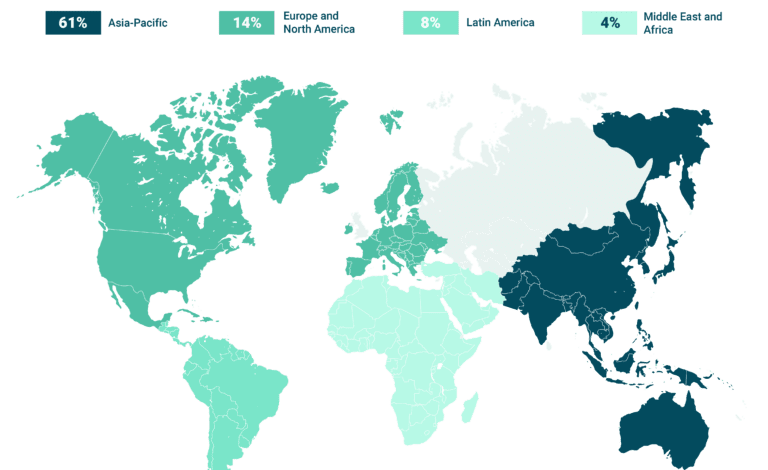
Top 10 Industries Most Vulnerable to Cyber Attacks
Top 10 industries most vulnerable to cyber attacks – it’s a headline that grabs your attention, right? We live in a hyper-connected world, and that means almost every industry faces digital threats. But some are way more exposed than others. Think about the sheer volume of sensitive data held by healthcare providers, financial institutions, and government agencies. This post dives deep into the ten sectors facing the biggest cyber risks, exploring the types of attacks they’re facing and what’s at stake.
From the intricate workings of energy grids to the seemingly simple transactions of online retail, the potential for disruption and damage is immense. We’ll examine real-world examples, discuss the unique vulnerabilities of each sector, and explore the steps being taken (and those that
-should* be taken) to improve cybersecurity defenses. Get ready for a fascinating (and slightly terrifying) look at the front lines of the digital battleground.
Introduction
Understanding cybersecurity vulnerability is crucial in today’s interconnected world. A cybersecurity vulnerability is essentially a weakness in a system’s design, implementation, operation, or internal controls that could be exploited by a threat actor to gain unauthorized access, disrupt operations, steal data, or cause other damage. This weakness can exist in hardware, software, firmware, or even human processes. Industries vary significantly in their vulnerability due to several interconnected factors.An industry’s vulnerability to cyberattacks is a complex interplay of several factors.
These include the value and sensitivity of the data they handle, the sophistication of their cybersecurity defenses, the reliance on outdated technologies, the level of employee training and awareness, and the regulatory landscape they operate within. Industries with large amounts of sensitive personal data, such as healthcare or finance, are inherently more attractive targets than others. Similarly, industries with legacy systems and limited resources dedicated to cybersecurity are more likely to be successfully compromised.
The interconnected nature of modern systems also plays a role; a vulnerability in one part of a supply chain can expose the entire chain.
Factors Contributing to Industry Vulnerability
The susceptibility of an industry to cyberattacks is multifaceted. A lack of robust cybersecurity infrastructure, including outdated software and insufficient security protocols, significantly increases vulnerability. Inadequate employee training and awareness regarding phishing scams and other social engineering tactics further exacerbate the problem. Moreover, industries operating in heavily regulated environments often face increased scrutiny and potential penalties following a breach, but the very act of regulation doesn’t automatically guarantee robust security.
Finally, the sheer volume and sophistication of cyberattacks are constantly increasing, leaving even the most well-defended industries at risk.
Real-World Consequences of Cyberattacks
The consequences of successful cyberattacks can be devastating and far-reaching, impacting not only the targeted organization but also its customers, partners, and the wider economy. For example, the 2017 NotPetya ransomware attack crippled global businesses, particularly in the shipping and transportation industries, causing billions of dollars in losses. The 2013 Target data breach exposed the personal information of millions of customers, resulting in significant financial losses and reputational damage.
In the healthcare sector, breaches can lead to the exposure of sensitive patient data, potentially violating privacy laws and causing irreparable harm to patients’ trust. These examples highlight the wide-ranging and severe consequences that cyberattacks can have across various industries.
