actual data breaches. This approach allows security teams to gain valuable intelligence about attackers, understand their methods, and improve overall security posture.Proactive deception detection involves embedding deceptive mechanisms within a system to identify and analyze attacker behaviors.
By creating an environment where attackers believe they have successfully compromised a system, we can observe their actions, collect forensic evidence, and respond effectively. This strategy is particularly useful in detecting advanced persistent threats (APTs) and other sophisticated attacks that may otherwise go unnoticed.
Deception Detection Strategies
Effective deception strategies require careful planning and execution. The goal is to create realistic yet enticing decoys that attract attackers without compromising sensitive data. This involves understanding attacker motivations and typical attack vectors. For example, decoys can mimic sensitive databases, web servers, or other valuable assets. The key is to make them appear legitimate, yet contain mechanisms to detect and record attacker activity.
These mechanisms could range from simple log file monitoring to more sophisticated behavioral analysis tools.
Embedding Deception Mechanisms
Integrating deception mechanisms into existing systems requires a multi-layered approach. This can involve deploying virtual machines acting as honeypots, embedding deceptive data within databases, or using specialized deception platforms that automate the deployment and management of decoys. Careful consideration should be given to the placement and configuration of these mechanisms to maximize their effectiveness and minimize the risk of unintended consequences.
For instance, poorly configured honeypots can inadvertently expose vulnerabilities or become a source of false positives.
Hypothetical Proactive Deception Detection System
A hypothetical system might consist of several components: a decoy management system for creating and deploying decoys; a sensor network for monitoring decoy activity; a central analytics platform for analyzing collected data; and an automated response system for initiating countermeasures. The decoy management system would allow security teams to create realistic decoys tailored to specific threats. The sensor network would continuously monitor the decoys for suspicious activity, such as file access, network connections, or command execution.
The analytics platform would process the collected data, identifying patterns and correlations that indicate malicious activity. Finally, the automated response system would trigger countermeasures, such as isolating infected systems or alerting security personnel.
Examples of Deceptive Techniques and Countermeasures
Attackers employ various techniques to compromise systems, including credential stuffing, phishing, and exploiting known vulnerabilities. A common deceptive technique is using fake login credentials within a decoy system. When an attacker attempts to use these credentials, the system logs the event, providing evidence of the attack. Another technique involves deploying decoys containing seemingly valuable data, such as financial records or customer information.
Access attempts to these decoys reveal the attacker’s goals and methods. To counter these, organizations can use techniques like multi-factor authentication, robust intrusion detection systems, and regular security audits to detect and mitigate vulnerabilities. Furthermore, training employees to identify and report phishing attempts is crucial.
Analyzing Deception Indicators
Analyzing deception indicators is crucial for effectively responding to and mitigating the impact of deception breaches. A proactive approach involves continuously monitoring the environment for subtle anomalies that might signal malicious activity. By understanding the various indicators and their potential severity, security teams can prioritize their responses and effectively neutralize threats.
The process of analyzing deception indicators involves a multi-layered approach. It starts with the detection of suspicious activity within the deception infrastructure, followed by correlation with other system logs and security events to confirm the nature and scope of the breach. Finally, this information is used to inform a targeted response, potentially including incident containment, threat hunting, and remediation efforts.
The accuracy and timeliness of this analysis directly impacts the effectiveness of the overall security posture.
Key Deception Indicators
Several key indicators consistently signal a potential deception breach. These indicators can be categorized for easier analysis and prioritization. Understanding the context and interrelation of these indicators is essential for effective response.
- Unexpected Network Traffic: Unusual communication patterns, such as connections to unexpected destinations or ports, or an unusually high volume of traffic from a specific source, can suggest a breach. For instance, a sudden surge in outbound connections to a known malicious IP address would be a strong indicator.
- Suspicious File Accesses: Attempts to access sensitive files or directories not typically accessed by legitimate users or processes are highly suspicious. This could include attempts to read, write, or execute files within protected areas of the system. For example, an attempt to access system configuration files from an unknown user account would raise significant concern.
- Credential Stuffing Attempts: Repeated login attempts using common or previously compromised credentials indicate a potential brute-force or credential stuffing attack. This often occurs after a data breach exposing user credentials.
- Unusual Command Execution: The execution of unusual or unauthorized commands, especially those involving system administration or data manipulation, can be a critical indicator. An example would be an attempt to execute a command that disables system logging or firewall rules.
- Deception Trap Activation: The most direct indicator is the activation of a deception trap itself. This provides immediate confirmation of a potential breach and allows for immediate investigation and response. For example, a honeypot system detecting an unauthorized connection attempt provides direct evidence of malicious activity.
