Unlocking the Future of Commerce with Cloud Native
Unlocking the future of commerce with cloud native technologies isn’t just a buzzphrase; it’s a revolution reshaping how businesses operate and interact with customers. Imagine a world where online stores effortlessly scale to handle Black Friday traffic, personalize shopping experiences in real-time, and adapt to changing market demands with unprecedented speed. This is the promise of cloud-native commerce, a paradigm shift driven by microservices, containerization, and serverless functions.
Get ready to dive into a world of agility, resilience, and innovation.
This exploration will unpack the core principles of cloud-native architectures, demonstrating how they enhance customer experience, improve scalability and resilience, bolster security, and optimize costs. We’ll also examine the integration challenges and explore the exciting future trends that are poised to transform the e-commerce landscape. From AI-powered personalization to the rise of edge computing, we’ll cover it all.
Defining Cloud-Native Commerce
Cloud-native commerce represents a fundamental shift in how online retail businesses are built and operated. It leverages the scalability, flexibility, and resilience inherent in cloud computing to create highly responsive and adaptable e-commerce platforms. This approach moves away from traditional monolithic architectures towards a more distributed, modular design, enabling businesses to react swiftly to changing market demands and customer expectations.Cloud-native architectures in e-commerce prioritize modularity, automation, and continuous delivery.
This allows for faster development cycles, improved resource utilization, and enhanced resilience in the face of unexpected traffic spikes or failures. The core principle is to decouple various functionalities into independent services, making the entire system more manageable and adaptable.
Microservices and Agility in Online Retail
Microservices architecture is a cornerstone of cloud-native commerce. Instead of a single, large application, e-commerce functionalities (e.g., product catalog, shopping cart, payment processing, order management) are broken down into smaller, independent services. Each microservice is responsible for a specific business function and can be developed, deployed, and scaled independently. This allows for greater agility – new features can be added or existing ones updated without impacting the entire system.
For example, a retailer could deploy a new payment gateway integration without requiring a complete application update, minimizing downtime and accelerating innovation. The independent scaling of microservices also ensures that resources are allocated efficiently, responding effectively to peak demand periods like Black Friday or Cyber Monday. A surge in order processing, for instance, can be handled by scaling only the order management microservice, rather than the entire application.
Containerization and E-commerce Applications
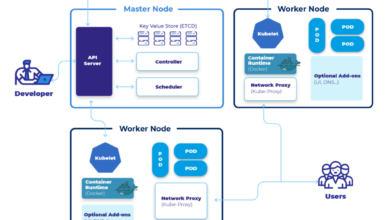
Containerization technologies, primarily Docker and Kubernetes, are crucial for implementing cloud-native e-commerce. Docker packages applications and their dependencies into isolated containers, ensuring consistent execution across different environments (development, testing, production). This portability simplifies deployment and reduces the risk of environment-specific issues. Kubernetes orchestrates the deployment, scaling, and management of these containers, automating many of the operational tasks. This automation significantly reduces operational overhead and increases reliability.
Imagine a scenario where a specific microservice experiences a failure. Kubernetes automatically detects the failure, terminates the faulty container, and spins up a new, healthy instance, ensuring minimal disruption to the overall e-commerce platform. This level of automated self-healing is a significant advantage of using containerization in e-commerce.
Enhanced Customer Experience
Cloud-native architectures offer a powerful toolkit for dramatically improving the customer experience in e-commerce. By leveraging the scalability, flexibility, and agility inherent in these systems, businesses can create online shopping experiences that are personalized, responsive, and truly engaging. This leads to increased customer satisfaction, loyalty, and ultimately, higher conversion rates.The shift towards cloud-native empowers businesses to move away from monolithic systems that struggle to keep pace with modern customer expectations.
Instead, they can adopt microservices, enabling independent scaling and faster updates, resulting in a more dynamic and responsive online environment.
Designing User Interfaces for Enhanced Engagement
Cloud-native technologies provide the infrastructure for building highly interactive and personalized user interfaces. Real-time data processing, facilitated by technologies like Apache Kafka and other streaming platforms, allows for immediate feedback and dynamic content updates. For example, a clothing retailer could use real-time data to show a user products similar to those they’ve viewed or added to their cart, creating a more personalized and engaging shopping journey.