Healthcare: Top 10 Industries Most Vulnerable To Cyber Attacks
The healthcare industry, entrusted with sensitive patient data and critical life-sustaining operations, faces a unique and ever-evolving landscape of cyber threats. The interconnected nature of modern healthcare systems, coupled with the increasing reliance on digital technologies, creates a vast attack surface vulnerable to exploitation by malicious actors. This vulnerability translates into significant risks to patient privacy, operational efficiency, and even patient safety.
Cyber Threats Targeting Healthcare
Healthcare organizations are prime targets for various cyberattacks. Ransomware attacks, designed to encrypt critical data and demand a ransom for its release, are particularly prevalent. These attacks can disrupt essential services, including electronic health record (EHR) access, diagnostic imaging, and patient monitoring systems. Phishing attacks, which involve deceptive emails or messages designed to trick individuals into revealing sensitive information, remain a significant threat.
These attacks can compromise employee credentials, providing attackers with access to sensitive systems and data. Additionally, denial-of-service (DoS) attacks can overwhelm healthcare systems, rendering them inaccessible to patients and staff. Finally, insider threats, whether malicious or unintentional, pose a considerable risk, as employees may inadvertently expose sensitive data or grant access to unauthorized individuals.
Impact of Data Breaches on Patient Privacy and Healthcare Delivery
Data breaches in the healthcare sector can have devastating consequences. The unauthorized disclosure of protected health information (PHI), including patient names, addresses, medical records, and insurance details, can lead to identity theft, financial fraud, and reputational damage for both the patients and the healthcare provider. Beyond the immediate impact on individuals, data breaches can disrupt healthcare delivery, leading to delays in treatment, compromised patient care, and increased costs associated with remediation and legal action.
The loss of patient trust and the erosion of public confidence in the healthcare system are also significant consequences.
Hypothetical Cyberattack Scenario and Consequences
Imagine a scenario where a major hospital system falls victim to a sophisticated ransomware attack. Attackers infiltrate the network through a phishing email targeting a hospital employee, gaining access to administrative credentials. They then encrypt critical systems, including EHRs, radiology imaging systems, and laboratory information systems. The hospital is forced to shut down operations, delaying surgeries, disrupting patient care, and impacting emergency services.
The attackers demand a substantial ransom for the decryption key, placing the hospital in a difficult position: pay the ransom and risk encouraging further attacks, or refuse and potentially lose irreplaceable patient data and face significant financial losses and legal repercussions. The resulting disruption could lead to patient harm, loss of revenue, damage to reputation, and potential legal penalties for non-compliance with data protection regulations.
Comparison of Healthcare Cybersecurity Measures
| Measure | Cost | Effectiveness | Implementation Difficulty |
|---|---|---|---|
| Multi-factor authentication (MFA) | Medium | High | Low |
| Intrusion detection/prevention systems (IDS/IPS) | High | High | Medium |
| Regular security awareness training | Low | Medium | Low |
| Data encryption | Medium | High | Medium |
Finance

The financial sector, encompassing banking, fintech, and investment firms, is a prime target for cyberattacks due to the sheer volume of sensitive data it handles and the potentially devastating consequences of a breach. The interconnected nature of global financial systems makes a successful attack potentially catastrophic, impacting not only individual institutions but also broader economic stability. Understanding the specific threats and implementing robust security measures are paramount for survival in this high-stakes environment.
Common Cyber Threats Targeting Financial Institutions
Financial institutions face a diverse range of cyber threats, each posing unique challenges. Phishing attacks remain a persistent problem, aiming to trick employees into revealing credentials or downloading malware. Ransomware attacks encrypt critical data, demanding payment for its release, causing significant operational disruption and reputational damage. Data breaches, often facilitated by exploiting vulnerabilities in software or through insider threats, can expose sensitive customer information, leading to financial losses and legal repercussions.
Advanced Persistent Threats (APTs), sophisticated and long-term attacks often sponsored by nation-states, aim to steal intellectual property or financial data, requiring highly advanced detection and response capabilities. Finally, denial-of-service (DoS) attacks can overwhelm systems, making them unavailable to legitimate users, disrupting critical financial transactions.