Methods for Analyzing Deception Indicators
Several methods exist for analyzing deception indicators, each offering unique advantages and disadvantages. The optimal approach often involves a combination of techniques tailored to the specific environment and threat landscape.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security logs from various sources, enabling the identification of patterns and anomalies that might indicate a deception breach. SIEMs provide a centralized view of security events, facilitating correlation and analysis.
- Threat Intelligence Platforms (TIPs): TIPs provide access to threat intelligence feeds, allowing security teams to correlate observed indicators with known threats and attack patterns. This context enhances the accuracy and efficiency of the analysis.
- Deception-Specific Platforms: Dedicated deception platforms offer advanced analytics capabilities tailored specifically to deception data. These platforms often provide automated analysis and reporting, streamlining the process of identifying and responding to breaches.
- Manual Analysis: In some cases, manual analysis of security logs and deception data might be necessary, particularly when dealing with sophisticated or novel attacks. This requires significant expertise and experience in security analysis.
Hierarchical Structure of Deception Indicators
Organizing deception indicators hierarchically based on severity and impact allows for prioritized responses. Critical indicators require immediate attention, while less severe indicators can be addressed with lower urgency.
| Severity | Indicator | Impact |
|---|---|---|
| Critical | Deception trap activation leading to data exfiltration | Significant data loss, potential for major disruption |
| High | Unusual command execution attempting to disable security controls | Potential for escalation of privileges, compromised system integrity |
| Medium | Suspicious file accesses to sensitive directories | Potential data breach, compromise of sensitive information |
| Low | Unexpected network traffic to a known suspicious IP address | Potential reconnaissance activity, low immediate impact |
Interpreting Suspicious Activity: Examples
Interpreting suspicious activity requires careful consideration of the context and surrounding events. A single indicator might not be sufficient to confirm a breach, but a combination of indicators strengthens the evidence.
Example 1: A honeypot server detects an incoming SSH connection from an unknown IP address. This, in itself, might be benign. However, if this is followed by attempts to access sensitive files within the honeypot’s file system and an unusual amount of data transfer to an external server, it strongly suggests a malicious actor attempting data exfiltration.
Example 2: An account with limited privileges attempts to execute a command to modify system firewall rules. While seemingly innocuous, this event, coupled with previous failed login attempts from the same account and unusual network traffic originating from the account’s machine, indicates a potential compromised account used for lateral movement.
Responding to Deception Breaches
Responding to a confirmed deception breach requires a swift and coordinated effort. The goal isn’t just to remediate the immediate threat, but also to learn from the experience and strengthen future defenses. A well-defined incident response plan is crucial for effective mitigation and minimizes the overall impact.
Steps Involved in Responding to a Confirmed Deception Breach
The response process begins with immediate containment. This involves isolating affected systems to prevent further lateral movement. Next, the breach needs to be thoroughly investigated to determine the attacker’s techniques, tools, and procedures (TTPs). This analysis is key to understanding the scope of the compromise and identifying any potential backdoors or persistent threats. Finally, remediation involves patching vulnerabilities, removing malware, and restoring systems to a secure state.
This is followed by a comprehensive review of security controls and processes to identify and address weaknesses that allowed the breach to occur.
Containing the Damage Caused by a Deception Breach
Containment is paramount. Immediately isolate compromised systems from the network to prevent further damage. This might involve disconnecting the system from the network, disabling network interfaces, or using firewall rules to restrict access. Analyzing network traffic logs and system logs can help identify the extent of the attacker’s activities. Consider using endpoint detection and response (EDR) tools to identify and remove any malware or malicious processes.
Regular backups are crucial; restoring systems from a known good backup is often the fastest and most effective remediation strategy.
Incident Response Process Flowchart for Deception Breaches
Imagine a flowchart with the following stages:
1. Detection
A deception platform alerts on suspicious activity.
2. Verification
Analysts confirm the alert indicates a genuine breach, not a false positive.
3. Containment
Isolate the compromised system(s) from the network.
4. Eradication
Remove malware and malicious artifacts.
5. Recovery
Restore systems from backups or re-image them.
Deception breaches are a game of cat and mouse, so sometimes you need to get proactive. Instead of just reacting, seeding the hunt with deceptive lures is crucial. This requires robust, adaptable systems, and that’s where understanding the future of app development comes in, like what’s discussed in this great article on domino app dev the low code and pro code future.
By leveraging these advancements, we can create more sophisticated deception technologies to outsmart attackers and gain valuable intelligence on their methods before they even strike.