This dynamic adjustment of the user interface, driven by real-time insights, is significantly more challenging with traditional, monolithic systems. Imagine a website that instantly suggests relevant accessories based on the item in your shopping cart, or dynamically adjusts product displays based on your past purchase history – this is the power of cloud-native UI design.
Real-Time Data Processing and Personalization
Real-time data processing is the engine driving personalized online shopping experiences. By analyzing user behavior in real-time – browsing history, cart contents, location, even device type – businesses can deliver highly targeted recommendations and offers. For instance, a travel website might use real-time data to show a user flight deals based on their current location and search history, or a bookstore might suggest books similar to those they’ve recently purchased.
This level of personalization fosters a sense of connection and understanding, making the customer feel valued and understood. The speed and efficiency of cloud-native platforms are crucial for processing the vast amounts of data required for this level of personalization. A lag in response time would significantly diminish the impact of these personalized recommendations.
Serverless Functions and Seamless User Experiences
Serverless functions, such as those offered by AWS Lambda or Google Cloud Functions, play a vital role in creating seamless and responsive user experiences. These functions can be triggered by specific events, such as a user adding an item to their cart or completing a purchase, allowing for immediate processing and updates. For example, a serverless function could automatically send a confirmation email, update inventory levels, or trigger a personalized marketing campaign.
This event-driven architecture eliminates the need for constantly running servers, reducing costs and improving efficiency while ensuring rapid responses to user interactions. The responsiveness translates directly to a more enjoyable and frustration-free shopping experience.
Comparison of Traditional and Cloud-Native E-commerce Architectures
| Feature | Traditional E-commerce | Cloud-Native E-commerce |
|---|---|---|
| Scalability | Limited, requires significant upfront investment and planning | Highly scalable, easily adapts to traffic spikes and fluctuations |
| Personalization | Often limited to basic segmentation and batch processing | Real-time personalization based on individual user behavior |
| Responsiveness | Can be slow, especially during peak times | Highly responsive, providing near-instantaneous feedback |
| Deployment Speed | Slow and complex, requiring extensive testing and downtime | Fast and iterative, allowing for frequent updates and new feature releases |
Scalability and Resilience

Building a cloud-native e-commerce platform isn’t just about creating a slick online store; it’s about building a system that can handle anything the market throws at it. This means designing for massive scalability to accommodate peak demand during holiday seasons or flash sales, and building in robust resilience to ensure the platform remains operational even in the face of unexpected outages or failures.
This section dives into the strategies and technologies that make this possible.The ability to seamlessly scale your e-commerce platform is crucial for success. Imagine a Black Friday scenario where your traffic spikes tenfold – a poorly designed system would buckle under the pressure, resulting in lost sales and damaged reputation. Cloud-native architectures, however, offer solutions to handle these surges gracefully and efficiently.
Strategies for Scaling Cloud-Native E-commerce Platforms
Horizontal scaling is the cornerstone of cloud-native scalability. Instead of relying on a single, powerful server, a cloud-native platform uses many smaller, independent servers that can be added or removed as needed. This allows the platform to dynamically adjust its capacity to match real-time demand. For example, during peak hours, additional servers can be automatically provisioned to handle the increased traffic, and then scaled back down during off-peak periods, optimizing resource utilization and cost-effectiveness.
This contrasts sharply with traditional monolithic architectures which require significant upfront investment and often struggle to adapt to sudden increases in demand.
Automated Deployments and Rollbacks for Business Continuity
Downtime in e-commerce is simply unacceptable. Automated deployment pipelines, a key feature of cloud-native environments, minimize the risk of disruptions. These pipelines automate the process of building, testing, and deploying new code, ensuring rapid and reliable updates. Crucially, they also include rollback mechanisms. If a new deployment introduces a bug or causes unexpected issues, the system can automatically revert to the previous stable version, minimizing the impact on customers and revenue.
This automated fail-safe mechanism is a significant advantage over manual deployments, which are prone to human error and significantly slower recovery times. For example, a company might use tools like Jenkins or GitLab CI/CD to orchestrate these automated processes.