Cybersecurity Challenges: Traditional Banks vs. Fintech Companies
Traditional banks and fintech companies face distinct cybersecurity challenges. Traditional banks grapple with legacy systems that may lack the security features of modern infrastructure. Their extensive branch networks and diverse customer base present a wider attack surface. Fintech companies, while often more agile and technologically advanced, may lack the established security protocols and resources of larger institutions. Their reliance on cloud-based services and APIs introduces new vulnerabilities.
The regulatory landscape also differs, with traditional banks facing stricter oversight, while the regulatory framework for fintech is still evolving, creating a potential gap in security standards. The speed of innovation in fintech, while advantageous, also means security measures may lag behind technological advancements.
Regulatory Landscape Concerning Cybersecurity in the Finance Industry
The regulatory landscape for cybersecurity in finance is complex and constantly evolving. Regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the US mandate specific data protection measures. The Payment Card Industry Data Security Standard (PCI DSS) sets stringent requirements for organizations handling credit card information. National and international bodies continually issue guidelines and best practices, pushing for increased security awareness and stronger regulatory enforcement.
Non-compliance can result in hefty fines and reputational damage. The ongoing evolution of regulations necessitates continuous adaptation and investment in security infrastructure and compliance practices.
Best Practices for Securing Financial Data and Systems
Implementing robust cybersecurity measures is crucial for protecting financial data and systems. This involves a multi-layered approach encompassing employee training, regular security audits, and strong access controls. Multi-factor authentication (MFA) should be mandatory for all employees and customers accessing sensitive systems. Regular software updates and patching are essential to address known vulnerabilities. Robust intrusion detection and prevention systems are necessary to monitor network traffic and detect malicious activity.
Incident response plans should be developed and regularly tested to ensure a swift and effective response to security breaches. Data encryption, both in transit and at rest, is vital for protecting sensitive information. Finally, continuous monitoring and threat intelligence are critical for proactively identifying and mitigating emerging threats. For example, JPMorgan Chase, a major player in the financial industry, invests heavily in cybersecurity, employing thousands of specialists and utilizing advanced technologies to protect its systems and data.
Their commitment underscores the critical importance of robust security in the financial sector.
Energy
The energy sector, encompassing electricity generation, transmission, and distribution, represents a critical national infrastructure. Its interconnected nature and reliance on sophisticated control systems make it uniquely vulnerable to cyberattacks. Disruptions to energy supply can have cascading effects across numerous other sectors, causing widespread economic damage and societal disruption.The unique vulnerabilities of energy infrastructure stem from several factors. Firstly, the extensive geographical spread of power grids and the diverse range of technologies employed present a significant challenge for comprehensive security management.
Secondly, many components of the energy infrastructure, including Supervisory Control and Data Acquisition (SCADA) systems, are legacy systems often lacking modern security features. Finally, the increasing reliance on internet connectivity for remote monitoring and control introduces new attack vectors for malicious actors.
Potential Consequences of Cyberattacks on the Energy Grid
A successful cyberattack on an energy grid could have devastating consequences. These range from localized power outages affecting individual communities to large-scale blackouts impacting entire regions or even nations. Such disruptions could cripple essential services like hospitals, transportation, and communication networks, leading to significant economic losses, social unrest, and potential threats to public safety. Beyond immediate outages, attackers could manipulate grid operations to cause physical damage to equipment, prolonging outages and increasing repair costs.
The disruption of supply chains related to energy production and distribution could further exacerbate the impact.
Examples of Past Cyberattacks Targeting the Energy Sector
Several notable cyberattacks have targeted the energy sector, highlighting the real and present threat. The Stuxnet worm, discovered in 2010, is a prime example of a sophisticated attack targeting industrial control systems in Iranian nuclear facilities. While not solely focused on the energy sector, it demonstrated the potential for cyberattacks to cause physical damage to critical infrastructure. Other incidents, though often not publicly disclosed due to security concerns, have involved attempts to compromise SCADA systems and manipulate grid operations, resulting in minor outages or data breaches.
These incidents underscore the need for continuous vigilance and proactive cybersecurity measures within the energy industry.
Strategies for Improving Cybersecurity Resilience of Energy Infrastructure
Improving the cybersecurity resilience of energy infrastructure requires a multi-faceted approach.