6. Analysis
Determine the attacker’s TTPs and the root cause of the breach.
7. Reporting
Document the incident and communicate findings to relevant stakeholders.
8. Remediation
Patch vulnerabilities and implement preventative measures.This visual representation clarifies the sequential steps involved in handling a deception breach effectively. Each stage is critical and contributes to the overall success of the incident response process.
Conducting a Post-Incident Analysis to Improve Future Defenses
A post-incident analysis is vital for improving future defenses. This involves a thorough review of the incident timeline, attacker TTPs, and the effectiveness of existing security controls. Key questions to consider include: How did the attacker gain initial access? What vulnerabilities were exploited? How effective were existing security controls in detecting and responding to the breach?
The analysis should lead to actionable improvements in security policies, procedures, and technologies. This might involve implementing new security controls, updating existing ones, or improving employee training programs. For example, a post-incident analysis might reveal a weakness in the organization’s vulnerability management program, leading to a more robust patching process. Or it might highlight the need for improved security awareness training for employees to better identify and report phishing attempts.
Offensive Deception Strategies

Deploying deception isn’t just about passively waiting for attackers to stumble into our traps. A proactive approach involves using deception offensively to shape the attacker’s behavior, gather intelligence, and even disrupt their operations. This requires careful planning, a deep understanding of attacker tactics, and a robust ethical framework.Offensive deception strategies, while powerful, present a unique set of ethical challenges.
Deception breaches are a sneaky way attackers test defenses, so proactively seeding the hunt is key. Understanding your cloud security posture is crucial in this game, and that’s where tools like Bitglass come in; check out this great article on bitglass and the rise of cloud security posture management for more info. By improving visibility into your cloud environment, you can better identify and respond to these deception breaches before they escalate into full-blown attacks, effectively turning the tables on the adversary.
The core principle is to remain within legal and moral boundaries, ensuring that any deceptive techniques employed don’t violate privacy laws or cross ethical lines. Transparency with internal stakeholders and clear documentation of the strategy are crucial for maintaining accountability and preventing unintended consequences. For instance, the use of deceptive honeypots should be clearly documented and understood by all relevant personnel, to avoid potential legal issues arising from data collected from these assets.
Ethical Considerations in Offensive Deception
The ethical considerations surrounding offensive deception are complex. It’s crucial to ensure that any deceptive techniques used are proportionate to the threat, and that they don’t cause undue harm or violate any applicable laws or regulations. A key aspect is ensuring that the information gathered is used solely for defensive purposes and not for any other illicit activities.
Furthermore, any potential risks to third parties need to be carefully assessed and mitigated. For example, a honeypot designed to attract attackers shouldn’t unintentionally expose sensitive data belonging to legitimate users. The principle of least privilege should always guide the design and deployment of offensive deception techniques.
Examples of Offensive Deception Techniques
Several offensive deception techniques can be used to deter and disrupt attackers. One example is deploying fake credentials or services that appear legitimate but lead attackers to dead ends or sandboxes where their activity can be monitored. Another technique is to create false network paths or servers that lure attackers away from critical systems, effectively diverting their attention and resources.
This can be combined with techniques like using decoy data, which can provide valuable insights into the attacker’s motives and techniques. For instance, presenting a seemingly valuable database with misleading information can reveal an attacker’s objectives and their level of sophistication.
Deploying Deceptive Assets to Identify and Track Attackers
A plan for deploying deceptive assets should begin with a thorough risk assessment, identifying the most valuable assets and likely attack vectors. The deployment should be phased, starting with low-risk assets and gradually expanding as confidence grows. Deceptive assets should be integrated seamlessly into the existing network infrastructure to avoid detection, and monitoring systems should be in place to capture attacker activity without compromising the deception.
Regular reviews and adjustments are essential to ensure the effectiveness of the deployed assets. A comprehensive plan would include clear procedures for incident response, escalation paths, and data analysis to maximize the value extracted from the gathered intelligence. This could involve establishing a dedicated team to monitor and analyze data from deceptive assets, ensuring timely responses to any detected breaches.
Challenges and Limitations of Offensive Deception Strategies
Offensive deception strategies, while effective, aren’t without their challenges. One major limitation is the risk of inadvertently revealing sensitive information or compromising legitimate systems. Another challenge is the need for ongoing maintenance and adaptation to keep pace with evolving attacker tactics. Attackers can become sophisticated in detecting and circumventing deception techniques, requiring continuous refinement of the strategy.
Additionally, the resources required to design, deploy, and maintain an effective offensive deception program can be significant. Finally, the legal and ethical implications must be carefully considered and addressed at every stage of the process to prevent unintended consequences.