Improving E-commerce System Resilience Against Failures
Cloud-native architectures inherently enhance resilience through several mechanisms. Microservices, a core component of cloud-native design, isolate functionalities into independent services. If one service fails, the others continue to operate normally, preventing a cascading failure that could cripple the entire system. Load balancing distributes traffic across multiple instances of each service, further mitigating the impact of individual service failures. Furthermore, the use of containerization (e.g., Docker) and orchestration (e.g., Kubernetes) simplifies deployment and management, allowing for rapid recovery from failures.
For instance, if a server fails, Kubernetes automatically restarts the affected containers on a healthy node, ensuring continuous availability.
Benefits of Using a Distributed Database System
Traditional, centralized databases become bottlenecks under high load. A distributed database system, on the other hand, spreads data across multiple servers, improving scalability, availability, and resilience. If one database server fails, the system can continue operating using data from other servers. This ensures high availability even in the event of hardware failures. Furthermore, distributed databases often offer improved performance through data partitioning and parallel processing.
Examples of distributed database systems suitable for e-commerce include Cassandra, MongoDB, and CockroachDB. These systems offer features like automatic replication and sharding, which are crucial for handling the scale and complexity of modern e-commerce applications. The improved performance translates directly to faster page load times and a smoother shopping experience for customers.
Security and Compliance
Building a secure and compliant cloud-native e-commerce platform is paramount. The distributed nature of microservices and the reliance on container orchestration introduce new security challenges, but also offer opportunities to enhance security posture through granular control and automation. Meeting regulatory requirements like GDPR and CCPA demands a proactive and layered approach to data protection and privacy.The inherent flexibility and scalability of cloud-native architectures, however, can be leveraged to build a robust security framework.
By strategically implementing security measures at each layer, from infrastructure to application, businesses can mitigate risks and ensure compliance. This approach not only protects sensitive customer data but also builds trust and maintains a positive brand reputation.
Key Security Considerations for Cloud-Native E-commerce Platforms
Several key areas demand careful consideration when securing a cloud-native e-commerce platform. These include securing the infrastructure, implementing robust authentication and authorization mechanisms, protecting sensitive data at rest and in transit, and ensuring the continuous monitoring and logging of system activity. A failure in any of these areas can lead to significant security breaches, data loss, and reputational damage.
A multi-layered approach is crucial, combining preventative measures with detection and response capabilities.
Securing Microservices and Containerized Applications
Securing microservices and containerized applications requires a shift from traditional perimeter-based security to a more granular, distributed approach. Each microservice needs to be secured individually, with appropriate authentication and authorization mechanisms implemented. Container images should be scanned for vulnerabilities before deployment, and runtime security measures, such as intrusion detection and prevention systems, should be integrated into the container orchestration platform.
Furthermore, secrets management and robust logging are critical for maintaining security and enabling effective incident response. Regular security audits and penetration testing are also essential to identify and address potential vulnerabilities proactively.
Meeting Regulatory Compliance Requirements with Cloud-Native Approaches
Cloud-native approaches can significantly aid in meeting regulatory compliance requirements such as GDPR and CCPA. The ability to track data flows, implement fine-grained access controls, and maintain detailed audit logs makes it easier to demonstrate compliance. For example, the ability to quickly identify and isolate compromised microservices minimizes the impact of a data breach and aids in complying with data breach notification requirements.
Features like data masking and encryption, readily integrated into cloud-native architectures, help protect sensitive customer data, fulfilling the requirements of regulations regarding data privacy and protection. Furthermore, the use of immutable infrastructure and automated deployment processes reduces the risk of human error and improves overall security posture.
Security Measures for Sensitive Customer Data in a Cloud-Native Environment
Implementing robust security measures for sensitive customer data is crucial in a cloud-native environment. The following list Artikels key security practices:
- Data Encryption at Rest and in Transit: Encrypting data both while it’s stored and while it’s being transmitted ensures that even if a breach occurs, the data remains unreadable.
- Access Control and Authorization: Implement granular access controls based on the principle of least privilege, ensuring that only authorized users and systems can access sensitive data.
- Data Loss Prevention (DLP): Employ DLP tools to monitor and prevent the unauthorized transfer of sensitive data outside the organization’s control.