The following strategies are crucial:
- Modernizing infrastructure: Replacing legacy systems with modern, secure alternatives and implementing robust network segmentation to limit the impact of potential breaches.
- Strengthening access control: Implementing strong authentication and authorization mechanisms to prevent unauthorized access to critical systems.
- Implementing intrusion detection and prevention systems: Deploying advanced security technologies to detect and prevent cyberattacks in real-time.
- Developing incident response plans: Establishing comprehensive plans to effectively respond to and recover from cyberattacks.
- Improving employee training and awareness: Educating employees about cybersecurity threats and best practices to prevent human error from becoming an attack vector.
- Enhancing collaboration and information sharing: Fostering collaboration between energy companies, government agencies, and cybersecurity experts to share threat intelligence and best practices.
- Investing in cybersecurity research and development: Continuously investing in research and development to stay ahead of evolving cyber threats.
Government
Government agencies at all levels, from local municipalities to national defense departments, are increasingly reliant on digital systems to manage critical infrastructure, citizen data, and national security. This dependence, while offering efficiency gains, significantly expands the attack surface and makes these entities prime targets for sophisticated cyberattacks. The consequences of a successful breach can be devastating, impacting not only national security but also public trust and the economy.Government agencies face a multitude of cybersecurity challenges.
These range from legacy systems lacking robust security features to the ever-evolving threat landscape, characterized by increasingly sophisticated attacks and well-funded malicious actors. Furthermore, the sheer volume and sensitivity of data handled by government agencies present unique challenges in terms of data protection and access control. The diverse technological landscape across different agencies also complicates the implementation of consistent security protocols and policies.
Cybersecurity Challenges Faced by Government Agencies
Government agencies face a complex web of interconnected cybersecurity challenges. Outdated infrastructure, a lack of skilled cybersecurity professionals, and the increasing sophistication of cyberattacks all contribute to a vulnerable environment. Budgetary constraints often limit the resources available for robust security upgrades and training. Moreover, the decentralized nature of many government structures can hinder effective collaboration and the implementation of uniform security standards.
The need to balance security with transparency and public access to information also presents a significant challenge.
Consequences of a Data Breach Affecting Sensitive Government Information
A data breach affecting sensitive government information can have far-reaching and severe consequences. The loss of classified information can compromise national security, potentially leading to espionage or sabotage. The exposure of citizen data, such as personal details, financial information, or medical records, can result in identity theft, financial losses, and significant damage to public trust. A breach can also lead to legal liabilities, financial penalties, and reputational damage for the affected agency and the government as a whole.
The 2015 Office of Personnel Management (OPM) breach, which compromised the personal data of millions of federal employees, serves as a stark reminder of the potential impact. This breach resulted in significant financial costs, reputational damage, and lasting security concerns.
The Role of Cybersecurity Regulations in Protecting Government Systems
Cybersecurity regulations play a crucial role in protecting government systems. Regulations such as the Federal Information Security Modernization Act (FISMA) in the United States mandate the implementation of security controls and risk management practices across federal agencies. These regulations often define minimum security standards, require regular security assessments, and establish frameworks for incident response. Compliance with these regulations is essential for ensuring the confidentiality, integrity, and availability of government data and systems.
However, the effectiveness of these regulations depends on consistent enforcement and adaptation to the ever-evolving threat landscape.
Hypothetical Cyberattack Scenario and its Potential Impact
Imagine a sophisticated phishing campaign targeting employees of a national tax agency. The attackers, using highly realistic phishing emails, successfully compromise multiple employee accounts, gaining access to the agency’s internal network. They then deploy ransomware, encrypting critical tax data and demanding a large ransom for its release. The attack disrupts tax processing, causing significant delays in tax refunds and potentially impacting government revenue.
The exposure of taxpayer data leads to widespread identity theft and financial losses for citizens. The resulting public outrage and loss of trust in the government could have long-term political and economic repercussions. This scenario highlights the devastating potential of a successful cyberattack against a government agency.
Manufacturing
The manufacturing sector, a cornerstone of global economies, is increasingly reliant on interconnected systems and digital technologies. This interconnectedness, while boosting efficiency and productivity, simultaneously expands the attack surface, making it a prime target for sophisticated cyberattacks. The vulnerabilities extend beyond traditional IT systems to encompass the critical infrastructure that drives production – Industrial Control Systems (ICS).