Building a Deception-Resilient System: Deception Breaches And Going On The Offense To Seed The Hunt
Building a system resilient to deception attacks requires a multi-layered approach that combines robust security controls with a proactive security culture. It’s not enough to simply deploy deception technologies; a holistic strategy is essential to minimize the impact of successful breaches and to maximize the effectiveness of your deception program. This involves careful system design, comprehensive security awareness training, and the implementation of a variety of security controls working in concert.
Best Practices for Designing Deception-Resistant Systems, Deception breaches and going on the offense to seed the hunt
Designing systems resistant to deception necessitates a shift from perimeter-based security to a more distributed and dynamic approach. This involves minimizing the attack surface by reducing the number of exposed services and endpoints. Implementing strong access controls, including least privilege access and multi-factor authentication, is crucial. Regular security audits and vulnerability assessments are vital to identify and remediate potential weaknesses that attackers could exploit.
Furthermore, employing robust logging and monitoring capabilities allows for quicker detection and response to suspicious activities. The use of micro-segmentation to isolate critical systems and data further reduces the potential impact of a successful attack.
The Role of Security Awareness Training in Mitigating Deception Breaches
Security awareness training plays a vital role in mitigating deception breaches. Educated users are less likely to fall victim to phishing attacks or other social engineering tactics that often precede deception attacks. Training should focus on identifying suspicious emails, websites, and attachments, as well as understanding the techniques used by attackers to gain access to systems. Regular, engaging training modules, combined with simulated phishing campaigns, are effective methods for reinforcing these lessons.
Furthermore, empowering employees to report suspicious activity promptly is critical for early detection and response.
Security Controls Enhancing Deception Resilience
A robust security posture is built upon multiple layers of defense. Here’s a list of security controls that enhance resilience against deception attacks:
- Network Segmentation: Isolating different parts of the network limits the impact of a breach.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can block or alert on suspicious patterns.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoint activity for malicious behavior and provide advanced threat hunting capabilities.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events.
- Data Loss Prevention (DLP): DLP tools prevent sensitive data from leaving the network without authorization.
- Vulnerability Management: Regularly scanning for and patching vulnerabilities reduces the attack surface.
- Strong Authentication: Implementing multi-factor authentication (MFA) makes it harder for attackers to gain unauthorized access.
- Regular Security Audits: Regular audits help identify weaknesses in security controls and processes.
Layered Security Architecture Incorporating Deception Techniques
Imagine a layered security architecture depicted as concentric circles. The outermost circle represents the perimeter security, encompassing firewalls, intrusion detection systems, and web application firewalls. The next layer consists of network segmentation, isolating different parts of the network to limit the spread of attacks. Within this layer, we find deception technologies deployed strategically – honeypots and decoy systems strategically placed to lure and trap attackers.
The innermost circle represents the critical assets and data, protected by robust access controls, encryption, and data loss prevention measures. The interaction between these layers allows for early detection and response, while the deception technologies provide valuable intelligence on attacker tactics and techniques. The entire system is monitored by a SIEM, providing a centralized view of security events across all layers.
This layered approach ensures that even if one layer is breached, subsequent layers provide additional protection and delay the attacker, giving security teams more time to respond.
Wrap-Up
So, there you have it – a deep dive into the fascinating and crucial world of deception breaches and offensive cybersecurity strategies. By understanding the different types of deception, proactively seeding the hunt, and effectively responding to incidents, we can significantly improve our overall security posture. Remember, the key is to be proactive, adaptable, and always one step ahead of the attackers.
The battlefield is digital, and the fight is constant. Let’s continue learning and evolving our defenses together!
FAQ Insights
What are the ethical implications of using deceptive techniques?
Using deception ethically requires careful consideration. It’s crucial to ensure you’re only targeting malicious actors and not inadvertently harming innocent users. Transparency and clear legal guidelines are essential. Always operate within the bounds of the law and your organization’s ethical policies.
How can I train my team to recognize deception attempts?
Regular security awareness training is vital. Simulations, phishing exercises, and interactive training modules can significantly improve your team’s ability to spot deception attempts. Focus on teaching critical thinking and skepticism.
What are some common misconceptions about deception technology?
A common misconception is that deception technology is a silver bullet. It’s a powerful tool, but it’s not a replacement for a robust security infrastructure. It should be used in conjunction with other security measures for optimal effectiveness.
How much does implementing deception technology cost?
The cost varies widely depending on the scale and complexity of your deployment. Factors include the number of decoys, the level of sophistication, and the integration with existing security systems. Consult with vendors for accurate pricing.