- Regular Security Audits and Penetration Testing: Conduct regular security assessments to identify vulnerabilities and ensure the effectiveness of security controls.
- Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS to monitor network traffic and system activity for malicious behavior.
- Vulnerability Scanning and Patch Management: Regularly scan for vulnerabilities in applications and infrastructure components and promptly apply security patches.
- Secure Development Practices: Integrate security into the software development lifecycle (SDLC) to prevent vulnerabilities from being introduced into the codebase.
- Centralized Logging and Monitoring: Implement a centralized logging and monitoring system to track system activity and detect security incidents in real-time.
Innovation and Future Trends
Cloud-native architecture isn’t just about building better e-commerce platforms; it’s about fostering a climate of continuous innovation. By embracing microservices, serverless functions, and agile development methodologies, businesses unlock the potential to rapidly adapt to changing market demands and integrate cutting-edge technologies seamlessly. This flexibility allows for experimentation and the rapid deployment of new features, ultimately leading to a more dynamic and responsive e-commerce experience.The inherent scalability and resilience of cloud-native systems are crucial for supporting innovative applications.
This allows businesses to experiment with new features and functionalities without fear of overwhelming their infrastructure. This trial-and-error approach is essential for driving innovation and staying ahead of the curve in the rapidly evolving e-commerce landscape.
Innovative Applications of Cloud-Native Technologies
Several innovative applications of cloud-native technologies are transforming the e-commerce sector. Personalized shopping experiences, driven by microservices that analyze individual customer data in real-time, are becoming increasingly common. For example, a clothing retailer might use a microservice to analyze a customer’s browsing history and recommend relevant products, while another microservice handles personalized promotions and discounts. Similarly, serverless functions can power features like automated order processing, fraud detection, and real-time inventory updates, streamlining operations and enhancing efficiency.
The ability to scale these functions independently based on demand ensures a smooth and responsive experience, even during peak shopping seasons.
The Impact of AI and Machine Learning
Artificial intelligence and machine learning are poised to revolutionize cloud-native commerce. AI-powered chatbots can provide 24/7 customer support, handling routine inquiries and freeing up human agents to focus on more complex issues. Machine learning algorithms can analyze vast amounts of customer data to predict demand, optimize pricing strategies, and personalize product recommendations with unprecedented accuracy. For example, Amazon’s recommendation engine, a prime example of AI’s impact, leverages vast datasets and sophisticated algorithms to suggest relevant products to users, significantly boosting sales.
Furthermore, AI can enhance fraud detection systems, identifying and preventing fraudulent transactions before they occur. This proactive approach minimizes losses and enhances the security of the entire e-commerce ecosystem.
Predictions for the Future of Cloud-Native E-commerce
The future of cloud-native e-commerce will be shaped by several emerging technologies and trends. The rise of edge computing will enable faster loading times and reduced latency, particularly crucial for customers in areas with limited internet connectivity. This will be especially impactful for businesses serving geographically diverse customer bases. Furthermore, the increasing adoption of blockchain technology holds the potential to enhance transparency and security in supply chain management and payment processing.
Imagine a scenario where the entire journey of a product, from its origin to the customer’s doorstep, is transparently tracked on a blockchain, building trust and accountability. We can also expect a continued rise in the use of augmented and virtual reality (AR/VR) technologies to enhance the online shopping experience, allowing customers to virtually try on clothes or visualize furniture in their homes before purchasing.
This immersive experience is expected to significantly improve customer engagement and conversion rates.
Challenges in Adopting Cloud-Native Technologies
Adopting cloud-native technologies presents several challenges for e-commerce businesses. The initial investment in infrastructure and expertise can be significant, requiring a substantial commitment of resources. Furthermore, migrating existing legacy systems to a cloud-native architecture can be complex and time-consuming, requiring careful planning and execution. Businesses must also address the security and compliance requirements associated with cloud-based environments, ensuring the protection of sensitive customer data.
Finally, finding and retaining skilled professionals with expertise in cloud-native technologies can be a significant hurdle, given the high demand for such talent in the current market. Companies like Shopify, however, demonstrate that with proper planning and execution, these challenges can be overcome, leading to significant competitive advantages.