So, you’re probably thinking about the top 10 industries most vulnerable to cyber attacks – finance, healthcare, and government immediately spring to mind, right? But building robust security requires adaptable solutions, which is why I’ve been exploring the advancements in application development. Check out this article on domino app dev the low code and pro code future – it highlights how streamlined development can help even the most vulnerable sectors bolster their defenses against sophisticated threats.
Ultimately, strengthening security across these top 10 industries depends on innovative tech solutions.
The reliance on sophisticated technology in modern manufacturing presents unique challenges. Data breaches can expose sensitive intellectual property, disrupt operations, and even lead to physical damage to equipment. The interconnected nature of modern manufacturing facilities, often including remote access for maintenance and control, creates numerous entry points for malicious actors.
Industrial Control System Vulnerabilities
Industrial Control Systems (ICS), responsible for managing and monitoring physical processes in manufacturing plants, often utilize older, less secure technologies. These systems, unlike typical IT networks, are frequently designed with minimal security in mind, prioritizing reliability and operational continuity over robust cybersecurity measures. This legacy infrastructure is often vulnerable to various attacks, including malware infections, unauthorized access, and denial-of-service attacks.
The consequences of successful attacks can range from minor production delays to catastrophic equipment failures and safety hazards.
Consequences of Cyberattacks on Manufacturing Operations
A successful cyberattack on a manufacturing facility can have far-reaching and devastating consequences. Disruption of operations leads to significant financial losses due to production downtime, lost sales, and potential damage to equipment. Reputational damage can also be substantial, affecting customer trust and investor confidence. Furthermore, depending on the nature of the manufacturing process, a cyberattack could pose significant safety risks to workers and the surrounding community.
The 2010 Stuxnet attack, which targeted Iranian nuclear facilities, serves as a stark reminder of the potential for severe physical consequences from ICS compromises.
Supply Chain Security in Manufacturing
The complexity of modern manufacturing supply chains introduces additional vulnerabilities. Cyberattacks can target any point in the chain, from raw material suppliers to distributors and logistics providers. Compromised suppliers could introduce malware into the manufacturing process through tainted software or hardware, potentially disrupting the entire production line. Securing the supply chain requires robust vendor risk management, secure communication protocols, and continuous monitoring of all involved parties.
Implementing stringent security standards throughout the entire supply chain is paramount to mitigating these risks.
ICS Vulnerabilities and Mitigation Strategies
| ICS Type | Vulnerability | Mitigation Strategy |
|---|---|---|
| Supervisory Control and Data Acquisition (SCADA) systems | Outdated protocols, lack of authentication, remote access vulnerabilities | Implement strong authentication mechanisms, regularly update software, segment networks, deploy intrusion detection/prevention systems. |
| Programmable Logic Controllers (PLCs) | Default passwords, insecure firmware, lack of patching mechanisms | Change default passwords, regularly update firmware, implement network segmentation, utilize secure remote access solutions. |
| Human-Machine Interfaces (HMIs) | Phishing attacks, malware infections via USB drives, insecure remote access | Employee security awareness training, robust access control measures, network segmentation, regular security audits. |
Retail
The retail sector, with its vast networks of physical stores and robust online presence, is a prime target for cyberattacks. The industry’s reliance on sensitive customer data, payment processing systems, and interconnected supply chains creates a large attack surface vulnerable to various threats. The consequences of a successful cyberattack can be devastating, impacting not only the retailer’s financial stability but also its reputation and customer trust.
Common Cyber Threats Targeting the Retail Sector
Retailers face a diverse range of cyber threats, each with the potential to inflict significant damage. These threats exploit vulnerabilities in systems and human behavior to gain unauthorized access to sensitive information and disrupt operations. Understanding these threats is crucial for implementing effective security measures. Examples include malware infections, ransomware attacks, phishing campaigns, denial-of-service (DoS) attacks, and data breaches targeting payment systems.
These attacks can lead to financial losses, reputational damage, regulatory penalties, and legal liabilities.
Consequences of a Data Breach Exposing Customer Payment Information
A data breach exposing customer payment information can have far-reaching and severe consequences for a retail company. The immediate impact includes significant financial losses from fraudulent transactions, chargebacks, and the costs associated with investigation, remediation, and notification. Beyond the direct financial costs, a data breach severely damages a retailer’s reputation, eroding customer trust and potentially leading to a decline in sales.
Legal and regulatory penalties, such as fines and lawsuits, can also add substantially to the overall cost. The 2017 Equifax breach, for example, resulted in billions of dollars in losses and significant reputational damage. This underscores the critical importance of robust security measures to protect customer data.
Importance of PCI DSS Compliance for Retailers
Payment Card Industry Data Security Standard (PCI DSS) compliance is not merely a suggestion; it’s a critical necessity for any retailer handling credit card information. PCI DSS provides a framework of security standards designed to protect credit card data from unauthorized access, use, disclosure, disruption, modification, or destruction. Compliance involves implementing technical and operational security controls, regularly assessing vulnerabilities, and maintaining detailed security documentation.
Failure to comply with PCI DSS can result in significant fines, penalties, and the loss of the ability to process credit card payments, potentially crippling a retail business. The standards are designed to mitigate the risks associated with processing, storing, and transmitting sensitive payment information.
Hypothetical Phishing Attack Targeting a Retail Company and Its Impact
Imagine a phishing campaign targeting employees of a large retail chain. The attackers send emails appearing to be from a legitimate supplier, requesting urgent payment information. Employees, unaware of the deception, unknowingly provide login credentials or financial details. The attackers then gain access to the company’s internal systems, potentially compromising customer data, financial records, and intellectual property.
The impact of such an attack could be catastrophic, leading to a significant data breach, financial losses, reputational damage, and potential legal action. The recovery process would be costly and time-consuming, potentially impacting the company’s long-term stability. This illustrates the importance of robust employee training programs focused on phishing awareness and secure email practices.
Education
Educational institutions, from K-12 schools to universities, are increasingly becoming targets for cyberattacks. Their reliance on interconnected systems, coupled with the sensitive nature of the data they hold, makes them particularly vulnerable. The consequences of a successful breach can be severe, impacting not only the institution’s reputation but also the privacy and security of students, faculty, and staff.Educational institutions face a multitude of cybersecurity challenges.
These include the ever-evolving landscape of threats, limited budgets for robust security measures, and a lack of awareness and training among both staff and students. The sheer volume of data handled – student records, research data, financial information – presents a large attack surface. Furthermore, the decentralized nature of many educational networks, with multiple campuses and departments, can make comprehensive security management difficult.
Consequences of Data Breaches in Educational Institutions
A data breach exposing student or faculty information can have far-reaching consequences. The immediate impact could include identity theft, financial fraud, and reputational damage to both the individuals affected and the institution. Stolen student data, for example, could be used to apply for loans or credit cards in their names. Faculty research data, if compromised, could lead to intellectual property theft and loss of funding.
Beyond the immediate financial and personal impacts, a breach can severely erode trust in the institution, leading to decreased enrollment and diminished public confidence. Legal ramifications, including hefty fines and lawsuits, are also significant possibilities. The 2017 Equifax breach, though not in education, serves as a stark example of the widespread and long-lasting damage a data breach can cause, highlighting the importance of robust data protection.
Best Practices for Securing Educational Networks and Systems, Top 10 industries most vulnerable to cyber attacks
Implementing robust cybersecurity practices is crucial for educational institutions. This involves a multi-layered approach encompassing technical safeguards, security policies, and employee training. Strong password policies, multi-factor authentication, regular software updates, and robust firewall protection are essential. Regular security audits and penetration testing can identify vulnerabilities before they can be exploited. Data encryption both in transit and at rest is critical to protecting sensitive information.
Implementing a comprehensive data loss prevention (DLP) strategy helps prevent sensitive data from leaving the network unauthorized. Finally, establishing clear incident response plans is vital for mitigating the impact of a successful attack.
Strategies for Educating Students About Cybersecurity Threats
Educating students about cybersecurity threats is paramount. A comprehensive cybersecurity awareness program should be integrated into the curriculum, starting at a young age. This program should include:
- Regular workshops and seminars on topics such as phishing, malware, and social engineering.
- Interactive online modules that teach students about safe online practices.
- Simulations and role-playing exercises to help students learn to identify and respond to real-world threats.
- Encouraging students to report suspicious activity to IT security personnel.