Cost Optimization and Efficiency

Migrating to a cloud-native e-commerce platform offers significant cost advantages over traditional on-premise solutions. The inherent scalability and flexibility of cloud-native architectures directly translate into reduced operational expenses and improved resource utilization. Let’s delve into the specifics.Traditional e-commerce platforms often involve substantial upfront investments in hardware, software licenses, and dedicated IT staff. Maintaining this infrastructure requires ongoing capital expenditure for upgrades, maintenance, and security patches.
In contrast, cloud-native solutions leverage a pay-as-you-go model, minimizing upfront costs and aligning expenses directly with actual usage.
Infrastructure Cost Comparison
Traditional e-commerce platforms demand significant upfront investment in servers, networking equipment, and data centers. These investments are substantial and often require long-term contracts, leading to inflexible scaling and potential overspending on resources that remain underutilized during periods of low demand. Cloud-native platforms, on the other hand, utilize virtualized infrastructure and serverless functions, allowing businesses to scale resources dynamically based on real-time demand.
This eliminates the need for over-provisioning and reduces capital expenditure significantly. For example, a traditional setup might require purchasing and maintaining ten servers to handle peak traffic, even if only three are utilized during off-peak hours. A cloud-native system can dynamically scale to use only three servers during off-peak times and then automatically scale up to ten (or more) during peak demand, only paying for the resources consumed.
Operational Cost Savings
The operational costs associated with managing traditional e-commerce infrastructure are considerable. This includes salaries for IT staff responsible for maintenance, updates, and security, as well as expenses for software licenses, energy consumption, and physical space. Cloud-native architectures drastically reduce these operational overheads. Automated deployments, scaling, and monitoring capabilities significantly decrease the need for manual intervention, reducing the reliance on large IT teams.
Furthermore, cloud providers handle the underlying infrastructure maintenance, freeing up internal resources to focus on business-critical tasks. Consider the example of patching security vulnerabilities: in a traditional setup, this is a manual, time-consuming process requiring dedicated personnel. In a cloud-native environment, these updates are often automated, significantly reducing downtime and operational costs.
Resource Optimization Strategies
Cloud-native architectures offer a range of tools and techniques to optimize resource utilization and minimize costs. These include auto-scaling, containerization, and serverless computing. Auto-scaling dynamically adjusts computing resources based on real-time demand, ensuring optimal performance while avoiding wasted capacity. Containerization improves resource efficiency by packaging applications and their dependencies into isolated units, allowing for efficient resource sharing and improved utilization.
Serverless computing further optimizes resource usage by executing code only when needed, eliminating the need to maintain idle servers. Implementing these strategies results in a more efficient and cost-effective operation. For instance, a company running a seasonal promotion can leverage auto-scaling to automatically increase server capacity during peak demand and then scale down once the promotion ends, resulting in significant cost savings compared to maintaining a consistently high capacity throughout the year.
Resource Utilization Comparison
Imagine two diagrams representing resource utilization. The first, representing a traditional e-commerce platform, shows a mostly flat line at a high level, indicating consistent resource allocation regardless of demand. Significant portions of the allocated resources remain underutilized, especially during off-peak hours. The second diagram, illustrating a cloud-native setup, shows a fluctuating line closely mirroring demand. Resources are dynamically allocated, peaking during high traffic periods and minimizing during low traffic, reflecting efficient resource usage and minimizing waste.
This visual comparison effectively highlights the cost-saving potential of cloud-native architectures.
Integration and Interoperability: Unlocking The Future Of Commerce With Cloud Native
Building a truly effective cloud-native e-commerce platform isn’t just about deploying microservices; it’s about seamlessly integrating them with existing systems and ensuring smooth communication between different parts of your architecture. This requires careful planning and the right technological choices to avoid creating a fragmented, inefficient system. Successfully navigating this integration process is key to unlocking the full potential of cloud-native commerce.Integrating a modern, cloud-native e-commerce platform with legacy systems presents unique challenges.
These older systems often lack the agility and flexibility of their cloud-native counterparts, employing different data formats, communication protocols, and security measures. However, strategic approaches can bridge this gap and unlock the benefits of both worlds.