- Promoting the use of strong passwords and multi-factor authentication.
By combining technical safeguards with comprehensive education and training, educational institutions can significantly reduce their vulnerability to cyberattacks and protect the sensitive data entrusted to their care.
Transportation
The transportation sector, encompassing everything from air travel to maritime shipping and ground transportation, is increasingly reliant on interconnected computer systems and networks. This interconnectedness, while boosting efficiency and safety in many ways, creates significant vulnerabilities to cyberattacks. The sheer scale and complexity of these systems, combined with the often outdated security protocols in place, makes them prime targets for malicious actors.Transportation systems face unique vulnerabilities due to their reliance on real-time operations and the critical nature of their services.
A disruption to even a small part of the system can have cascading effects, causing widespread delays, economic losses, and potentially even endangering lives. Furthermore, the diversity of technologies used across different modes of transport creates a complex security landscape, making it challenging to implement comprehensive protection measures.
Cyberattack Consequences on Transportation Operations
A successful cyberattack on a transportation system could have devastating consequences. Consider a scenario involving a ransomware attack targeting a major airport’s air traffic control system. The resulting disruption could ground flights, stranding thousands of passengers, causing massive economic losses for airlines and related businesses, and creating significant security risks. Similarly, a cyberattack targeting a railway network could lead to derailments, collisions, and significant delays, impacting the movement of goods and people.
Attacks on maritime shipping could disrupt global supply chains, leading to shortages of essential goods. The consequences extend beyond immediate operational disruptions; reputational damage and legal liabilities can also be significant.
Cybersecurity’s Role in Transportation Safety and Efficiency
Robust cybersecurity measures are not merely an added expense; they are crucial for maintaining the safety and efficiency of transportation systems. Implementing strong security protocols, including regular security audits, penetration testing, and employee training, is essential to mitigating the risks of cyberattacks. This includes the use of advanced technologies like intrusion detection systems, firewalls, and encryption to protect sensitive data and critical infrastructure.
Collaboration between industry stakeholders, government agencies, and cybersecurity experts is also crucial in sharing threat intelligence and developing best practices.
Hypothetical Cyberattack Scenario and its Consequences
Imagine a sophisticated cyberattack targeting a major port’s container management system. The attackers, using advanced malware, gain unauthorized access and manipulate the system’s data, causing delays and misdirection of cargo containers. This leads to: Significant delays in shipping schedules, resulting in financial losses for businesses reliant on timely delivery of goods; Confusion and logistical nightmares for port operators, customs officials, and freight forwarders; Potential for theft or damage of valuable cargo due to misplaced containers; Reputational damage to the port and its stakeholders, leading to loss of business and trust.
Further, if the attackers gain control of port cranes or other critical infrastructure, physical damage and even casualties could result. This scenario illustrates the far-reaching and potentially catastrophic consequences of a successful cyberattack on a vital transportation hub.
Technology
The technology sector, ironically, faces some of the most significant cybersecurity challenges. While these companies build and sell security solutions, they are also prime targets for sophisticated attacks. Their vast networks, intricate software ecosystems, and the sensitive data they handle make them incredibly vulnerable. The consequences of a successful breach can be devastating, impacting not only the company’s reputation and finances but also the security of their customers and the broader digital landscape.The responsibility of technology companies in ensuring the security of their products and services is paramount.
They are entrusted with protecting vast amounts of personal data, critical infrastructure, and intellectual property. A failure to uphold this responsibility can lead to significant legal repercussions, financial losses, and erosion of public trust. This responsibility extends beyond simply building secure products; it encompasses the entire lifecycle, from design and development to deployment and maintenance.
Software Development Security Best Practices
Secure software development is not an afterthought; it’s a fundamental aspect of the entire process. Implementing robust security measures throughout the software development lifecycle (SDLC) is crucial. This includes employing secure coding practices, rigorous testing, and continuous monitoring. For instance, regularly performing penetration testing can identify vulnerabilities before malicious actors exploit them. Employing static and dynamic code analysis tools can automatically detect common coding flaws that could lead to security breaches.
Furthermore, implementing a comprehensive vulnerability management program, which includes regular patching and updates, is essential to address known weaknesses promptly.
Securing Data and Infrastructure
Protecting data and infrastructure requires a multi-layered approach. Data encryption, both in transit and at rest, is a critical step. Access control mechanisms, such as role-based access control (RBAC), limit access to sensitive data only to authorized personnel. Regular security audits and vulnerability assessments help identify and address weaknesses in the infrastructure. Furthermore, implementing robust incident response plans is essential to minimize the impact of successful attacks.
This includes procedures for detecting, containing, and recovering from security incidents. The use of cloud security tools and services can provide additional layers of protection and help manage the complexity of modern IT infrastructures.
Recommendations for Improving Cybersecurity Posture
Technology companies must proactively invest in and implement robust cybersecurity measures. This requires a cultural shift, emphasizing security as a shared responsibility across all teams and departments.
- Implement a comprehensive security awareness training program: Educate employees about the latest threats and best practices for secure computing.
- Invest in advanced security technologies: Employ intrusion detection and prevention systems, security information and event management (SIEM) tools, and endpoint detection and response (EDR) solutions.
- Regularly update and patch software and systems: This is crucial for mitigating known vulnerabilities.
- Conduct regular security audits and penetration testing: Identify and address security weaknesses before they can be exploited.
- Develop and maintain an incident response plan: Prepare for and respond effectively to security incidents.
- Establish strong data governance policies: Define clear policies for data access, storage, and disposal.
- Embrace DevSecOps: Integrate security practices throughout the entire software development lifecycle.
Ending Remarks
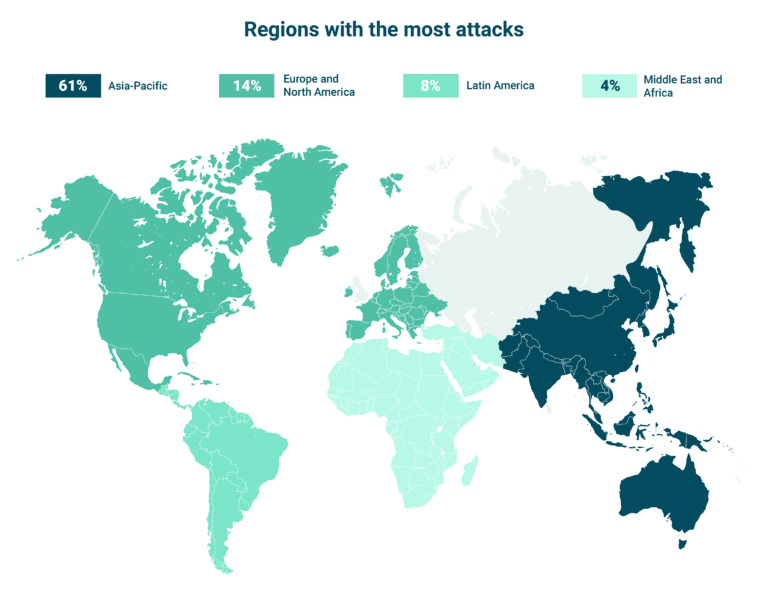
So, there you have it – a glimpse into the top 10 industries most vulnerable to cyberattacks. It’s a sobering picture, but not a hopeless one. While the threats are real and ever-evolving, the solutions are also constantly improving. Increased awareness, robust security measures, and proactive collaboration across industries are crucial in mitigating the risks. By understanding the vulnerabilities, we can better equip ourselves to fight back against these digital threats and protect our critical infrastructure and sensitive data.
Stay vigilant, stay informed, and stay safe in the digital world!
User Queries
What are the most common types of cyberattacks?
Common attacks include phishing (deceptive emails), malware (malicious software), ransomware (data encryption for ransom), denial-of-service (overwhelming systems), and SQL injection (database attacks).
How can individuals protect themselves from cyberattacks?
Strong passwords, up-to-date software, caution with email attachments, avoiding suspicious websites, and using antivirus software are crucial for personal protection.
What is the role of government regulation in cybersecurity?
Governments create and enforce laws and regulations to mandate security practices, investigate breaches, and impose penalties for non-compliance. This helps set a baseline for security standards across industries.
What is the future of cybersecurity?
The future likely involves more sophisticated AI-powered defenses, improved threat intelligence sharing, and a greater emphasis on proactive security measures rather than solely reactive ones.