Strategies for Integrating Cloud-Native E-commerce Platforms with Existing Legacy Systems
Successful integration hinges on a well-defined strategy. Common approaches include building custom connectors to translate data and communication between the new and old systems. Another effective method is employing an Enterprise Service Bus (ESB) which acts as a central hub, managing communication and data transformation between disparate systems. API gateways also play a crucial role, providing a controlled and secure interface to legacy systems, exposing only necessary functionalities to the cloud-native platform.
Finally, a phased approach, gradually migrating functionality from legacy systems to the cloud-native platform, minimizes disruption and risk.
APIs and Microservices Facilitate Interoperability
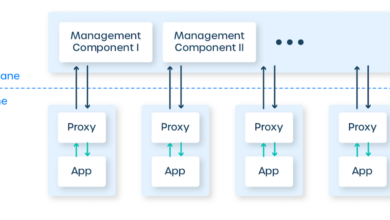
APIs (Application Programming Interfaces) are the cornerstone of interoperability in a cloud-native architecture. Microservices, by their very nature, expose their functionality through well-defined APIs, allowing different services to communicate and exchange data. This promotes modularity, allowing for independent development, deployment, and scaling of individual services. For example, a microservice responsible for order management can expose APIs to communicate with a payment processing service, a shipping service, and an inventory management service, all without direct dependencies.
This loose coupling is essential for flexibility and resilience.
Benefits of Using Message Queues for Asynchronous Communication
In a cloud-native environment, asynchronous communication, facilitated by message queues, offers significant advantages. Message queues decouple services, allowing them to operate independently and preventing one slow service from impacting others. This improves overall system resilience and scalability. For instance, when a customer places an order, the order processing service can send a message to the queue, and the payment processing service can retrieve the message at its own pace.
This prevents bottlenecks and ensures that the entire system remains responsive even under high load. Furthermore, message queues provide a buffer, enabling services to handle temporary outages or surges in demand.
System Architecture Diagram: Integrating Components in a Cloud-Native E-commerce Platform, Unlocking the future of commerce with cloud native
Imagine a system architecture where the frontend (website or mobile app) interacts with an API gateway. This gateway acts as a central point of entry, routing requests to various microservices. These microservices handle specific functionalities, such as catalog management, order processing, payment processing, inventory management, and customer relationship management (CRM). Each microservice communicates with others through APIs, often using message queues for asynchronous communication.
Legacy systems, such as an older ERP system, might be integrated via custom connectors or an ESB, feeding data into the cloud-native platform or receiving data from it via APIs. A database, potentially a distributed NoSQL database, underpins the entire system, providing persistent storage for data. Security measures, such as authentication and authorization, are implemented at various layers, including the API gateway and individual microservices.
Monitoring and logging tools provide insights into the system’s performance and health. This layered architecture promotes scalability, resilience, and maintainability.
Closure
The journey into the cloud-native future of commerce is both exciting and transformative. While challenges exist in adoption and integration, the potential rewards – increased agility, enhanced customer experiences, and significant cost savings – are undeniable. By embracing these technologies, businesses can not only survive but thrive in the ever-evolving digital marketplace. The key is strategic planning, careful implementation, and a willingness to embrace the innovative potential of cloud-native architectures.
The future of commerce is here, and it’s built in the cloud.
FAQ
What are the biggest challenges in migrating to a cloud-native e-commerce platform?
The biggest hurdles often include legacy system integration, the need for skilled DevOps talent, and the potential complexities of managing a distributed architecture. Careful planning and phased migration strategies are crucial.
How does cloud-native architecture improve security?
Cloud-native approaches enhance security through features like granular access control, improved monitoring and logging, and automated security patching within containers and microservices. This allows for faster response to vulnerabilities.
What’s the difference between serverless and microservices?
Microservices are independently deployable units of application functionality, while serverless functions are event-driven and automatically scale based on demand. Serverless can be
-part* of a microservices architecture.
Is cloud-native commerce suitable for small businesses?
While the initial investment might seem high, cloud-native offers scalability that can benefit small businesses as they grow. Leveraging managed services can help reduce operational overhead.